
You're engaging in professional malpractice if you don't share this with your stakeholders. Corey may be an engineer, but he communicates about the issues in an accessible manner.
www.theregister.com/2025/10/20/a...

You're engaging in professional malpractice if you don't share this with your stakeholders. Corey may be an engineer, but he communicates about the issues in an accessible manner.
www.theregister.com/2025/10/20/a...


spacefromspace.com/declassified...
spacefromspace.com/declassified...
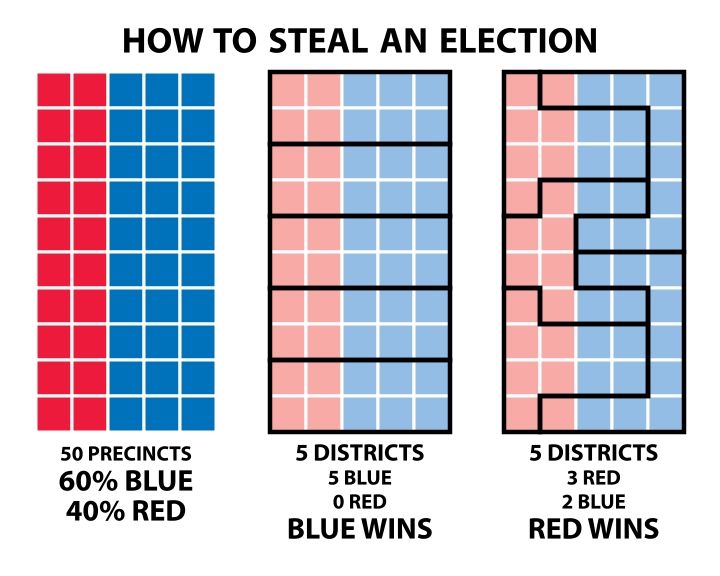


youtu.be/xMYm2d9bmEA

youtu.be/xMYm2d9bmEA

memoryanalysis.net/courses-malw...

memoryanalysis.net/courses-malw...

www.youtube.com/watch?v=vc4y...

www.youtube.com/watch?v=vc4y...



