ϻг_ϻε
@steven.srcincite.io
Hermetic Initiate. Exploring conscience and the nature of reality. I also hack things.
Reposted by ϻг_ϻε
If you're using ruby-saml or omniauth-saml for SAML authentication make sure to update these libraries as fast as possible! Fixes for two critical authentication bypass vulnerabilities were published today (CVE-2025-25291 + CVE-2025-25292).
github.blog/security/sig...
github.blog/security/sig...
Sign in as anyone: Bypassing SAML SSO authentication with parser differentials
Critical authentication bypass vulnerabilities were discovered in ruby-saml up to version 1.17.0. See how they were uncovered.
github.blog
March 12, 2025 at 9:50 PM
If you're using ruby-saml or omniauth-saml for SAML authentication make sure to update these libraries as fast as possible! Fixes for two critical authentication bypass vulnerabilities were published today (CVE-2025-25291 + CVE-2025-25292).
github.blog/security/sig...
github.blog/security/sig...
Reposted by ϻг_ϻε
NEW JWST IMAGE SHOWING A PROTOPLANETARY DISK AROUND A NEWLY FORMED STAR!!! 🤩

February 5, 2025 at 12:00 AM
NEW JWST IMAGE SHOWING A PROTOPLANETARY DISK AROUND A NEWLY FORMED STAR!!! 🤩
Reposted by ϻг_ϻε
Last year, I committed to uncovering critical vulnerabilities in Maven repositories. Now it’s time to share the findings: RCE in Sonatype Nexus, Cache Poisoning in JFrog Artifactory, and more! github.blog/security/vul...
January 22, 2025 at 6:16 PM
Last year, I committed to uncovering critical vulnerabilities in Maven repositories. Now it’s time to share the findings: RCE in Sonatype Nexus, Cache Poisoning in JFrog Artifactory, and more! github.blog/security/vul...
This is what I love about Chris, authenticity: muffsec.com/blog/abstain.... Btw I couldn’t agree more with his conclusion about the event.
Abstaining From Pwn2own – muffSec
muffsec.com
January 22, 2025 at 9:37 AM
This is what I love about Chris, authenticity: muffsec.com/blog/abstain.... Btw I couldn’t agree more with his conclusion about the event.
Reposted by ϻг_ϻε
Bitcoin is enemy of culture because it introduces monetary incentive where only prestige belongs.
January 17, 2025 at 6:13 PM
Bitcoin is enemy of culture because it introduces monetary incentive where only prestige belongs.
Reposted by ϻг_ϻε
I wrote a PoC for the recent Ivanti Connect Secure stack buffer overflow, CVE-2025-0282, based on the exploitation strategy watchTowr published, along with an assessment of exploitability given the lack of a suitable info leak to break ASLR: attackerkb.com/assessments/...
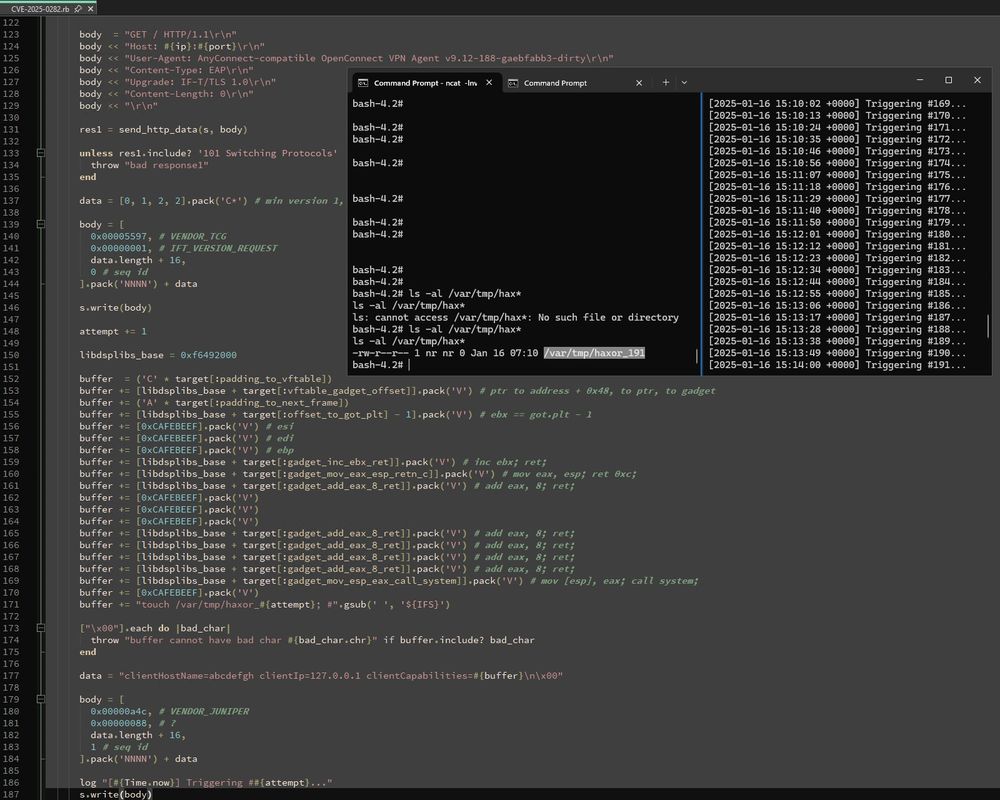
January 16, 2025 at 3:52 PM
I wrote a PoC for the recent Ivanti Connect Secure stack buffer overflow, CVE-2025-0282, based on the exploitation strategy watchTowr published, along with an assessment of exploitability given the lack of a suitable info leak to break ASLR: attackerkb.com/assessments/...
Reposted by ϻг_ϻε
What's the point of being rich if you can't afford to do the right thing.
January 13, 2025 at 4:29 PM
What's the point of being rich if you can't afford to do the right thing.
Reposted by ϻг_ϻε
Nominations are now open for the Top 10 Web Hacking Techniques of 2024! Browse the contestants and submit your own here:
portswigger.net/research/top...
portswigger.net/research/top...

Top ten web hacking techniques of 2024: nominations open
Nominations are now open for the top 10 new web hacking techniques of 2024! Every year, security researchers from all over the world share their latest findings via blog posts, presentations, PoCs, an
portswigger.net
January 8, 2025 at 2:09 PM
Nominations are now open for the Top 10 Web Hacking Techniques of 2024! Browse the contestants and submit your own here:
portswigger.net/research/top...
portswigger.net/research/top...
Reposted by ϻг_ϻε
Just unrestricted an issue that shows a fun new attack surface. Android RCS locally transcribes incoming media, making vulnerabilities audio codecs now fully-remote. This bug in an obscure Samsung S24 codec is 0-click
project-zero.issues.chromium.org/issues/36869...
project-zero.issues.chromium.org/issues/36869...
Project Zero
project-zero.issues.chromium.org
January 10, 2025 at 12:08 AM
Just unrestricted an issue that shows a fun new attack surface. Android RCS locally transcribes incoming media, making vulnerabilities audio codecs now fully-remote. This bug in an obscure Samsung S24 codec is 0-click
project-zero.issues.chromium.org/issues/36869...
project-zero.issues.chromium.org/issues/36869...
Reposted by ϻг_ϻε
Positive Technologies published two scenarios they encountered during pentests, where they pivot to the internal network thanks to an Internet-facing Exchange server and its numerous SSRF vectors 💎
static.ptsecurity.com
December 27, 2024 at 1:39 PM
Positive Technologies published two scenarios they encountered during pentests, where they pivot to the internal network thanks to an Internet-facing Exchange server and its numerous SSRF vectors 💎
Reposted by ϻг_ϻε
TIL how easy it is to ask curl to dump TLS session keys to disk 🛠️
Simply set the environment variable `SSLKEYLOGFILE=/path/to/file` 😅 Note: it also works for Firefox and Chrome
Extremely useful when combined with Wireshark 👍
Simply set the environment variable `SSLKEYLOGFILE=/path/to/file` 😅 Note: it also works for Firefox and Chrome
Extremely useful when combined with Wireshark 👍
December 20, 2024 at 11:35 AM
TIL how easy it is to ask curl to dump TLS session keys to disk 🛠️
Simply set the environment variable `SSLKEYLOGFILE=/path/to/file` 😅 Note: it also works for Firefox and Chrome
Extremely useful when combined with Wireshark 👍
Simply set the environment variable `SSLKEYLOGFILE=/path/to/file` 😅 Note: it also works for Firefox and Chrome
Extremely useful when combined with Wireshark 👍
Reposted by ϻг_ϻε
CVE-2024-12727 Sophos coming in with an unauthenticated SQLi in their firewall appliance 👏
December 22, 2024 at 8:43 AM
CVE-2024-12727 Sophos coming in with an unauthenticated SQLi in their firewall appliance 👏
These are some really nice blog posts regarding algo confusion bugs in JWT by @pentesterlab.com pentesterlab.com/blog/jwt-alg... & pentesterlab.com/blog/another... nice one @snyff.pentesterlab.com!

PentesterLab Blog: Another JWT Algorithm Confusion Vulnerability: CVE-2024-54150
Discover how a code review uncovered a JWT algorithm confusion vulnerability (CVE-2024-54150). Learn key insights to enhance your security skills and spot vulnerabilities effectively.
pentesterlab.com
December 22, 2024 at 7:06 PM
These are some really nice blog posts regarding algo confusion bugs in JWT by @pentesterlab.com pentesterlab.com/blog/jwt-alg... & pentesterlab.com/blog/another... nice one @snyff.pentesterlab.com!
Reposted by ϻг_ϻε
Happy Winter Solstice!
These photos were taken with a pinhole camera I made from a beer can and left out from Summer to Winter Solstice - a 6 month exposure.
Bottom line = Winter Solstice. Top line = Summer Solstice.
The lines are the Sun moving across the sky w/some reflections. No line = clouds
These photos were taken with a pinhole camera I made from a beer can and left out from Summer to Winter Solstice - a 6 month exposure.
Bottom line = Winter Solstice. Top line = Summer Solstice.
The lines are the Sun moving across the sky w/some reflections. No line = clouds


December 21, 2024 at 2:01 PM
Happy Winter Solstice!
These photos were taken with a pinhole camera I made from a beer can and left out from Summer to Winter Solstice - a 6 month exposure.
Bottom line = Winter Solstice. Top line = Summer Solstice.
The lines are the Sun moving across the sky w/some reflections. No line = clouds
These photos were taken with a pinhole camera I made from a beer can and left out from Summer to Winter Solstice - a 6 month exposure.
Bottom line = Winter Solstice. Top line = Summer Solstice.
The lines are the Sun moving across the sky w/some reflections. No line = clouds
Reposted by ϻг_ϻε
[4/n] My Hexacon 2023 talk about .NET Deserialization. New gadgets, insecure serialization (RCE through serialization) and custom gadgets found in the products codebase.
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
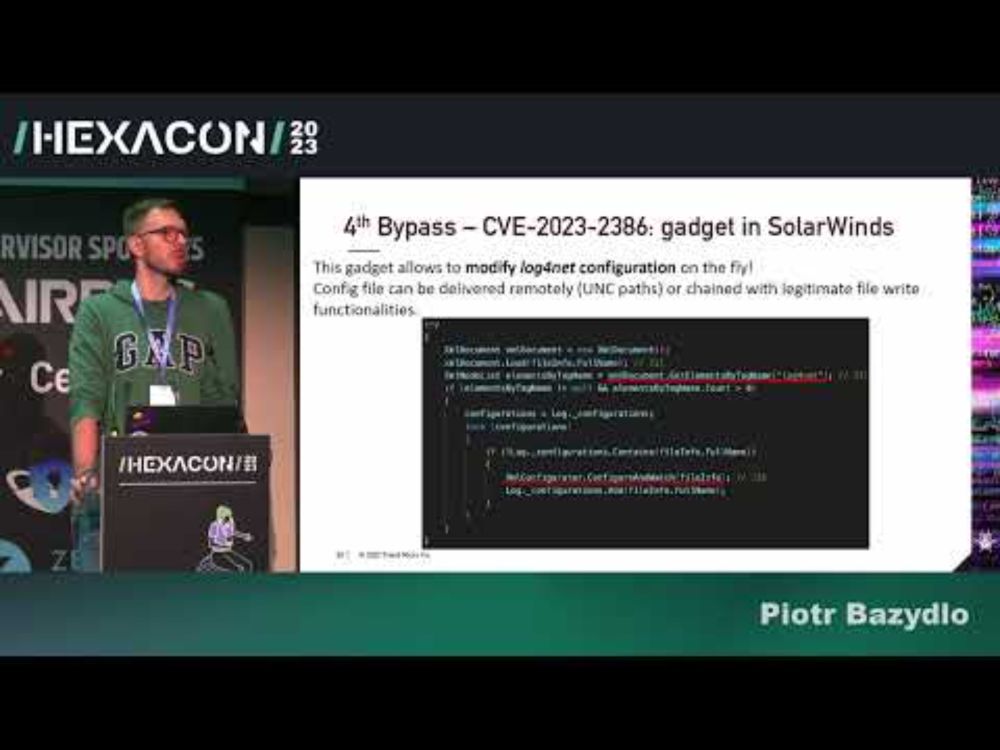
HEXACON2023 - Exploiting Hardened .NET Deserialization by Piotr Bazydło
YouTube video by Hexacon
www.youtube.com
December 19, 2024 at 11:39 AM
[4/n] My Hexacon 2023 talk about .NET Deserialization. New gadgets, insecure serialization (RCE through serialization) and custom gadgets found in the products codebase.
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
Reposted by ϻг_ϻε
I put together a VERY limited (for now) list of web hackers in a Starter pack:
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
December 18, 2024 at 12:54 AM
I put together a VERY limited (for now) list of web hackers in a Starter pack:
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
S2-067 is a fantastic bypass of the patch for S2-066. It uses ONGL to re-write the upload filename property in order to bypass the filename path traversal checks.
PoC: if the target bean is called "UploadFile" the your target parameter is "top.UploadFileFileName". 🤯
PoC: if the target bean is called "UploadFile" the your target parameter is "top.UploadFileFileName". 🤯
December 17, 2024 at 8:29 PM
S2-067 is a fantastic bypass of the patch for S2-066. It uses ONGL to re-write the upload filename property in order to bypass the filename path traversal checks.
PoC: if the target bean is called "UploadFile" the your target parameter is "top.UploadFileFileName". 🤯
PoC: if the target bean is called "UploadFile" the your target parameter is "top.UploadFileFileName". 🤯
Reposted by ϻг_ϻε
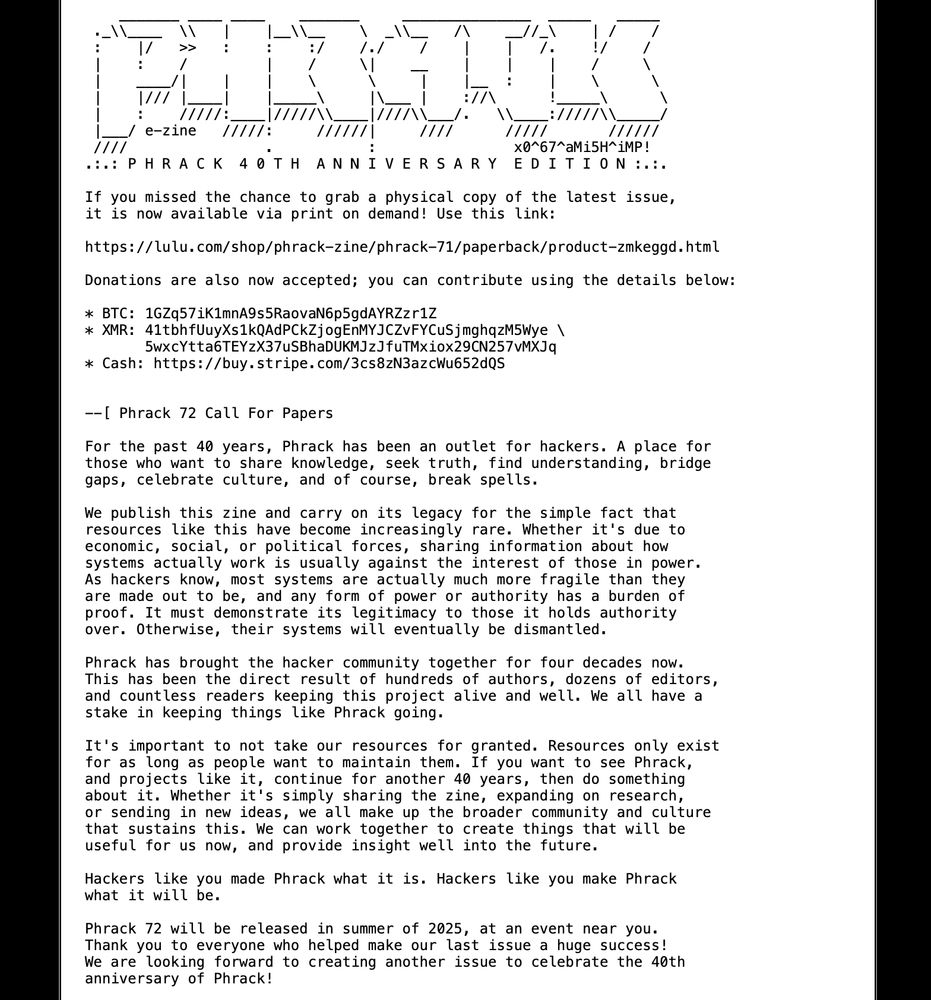
We updated our CFP for Phrack 72! The deadline is now April 1st 2025. Check the site for specifics on how to contribute, as well as some inspiration! We also posted a link to purchase physical copies of Phrack 71, and a donation link too. Enjoy!
phrack.org
phrack.org
December 16, 2024 at 10:56 PM
We updated our CFP for Phrack 72! The deadline is now April 1st 2025. Check the site for specifics on how to contribute, as well as some inspiration! We also posted a link to purchase physical copies of Phrack 71, and a donation link too. Enjoy!
phrack.org
phrack.org
Reposted by ϻг_ϻε
wokism is out of control

December 17, 2024 at 5:21 AM
wokism is out of control
…and what is your office? My office is that which is in the higher aspirant of the soul - Ma’at
December 16, 2024 at 11:05 PM
…and what is your office? My office is that which is in the higher aspirant of the soul - Ma’at
Reposted by ϻг_ϻε
A companion blog to my Bluehat 2024 presentation on OleView.NET is up now. googleprojectzero.blogspot.com/2024/12/wind...
googleprojectzero.blogspot.com
December 12, 2024 at 11:32 PM
A companion blog to my Bluehat 2024 presentation on OleView.NET is up now. googleprojectzero.blogspot.com/2024/12/wind...
Reposted by ϻг_ϻε
I wrote a fun, little blog post. Remote pre-auth file deletion in SolarWinds ARM allowed to achieve LPE on AD machines 🙃
In his latest blog, @chudypb.bsky.social covers a pre-auth Arbitrary File Deletion bug he discovered in the SolarWinds Access Rights Manager (ARM). It may not sound exciting, but it can lead to an LPE on domain-joined Windows machines. Read the details at www.zerodayinitiative.com/blog/2024/12...

Zero Day Initiative — SolarWinds Access Rights Manager: One Vulnerability to LPE Them All
Some time ago, I spent some time researching a core SolarWinds product, SolarWinds Platform (previously Orion Platform). At that time, I hadn’t been aware of the SolarWinds Access Right Manager produc...
www.zerodayinitiative.com
December 12, 2024 at 6:03 PM
I wrote a fun, little blog post. Remote pre-auth file deletion in SolarWinds ARM allowed to achieve LPE on AD machines 🙃
Here is a great follow up blog post to my blog Remote Code Execution with Spring properties written by Elliot Ward: snyk.io/articles/rem...

Remote Code Execution with Spring Boot 3.4.0 Properties | Snyk
this article introduces two methods for leveraging Logback configuration to achieve Remote Code Execution (RCE) in Spring Boot applications. These techniques are effective on the latest version of Spr...
snyk.io
December 6, 2024 at 9:46 PM
Here is a great follow up blog post to my blog Remote Code Execution with Spring properties written by Elliot Ward: snyk.io/articles/rem...
Shit posting on wastebook and having my family all triggered is the glory I get on a Friyay!
December 6, 2024 at 2:38 AM
Shit posting on wastebook and having my family all triggered is the glory I get on a Friyay!



