@PentesterLab. Security engineer. Bugs are my own, not of my employer...
Not just alg=none: unsupported alg => empty signature, so forged token header.payload. passes.
Write-up + fix: pentesterlab.com/blog/cve-202...

So it’s the first day of ISO week-year 2026, even though the date is still 2025.
(Week 1 = week with the first Thursday)
So it’s the first day of ISO week-year 2026, even though the date is still 2025.
(Week 1 = week with the first Thursday)
For a limited time:
🔒 1 year of PRO for $146.52
🎓 Student special: 3 months PRO for $25.99
Hands-on labs. Real CVEs. Security code review training used by real AppSec & pentest teams.
⏰ Offer ends 2 Dec 2025, 23:59:59 UTC
👉 pentesterlab.com/pro

For a limited time:
🔒 1 year of PRO for $146.52
🎓 Student special: 3 months PRO for $25.99
Hands-on labs. Real CVEs. Security code review training used by real AppSec & pentest teams.
⏰ Offer ends 2 Dec 2025, 23:59:59 UTC
👉 pentesterlab.com/pro
Today I learned that you don't need to provide the full container id when you run docker exec...

Today I learned that you don't need to provide the full container id when you run docker exec...
Can someone tell me what I’m doing wrong?
#bugbountytips
Can someone tell me what I’m doing wrong?
#bugbountytips
Read more in our new blog post:
pentesterlab.com/blog/secure-...
What do you think?

Read more in our new blog post:
pentesterlab.com/blog/secure-...
What do you think?
In reality, a bit of hacking knowledge helps them spot vulnerabilities early and build stronger apps.
Discover why having devs with a 'hacker mindset' is a win for security:
pentesterlab.com/blog/why-dev...

In reality, a bit of hacking knowledge helps them spot vulnerabilities early and build stronger apps.
Discover why having devs with a 'hacker mindset' is a win for security:
pentesterlab.com/blog/why-dev...
"Security Code Review Porn"
It gives the wrong expectations about what real code review actually involves.
"Security Code Review Porn"
It gives the wrong expectations about what real code review actually involves.
🤝 blog.doyensec.com/2025/01/30/o...
☠️ www.feistyduck.com/newsletter/i...
📚 pathonproject.com/zb/?871f0933...
And as always, it’s in our blog: pentesterlab.com/blog/researc...
#PentesterLabWeekly
🤝 blog.doyensec.com/2025/01/30/o...
☠️ www.feistyduck.com/newsletter/i...
📚 pathonproject.com/zb/?871f0933...
And as always, it’s in our blog: pentesterlab.com/blog/researc...
#PentesterLabWeekly
@pentesterlab.com swag along too!
@pentesterlab.com swag along too!
Earn the Recon Badge with Pentesterlab and master: 🔍 Virtual Hosts 🌐 DNS Recon 🔒 TLS Recon ...and so much more!
Start your journey today
👉 pentesterlab.com/badges/recon

Earn the Recon Badge with Pentesterlab and master: 🔍 Virtual Hosts 🌐 DNS Recon 🔒 TLS Recon ...and so much more!
Start your journey today
👉 pentesterlab.com/badges/recon
Discover how meetups, conferences, and volunteering can open big career doors in InfoSec.
Read more: pentesterlab.com/blog/infosec...

Discover how meetups, conferences, and volunteering can open big career doors in InfoSec.
Read more: pentesterlab.com/blog/infosec...
www.wiz.io/blog/nuclei-...
I love this article so much! The content and the analysis are A+
I really like the 🚩 (very similar to pentesterlab.com/blog/another...)

www.wiz.io/blog/nuclei-...
I love this article so much! The content and the analysis are A+
I really like the 🚩 (very similar to pentesterlab.com/blog/another...)
pentesterlab.gumroad.com

pentesterlab.gumroad.com
pentesterlab.com/gift/xDzcB35... (3-month)
pentesterlab.com/gift/UBMtCsi... (3-month)
pentesterlab.com/gift/BWEYEme... (3-month)

pentesterlab.com/gift/xDzcB35... (3-month)
pentesterlab.com/gift/UBMtCsi... (3-month)
pentesterlab.com/gift/BWEYEme... (3-month)
pentesterlab.com/gift/v5kegJq... (3-month)
pentesterlab.com/gift/4VG6RYU... (3-month)
pentesterlab.com/gift/lsgfEwJ... (3-month)

pentesterlab.com/gift/v5kegJq... (3-month)
pentesterlab.com/gift/4VG6RYU... (3-month)
pentesterlab.com/gift/lsgfEwJ... (3-month)
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
https://nastystereo.com/security/cross-site-post-without-content-type.html
#BBRENewsletter85
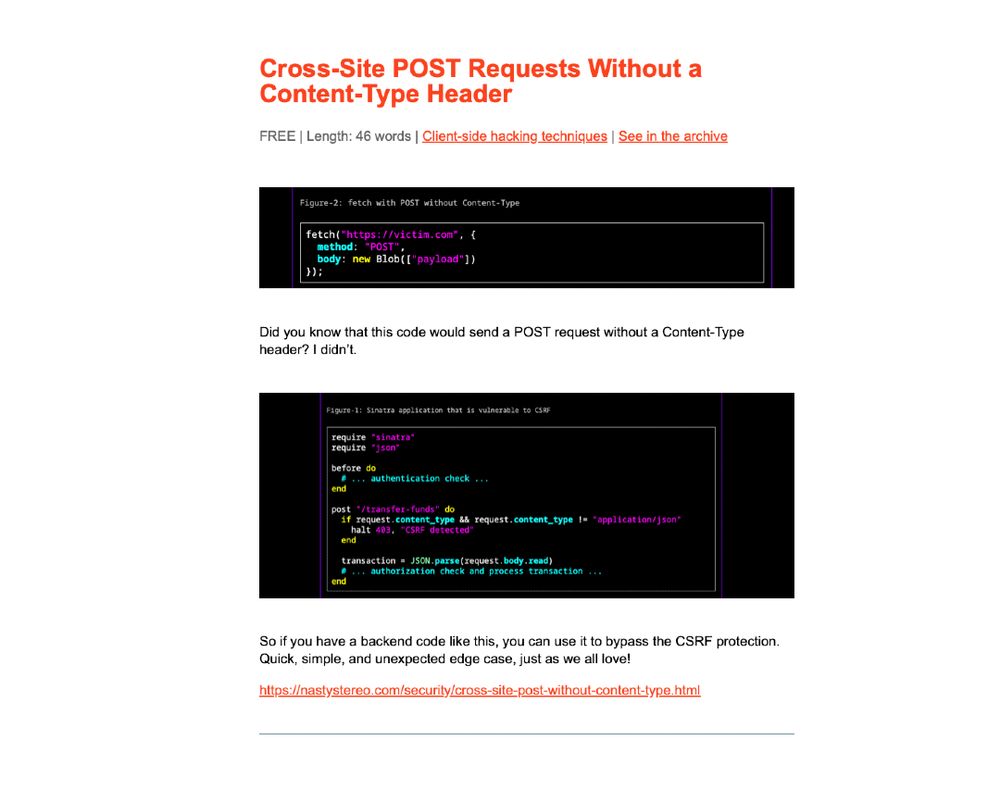
https://nastystereo.com/security/cross-site-post-without-content-type.html
#BBRENewsletter85
😱This lab show me that I was wrong, since several years, recommending to dev teams using a hash of the token as identifier in a revocation list.
🥰Now, I know the correct recommendation to provide.
#appsec #jwt
💡 How NOT to revoke JWTs: Learn how Base64 malleability can be used to bypass weak revocation mechanisms.
Ready to test your skills? 💥
👉 pentesterlab.com/exercises/ap...
#APISecurity #Pentesting

😱This lab show me that I was wrong, since several years, recommending to dev teams using a hash of the token as identifier in a revocation list.
🥰Now, I know the correct recommendation to provide.
#appsec #jwt
'Reading Between the Lines' challenges you to dig deeper:
1️⃣ What can I learn from this?
2️⃣ What patterns apply elsewhere?
3️⃣ Why didn’t I spot this?
The real breakthroughs come when you ask the right questions. 💡
👇

'Reading Between the Lines' challenges you to dig deeper:
1️⃣ What can I learn from this?
2️⃣ What patterns apply elsewhere?
3️⃣ Why didn’t I spot this?
The real breakthroughs come when you ask the right questions. 💡
👇




