
https://yeti-platform.io and more (github.com/tomchop)
views are my own • he/him • tomchop.me
https://www.ft.com/content/a0dfedd1-5255-4fa9-8ccc-1fe01de87ea6

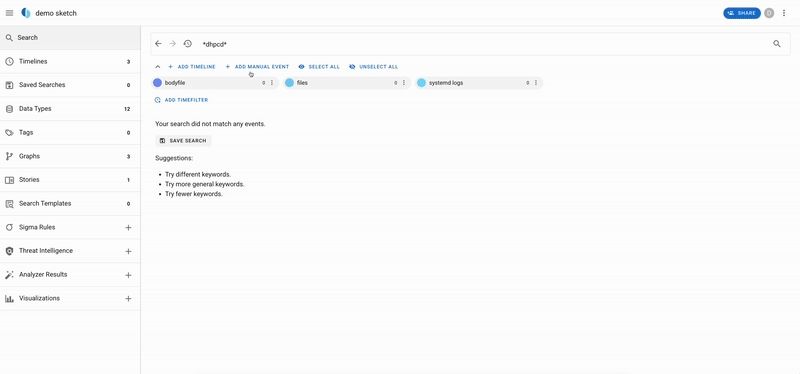
* github.com/tomchop/open...: Scan memory images using @volatilityfoundation.org plugins. Supports Yara rules
* github.com/tomchop/open... - Run Yara rules on a directory. Supports third-party systems like #Yeti!
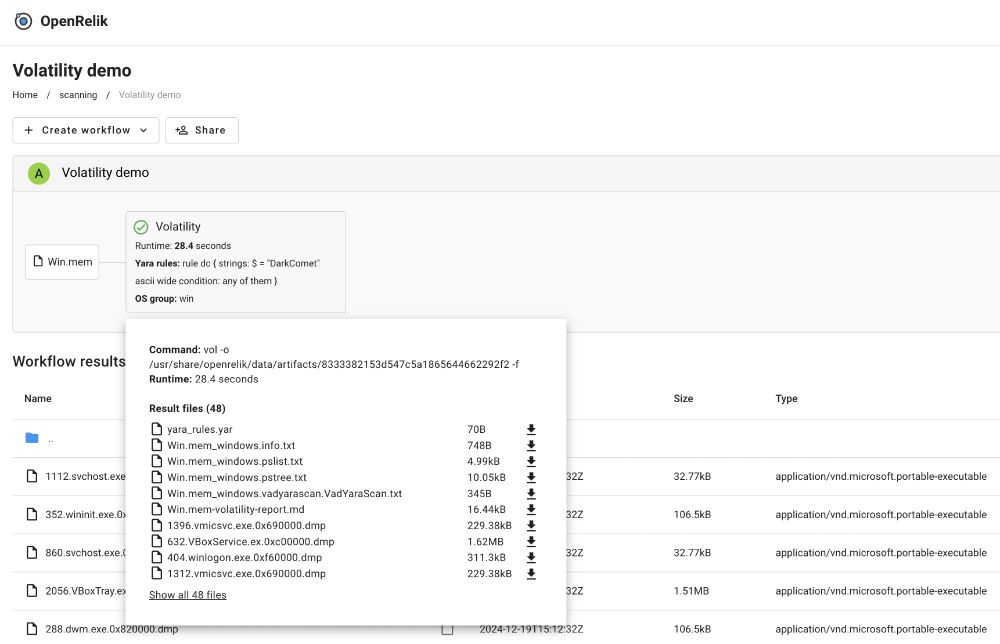
* github.com/tomchop/open...: Scan memory images using @volatilityfoundation.org plugins. Supports Yara rules
* github.com/tomchop/open... - Run Yara rules on a directory. Supports third-party systems like #Yeti!


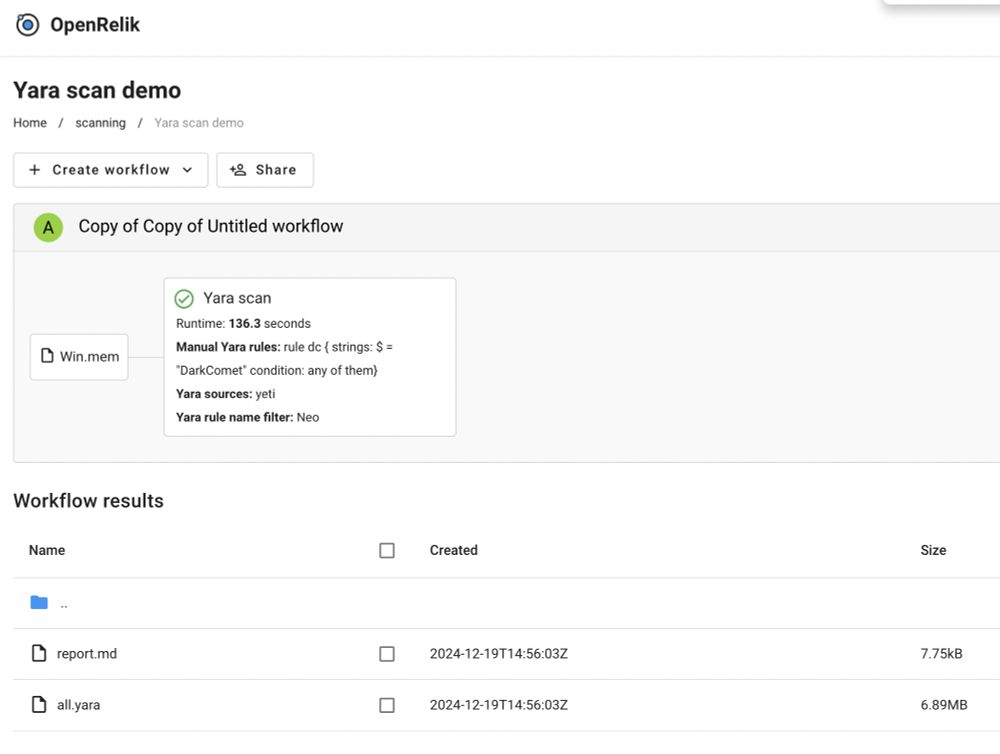
* github.com/tomchop/open...: Scan memory images using @volatilityfoundation.org plugins. Supports Yara rules
* github.com/tomchop/open... - Run Yara rules on a directory. Supports third-party systems like #Yeti!
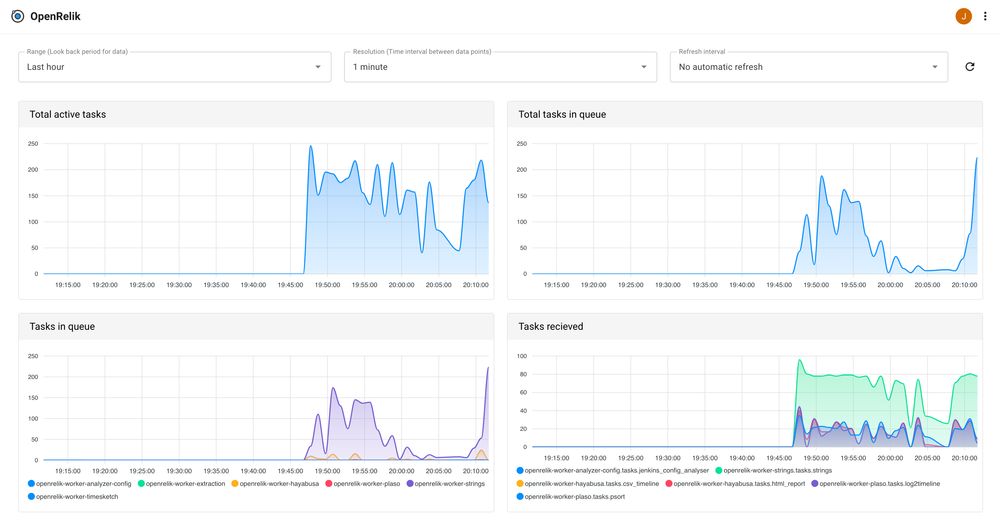
📝 openrelik.org/changelog/
🔗 discord.gg/hg652gktwX
#DFIR
📝 openrelik.org/changelog/
🔗 discord.gg/hg652gktwX
#DFIR
Don't share any information Ron Swanson wouldn't share


Kudos to @volexity.com for going into so much detail on this novel network attack technique.
www.volexity.com/blog/2024/11...

Kudos to @volexity.com for going into so much detail on this novel network attack technique.
www.volexity.com/blog/2024/11...
www.volexity.com/blog/2024/11...

www.volexity.com/blog/2024/11...
👉 it enables some very cool integrations, like auto curated feeds and starter packs for contributors and tech
👉 it enables some very cool integrations, like auto curated feeds and starter packs for contributors and tech
pivotcon.org
#CTI #ThreatResearch #ThreatIntel
Please read carefully the whole 🧵 for the rules about invite -> registration (1/5)

"plaso I choose you!!"
"plaso I choose you!!"
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
Looks like this got caught by chance. Wonder how long it would have taken otherwise.
www.openwall.com/lists/oss-se...
It has everything: malicious upstream, masterful obfuscation, detection due to performance degradation, inclusion in OpenSSH via distro patches for systemd support…
Now I’m curious what it does in RSA_public_decrypt
The hooked RSA_public_decrypt verifies a signature on the server's host key by a fixed Ed448 key, and then passes a payload to system().
It's RCE, not auth bypass, and gated/unreplayable.
Website: yeti-platform.io
Release: github.com/yeti-platform/yeti
mini-🧵👇🏻
#DFIR #infosec #CTI #cybersec
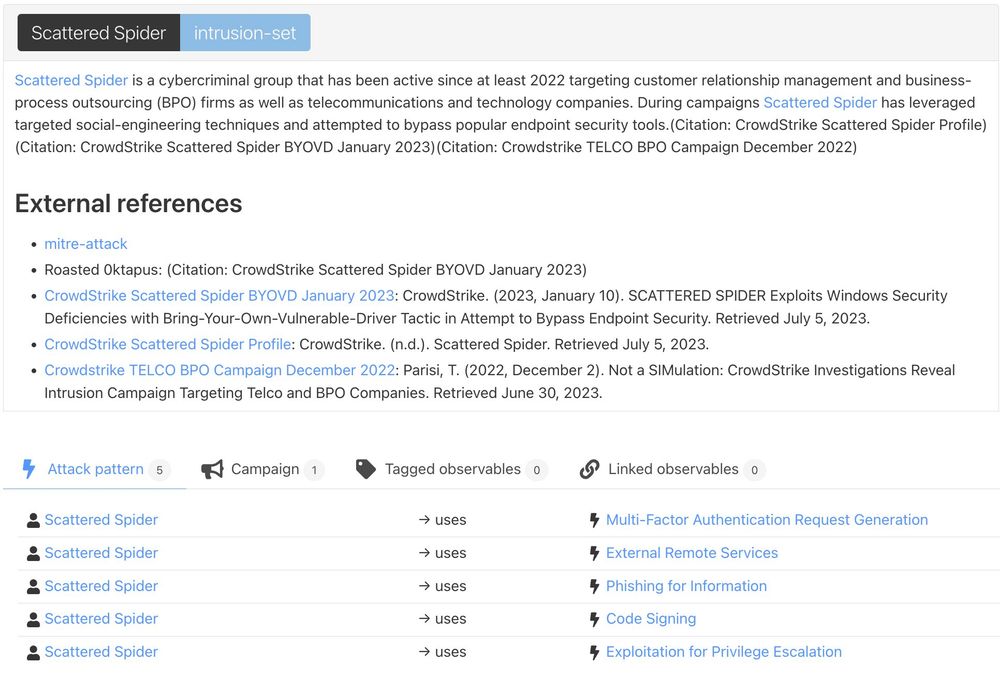
Website: yeti-platform.io
Release: github.com/yeti-platform/yeti
mini-🧵👇🏻
#DFIR #infosec #CTI #cybersec
We're already getting lots of FRs, which we'll do our best to implement before our official release EOM.
Hope I made @Sebdraven proud 🥹 #dfir #infosec
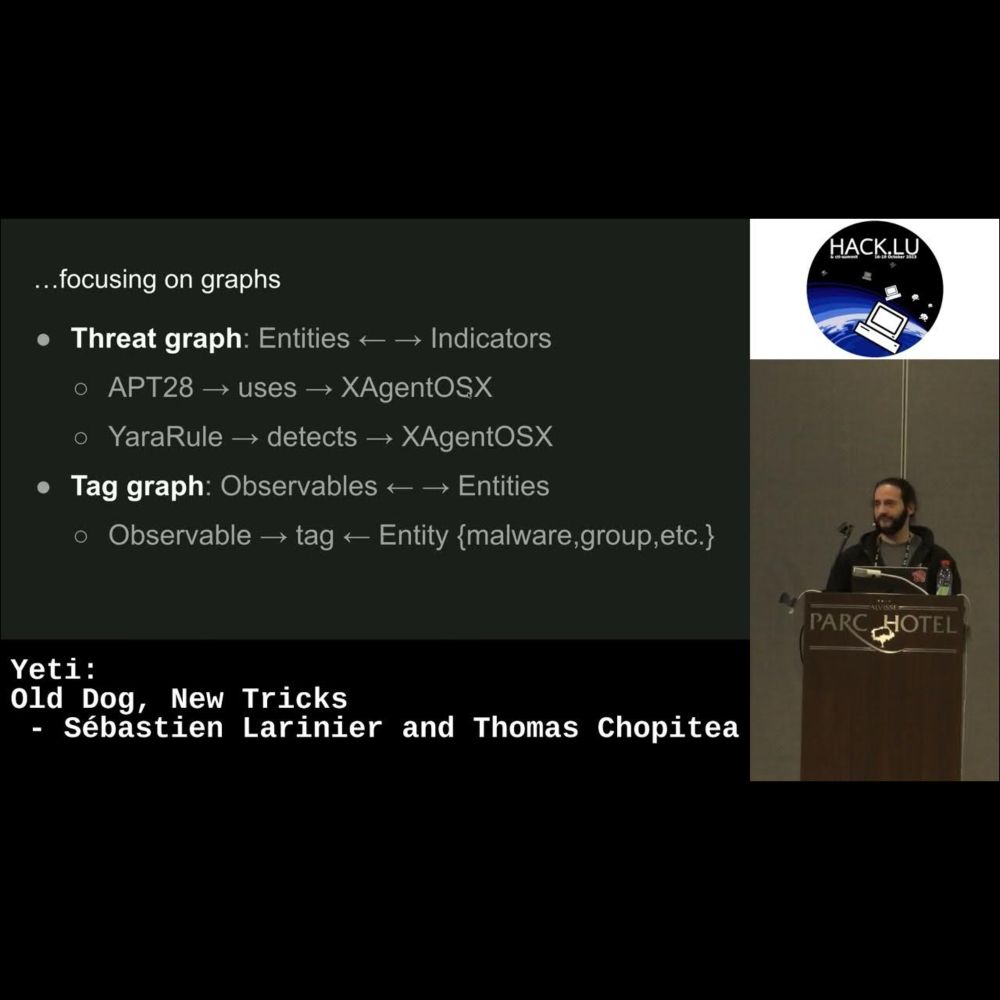
It's going to be fun to talk about this project that has been on my todo list for 10+ years! 😅 #DFIR #infosec #CTI

It's going to be fun to talk about this project that has been on my todo list for 10+ years! 😅 #DFIR #infosec #CTI
The idea came from the will to organize investigative approaches to similar cases to increase consistency across response efforts. #dfir #infosec
The idea came from the will to organize investigative approaches to similar cases to increase consistency across response efforts. #dfir #infosec
https://blog.virustotal.com/2023/07/actionable-threat-intel-iv-yara-beyond.html
https://blog.virustotal.com/2023/07/actionable-threat-intel-iv-yara-beyond.html





