www.404media.co/anyone-can-p...
www.404media.co/anyone-can-p...

PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
Great first-person interface.
Web | Free | 10 min
sheepolution.itch.io/vox-regis
Great first-person interface.
Web | Free | 10 min
sheepolution.itch.io/vox-regis
![Screenshot of Python code from the iPython interpreter:
class Person:
name: str
age: int
def __init__(self, name, age):
self.name = name
self.age = age
def __str__(self):
return f"Person(name='{self.name}', age={self.age})"
def __eq__(self, other):
prompt = f"Is:\n\n{self}\n\nbasically equal to:\n\n{other}\n\n?\n\nJust answer 'Yes' or 'No'"
response = client.messages.create(
model='claude-3-5-sonnet-latest',
messages=[{'role': 'user', 'content': prompt}],
max_tokens=16
)
return 'yes' in response.content[0].text.lower()
>>> Person('Brendan D-G', 41) == "Brendan Dolan-Gavitt, who is 41 years old"
True
>>> Person('Brendan D-G', 41) == "John Smith, a 25 year-old"
False](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:r5q2jrgxqoa2ovw6lz667it7/bafkreiboqhd6k7x72zl6cmveei55ldib425xu4efth5ekjf4ibtpqcexoa@jpeg)




nastystereo.com/security/rai...
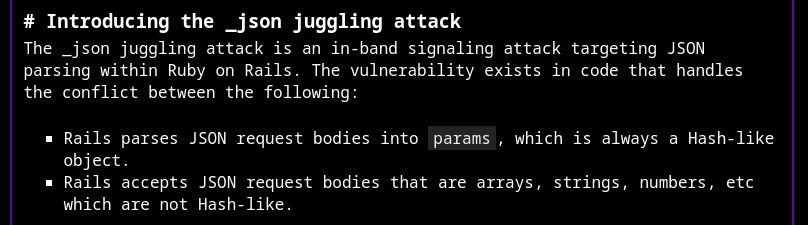
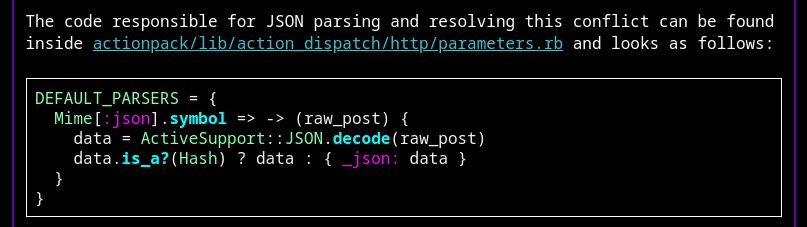
nastystereo.com/security/rai...
Detection:
* https://github.com/exein-io/pulsar - IoT security framework powered by eBPF
Exploitation:
* https://github.com/danielmiessler/SecLists - lists for fuzzing
* https://github.com/swisskyrepo/PayloadsAllTheThings - more payloads for apps
* […]
Detection:
* https://github.com/exein-io/pulsar - IoT security framework powered by eBPF
Exploitation:
* https://github.com/danielmiessler/SecLists - lists for fuzzing
* https://github.com/swisskyrepo/PayloadsAllTheThings - more payloads for apps
* […]

x.com/icesfont2/st...

x.com/icesfont2/st...
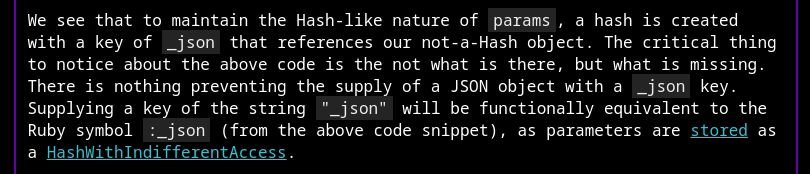
portswigger.net/research/byp...

Violent crackdowns are happening in Tbilisi, Georgia. We are fighting for our lives here.
Please, please, please help us spread the word.
Violent crackdowns are happening in Tbilisi, Georgia. We are fighting for our lives here.
Please, please, please help us spread the word.
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Join the #OWASP community today & start building secure software! #securecodingtraining #threatmodeling

Join the #OWASP community today & start building secure software! #securecodingtraining #threatmodeling
Exploitation:
* https://github.com/BishopFox/BrokenHill - a productionized greedy coordinate gradient (GCG) attack tool for large language models (LLMs)
* https://github.com/DaddyBigFish/enumx - the tool enumx is a framework built for Kali Linux that uses a […]
Exploitation:
* https://github.com/BishopFox/BrokenHill - a productionized greedy coordinate gradient (GCG) attack tool for large language models (LLMs)
* https://github.com/DaddyBigFish/enumx - the tool enumx is a framework built for Kali Linux that uses a […]
It was also cool to collab w/ him on the second chall 🤜🏿🤛🏻
blig.one/2024/11/29/f...
It was also cool to collab w/ him on the second chall 🤜🏿🤛🏻
blig.one/2024/11/29/f...
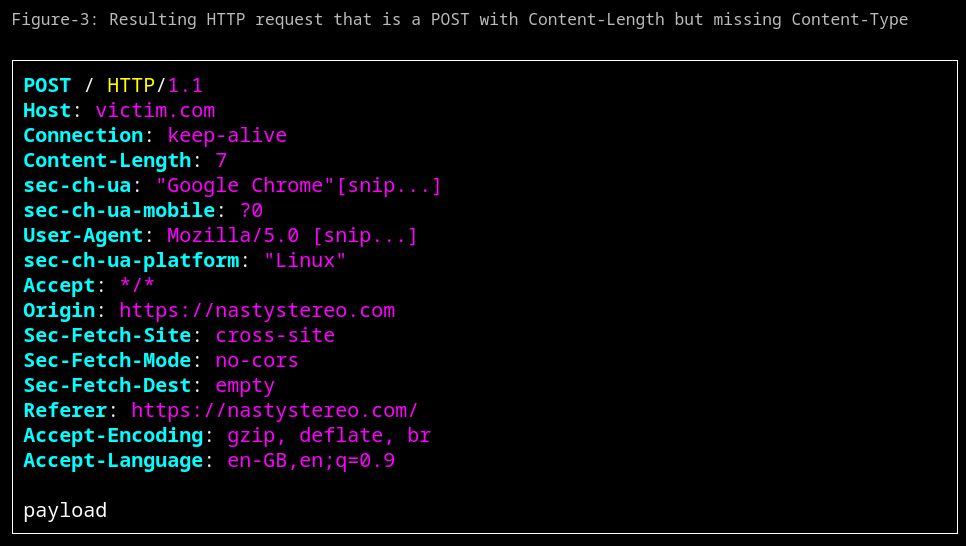
Read how to send a cross-site POST without including a Content-Type header (without CORS). It even works with navigator.sendBeacon