𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
@netresec.com
Experts in Network Forensics and Network Security Monitoring. Creators of #NetworkMiner, #CapLoader, PacketCache, #PolarProxy and RawCap.
Website: https://www.netresec.com/
Mastodon: @[email protected]
Website: https://www.netresec.com/
Mastodon: @[email protected]
Reposted by 𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
I love the idea of calculating the decay rate of an IOC. It's not always strictly mathematical, because it also relies on threat actors' choices about how they use the IOCs, but as an estimate and for decision making, this seems promising.
Also, I really like @netresec.com's ASCII art Pyramid. 😀
Also, I really like @netresec.com's ASCII art Pyramid. 😀
Monitoring for too many old indicators not only costs money, it can even inhibit detection of real intrusions.
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
netresec.com?b=25Be9dd
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
netresec.com?b=25Be9dd

Optimizing IOC Retention Time
Are you importing indicators of compromise (IOC) in the form of domain names and IP addresses into your SIEM, NDR or IDS? If so, have you considered for how long you should keep looking for those IOCs...
netresec.com
November 6, 2025 at 1:23 PM
I love the idea of calculating the decay rate of an IOC. It's not always strictly mathematical, because it also relies on threat actors' choices about how they use the IOCs, but as an estimate and for decision making, this seems promising.
Also, I really like @netresec.com's ASCII art Pyramid. 😀
Also, I really like @netresec.com's ASCII art Pyramid. 😀
Monitoring for too many old indicators not only costs money, it can even inhibit detection of real intrusions.
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
netresec.com?b=25Be9dd
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
netresec.com?b=25Be9dd

Optimizing IOC Retention Time
Are you importing indicators of compromise (IOC) in the form of domain names and IP addresses into your SIEM, NDR or IDS? If so, have you considered for how long you should keep looking for those IOCs...
netresec.com
November 6, 2025 at 1:08 PM
Monitoring for too many old indicators not only costs money, it can even inhibit detection of real intrusions.
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
netresec.com?b=25Be9dd
📆 Include "last seen" date when publishing IOCs
❌ Prune old IOCs
📜 Prioritize long lived IOCs over short lived ones
netresec.com?b=25Be9dd
Reposted by 𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
🚨 The #DFRWSEU 2026 paper submission deadline has been extended to 10th October 2025 🎉
Submit your paper showcasing cutting-edge digital forensics research.
📤 Submit here: buff.ly/BN8Jlnb
ℹ️ Conference details: buff.ly/KOw9Xpr
#DFRWS #DigitalForensics #CFP
Submit your paper showcasing cutting-edge digital forensics research.
📤 Submit here: buff.ly/BN8Jlnb
ℹ️ Conference details: buff.ly/KOw9Xpr
#DFRWS #DigitalForensics #CFP

September 24, 2025 at 3:15 PM
🚨 The #DFRWSEU 2026 paper submission deadline has been extended to 10th October 2025 🎉
Submit your paper showcasing cutting-edge digital forensics research.
📤 Submit here: buff.ly/BN8Jlnb
ℹ️ Conference details: buff.ly/KOw9Xpr
#DFRWS #DigitalForensics #CFP
Submit your paper showcasing cutting-edge digital forensics research.
📤 Submit here: buff.ly/BN8Jlnb
ℹ️ Conference details: buff.ly/KOw9Xpr
#DFRWS #DigitalForensics #CFP
Gh0stKCP is a C2 transport protocol based on KCP. It has been used by malware families such as #PseudoManuscrypt and #ValleyRAT.
netresec.com?b=259a5af
netresec.com?b=259a5af

Gh0stKCP Protocol
Gh0stKCP is a command-and-control (C2) transport protocol based on KCP. It has been used by malware families such as PseudoManuscrypt and ValleyRAT/Winos4.0. @Jane_0sint recently tweeted about ValleyR...
netresec.com
September 24, 2025 at 12:22 PM
Gh0stKCP is a C2 transport protocol based on KCP. It has been used by malware families such as #PseudoManuscrypt and #ValleyRAT.
netresec.com?b=259a5af
netresec.com?b=259a5af
Video: Detecting #XenoRAT C2 connections using example traffic from known malware sample.
🔥 e0b465d3bd1ec5e95aee016951d55640
🔥 5ab23ac79ede02166d6f5013d89738f9
📡 Huy1612-24727.portmap[.]io:24727
📡 193.161.193.99:24727
📡 147.185.221.30:54661
netresec.com?b=258f641
🔥 e0b465d3bd1ec5e95aee016951d55640
🔥 5ab23ac79ede02166d6f5013d89738f9
📡 Huy1612-24727.portmap[.]io:24727
📡 193.161.193.99:24727
📡 147.185.221.30:54661
netresec.com?b=258f641

Define Protocol from Traffic (XenoRAT)
This video shows how to define a protocol in CapLoader just by providing examples of what the protocol looks like. CapLoader can then identify that protocol in other traffic, regardless of IP address ...
netresec.com
August 21, 2025 at 1:22 PM
Video: Detecting #XenoRAT C2 connections using example traffic from known malware sample.
🔥 e0b465d3bd1ec5e95aee016951d55640
🔥 5ab23ac79ede02166d6f5013d89738f9
📡 Huy1612-24727.portmap[.]io:24727
📡 193.161.193.99:24727
📡 147.185.221.30:54661
netresec.com?b=258f641
🔥 e0b465d3bd1ec5e95aee016951d55640
🔥 5ab23ac79ede02166d6f5013d89738f9
📡 Huy1612-24727.portmap[.]io:24727
📡 193.161.193.99:24727
📡 147.185.221.30:54661
netresec.com?b=258f641
How to identify #PureRAT (aka #ResolverRAT):
⛳️ C2 port is often 56001, 56002 or 56003
🔢 Bot sends 04 00 00 00, then TLS handshake
🔑 Client and server run TLS 1.0
🖊️ X.509 cert is self signed
📅 X.509 cert expires 9999-12-31
netresec.com?b=2589522
⛳️ C2 port is often 56001, 56002 or 56003
🔢 Bot sends 04 00 00 00, then TLS handshake
🔑 Client and server run TLS 1.0
🖊️ X.509 cert is self signed
📅 X.509 cert expires 9999-12-31
netresec.com?b=2589522

PureRAT = ResolverRAT = PureHVNC
PureRAT is a Remote Access Trojan, which can be used by an attacker to remotely control someone else's PC. PureRAT provides the following features to an attacker: See the victims user interfaceInt...
netresec.com
August 12, 2025 at 6:20 PM
How to identify #PureRAT (aka #ResolverRAT):
⛳️ C2 port is often 56001, 56002 or 56003
🔢 Bot sends 04 00 00 00, then TLS handshake
🔑 Client and server run TLS 1.0
🖊️ X.509 cert is self signed
📅 X.509 cert expires 9999-12-31
netresec.com?b=2589522
⛳️ C2 port is often 56001, 56002 or 56003
🔢 Bot sends 04 00 00 00, then TLS handshake
🔑 Client and server run TLS 1.0
🖊️ X.509 cert is self signed
📅 X.509 cert expires 9999-12-31
netresec.com?b=2589522
💧 Dropper connects to legitimate website
📄 Fake PDF is downloaded over HTTPS
💾 Fake PDF is decrypted to a #PureLogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
netresec.com?b=257eead
📄 Fake PDF is downloaded over HTTPS
💾 Fake PDF is decrypted to a #PureLogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
netresec.com?b=257eead
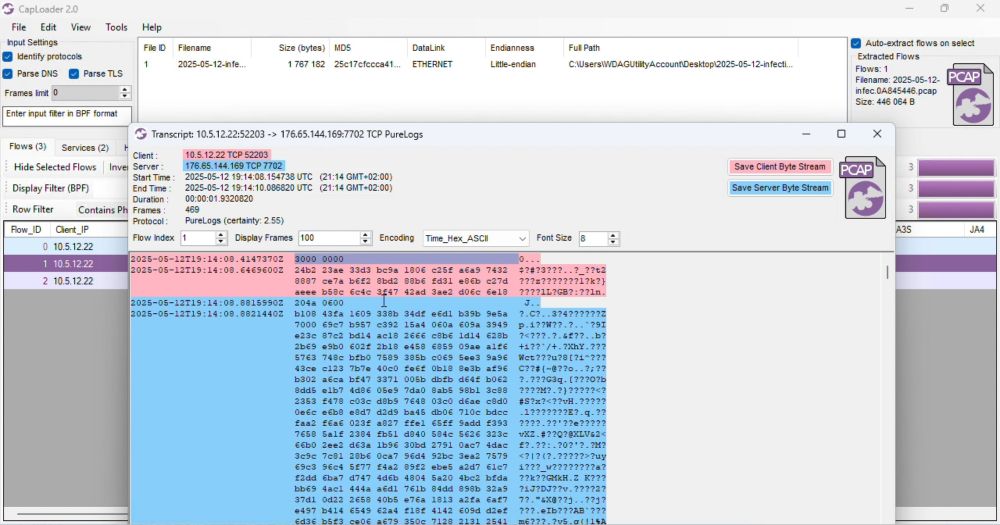
PureLogs Forensics
I analyzed some PureLogs malware infections this morning and found some interesting behavior and artifacts that I want to share. PureLogs infections sometimes start with a dropper/downloader that retr...
netresec.com
July 2, 2025 at 12:15 PM
💧 Dropper connects to legitimate website
📄 Fake PDF is downloaded over HTTPS
💾 Fake PDF is decrypted to a #PureLogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
netresec.com?b=257eead
📄 Fake PDF is downloaded over HTTPS
💾 Fake PDF is decrypted to a #PureLogs DLL
⚙️ InstallUtil.exe or RegAsm.exe is started
💉 PureLogs DLL is injected into the running process
👾 PureLogs connects to C2 server
netresec.com?b=257eead
CapLoader 2.0.1 Released
⚠️ IP lookup alert
🔎 Better protocol identification
🐛 Bug fixes
netresec.com?b=2571527
⚠️ IP lookup alert
🔎 Better protocol identification
🐛 Bug fixes
netresec.com?b=2571527
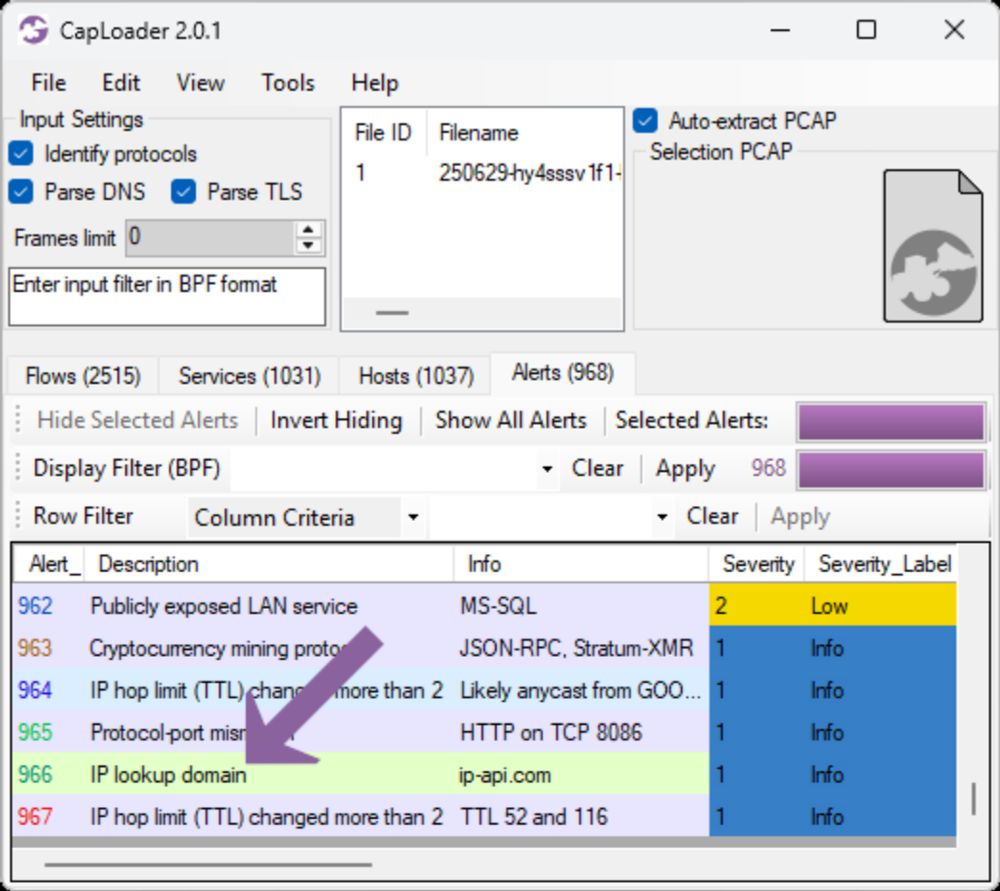
CapLoader 2.0.1 Released
This update resolves several minor bugs, but also brings better protocol identification and a new IP lookup alert to CapLoader. Alert for IP lookup using ip-api.com in PCAP from tria.ge Transcript of ...
netresec.com
July 1, 2025 at 1:58 PM
CapLoader 2.0.1 Released
⚠️ IP lookup alert
🔎 Better protocol identification
🐛 Bug fixes
netresec.com?b=2571527
⚠️ IP lookup alert
🔎 Better protocol identification
🐛 Bug fixes
netresec.com?b=2571527
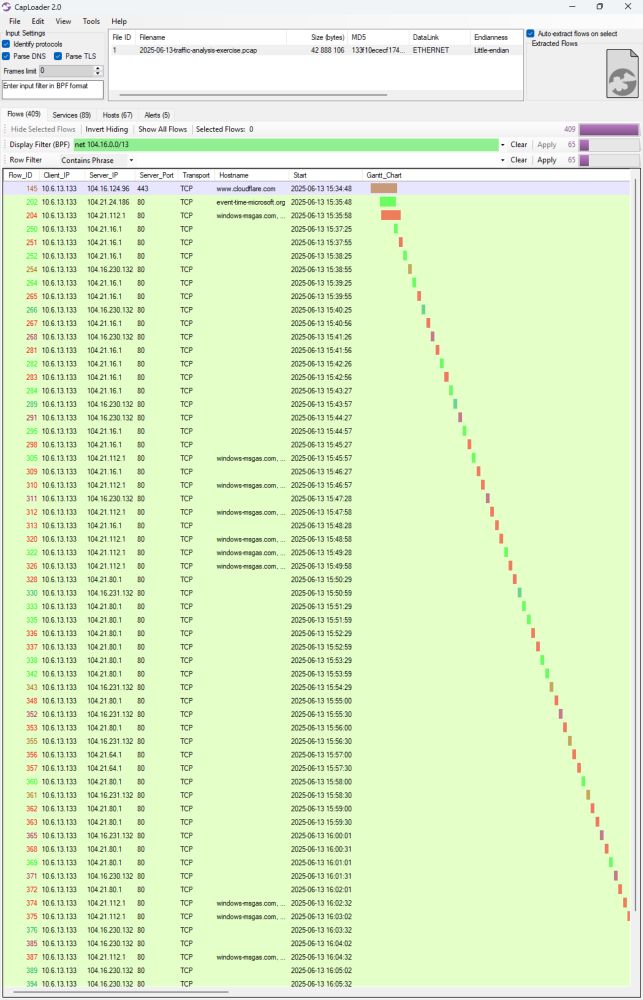
Does anyone know what malware this is? C2 is on 104.16.0.0/13 (CloudFlare).
C2 domains:
🔥 event-time-microsoft[.]org
🔥 windows-msgas[.]com
🔥 event-datamicrosoft[.]live
🔥 eventdata-microsoft[.]live
PCAP from @malware-traffic-analysis.net
infosec.exchange/@netresec/11...
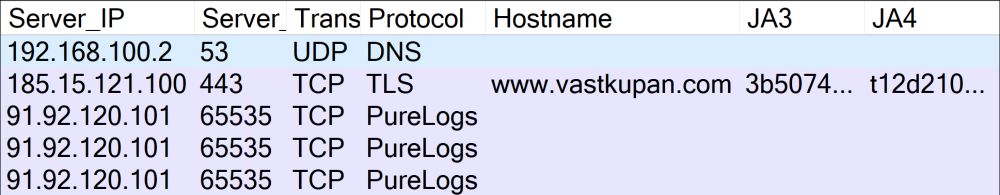
C2 domains:
🔥 event-time-microsoft[.]org
🔥 windows-msgas[.]com
🔥 event-datamicrosoft[.]live
🔥 eventdata-microsoft[.]live
PCAP from @malware-traffic-analysis.net
infosec.exchange/@netresec/11...
𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲 (@[email protected])
Attached: 1 image
@malware_traffic There's some unknown but interesting C2 traffic going on to net 104.16.0.0/13 (on CloudFlare). An HTTP POST is sent every 30 seconds (see Gantt chart) with gz compr...
infosec.exchange
June 24, 2025 at 4:03 PM
Does anyone know what malware this is? C2 is on 104.16.0.0/13 (CloudFlare).
C2 domains:
🔥 event-time-microsoft[.]org
🔥 windows-msgas[.]com
🔥 event-datamicrosoft[.]live
🔥 eventdata-microsoft[.]live
PCAP from @malware-traffic-analysis.net
infosec.exchange/@netresec/11...
C2 domains:
🔥 event-time-microsoft[.]org
🔥 windows-msgas[.]com
🔥 event-datamicrosoft[.]live
🔥 eventdata-microsoft[.]live
PCAP from @malware-traffic-analysis.net
infosec.exchange/@netresec/11...
CapLoader 2.0 released today!
🔎 Identifies over 250 protocols in #PCAP
🎨 Define protocols from example traffic
🇶 Extracts JA3, JA4 and SNI from QUIC
💻 10x faster user interface
netresec.com?b=256dbbc
🔎 Identifies over 250 protocols in #PCAP
🎨 Define protocols from example traffic
🇶 Extracts JA3, JA4 and SNI from QUIC
💻 10x faster user interface
netresec.com?b=256dbbc

CapLoader 2.0 Released
I am thrilled to announce the release of CapLoader 2.0 today! This major update includes a lot of new features, such as a QUIC parser, alerts for threat hunting and a feature that allow users to defin...
netresec.com
June 2, 2025 at 3:56 PM
CapLoader 2.0 released today!
🔎 Identifies over 250 protocols in #PCAP
🎨 Define protocols from example traffic
🇶 Extracts JA3, JA4 and SNI from QUIC
💻 10x faster user interface
netresec.com?b=256dbbc
🔎 Identifies over 250 protocols in #PCAP
🎨 Define protocols from example traffic
🇶 Extracts JA3, JA4 and SNI from QUIC
💻 10x faster user interface
netresec.com?b=256dbbc
Thank you CISA, @ncsc.gov.uk, @bsi.bund.de et al. for publishing the advisory on Russian GRU Targeting Western Logistics Entities and Technology Companies. This list of mocking services is great for threat hunting!
www.cisa.gov/news-events/...
www.cisa.gov/news-events/...
![Many organizations may not need to allow outgoing traffic to hosting and API mocking services, which are frequently used by GRU unit 26165. Organizations should consider alerting on or blocking the following services, with exceptions allowlisted for legitimate activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for each sub-domain requested by users on a network, such as in DNS or firewall logs, may enable system administrators to identify new targeting and victims.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:2qrgzoyfwkguclususquvdz2/bafkreidsg3ldjaxglxhetka5xmbm2gc7xlthvuyoek2vmeo6ny5tsdi3di@jpeg)
May 22, 2025 at 5:16 PM
Thank you CISA, @ncsc.gov.uk, @bsi.bund.de et al. for publishing the advisory on Russian GRU Targeting Western Logistics Entities and Technology Companies. This list of mocking services is great for threat hunting!
www.cisa.gov/news-events/...
www.cisa.gov/news-events/...
Comparison of tools that extract files from #PCAP
📖 #Chaosreader
⛏️ #NetworkMiner
🐿️ #Suricata
🌊 #tcpflow
🦈 #Wireshark
👁️ #Zeek
netresec.com?b=255329f
📖 #Chaosreader
⛏️ #NetworkMiner
🐿️ #Suricata
🌊 #tcpflow
🦈 #Wireshark
👁️ #Zeek
netresec.com?b=255329f

Comparison of tools that extract files from PCAP
One of the premier features in NetworkMiner is the ability to extract files from captured network traffic in PCAP files. NetworkMiner reassembles the file contents by parsing protocols that are used t...
netresec.com
May 5, 2025 at 4:16 PM
Comparison of tools that extract files from #PCAP
📖 #Chaosreader
⛏️ #NetworkMiner
🐿️ #Suricata
🌊 #tcpflow
🦈 #Wireshark
👁️ #Zeek
netresec.com?b=255329f
📖 #Chaosreader
⛏️ #NetworkMiner
🐿️ #Suricata
🌊 #tcpflow
🦈 #Wireshark
👁️ #Zeek
netresec.com?b=255329f
Did you know that NetworkMiner parses the #njRAT protocol? The following artefacts are extracted from njRAT C2 traffic:
🖥️ Screenshots of victim computer
📁 Transferred files
👾 Commands from C2 server
🤖 Replies from bot
🔑 Stolen credentials/passwords
⌨️ Keylog data
netresec.com?b=2541a39
🖥️ Screenshots of victim computer
📁 Transferred files
👾 Commands from C2 server
🤖 Replies from bot
🔑 Stolen credentials/passwords
⌨️ Keylog data
netresec.com?b=2541a39

Decoding njRAT traffic with NetworkMiner
I investigate network traffic from a Triage sandbox execution of njRAT in this video. The analysis is performed using NetworkMiner in Linux (REMnux to be specific). About njRAT / Bladabindi njRAT is a...
netresec.com
April 28, 2025 at 6:28 AM
Did you know that NetworkMiner parses the #njRAT protocol? The following artefacts are extracted from njRAT C2 traffic:
🖥️ Screenshots of victim computer
📁 Transferred files
👾 Commands from C2 server
🤖 Replies from bot
🔑 Stolen credentials/passwords
⌨️ Keylog data
netresec.com?b=2541a39
🖥️ Screenshots of victim computer
📁 Transferred files
👾 Commands from C2 server
🤖 Replies from bot
🔑 Stolen credentials/passwords
⌨️ Keylog data
netresec.com?b=2541a39
New instructions for installing NetworkMiner on Linux
netresec.com?b=2542784
netresec.com?b=2542784

How to Install NetworkMiner in Linux
This guide shows how to install the latest version of NetworkMiner in Linux. To install an older NetworkMiner release, prior to version 3.0, please see our legacy NetworkMiner in Linux guide. STEP 1: ...
netresec.com
April 10, 2025 at 7:56 AM
New instructions for installing NetworkMiner on Linux
netresec.com?b=2542784
netresec.com?b=2542784
NetworkMiner 3.0 Released!
🔐 QUIC
🏭 CIP (EtherNet/IP)
🏭 UMAS (over Mobdus)
👾 Remcos RAT
🔍 Improved OS fingerprinting
🐧 Better Linux integration
netresec.com?b=254caa9
🔐 QUIC
🏭 CIP (EtherNet/IP)
🏭 UMAS (over Mobdus)
👾 Remcos RAT
🔍 Improved OS fingerprinting
🐧 Better Linux integration
netresec.com?b=254caa9

NetworkMiner 3.0 Released
I am very proud to announce the release of NetworkMiner 3.0 today! This version brings several new protocols as well as user interface improvements to NetworkMiner. We have also made significant chang...
netresec.com
April 4, 2025 at 11:22 AM
NetworkMiner 3.0 Released!
🔐 QUIC
🏭 CIP (EtherNet/IP)
🏭 UMAS (over Mobdus)
👾 Remcos RAT
🔍 Improved OS fingerprinting
🐧 Better Linux integration
netresec.com?b=254caa9
🔐 QUIC
🏭 CIP (EtherNet/IP)
🏭 UMAS (over Mobdus)
👾 Remcos RAT
🔍 Improved OS fingerprinting
🐧 Better Linux integration
netresec.com?b=254caa9
How to set #PCAP as default savefile format in #Wireshark
📝 Edit
📃 Preferences
💡 Advanced
✍️ Change capture.pcap_ng to FALSE
netresec.com?b=2523d40
📝 Edit
📃 Preferences
💡 Advanced
✍️ Change capture.pcap_ng to FALSE
netresec.com?b=2523d40
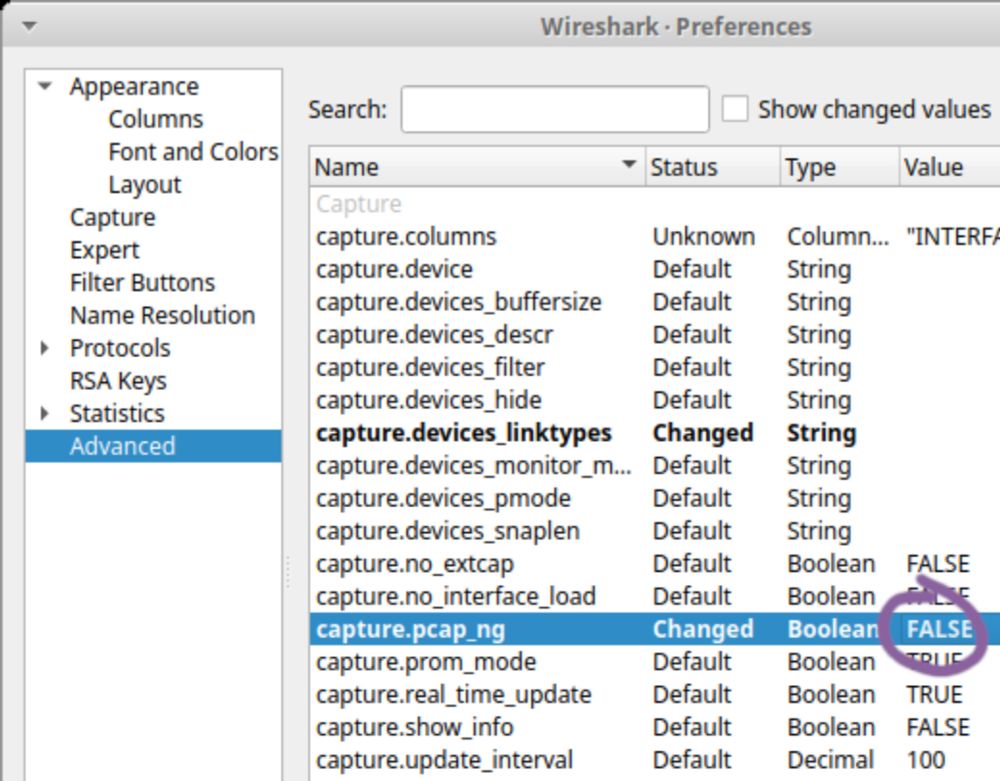
How to set PCAP as default save file format in Wireshark
Did you know that there is a setting in Wireshark for changing the default save file format from pcapng to pcap? In Wireshark, click Edit, Preferences. Then select Advanced and look for the capture.pc...
netresec.com
February 25, 2025 at 10:49 AM
How to set #PCAP as default savefile format in #Wireshark
📝 Edit
📃 Preferences
💡 Advanced
✍️ Change capture.pcap_ng to FALSE
netresec.com?b=2523d40
📝 Edit
📃 Preferences
💡 Advanced
✍️ Change capture.pcap_ng to FALSE
netresec.com?b=2523d40
Here's a feature request to have #Wireshark bring back PCAP as the default savefile format instead of pcapng.
gitlab.com/wireshark/wi...
gitlab.com/wireshark/wi...
Use pcap as default savefile format instead of pcapng (#20388) · Issues · Wireshark Foundation / Wireshark · GitLab
Description The pcapng file format provides some useful features, such as allowing multiple link layer types to be defined in a...
gitlab.com
February 13, 2025 at 9:03 AM
Here's a feature request to have #Wireshark bring back PCAP as the default savefile format instead of pcapng.
gitlab.com/wireshark/wi...
gitlab.com/wireshark/wi...
PolarProxy 1.0.1 Released
🆔 More #JA4
🔂 Fail-open on #TLS errors
⏩ Better performance
netresec.com?b=2523c96
🆔 More #JA4
🔂 Fail-open on #TLS errors
⏩ Better performance
netresec.com?b=2523c96

PolarProxy 1.0.1 Released
The new release of PolarProxy generates JA4 fingerprints and enables ruleset to match on specific decryption errors, for example to enable fail-open in case the TLS traffic cannot be decrypted and ins...
netresec.com
February 7, 2025 at 10:22 AM
PolarProxy 1.0.1 Released
🆔 More #JA4
🔂 Fail-open on #TLS errors
⏩ Better performance
netresec.com?b=2523c96
🆔 More #JA4
🔂 Fail-open on #TLS errors
⏩ Better performance
netresec.com?b=2523c96
This is an interesting Kerberos relay attack! It leverages LLMNR spoofing/poisoning to trick victims to connect to the attacker's machine and authenticate using Kerberos.
January 29, 2025 at 3:09 PM
This is an interesting Kerberos relay attack! It leverages LLMNR spoofing/poisoning to trick victims to connect to the attacker's machine and authenticate using Kerberos.
A TLS firewall is similar to a DNS firewall, except it blocks connections to unwanted websites even if the DNS traffic is encrypted.
netresec.com?b=2515cf0
netresec.com?b=2515cf0
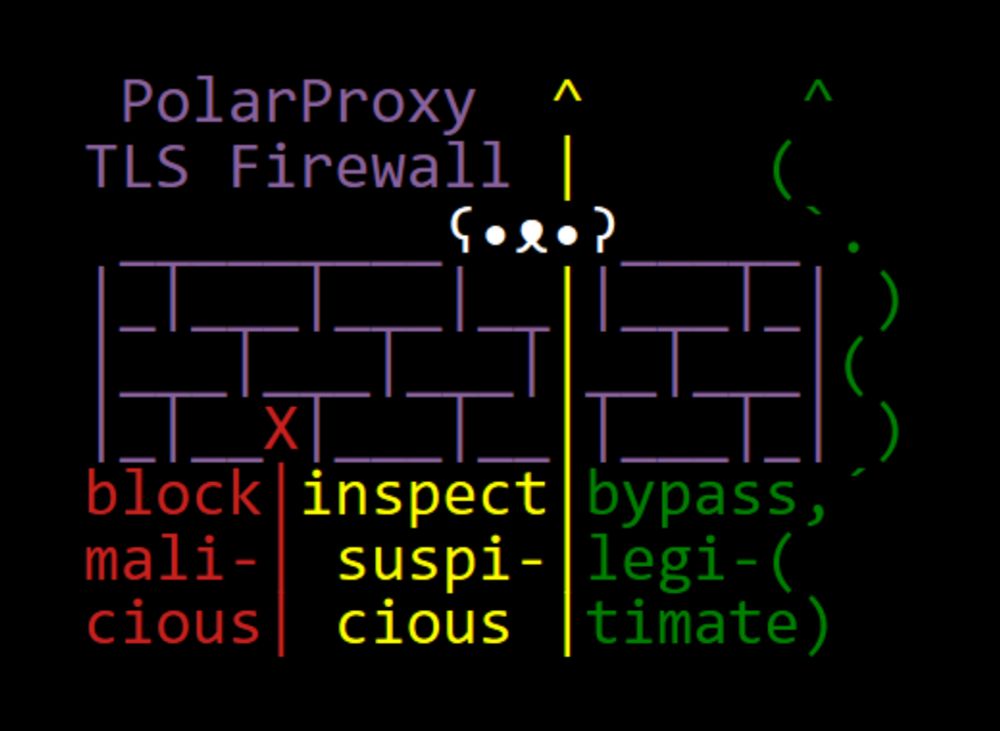
Blocking Malicious sites with a TLS Firewall
Over 90 percent of all web traffic is encrypted nowadays, which is great of course. However, as HTTP and DNS traffic gets encrypted, defenders have a more difficult time blocking malicious network tra...
netresec.com
January 27, 2025 at 11:04 AM
A TLS firewall is similar to a DNS firewall, except it blocks connections to unwanted websites even if the DNS traffic is encrypted.
netresec.com?b=2515cf0
netresec.com?b=2515cf0
We’ve now scheduled our next Network Forensics for Incident Response training
📅 Dates: May 12-15, 2025
🕑 Duration: Four half-days
🌐 Type: Live Online Network Forensics Training
💵 Price: € 960 EUR
www.netresec.com?page=Training
📅 Dates: May 12-15, 2025
🕑 Duration: Four half-days
🌐 Type: Live Online Network Forensics Training
💵 Price: € 960 EUR
www.netresec.com?page=Training

Network Forensics Training
Upcoming Network Forensics Trainings and Classes from Netresec
www.netresec.com
December 20, 2024 at 12:03 PM
We’ve now scheduled our next Network Forensics for Incident Response training
📅 Dates: May 12-15, 2025
🕑 Duration: Four half-days
🌐 Type: Live Online Network Forensics Training
💵 Price: € 960 EUR
www.netresec.com?page=Training
📅 Dates: May 12-15, 2025
🕑 Duration: Four half-days
🌐 Type: Live Online Network Forensics Training
💵 Price: € 960 EUR
www.netresec.com?page=Training

December 18, 2024 at 6:14 PM
APT29 / Midnight Blizzard / Earth Koshchei use RDP relays to gain control of victims’ machines. One RDP config pretends to be for Regeringskansliet (Swedish Gov).
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...

December 17, 2024 at 3:47 PM
APT29 / Midnight Blizzard / Earth Koshchei use RDP relays to gain control of victims’ machines. One RDP config pretends to be for Regeringskansliet (Swedish Gov).
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...
Reposted by 𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
@piotrkijewski.bsky.social on Shadowserver & our unique non-profit approach to raising the bar on cybersecurity worldwide by sharing free threat intelligence, supporting LE in disrupting cybercrime & cybersecurity capacity building all around the planet!
www.helpnetsecurity.com/2024/12/05/p...
www.helpnetsecurity.com/2024/12/05/p...

How the Shadowserver Foundation helps network defenders with free intelligence feeds - Help Net Security
The Shadowserver Foundation’s mission is to make the internet secure by exposing vulnerabilities, malicious activity, and emerging threats.
www.helpnetsecurity.com
December 6, 2024 at 8:30 AM
@piotrkijewski.bsky.social on Shadowserver & our unique non-profit approach to raising the bar on cybersecurity worldwide by sharing free threat intelligence, supporting LE in disrupting cybercrime & cybersecurity capacity building all around the planet!
www.helpnetsecurity.com/2024/12/05/p...
www.helpnetsecurity.com/2024/12/05/p...