
𝙽𝙴𝚃𝚁𝙴𝚂𝙴𝙲
@netresec.com
Experts in Network Forensics and Network Security Monitoring. Creators of #NetworkMiner, #CapLoader, PacketCache, #PolarProxy and RawCap.
Website: https://www.netresec.com/
Mastodon: @[email protected]
Website: https://www.netresec.com/
Mastodon: @[email protected]
Thank you CISA, @ncsc.gov.uk, @bsi.bund.de et al. for publishing the advisory on Russian GRU Targeting Western Logistics Entities and Technology Companies. This list of mocking services is great for threat hunting!
www.cisa.gov/news-events/...
www.cisa.gov/news-events/...
![Many organizations may not need to allow outgoing traffic to hosting and API mocking services, which are frequently used by GRU unit 26165. Organizations should consider alerting on or blocking the following services, with exceptions allowlisted for legitimate activity [D3-DNSDL].
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Heuristic detections for web requests to new subdomains, including of the above providers, may uncover malicious phishing activity [D3-DNRA]. Logging the requests for each sub-domain requested by users on a network, such as in DNS or firewall logs, may enable system administrators to identify new targeting and victims.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:2qrgzoyfwkguclususquvdz2/bafkreidsg3ldjaxglxhetka5xmbm2gc7xlthvuyoek2vmeo6ny5tsdi3di@jpeg)
May 22, 2025 at 5:16 PM
Thank you CISA, @ncsc.gov.uk, @bsi.bund.de et al. for publishing the advisory on Russian GRU Targeting Western Logistics Entities and Technology Companies. This list of mocking services is great for threat hunting!
www.cisa.gov/news-events/...
www.cisa.gov/news-events/...
NetworkMiner automatically extracts EML files as well as attachments (here a jpg image) to disk when it parses emails in SMTP, POP3 or IMAP traffic.
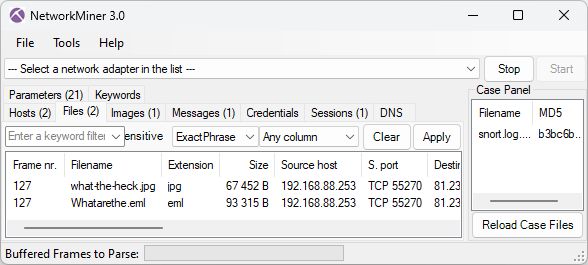
May 6, 2025 at 6:25 AM
NetworkMiner automatically extracts EML files as well as attachments (here a jpg image) to disk when it parses emails in SMTP, POP3 or IMAP traffic.
That's a very useful feature! Thanks for sharing 🙏
February 24, 2025 at 10:20 AM
That's a very useful feature! Thanks for sharing 🙏
Here's a Wireshark display filter that detects this type of LLMNR (multicast name resolution) spoofing:
dns.count.answers > 0 and lower(dns.qry.name) != lower(dns.resp.name)
dns.count.answers > 0 and lower(dns.qry.name) != lower(dns.resp.name)
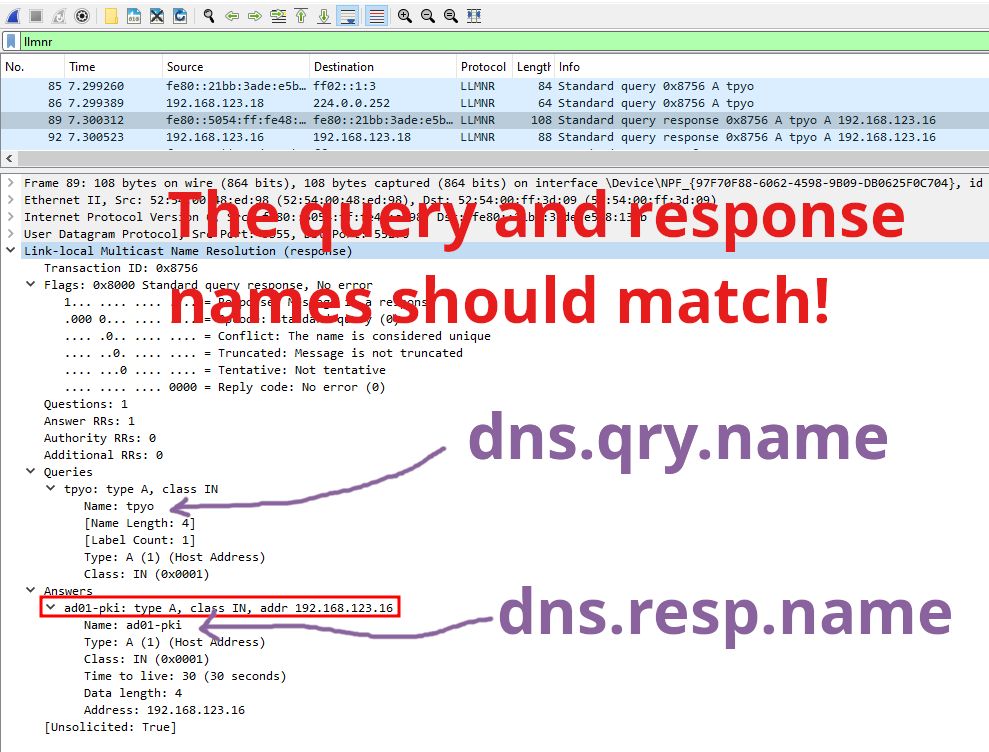
January 29, 2025 at 3:09 PM
Here's a Wireshark display filter that detects this type of LLMNR (multicast name resolution) spoofing:
dns.count.answers > 0 and lower(dns.qry.name) != lower(dns.resp.name)
dns.count.answers > 0 and lower(dns.qry.name) != lower(dns.resp.name)

December 18, 2024 at 6:14 PM
APT29 / Midnight Blizzard / Earth Koshchei use RDP relays to gain control of victims’ machines. One RDP config pretends to be for Regeringskansliet (Swedish Gov).
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...

December 17, 2024 at 3:47 PM
APT29 / Midnight Blizzard / Earth Koshchei use RDP relays to gain control of victims’ machines. One RDP config pretends to be for Regeringskansliet (Swedish Gov).
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...
Thanks to @feikeh.bsky.social and @sjhilt.hilt.zip for sharing indicators!
www.trendmicro.com/en_us/resear...
tria.ge/241023-qpfnl...
The dropped bot (which?) uses the NKN peer-to-peer network to hide its C2 traffic.


December 6, 2024 at 11:24 AM
The dropped bot (which?) uses the NKN peer-to-peer network to hide its C2 traffic.
Downloaded a fresh pcap from any.run to verify that #CapLoader identifies this traffic as Socks5Systemz backconnect ✅
app.any.run/tasks/c1b2dc...
app.any.run/tasks/c1b2dc...

December 5, 2024 at 3:35 PM
Downloaded a fresh pcap from any.run to verify that #CapLoader identifies this traffic as Socks5Systemz backconnect ✅
app.any.run/tasks/c1b2dc...
app.any.run/tasks/c1b2dc...
#Socks5Systemz backconnect traffic now uses TCP port 2024 (previously 2023)
infosec.exchange/@abuse_ch@io...
infosec.exchange/@abuse_ch@io...

December 5, 2024 at 3:35 PM
#Socks5Systemz backconnect traffic now uses TCP port 2024 (previously 2023)
infosec.exchange/@abuse_ch@io...
infosec.exchange/@abuse_ch@io...
Here's another one with instructions from C2 server to download the next stage DLL.
Initial JS: 61dfc228a478f21326908f0231ff553c
Dropped DLL: c6ef634779facf10516f0dd6d0d1757c
app.any.run/tasks/8831ab...
Initial JS: 61dfc228a478f21326908f0231ff553c
Dropped DLL: c6ef634779facf10516f0dd6d0d1757c
app.any.run/tasks/8831ab...

November 28, 2024 at 9:51 AM
Here's another one with instructions from C2 server to download the next stage DLL.
Initial JS: 61dfc228a478f21326908f0231ff553c
Dropped DLL: c6ef634779facf10516f0dd6d0d1757c
app.any.run/tasks/8831ab...
Initial JS: 61dfc228a478f21326908f0231ff553c
Dropped DLL: c6ef634779facf10516f0dd6d0d1757c
app.any.run/tasks/8831ab...
Nice malware lab setup using FLARE VM, #PolarProxy and #REMnux to decrypt and inspect TLS traffic.
www.koenmolenaar.nl/nl/write-ups...
www.koenmolenaar.nl/nl/write-ups...

November 28, 2024 at 9:20 AM
Nice malware lab setup using FLARE VM, #PolarProxy and #REMnux to decrypt and inspect TLS traffic.
www.koenmolenaar.nl/nl/write-ups...
www.koenmolenaar.nl/nl/write-ups...
Two new Network Forensics training events!
🇪🇺 PCAP in the Morning Europe, March 4-7
🇺🇸 PCAP in the Morning US, March 25-28
netresec.com?b=23C9979
🇪🇺 PCAP in the Morning Europe, March 4-7
🇺🇸 PCAP in the Morning US, March 25-28
netresec.com?b=23C9979

February 6, 2024 at 4:23 PM
Two new Network Forensics training events!
🇪🇺 PCAP in the Morning Europe, March 4-7
🇺🇸 PCAP in the Morning US, March 25-28
netresec.com?b=23C9979
🇪🇺 PCAP in the Morning Europe, March 4-7
🇺🇸 PCAP in the Morning US, March 25-28
netresec.com?b=23C9979


