https://shadowserver.org/partner

We have introduced an ECS logging script for our intelligence reports. This script uses Redis to queue events for Logstash.
Check it out at github.com/The-Shadowse...


It's worth mentioning we share many End-of-Life devices/apps in our daily reporting, tagged 'eol'.
See: dashboard.shadowserver.org/statistics/c...


It's worth mentioning we share many End-of-Life devices/apps in our daily reporting, tagged 'eol'.
See: dashboard.shadowserver.org/statistics/c...
Data in shadowserver.org/what-we-do/n...
Tree Map view: dashboard.shadowserver.org/statistics/c...
Thank you to the KSA NCA for the heads up!

Data in shadowserver.org/what-we-do/n...
Tree Map view: dashboard.shadowserver.org/statistics/c...
Thank you to the KSA NCA for the heads up!
#CyberCivilDefense #take9
Dashboard Tree Map: dashboard.shadowserver.org/statistics/c...

#CyberCivilDefense #take9
Dashboard Tree Map: dashboard.shadowserver.org/statistics/c...

Dashboard Tree Map: dashboard.shadowserver.org/statistics/c...
World Map: dashboard.shadowserver.org/statistics/i...


World Map: dashboard.shadowserver.org/statistics/i...
Ivanti hotfix guidance: forums.ivanti.com/s/article/Se...


Ivanti hotfix guidance: forums.ivanti.com/s/article/Se...
We share exposed Fortinet instances with FortiCloud SSO enabled daily in our feeds (~10 000 seen)


We share exposed Fortinet instances with FortiCloud SSO enabled daily in our feeds (~10 000 seen)
CVE-2026-23760 Geo Treemap View: dashboard.shadowserver.org/statistics/c...

CVE-2026-23760 Geo Treemap View: dashboard.shadowserver.org/statistics/c...
~800K exposed

~800K exposed
8001 unique IPs likely vulnerable on 2026-01-12 (18783 exposed). Note Exploit PoCs are public.
Tree Map: dashboard.shadowserver.org/statistics/c...
Raw IP data: www.shadowserver.org/what-we-do/n...

8001 unique IPs likely vulnerable on 2026-01-12 (18783 exposed). Note Exploit PoCs are public.
Tree Map: dashboard.shadowserver.org/statistics/c...
Raw IP data: www.shadowserver.org/what-we-do/n...
Scan results: dashboard.shadowserver.org/statistics/c...
Sinkhole results:
dashboard.shadowserver.org/statistics/c...


Scan results: dashboard.shadowserver.org/statistics/c...
Sinkhole results:
dashboard.shadowserver.org/statistics/c...
dashboard.shadowserver.org/statistics/c...
dashboard.shadowserver.org/statistics/c...


dashboard.shadowserver.org/statistics/c...
dashboard.shadowserver.org/statistics/c...
Dashboard Tree Map view: dashboard.shadowserver.org/statistics/c...
IP data in Vulnerable HTTP: www.shadowserver.org/what-we-do/n...


Dashboard Tree Map view: dashboard.shadowserver.org/statistics/c...
IP data in Vulnerable HTTP: www.shadowserver.org/what-we-do/n...
After 5 1/2 years since being published still over 10K Fortinet firewalls remain unpatched. Actively exploited as recently highlighted by Fortinet: www.fortinet.com/blog/psirt-b...


After 5 1/2 years since being published still over 10K Fortinet firewalls remain unpatched. Actively exploited as recently highlighted by Fortinet: www.fortinet.com/blog/psirt-b...

interpol.int/en/News-and-...
Undertaken as part of African Joint Operation against Cybercrime (AFJOC) project, funded by UK FCDO, & EU/Council of Europe GLACY-e project

interpol.int/en/News-and-...
Undertaken as part of African Joint Operation against Cybercrime (AFJOC) project, funded by UK FCDO, & EU/Council of Europe GLACY-e project
WatchGuard Advisory: www.watchguard.com/wgrd-psirt/a...

WatchGuard Advisory: www.watchguard.com/wgrd-psirt/a...


92M stolen data items from 567K victim IPs across 228 countries
Additional data shared by LE partners under Operation Endgame
Updated blog:
shadowserver.org/news/rhadama...
Check your reports!

92M stolen data items from 567K victim IPs across 228 countries
Additional data shared by LE partners under Operation Endgame
Updated blog:
shadowserver.org/news/rhadama...
Check your reports!
We have introduced an ECS logging script for our intelligence reports. This script uses Redis to queue events for Logstash.
Check it out at github.com/The-Shadowse...

We have introduced an ECS logging script for our intelligence reports. This script uses Redis to queue events for Logstash.
Check it out at github.com/The-Shadowse...
See: dashboard.shadowserver.org/statistics/c...
Check for compromise & patch!
Thank you to Validin & LeakIX for the collaboration!

See: dashboard.shadowserver.org/statistics/c...
Check for compromise & patch!
Thank you to Validin & LeakIX for the collaboration!
dashboard.shadowserver.org/statistics/h...

dashboard.shadowserver.org/statistics/h...
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...
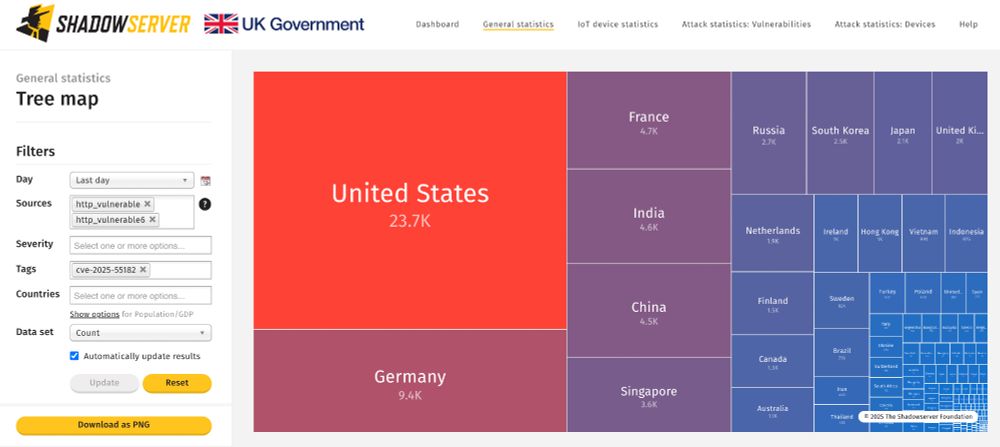
IP data is being shared in Vulnerable HTTP reports: www.shadowserver.org/what-we-do/n...
Dashboard geo breakdown: dashboard.shadowserver.org/statistics/c...

