
UK_Daniel_Card
@mrr3b00t.bsky.social
Pinned
UK_Daniel_Card
@mrr3b00t.bsky.social
· Nov 20

On gang let’s see how this goes! The victim machine is just having a clean windows 11 build deployed to it! #Wifi #hacking #fun #wificafe #pwndefend
Reposted by UK_Daniel_Card
Just in time for my annual review. 🙌 This should get me at least another 10% salary increase.
Thanks @mrr3b00t.bsky.social
mr-r3b00t.github.io/how_to_be_a_...
Thanks @mrr3b00t.bsky.social
mr-r3b00t.github.io/how_to_be_a_...


November 2, 2025 at 9:00 PM
Just in time for my annual review. 🙌 This should get me at least another 10% salary increase.
Thanks @mrr3b00t.bsky.social
mr-r3b00t.github.io/how_to_be_a_...
Thanks @mrr3b00t.bsky.social
mr-r3b00t.github.io/how_to_be_a_...
Reposted by UK_Daniel_Card
Hosting a site with no public IP and minimal attack surface.
No open ports. No brute-force noise. No drama.
@cloudflare.social Tunnel for the win :)
clarkee.co.uk/hosting-a-st...
No open ports. No brute-force noise. No drama.
@cloudflare.social Tunnel for the win :)
clarkee.co.uk/hosting-a-st...

Publishing a Website With No Public IP (And No Attack Surface)
Recently, I needed to publish a simple website for a small community, nothing fancy, but I didn’t want to open any unnecessary holes. I wanted it secure. I also wanted caching to save bandwidth and CP...
clarkee.co.uk
October 31, 2025 at 3:01 PM
Hosting a site with no public IP and minimal attack surface.
No open ports. No brute-force noise. No drama.
@cloudflare.social Tunnel for the win :)
clarkee.co.uk/hosting-a-st...
No open ports. No brute-force noise. No drama.
@cloudflare.social Tunnel for the win :)
clarkee.co.uk/hosting-a-st...
Reposted by UK_Daniel_Card
1/ Hi, I'm TProphet. I write the Telecom Informer for @2600.com. A lot of people have been asking me about www.nbcnews.com/politics/nat... given that I'm somewhat knowledgeable in the area.
Here's my take: I'm kind of astonished that this is public, and it isn't normal that it would ever be.
Here's my take: I'm kind of astonished that this is public, and it isn't normal that it would ever be.

Secret Service agents dismantle network that could shut down New York cellphone system
Agents discovered electronic devices in five locations in and around the city that could be used to disable cellphone towers. The system could also be used for criminal activities.
www.nbcnews.com
September 23, 2025 at 6:49 PM
1/ Hi, I'm TProphet. I write the Telecom Informer for @2600.com. A lot of people have been asking me about www.nbcnews.com/politics/nat... given that I'm somewhat knowledgeable in the area.
Here's my take: I'm kind of astonished that this is public, and it isn't normal that it would ever be.
Here's my take: I'm kind of astonished that this is public, and it isn't normal that it would ever be.
Reposted by UK_Daniel_Card
Night All,
LMAO👇😁😆😂🤣💜
LMAO👇😁😆😂🤣💜

September 23, 2025 at 9:36 PM
Night All,
LMAO👇😁😆😂🤣💜
LMAO👇😁😆😂🤣💜
Reposted by UK_Daniel_Card
The Secret Service isn't claiming it foiled any plot targeting the UN General Assembly. Just that a big collection of SIMs (probably used for fraud) could have *potentially* disrupted NYC cell service. The SIMs were in a *35 MILE* radius of the UN.
These headlines are all pretty egregiously wrong:
These headlines are all pretty egregiously wrong:



September 23, 2025 at 9:20 PM
The Secret Service isn't claiming it foiled any plot targeting the UN General Assembly. Just that a big collection of SIMs (probably used for fraud) could have *potentially* disrupted NYC cell service. The SIMs were in a *35 MILE* radius of the UN.
These headlines are all pretty egregiously wrong:
These headlines are all pretty egregiously wrong:
👀👀👀👀👀👀👀
The European airports ransomware incident is a little heard of ransomware variant, Hardbit, which has no portal/blog and normally hits tiny companies.
Today, day four, they had to restart recovery again as the machines got reinfected.. again.
Today, day four, they had to restart recovery again as the machines got reinfected.. again.
September 23, 2025 at 8:39 PM
👀👀👀👀👀👀👀
Yo bleeps, how's it going?
September 23, 2025 at 8:27 PM
Yo bleeps, how's it going?
Reposted by UK_Daniel_Card
Only ~6% of CVEs are ever exploited… yet scanners still flood teams with endless alerts.
More signatures ≠ more security. They guess. We validate.
Curious what actually matters? Check out our latest blog: The Coverage Lie 👉 projectdiscovery.io/blog/why-cur...
More signatures ≠ more security. They guess. We validate.
Curious what actually matters? Check out our latest blog: The Coverage Lie 👉 projectdiscovery.io/blog/why-cur...

September 3, 2025 at 8:43 PM
Only ~6% of CVEs are ever exploited… yet scanners still flood teams with endless alerts.
More signatures ≠ more security. They guess. We validate.
Curious what actually matters? Check out our latest blog: The Coverage Lie 👉 projectdiscovery.io/blog/why-cur...
More signatures ≠ more security. They guess. We validate.
Curious what actually matters? Check out our latest blog: The Coverage Lie 👉 projectdiscovery.io/blog/why-cur...
is everyone loving salesforce today???
September 2, 2025 at 6:41 PM
is everyone loving salesforce today???
howdy Bleeps! checking in with the world! what's new? anyone got any cool cyber stuff going on?
August 30, 2025 at 9:58 AM
howdy Bleeps! checking in with the world! what's new? anyone got any cool cyber stuff going on?
Please don't DM me here, use LinkedIN or twitter as I'm not sending my ID/PII here. thanks!
August 23, 2025 at 6:35 PM
Please don't DM me here, use LinkedIN or twitter as I'm not sending my ID/PII here. thanks!
Reposted by UK_Daniel_Card
NEW: Earlier this month, two hackers published their findings in Phrack magazine after earlier breaking into the computer of a North Korean government hacker.
Now, in speaking with @lorenzofb.bsky.social, the two hackers explain why they went public — even though their breach was probably illegal.
Now, in speaking with @lorenzofb.bsky.social, the two hackers explain why they went public — even though their breach was probably illegal.

Hackers who exposed North Korean government hacker explain why they did it | TechCrunch
The two self-described hacktivists said they had access to the North Korean spy’s computer for around four months before deciding what they had found should be made public.
techcrunch.com
August 21, 2025 at 12:39 PM
NEW: Earlier this month, two hackers published their findings in Phrack magazine after earlier breaking into the computer of a North Korean government hacker.
Now, in speaking with @lorenzofb.bsky.social, the two hackers explain why they went public — even though their breach was probably illegal.
Now, in speaking with @lorenzofb.bsky.social, the two hackers explain why they went public — even though their breach was probably illegal.
Reposted by UK_Daniel_Card
wow, all it took was one week of restricted access to porn.
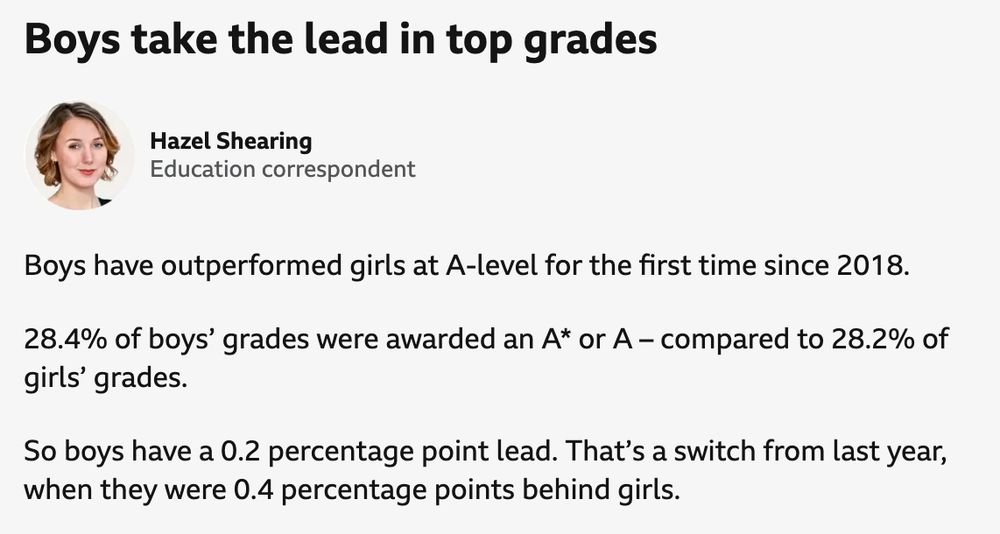
August 14, 2025 at 4:37 PM
wow, all it took was one week of restricted access to porn.
Reposted by UK_Daniel_Card
Looking back on last week gets us stoked for NoiseFest 2026! 🤘
August 14, 2025 at 7:59 PM
Looking back on last week gets us stoked for NoiseFest 2026! 🤘
the goal is typically not to be risk or harm free, it's to be at a reasonable level of risk based on appetite and tolerance....
zero risk isn't really a thing...
zero risk isn't really a thing...
August 13, 2025 at 5:24 PM
the goal is typically not to be risk or harm free, it's to be at a reasonable level of risk based on appetite and tolerance....
zero risk isn't really a thing...
zero risk isn't really a thing...
Reposted by UK_Daniel_Card
whut?? you guys only wear it outside??

August 13, 2025 at 3:16 PM
whut?? you guys only wear it outside??
Reposted by UK_Daniel_Card
Never use any WiFi unless it’s in your own house, but only if it’s Faraday cage!
Watch out when clicking on links, don’t do this if they look suspicious!
Watch out when clicking on links, don’t do this if they look suspicious!
August 13, 2025 at 1:39 PM
Never use any WiFi unless it’s in your own house, but only if it’s Faraday cage!
Watch out when clicking on links, don’t do this if they look suspicious!
Watch out when clicking on links, don’t do this if they look suspicious!
never go outside without chainmail on! #AssumeBreach

a man wearing chain mail and armor is smiling
ALT: a man wearing chain mail and armor is smiling
media.tenor.com
August 13, 2025 at 1:27 PM
never go outside without chainmail on! #AssumeBreach
what a load of nonsense!
Public wifi is reasonably safe! Airports are even more because they have more CCTV than you can imagine and armed police.
people get pwn3d via phishing and malware/infostealers....
#WIFI #Insanity
Public wifi is reasonably safe! Airports are even more because they have more CCTV than you can imagine and armed police.
people get pwn3d via phishing and malware/infostealers....
#WIFI #Insanity
📱 Many people forget that public Wi-Fi networks can be a goldmine for hackers! Always assume your data is at risk when connecting in cafes or airports. Stay safe! #MobileSecurity
August 11, 2025 at 8:08 AM

