
Learn about:
❓Why you should use them
📂Specific use cases
🦴Anatomy of a Sigma rule
🔍 Sigma rule event processing for adv. detection capabilities
graylog.org/post/the-ult...

Learn about:
❓Why you should use them
📂Specific use cases
🦴Anatomy of a Sigma rule
🔍 Sigma rule event processing for adv. detection capabilities
graylog.org/post/the-ult...
They gained access to their Chrome Web Store admin credentials and published a malicious version of the Cyberhaven extension.
Read my full writeup here:
www.vulnu.com/p/breaking-c...
Thanks @jaimeblascob.bsky.social and @johntuckner.me

They gained access to their Chrome Web Store admin credentials and published a malicious version of the Cyberhaven extension.
Read my full writeup here:
www.vulnu.com/p/breaking-c...
Thanks @jaimeblascob.bsky.social and @johntuckner.me



Well, then this is for you…
If you or someone you know aspires to be a SOC Analyst, check out my hands-on lab, "So you want to be a SOC Analyst?"
Thousands of people have been through it and the feedback has been 🔥
blog.ecapuano.com/p/so-you-wan... #infosec

Well, then this is for you…

Routers on windowsills are easier to hack.

Musicians can still speak out. In fact, we're hoping for a groundswell: www.savethearchive.com
Fans and archive-lovers can sign in solidarity, too!

go.bsky.app/SQygf7K

We are hiring the manager of our Patron Services team.
For more information please see this job listing ⤵️
app.trinethire.com/companies/32...

We are hiring the manager of our Patron Services team.
For more information please see this job listing ⤵️
app.trinethire.com/companies/32...
Trojans, worms, #ransomware & #botnets are all types of destructive malware that can wreck havoc on your systems. 😰
Learn about the motivations behind deploying it, how it works, & how #TDIR can help. 🛡️
graylog.org/post/destruc... #cybersecurity

Trojans, worms, #ransomware & #botnets are all types of destructive malware that can wreck havoc on your systems. 😰
Learn about the motivations behind deploying it, how it works, & how #TDIR can help. 🛡️
graylog.org/post/destruc... #cybersecurity
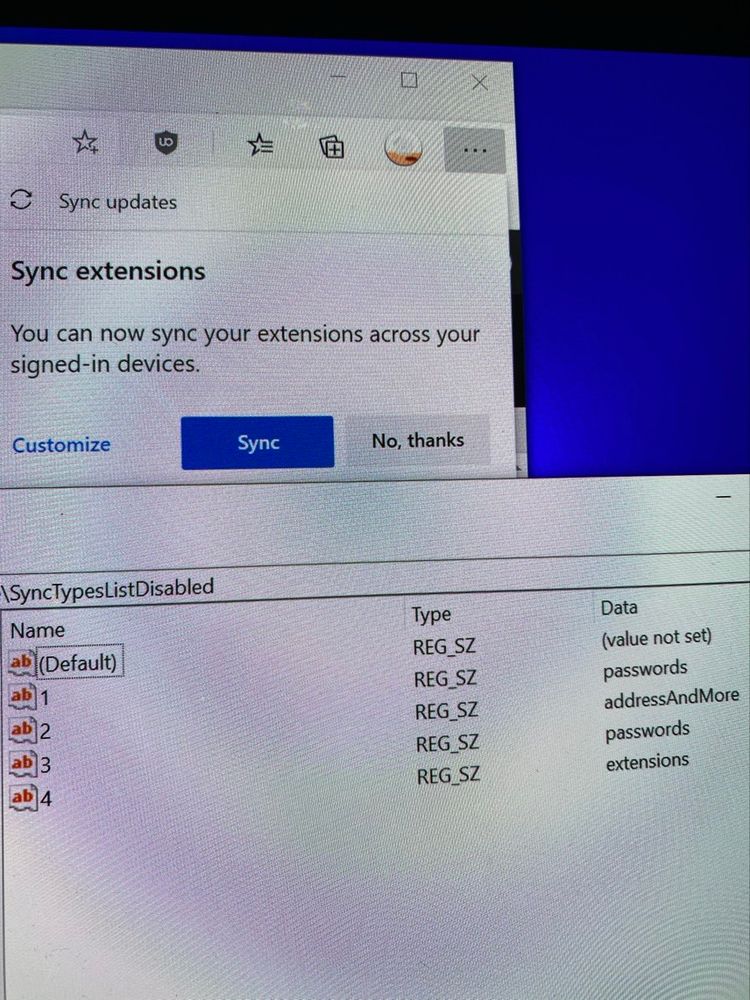
If so, this is for you…




If so, this is for you…
search.libraryofleaks.org
search.libraryofleaks.org
📢In my latest blog post I discuss another network based technique to prevent data ingest and ways to detect it.
And if you want even more, checkout part 2 released by @Cyb3rMonk Link in the post

📢In my latest blog post I discuss another network based technique to prevent data ingest and ways to detect it.
And if you want even more, checkout part 2 released by @Cyb3rMonk Link in the post
EDR Silencer and Beyond: Exploring Methods to Block EDR Communication - Part 2
In collaboration with
@fabian.bader.cloud
academy.bluraven.io/blog/edr-sil...
#redteam

EDR Silencer and Beyond: Exploring Methods to Block EDR Communication - Part 2
In collaboration with
@fabian.bader.cloud
academy.bluraven.io/blog/edr-sil...
#redteam

