
Listen as he shares the story behind his open-source tool, IoT Hunter, and explains how, through automation, it helps defenders cover hundreds of CVEs. brnw.ch/21wXDRr

Listen as he shares the story behind his open-source tool, IoT Hunter, and explains how, through automation, it helps defenders cover hundreds of CVEs. brnw.ch/21wXDRr
Rhadamanthys: brnw.ch/21wXsCc
VenomRAT: brnw.ch/21wXsCd

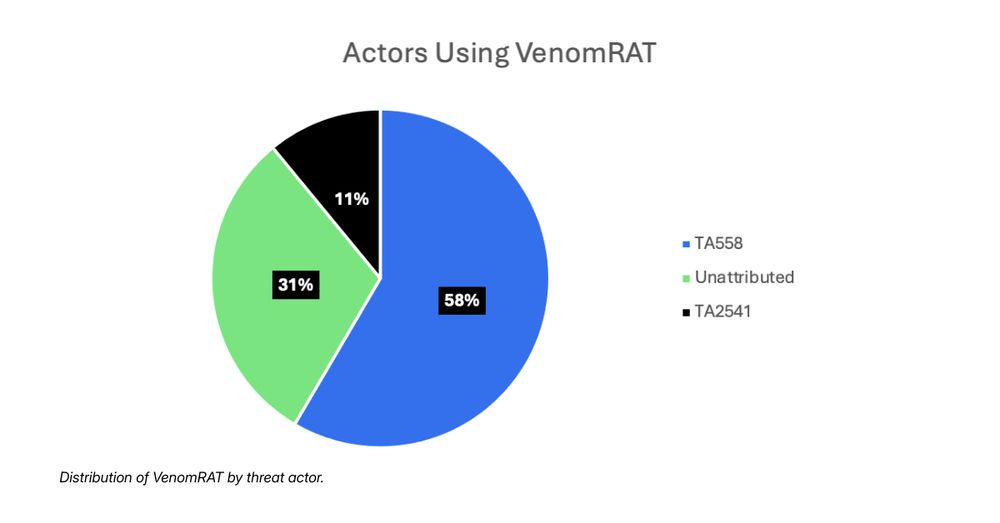
Rhadamanthys: brnw.ch/21wXsCc
VenomRAT: brnw.ch/21wXsCd
Blog: www.proofpoint.com/us/blog/thre...

Blog: www.proofpoint.com/us/blog/thre...
⬇️
Once the trucker replies, they infect them with malicious RMMs to overtake their company. They then try to bid on real loads to intercept and pick them up.
⬇️
The stolen physical goods are sold.

⬇️
Once the trucker replies, they infect them with malicious RMMs to overtake their company. They then try to bid on real loads to intercept and pick them up.
⬇️
The stolen physical goods are sold.



Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.

Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.

Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.

Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.
This is likely a concerted effort from #TA415 to blend in with existing legitimate traffic to trusted services, including Google Sheets/Calendar, & VS Code Remote Tunnels.

Key finding 1️⃣: TA415 spoofed the U.S.-China Business Council and a senior congressional leader to deliver spearphishing lures tied to trade and sanctions policy.

Key finding 1️⃣: TA415 spoofed the U.S.-China Business Council and a senior congressional leader to deliver spearphishing lures tied to trade and sanctions policy.


On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5

On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones

Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones
Threat actors create or clone websites that impersonate prominent brands, use CAPTCHA for filtering, and then post credentials to Telegram.

Threat actors create or clone websites that impersonate prominent brands, use CAPTCHA for filtering, and then post credentials to Telegram.
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo

We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo


On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L

On this DISCARDED episode, we discuss the chaotic brilliance of mid-tier eCrime actors, why shared commodity tooling can make attribution difficult, why TA582 is so interesting, and much more.
Stream here 👉 brnw.ch/21wUw3L
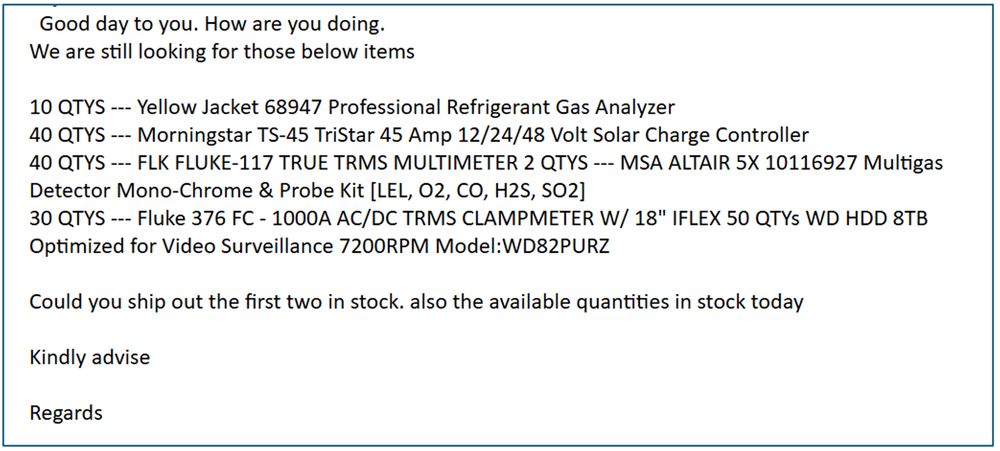
Many sent quote requests from #freemail accounts, but some used lookalike domains.
The emails typically requested highly specific items (example below).
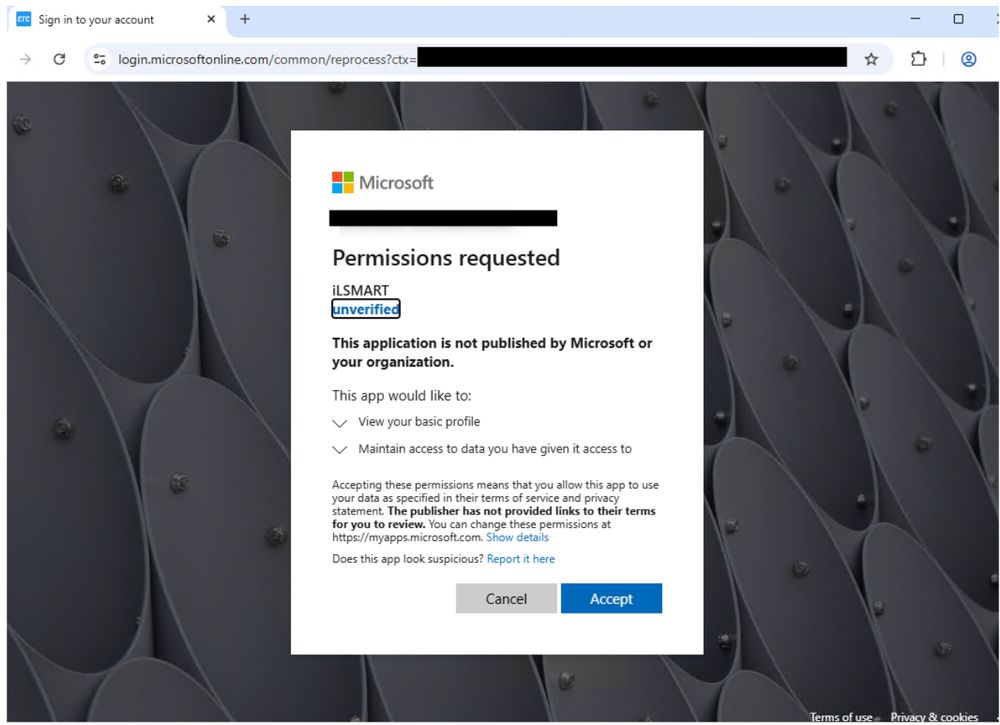
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
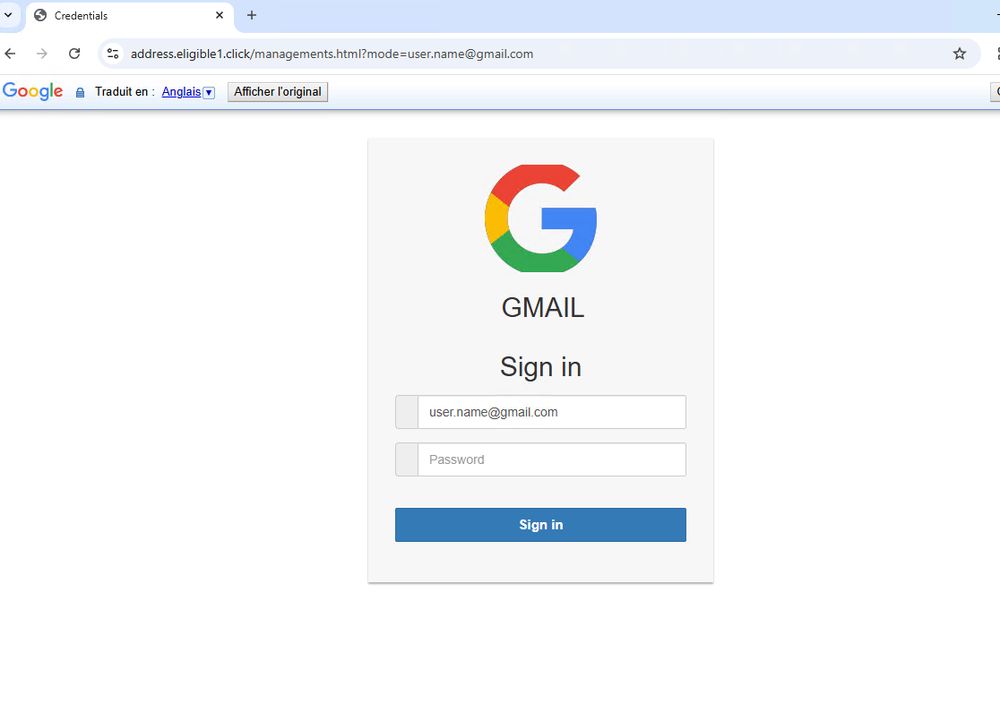
If clicked, it actually leads to a bogus authentication page designed to harvest credentials.
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️
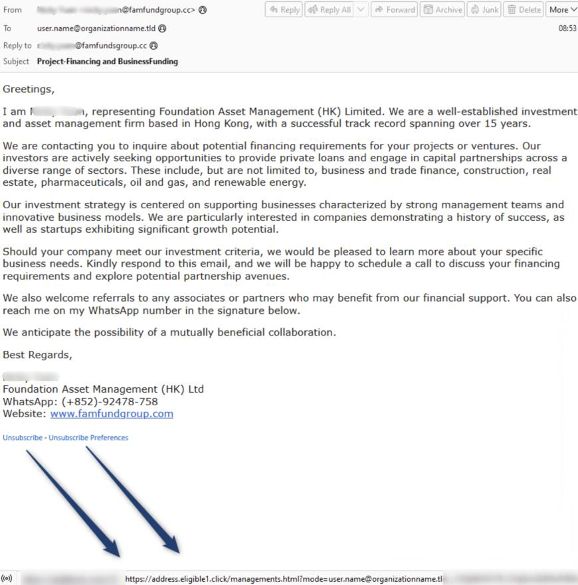
Learn about an interesting phishing campaign involving the “unsubscribe” link often included in marketing emails. 🔍 ⤵️

