
Behind the campaign—which has impacted over 100,000 users in over 3,000 tenants—is a cluster tracked as #UNK_BareZilla.

Behind the campaign—which has impacted over 100,000 users in over 3,000 tenants—is a cluster tracked as #UNK_BareZilla.
Proofpoint observed this technique used at scale across both financially motivated and state-aligned threat clusters.

Proofpoint observed this technique used at scale across both financially motivated and state-aligned threat clusters.
Join @selenalarson.bsky.social & Sarah Sabotka for our new monthly videocast, Intercepted.
The first #livestream will happen on Jan 21 at 10 AM ET.
Info: www.proofpoint.com/us/resources...
Join @selenalarson.bsky.social & Sarah Sabotka for our new monthly videocast, Intercepted.
The first #livestream will happen on Jan 21 at 10 AM ET.
Info: www.proofpoint.com/us/resources...
Stream now for an end-of-year look at how the cyber threat landscape evolved—and what defenders need to know as we enter 2026.
🎧: brnw.ch/21wYKI6

Stream now for an end-of-year look at how the cyber threat landscape evolved—and what defenders need to know as we enter 2026.
🎧: brnw.ch/21wYKI6
Threat actors are using #phishing tactics to trick users into giving access to #M365 accounts.
⚠️ Successful compromise leads to #accounttakeover, #dataexfiltration, and more.
Blog: brnw.ch/21wYtcM
Here’s what you need to know. 🧵⤵️

Threat actors are using #phishing tactics to trick users into giving access to #M365 accounts.
⚠️ Successful compromise leads to #accounttakeover, #dataexfiltration, and more.
Blog: brnw.ch/21wYtcM
Here’s what you need to know. 🧵⤵️
Our observations of #UNK_SmudgedSerpent, a newly identified cluster linked to Iran, exemplify the evolving complexity and resourcefulness of the country's modern threat ops.
Saher Naumaan shared her insights. brnw.ch/21wYrCZ

Our observations of #UNK_SmudgedSerpent, a newly identified cluster linked to Iran, exemplify the evolving complexity and resourcefulness of the country's modern threat ops.
Saher Naumaan shared her insights. brnw.ch/21wYrCZ
Here, @selenalarson.bsky.social shares her gratitude and a look at what’s to come in the new year.
Stay tuned for more threat insight and behind-the-scenes analysis in 2026! 🎊
Here, @selenalarson.bsky.social shares her gratitude and a look at what’s to come in the new year.
Stay tuned for more threat insight and behind-the-scenes analysis in 2026! 🎊
Join our ho-ho-hosts for a fun, insightful and very festive episode that highlights the seasonal threats that might be landing under your digital tree this year. ⛄
Stream now to explore how cybercriminals use seasonal themes to trick consumers & enterprises. brnw.ch/21wYf9o

Join our ho-ho-hosts for a fun, insightful and very festive episode that highlights the seasonal threats that might be landing under your digital tree this year. ⛄
Stream now to explore how cybercriminals use seasonal themes to trick consumers & enterprises. brnw.ch/21wYf9o
Proofpoint is seeing an increase in holiday-themed threats. Main #phishing lure themes include party invitations, holiday vouchers, end-of-year bonuses, and holiday travel.
Proofpoint is seeing an increase in holiday-themed threats. Main #phishing lure themes include party invitations, holiday vouchers, end-of-year bonuses, and holiday travel.
Listen as he shares the story behind his open-source tool, IoT Hunter, and explains how, through automation, it helps defenders cover hundreds of CVEs. brnw.ch/21wXDRr

Listen as he shares the story behind his open-source tool, IoT Hunter, and explains how, through automation, it helps defenders cover hundreds of CVEs. brnw.ch/21wXDRr
Rhadamanthys: brnw.ch/21wXsCc
VenomRAT: brnw.ch/21wXsCd

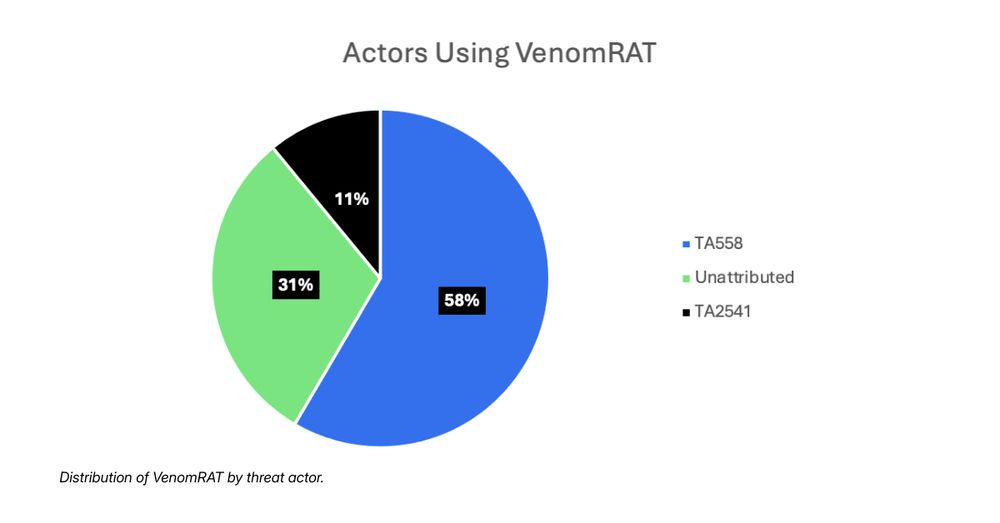
Rhadamanthys: brnw.ch/21wXsCc
VenomRAT: brnw.ch/21wXsCd
@bloomberg.com spoke with our #ecrime experts who warned, "It is a full-scale supply chain threat."
Read the article: www.bloomberg.com/news/article....

@bloomberg.com spoke with our #ecrime experts who warned, "It is a full-scale supply chain threat."
Read the article: www.bloomberg.com/news/article....
Blog: www.proofpoint.com/us/blog/thre...

Blog: www.proofpoint.com/us/blog/thre...
Today, cargo theft is commonly conducted digitally by hacking the #supplychain to exploit gaps and steal #freight remotely.
🧵⤵️
Today, cargo theft is commonly conducted digitally by hacking the #supplychain to exploit gaps and steal #freight remotely.
🧵⤵️
We use this tool internally to help track multiple threat actors with high confidence.
We use this tool internally to help track multiple threat actors with high confidence.
Here, we detail our findings and security implications. ⤵️ brnw.ch/21wWOgL

Here, we detail our findings and security implications. ⤵️ brnw.ch/21wWOgL
Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.

Messages are sent from hundreds of compromised sender accounts impersonating ELSTER and contain malicious URLs.
The sophisticated cybercriminal, notably, appears to own its entire attack chain with multiple delivery techniques.
Learn about TA585 and one of its favored payloads, MonsterV2: brnw.ch/21wWAAU.

The sophisticated cybercriminal, notably, appears to own its entire attack chain with multiple delivery techniques.
Learn about TA585 and one of its favored payloads, MonsterV2: brnw.ch/21wWAAU.
Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.

Activity was observed from September 20-30th, affecting nearly half a million users in over 4,000 tenants.
Blog: www.proofpoint.com/us/blog/thre....

Blog: www.proofpoint.com/us/blog/thre....

On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5

On this episode of DISCARDED, you'll hear why legacy features like Direct Send are a prime target for cybercriminals.
Stream now on our website: brnw.ch/21wVja5
Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones

Bookmark the show page and reserve your seat at the table 🪑 alongside Selena Larson, Dave Bittner and Keith Mularski.
🔥 You won't want to miss it! thecyberwire.com/podcasts/onl...
#podcast #hotones
We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo

We have observed threat actor campaigns leveraging the AI-generated website builder Lovable to create and host cred phishing, malware, and fraud websites.
Learn more in our blog: brnw.ch/21wV3Zo
We first spotted this post by ANY.RUN about ClickFix delivering Rhadamanthys and began investigating. infosec.exchange/@anyrun_app/...
We first spotted this post by ANY.RUN about ClickFix delivering Rhadamanthys and began investigating. infosec.exchange/@anyrun_app/...

