Sekoia.io
@sekoia.io
A #SOCplatform boosted by #AI and #threatintelligence, combining #SIEM, #SOAR, #Automation in a single solution. Used by End-users, MSSP and APIs
Our blog post provides an overview of the services facilitating this modus operandi and the market for infostealer logs tied to booking platforms, including underground activities around Booking[.]com data on Russian-speaking cybercrime forums.

November 6, 2025 at 10:27 AM
Our blog post provides an overview of the services facilitating this modus operandi and the market for infostealer logs tied to booking platforms, including underground activities around Booking[.]com data on Russian-speaking cybercrime forums.
In this report, we analysed a widespread, persistent campaign distributing the PureRAT malware via the #ClickFix social engineering tactic and emails impersonating Booking[.]com.
We also detailed the fraud scheme targeting hotel customers.
We also detailed the fraud scheme targeting hotel customers.

November 6, 2025 at 10:27 AM
In this report, we analysed a widespread, persistent campaign distributing the PureRAT malware via the #ClickFix social engineering tactic and emails impersonating Booking[.]com.
We also detailed the fraud scheme targeting hotel customers.
We also detailed the fraud scheme targeting hotel customers.
#TDR analysts dig into a modus operandi targeting the hospitality industry and the related cybercrime ecosystem that facilitates #phishing and #fraud campaigns.
blog.sekoia.io/phishing-cam...
blog.sekoia.io/phishing-cam...

November 6, 2025 at 10:27 AM
#TDR analysts dig into a modus operandi targeting the hospitality industry and the related cybercrime ecosystem that facilitates #phishing and #fraud campaigns.
blog.sekoia.io/phishing-cam...
blog.sekoia.io/phishing-cam...
Discover how #TransparentTribe (#APT36) uses a disguised DESKTOP dropper to deploy #DeskRAT, a Golang RAT, on BOSS Linux endpoints in India.
Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...
Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...

October 23, 2025 at 7:49 AM
Discover how #TransparentTribe (#APT36) uses a disguised DESKTOP dropper to deploy #DeskRAT, a Golang RAT, on BOSS Linux endpoints in India.
Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...
Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...
Our latest technical deep-dive unravels the mystery behind the opaque numeric codes (16, 272, 33554432, etc.) you see in #Microsoft365 audit logs.
blog.sekoia.io/userauthenti...
blog.sekoia.io/userauthenti...

October 21, 2025 at 9:14 AM
Our latest technical deep-dive unravels the mystery behind the opaque numeric codes (16, 272, 33554432, etc.) you see in #Microsoft365 audit logs.
blog.sekoia.io/userauthenti...
blog.sekoia.io/userauthenti...
After our initial #PolarEdge #botnet write-up, we’re happy to announce the second part: “Defrosting PolarEdge’s Backdoor,” a full technical deep-dive into its TLS-based implant.
blog.sekoia.io/polaredge-ba...
blog.sekoia.io/polaredge-ba...

October 14, 2025 at 1:35 PM
After our initial #PolarEdge #botnet write-up, we’re happy to announce the second part: “Defrosting PolarEdge’s Backdoor,” a full technical deep-dive into its TLS-based implant.
blog.sekoia.io/polaredge-ba...
blog.sekoia.io/polaredge-ba...
Key takeaways:
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable

October 2, 2025 at 1:56 PM
Key takeaways:
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
✉️ API exploitation: attackers leverage an exposed /cgi endpoint to push malicious SMS without authentication
🌐 Scale of exposure: over 18,000 routers accessible on the internet; 572 confirmed vulnerable
📱 Silent Smishing: The Hidden Abuse of Cellular Router APIs
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...

October 2, 2025 at 1:56 PM
📱 Silent Smishing: The Hidden Abuse of Cellular Router APIs
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
🌐 As usual, APT28 uses legitimate third-party services in its execution chain, such as Koofr or icedrive, or more recently Filen.
🎯 The campaign’s goal is to gather cyber intelligence on frontline combatants by targeting administrative and logistics personnel.
🎯 The campaign’s goal is to gather cyber intelligence on frontline combatants by targeting administrative and logistics personnel.

September 16, 2025 at 12:59 PM
🌐 As usual, APT28 uses legitimate third-party services in its execution chain, such as Koofr or icedrive, or more recently Filen.
🎯 The campaign’s goal is to gather cyber intelligence on frontline combatants by targeting administrative and logistics personnel.
🎯 The campaign’s goal is to gather cyber intelligence on frontline combatants by targeting administrative and logistics personnel.
📃 APT28 distributed weaponised Office documents masquerading as Ukrainian military admin forms to harvest cyber-military intelligence.
🕷️ Attackers deploy a custom backdoor dubbed BeardShell using a modified Covenant Grunt stager.
🕷️ Attackers deploy a custom backdoor dubbed BeardShell using a modified Covenant Grunt stager.

September 16, 2025 at 12:59 PM
📃 APT28 distributed weaponised Office documents masquerading as Ukrainian military admin forms to harvest cyber-military intelligence.
🕷️ Attackers deploy a custom backdoor dubbed BeardShell using a modified Covenant Grunt stager.
🕷️ Attackers deploy a custom backdoor dubbed BeardShell using a modified Covenant Grunt stager.
🐻 #APT28 – Operation Phantom Net Voxel: deep-dive into the latest spear-phishing campaign targeting Ukrainian military administrative staff.
blog.sekoia.io/apt28-operat...
blog.sekoia.io/apt28-operat...

September 16, 2025 at 12:59 PM
🐻 #APT28 – Operation Phantom Net Voxel: deep-dive into the latest spear-phishing campaign targeting Ukrainian military administrative staff.
blog.sekoia.io/apt28-operat...
blog.sekoia.io/apt28-operat...
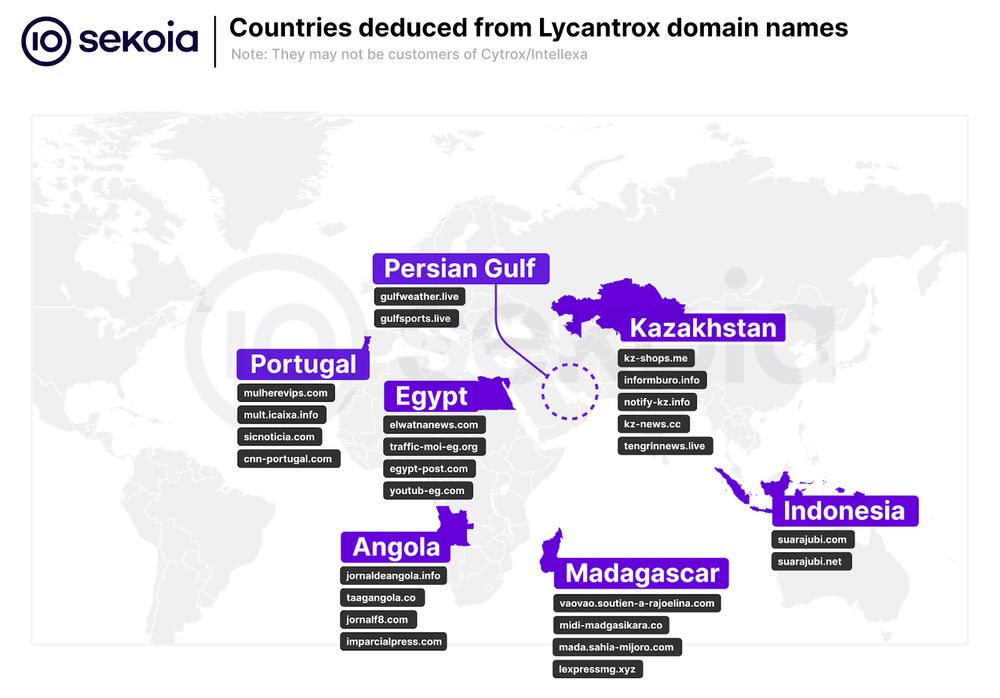
[Threat investigation alert 🚨] Predators for Hire: A Global Overview of Commercial Surveillance Vendors
➡️ blog.sekoia.io/predators-fo...
➡️ blog.sekoia.io/predators-fo...
September 2, 2025 at 9:55 AM
[Threat investigation alert 🚨] Predators for Hire: A Global Overview of Commercial Surveillance Vendors
➡️ blog.sekoia.io/predators-fo...
➡️ blog.sekoia.io/predators-fo...
No OS left behind. It happily infects Windows, macOS, and Linux systems.
Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
July 21, 2025 at 2:40 PM
No OS left behind. It happily infects Windows, macOS, and Linux systems.
Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
Unlike before, they're not impersonating a real crypto company. Instead, they have built a completely #fake brand from scratch: https://waventic[.]com.
🔥 Hot summer, sizzling crypto... and scammers turning up the heat 🔥
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.

July 21, 2025 at 2:40 PM
🔥 Hot summer, sizzling crypto... and scammers turning up the heat 🔥
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
🕵️ We also highlight multiple detection opportunities for AitM attacks in Microsoft Entra environments.
All technical details are available on our community GitHub: buff.ly/v5Y6amN
All technical details are available on our community GitHub: buff.ly/v5Y6amN

June 11, 2025 at 8:32 AM
🕵️ We also highlight multiple detection opportunities for AitM attacks in Microsoft Entra environments.
All technical details are available on our community GitHub: buff.ly/v5Y6amN
All technical details are available on our community GitHub: buff.ly/v5Y6amN
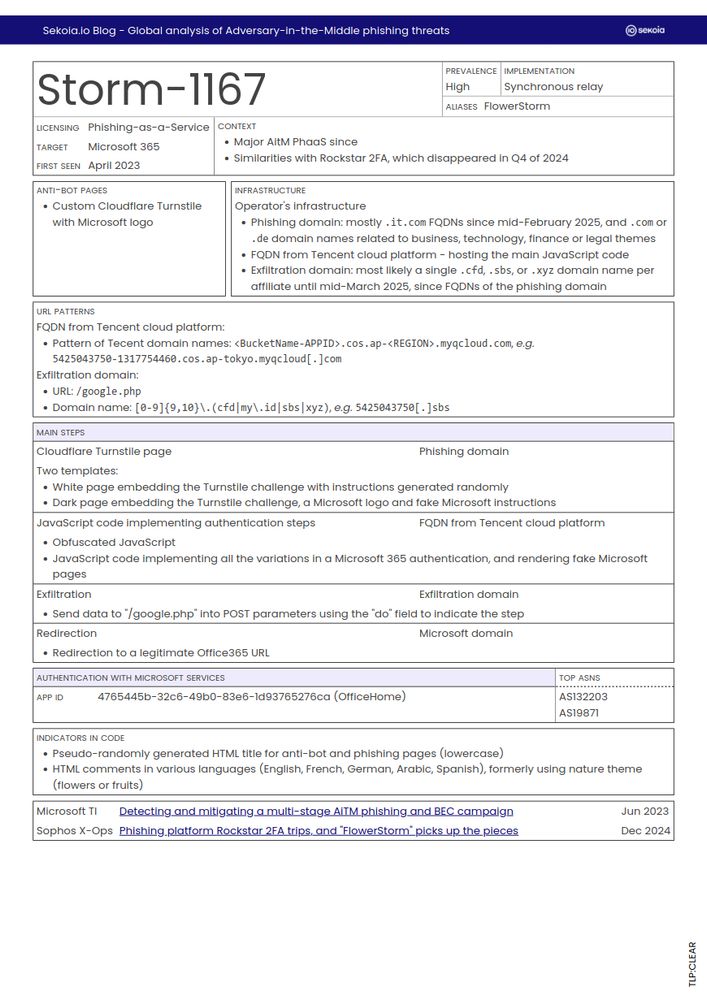
🎣 Leveraging our telemetry and proactive hunting, we ranked the most widespread AitM phishing kits - #Tycoon2FA, #Storm1167, #NakedPages, #Sneaky2FA, and more.
Additionally, the article includes summary sheets covering 11 AitM phishing kits.
Additionally, the article includes summary sheets covering 11 AitM phishing kits.

June 11, 2025 at 8:32 AM
🎣 Leveraging our telemetry and proactive hunting, we ranked the most widespread AitM phishing kits - #Tycoon2FA, #Storm1167, #NakedPages, #Sneaky2FA, and more.
Additionally, the article includes summary sheets covering 11 AitM phishing kits.
Additionally, the article includes summary sheets covering 11 AitM phishing kits.
🔍 Phishing-as-a-Service (#PhaaS) is driving a wave of large-scale, sophisticated attacks against organisations.
In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.
In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.

June 11, 2025 at 8:32 AM
🔍 Phishing-as-a-Service (#PhaaS) is driving a wave of large-scale, sophisticated attacks against organisations.
In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.
In our new blogpost, we provide an overview of the key techniques, tactics and social engineering schemes that cybercriminals use in AitM phishing attacks.
Our new report describes one of the latest observed infection chains (delivering #AsyncRAT) relying on the #Cloudflare tunnel infrastructure and the attacker’s #TTPs with a principal focus on detection opportunities.
blog.sekoia.io/detecting-mu...
blog.sekoia.io/detecting-mu...

April 23, 2025 at 8:33 AM
Our new report describes one of the latest observed infection chains (delivering #AsyncRAT) relying on the #Cloudflare tunnel infrastructure and the attacker’s #TTPs with a principal focus on detection opportunities.
blog.sekoia.io/detecting-mu...
blog.sekoia.io/detecting-mu...
Since the apparition of the #Interlock ransomware, the Sekoia #TDR team observed its operators evolving, improving their toolset (#LummaStealer and #BerserkStealer), and leveraging new techniques such as #ClickFix to deploy the ransomware payload.
blog.sekoia.io/interlock-ra...
blog.sekoia.io/interlock-ra...

April 16, 2025 at 9:13 AM
Since the apparition of the #Interlock ransomware, the Sekoia #TDR team observed its operators evolving, improving their toolset (#LummaStealer and #BerserkStealer), and leveraging new techniques such as #ClickFix to deploy the ransomware payload.
blog.sekoia.io/interlock-ra...
blog.sekoia.io/interlock-ra...
🎉 It's not about a CTI investigation or a Detection Engineering topic, but today we are happy to announce that Sekoia.io has raised €26m!
www.sekoia.io/en/presse/se...
www.sekoia.io/en/presse/se...

April 9, 2025 at 1:16 PM
🎉 It's not about a CTI investigation or a Detection Engineering topic, but today we are happy to announce that Sekoia.io has raised €26m!
www.sekoia.io/en/presse/se...
www.sekoia.io/en/presse/se...
🇰🇵 Sekoia #TDR team investigated a malicious campaign that employs fake job interview websites to deliver backdoors on Windows and macOS - #GolangGhost using #ClickFix tactic. Dubbed #ClickFake Interview, this campaign has been attributed to #Lazarus APT
blog.sekoia.io/clickfake-in...
blog.sekoia.io/clickfake-in...

March 31, 2025 at 9:27 AM
🇰🇵 Sekoia #TDR team investigated a malicious campaign that employs fake job interview websites to deliver backdoors on Windows and macOS - #GolangGhost using #ClickFix tactic. Dubbed #ClickFake Interview, this campaign has been attributed to #Lazarus APT
blog.sekoia.io/clickfake-in...
blog.sekoia.io/clickfake-in...
This new variant introduces additional interactions with the Binance Smart Chain, as well as new ClickFix lures displaying:
- a fake Cloudflare Turnstile with unusual web traffic
- a fake reCAPTCHA along with a DNS error
- a fake Cloudflare Turnstile with unusual web traffic
- a fake reCAPTCHA along with a DNS error

March 19, 2025 at 1:28 PM
This new variant introduces additional interactions with the Binance Smart Chain, as well as new ClickFix lures displaying:
- a fake Cloudflare Turnstile with unusual web traffic
- a fake reCAPTCHA along with a DNS error
- a fake Cloudflare Turnstile with unusual web traffic
- a fake reCAPTCHA along with a DNS error