

Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
Part 1: buff.ly/mpEzALh
Part 2: buff.ly/agWWCnp
Part3: buff.ly/Crz8rDh
🎄 Last part following Monday! 🎄

Part 1: buff.ly/mpEzALh
Part 2: buff.ly/agWWCnp
Part3: buff.ly/Crz8rDh
🎄 Last part following Monday! 🎄
Sekoia #TDR analysed a recent #Calisto (aka #ColdRiver #Star Blizzard) spear-phishing campaign aimed at Reporters sans frontières and other #Ukraine-supporting organisations.
blog.sekoia.io/ngo-reporter...

Sekoia #TDR analysed a recent #Calisto (aka #ColdRiver #Star Blizzard) spear-phishing campaign aimed at Reporters sans frontières and other #Ukraine-supporting organisations.
blog.sekoia.io/ngo-reporter...
@uybhys.bsky.social




@uybhys.bsky.social
blog.sekoia.io/phishing-cam...

blog.sekoia.io/phishing-cam...
Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...

Our Sekoia #TDR report breaks down the full infection chain and stealthy WebSocket C2 communications .
Read more 👉 blog.sekoia.io/transparentt...
blog.sekoia.io/userauthenti...

blog.sekoia.io/userauthenti...
blog.sekoia.io/polaredge-ba...

blog.sekoia.io/polaredge-ba...
Vous aimez faire des règles #Sigma et #Yara ? Vous adorez pivoter et traquer les infrastructures (C2) d’attaques des cybercriminels ?
Alors cette offre d’emploi est faite pour vous !
www.welcometothejungle.com/en/companies...

Vous aimez faire des règles #Sigma et #Yara ? Vous adorez pivoter et traquer les infrastructures (C2) d’attaques des cybercriminels ?
Alors cette offre d’emploi est faite pour vous !
www.welcometothejungle.com/en/companies...
Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...

Our latest #CTI investigation from Sekoia #TDR team uncovers a novel #smishing vector abusing Milesight industrial cellular router APIs to send phishing #SMS at scale.
blog.sekoia.io/silent-smish...
blog.sekoia.io/apt28-operat...

blog.sekoia.io/apt28-operat...
➡️ blog.sekoia.io/predators-fo...
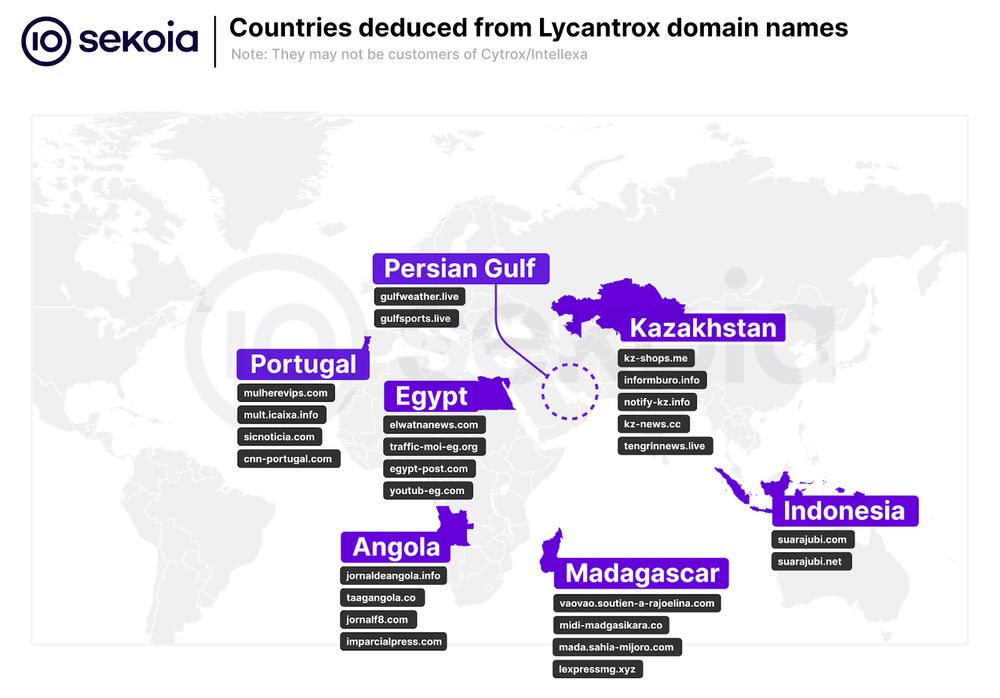
➡️ blog.sekoia.io/predators-fo...
Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.

Back in March, Sekoia #TDR team published a deep-dive report on a #Lazarus cluster we dubbed #ClickFake Interview, leveraging the #ClickFix technique in their #ContagiousInterview campaign.
blog.sekoia.io/the-sharp-ta...

blog.sekoia.io/the-sharp-ta...
blog.sekoia.io/vicioustrap-...

blog.sekoia.io/vicioustrap-...
blog.sekoia.io/detecting-mu...

blog.sekoia.io/detecting-mu...
blog.sekoia.io/interlock-ra...

blog.sekoia.io/interlock-ra...
www.sekoia.io/en/presse/se...

www.sekoia.io/en/presse/se...
blog.sekoia.io/clickfake-in...

blog.sekoia.io/clickfake-in...
buff.ly/vbiVbsN

buff.ly/vbiVbsN
buff.ly/vbiVbsN

buff.ly/vbiVbsN

https://buff.ly/4ibOEo8

https://buff.ly/4ibOEo8
We're thrilled to announce the release of the latest strategic report by Sekoia #TDR. This analysis highlights key cyber threats to the #financial sector in 2024.
https://buff.ly/3D3IZl7

We're thrilled to announce the release of the latest strategic report by Sekoia #TDR. This analysis highlights key cyber threats to the #financial sector in 2024.
https://buff.ly/3D3IZl7



