Matthias Kaiser
@matthiaskaiser.bsky.social
Java/Android Vulnerability Researcher. 0xACED. Ex-Apple. Posts are my own.
Reposted by Matthias Kaiser
Super cool potential ASLR leak involving dictionary hashes! googleprojectzero.blogspot.com/2025/09/poin...
Pointer leaks through pointer-keyed data structures
Posted by Jann Horn, Google Project Zero Introduction Some time in 2024, during a Project Zero team discussion, we were talking about how...
googleprojectzero.blogspot.com
September 26, 2025 at 5:07 PM
Super cool potential ASLR leak involving dictionary hashes! googleprojectzero.blogspot.com/2025/09/poin...
smalidea-ng: The moment your method references are indexed and your call-hierarchy returns within a second.

September 19, 2025 at 8:58 PM
smalidea-ng: The moment your method references are indexed and your call-hierarchy returns within a second.
Arrived in Berlin for @offensivecon.bsky.social. Don’t be shy and say hi! Looking forward to meet old and new friends👍
May 15, 2025 at 2:06 PM
Arrived in Berlin for @offensivecon.bsky.social. Don’t be shy and say hi! Looking forward to meet old and new friends👍
After many hours of development my Smalidea fork supports:
- parameters and variables with type information
- conditional breakpoints
- change parameters and variables via "expression" or "setValue". Quite happy with the results 😀
- parameters and variables with type information
- conditional breakpoints
- change parameters and variables via "expression" or "setValue". Quite happy with the results 😀
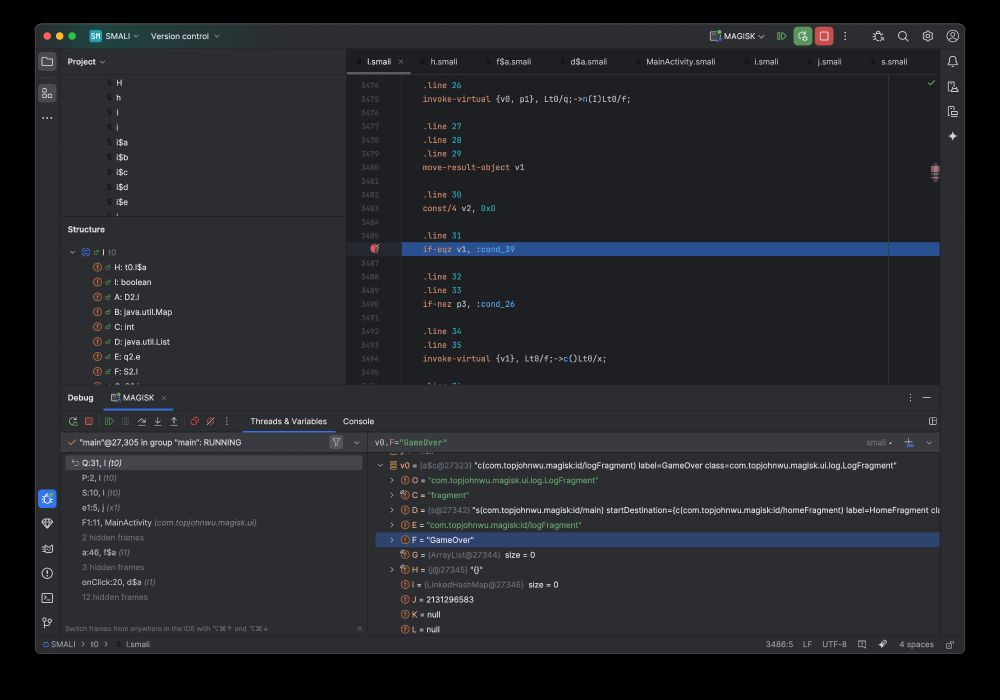
April 7, 2025 at 8:36 PM
After many hours of development my Smalidea fork supports:
- parameters and variables with type information
- conditional breakpoints
- change parameters and variables via "expression" or "setValue". Quite happy with the results 😀
- parameters and variables with type information
- conditional breakpoints
- change parameters and variables via "expression" or "setValue". Quite happy with the results 😀
Look Mom, smalidea (github.com/JesusFreke/s...) has new features: 1. Call-Hierarchy
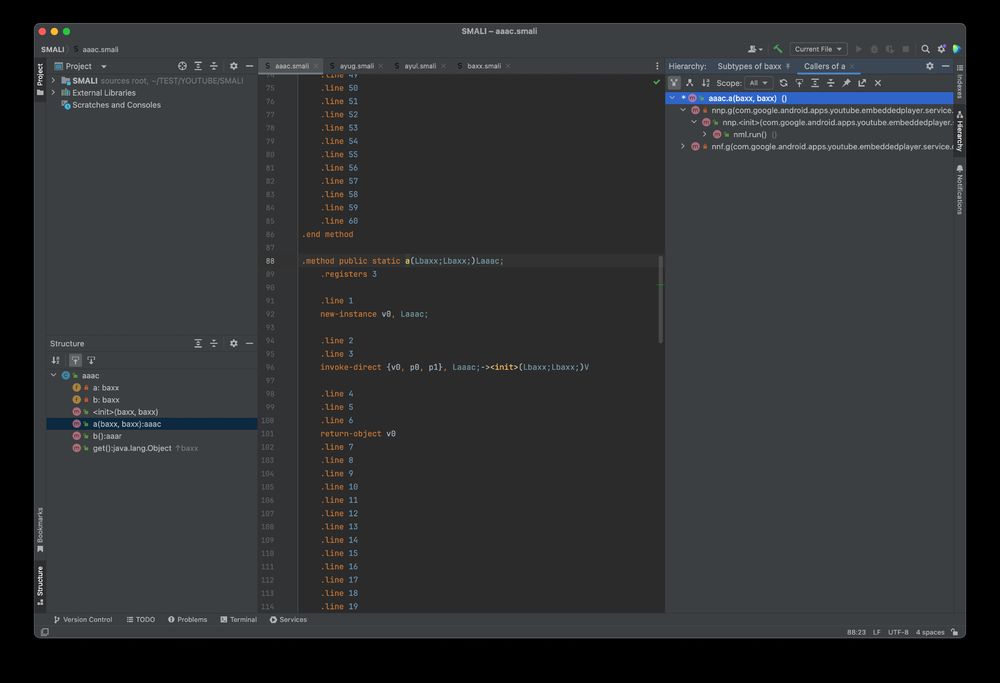
March 21, 2025 at 1:45 PM
Look Mom, smalidea (github.com/JesusFreke/s...) has new features: 1. Call-Hierarchy
Reposted by Matthias Kaiser
My first watchTowr post is out! It was my first take on a CMS solution and I was able to get some interesting pre-auth RCE chains on Kentico Xperience. 😎
labs.watchtowr.com/bypassing-au...
labs.watchtowr.com/bypassing-au...

Bypassing Authentication Like It’s The ‘90s - Pre-Auth RCE Chain(s) in Kentico Xperience CMS
I recently joined watchTowr, and it is, therefore, time - time for my first watchTowr Labs blogpost, previously teased in a tweet of a pre-auth RCE chain affecting some ‘unknown software’.
Joining th...
labs.watchtowr.com
March 17, 2025 at 12:45 PM
My first watchTowr post is out! It was my first take on a CMS solution and I was able to get some interesting pre-auth RCE chains on Kentico Xperience. 😎
labs.watchtowr.com/bypassing-au...
labs.watchtowr.com/bypassing-au...
Reposted by Matthias Kaiser
If you're using ruby-saml or omniauth-saml for SAML authentication make sure to update these libraries as fast as possible! Fixes for two critical authentication bypass vulnerabilities were published today (CVE-2025-25291 + CVE-2025-25292).
github.blog/security/sig...
github.blog/security/sig...
Sign in as anyone: Bypassing SAML SSO authentication with parser differentials
Critical authentication bypass vulnerabilities were discovered in ruby-saml up to version 1.17.0. See how they were uncovered.
github.blog
March 12, 2025 at 9:50 PM
If you're using ruby-saml or omniauth-saml for SAML authentication make sure to update these libraries as fast as possible! Fixes for two critical authentication bypass vulnerabilities were published today (CVE-2025-25291 + CVE-2025-25292).
github.blog/security/sig...
github.blog/security/sig...
Reposted by Matthias Kaiser
Finally had some time to put together a new blog post. It’s not groundbreaking, but it could still be interesting if you're into application security.
In our latest blog post, we dive into the hidden gems of the Java library c3p0 and explore how it can be leveraged in different exploitation scenarios. Happy reading! 😀
mogwailabs.de/en/blog/2025...
mogwailabs.de/en/blog/2025...

c3p0, you little rascal
The c3p0 library provides many useful exploitation primitives, deserving more attention
mogwailabs.de
February 28, 2025 at 9:56 AM
Finally had some time to put together a new blog post. It’s not groundbreaking, but it could still be interesting if you're into application security.
Reposted by Matthias Kaiser
New blog post on the abuse of the IDispatch COM interface to get unexpected objects loaded into a process. Demoed by using this to get arbitrary code execution in a PPL process. googleprojectzero.blogspot.com/2025/01/wind...
Windows Bug Class: Accessing Trapped COM Objects with IDispatch
Posted by James Forshaw, Google Project Zero Object orientated remoting technologies such as DCOM and .NET Remoting make it very easy ...
googleprojectzero.blogspot.com
January 30, 2025 at 6:37 PM
New blog post on the abuse of the IDispatch COM interface to get unexpected objects loaded into a process. Demoed by using this to get arbitrary code execution in a PPL process. googleprojectzero.blogspot.com/2025/01/wind...
Reposted by Matthias Kaiser
I'm happy to announce that I have recently joined watchTowr as a Principal Vulnerability Researcher. The break is over, it's time to do some new research 🫡
January 7, 2025 at 1:08 PM
I'm happy to announce that I have recently joined watchTowr as a Principal Vulnerability Researcher. The break is over, it's time to do some new research 🫡
Reposted by Matthias Kaiser
I just wrote a new blog post! This is how I (ab)used a jailed file write bug in Tomcat/Spring. Enjoy!
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties
Recently a past student came to me with a very interesting unauthenticated vulnerability in a Spring application that they were having a hard time exploiting...
srcincite.io
November 26, 2024 at 11:57 PM
I just wrote a new blog post! This is how I (ab)used a jailed file write bug in Tomcat/Spring. Enjoy!
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...

