techcrunch.com/2025/11/03/h...
#exploit #exploitation #zeroday #infosec #informationsecurity #cybersecurity

techcrunch.com/2025/11/03/h...
#exploit #exploitation #zeroday #infosec #informationsecurity #cybersecurity


popovicu.com/posts/making...
#programming #hardware #linux #blog

popovicu.com/posts/making...
#programming #hardware #linux #blog
www.synacktiv.com/en/publicati...

www.synacktiv.com/en/publicati...

www.usenix.org/system/files...
#infosec

www.usenix.org/system/files...
#infosec
In his latest blog post, Luis Casvella shows you how BYOVD can be used as a Reflective Rootkit Loader ! 🚀
➡️ blog.quarkslab.com/exploiting-l...

In his latest blog post, Luis Casvella shows you how BYOVD can be used as a Reflective Rootkit Loader ! 🚀
➡️ blog.quarkslab.com/exploiting-l...

qriousec.github.io/post/oob-angle
#infosec


qriousec.github.io/post/oob-angle
#infosec
github.com/google/syzka...
github.com/google/syzka...

A few training spots are still available if you want to join the party! 🎉
Unfortunately, trainings + conference packs are sold out
www.hexacon.fr/conference/s...

A few training spots are still available if you want to join the party! 🎉
Unfortunately, trainings + conference packs are sold out
www.hexacon.fr/conference/s...
Eh oui c’est la base… 🤷♂️
www.lemonde.fr/idees/articl...

Eh oui c’est la base… 🤷♂️
www.lemonde.fr/idees/articl...
asia.nikkei.com/Business/Tec...
You hide AI prompts in your paper that tell AI reviewers to say positive stuff (presumably both for public reviews and private analysis)
I wonder if Amazon sellers are already doing this?

asia.nikkei.com/Business/Tec...
You hide AI prompts in your paper that tell AI reviewers to say positive stuff (presumably both for public reviews and private analysis)
I wonder if Amazon sellers are already doing this?

Part 1: slavamoskvin.com/hunting-bugs...
Part 2: slavamoskvin.com/finding-bugs...
Part 3: slavamoskvin.com/finding-bugs...
#Linux #infosec


Part 1: slavamoskvin.com/hunting-bugs...
Part 2: slavamoskvin.com/finding-bugs...
Part 3: slavamoskvin.com/finding-bugs...
#Linux #infosec
Ghidra Data Types— When to Create Custom GDTs — Part 1 : medium.com/@clearblueja...
Creating Custom GDTs From Windows Headers — Part 2 : medium.com/@clearblueja...

Ghidra Data Types— When to Create Custom GDTs — Part 1 : medium.com/@clearblueja...
Creating Custom GDTs From Windows Headers — Part 2 : medium.com/@clearblueja...
watchfulip.github.io/28-12-24/tp-...
#embedded #infosec
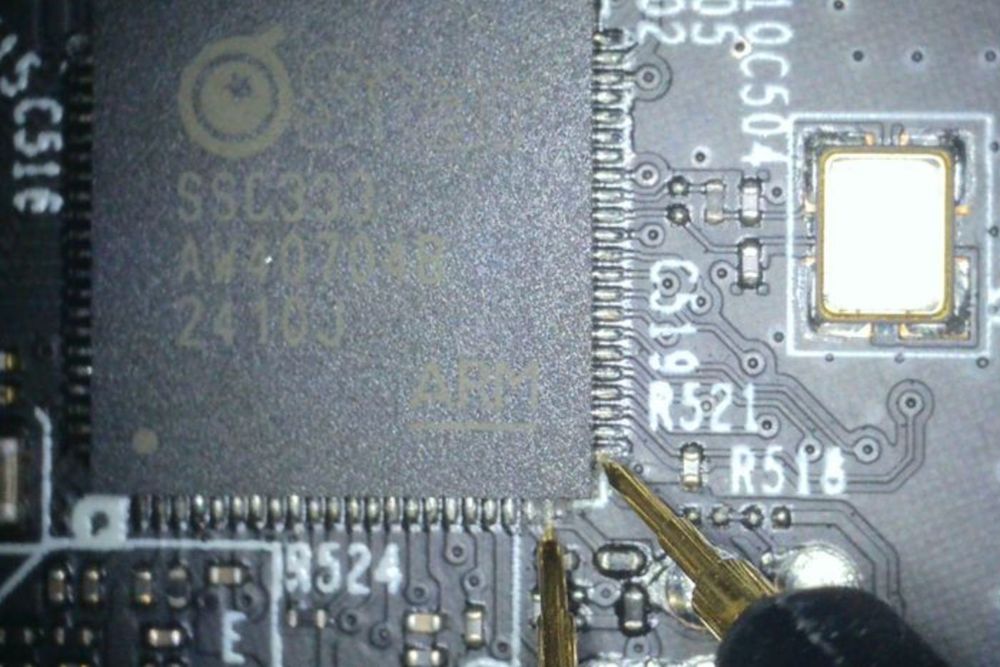
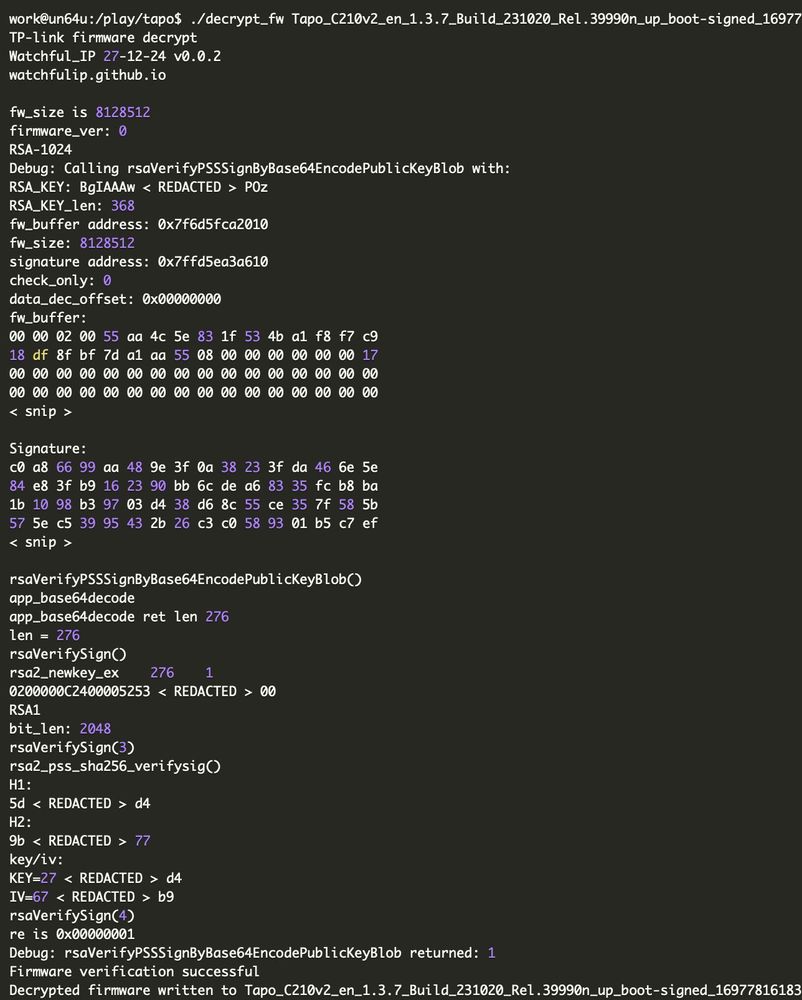
watchfulip.github.io/28-12-24/tp-...
#embedded #infosec


Finding and exploiting two vulnerabilities in AMD's UEFI firmware for fun and gaming.
A Christmas gift in February, brought to you by the amazing Gwaby 🫶
blog.quarkslab.com/being-overlo...
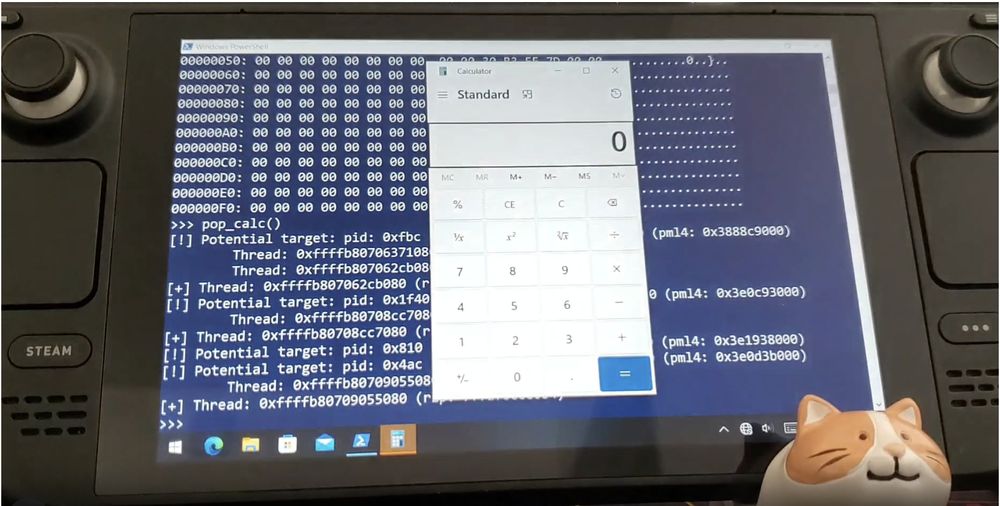
Finding and exploiting two vulnerabilities in AMD's UEFI firmware for fun and gaming.
A Christmas gift in February, brought to you by the amazing Gwaby 🫶
blog.quarkslab.com/being-overlo...

