Clément Labro
@itm4n.bsky.social
Pentest & Windows security research
🆕 New blog post!
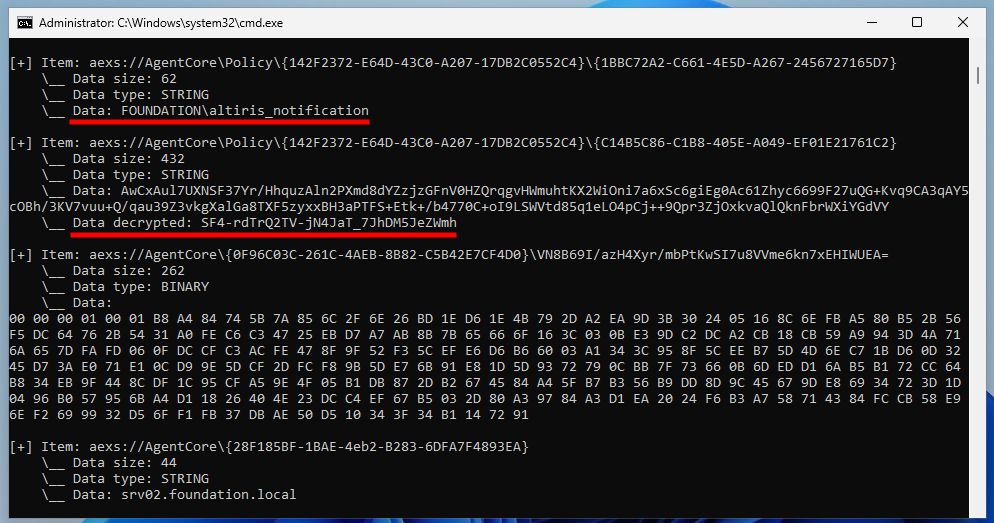
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
June 15, 2025 at 4:33 PM
🆕 New blog post!
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
🆕 New blog post!
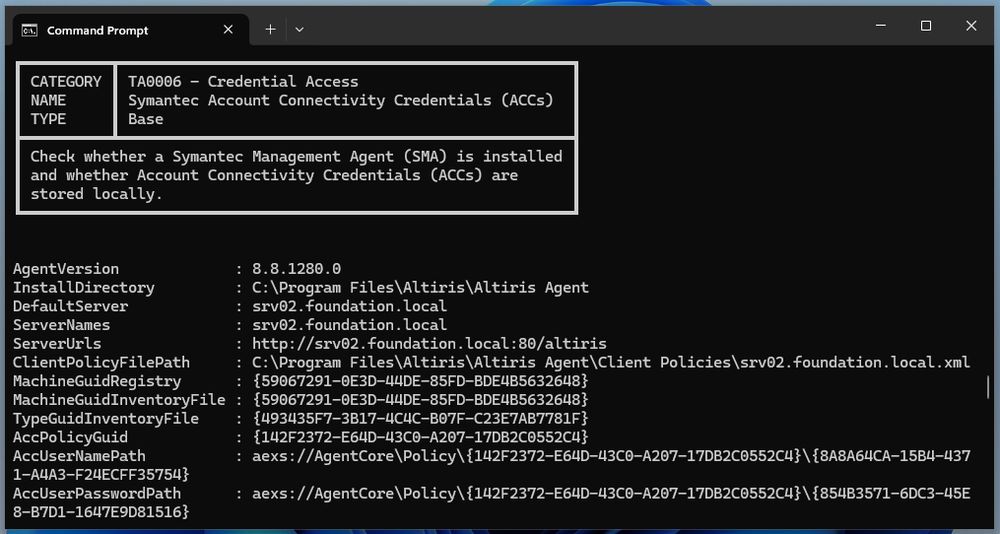
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
June 11, 2025 at 3:46 PM
🆕 New blog post!
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
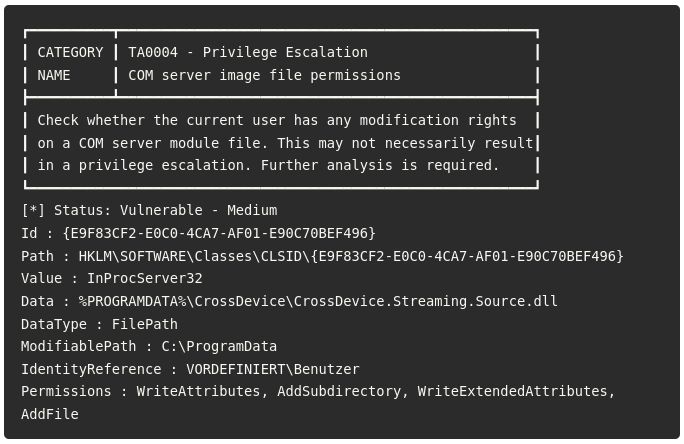
Another example of a Windows 0-day found with PrivescCheck. Congrats to Compass Security for investigating the issue and exploiting it. 👏
blog.compass-security.com/2025/04/3-mi...
blog.compass-security.com/2025/04/3-mi...
April 15, 2025 at 12:41 PM
Another example of a Windows 0-day found with PrivescCheck. Congrats to Compass Security for investigating the issue and exploiting it. 👏
blog.compass-security.com/2025/04/3-mi...
blog.compass-security.com/2025/04/3-mi...
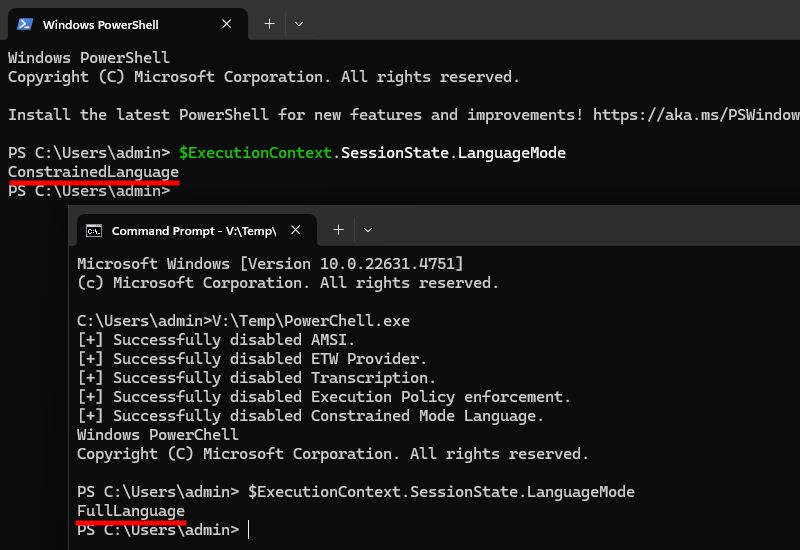
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
👉 blog.scrt.ch/2025/02/18/r...
February 19, 2025 at 9:13 AM
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
👉 blog.scrt.ch/2025/02/18/r...
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
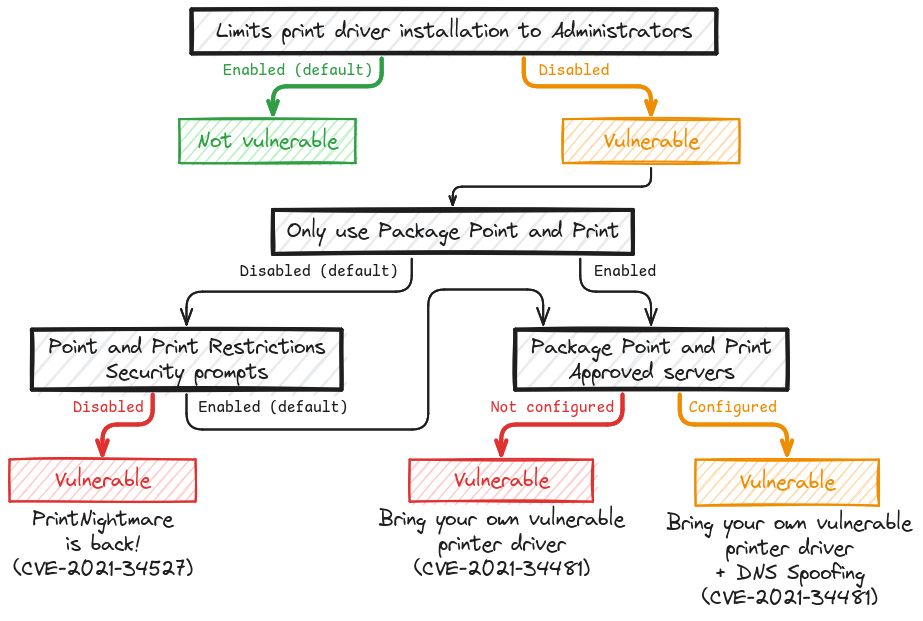
December 4, 2024 at 5:42 PM
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞

