Clément Labro
@itm4n.bsky.social
Pentest & Windows security research
🆕 New blog post!
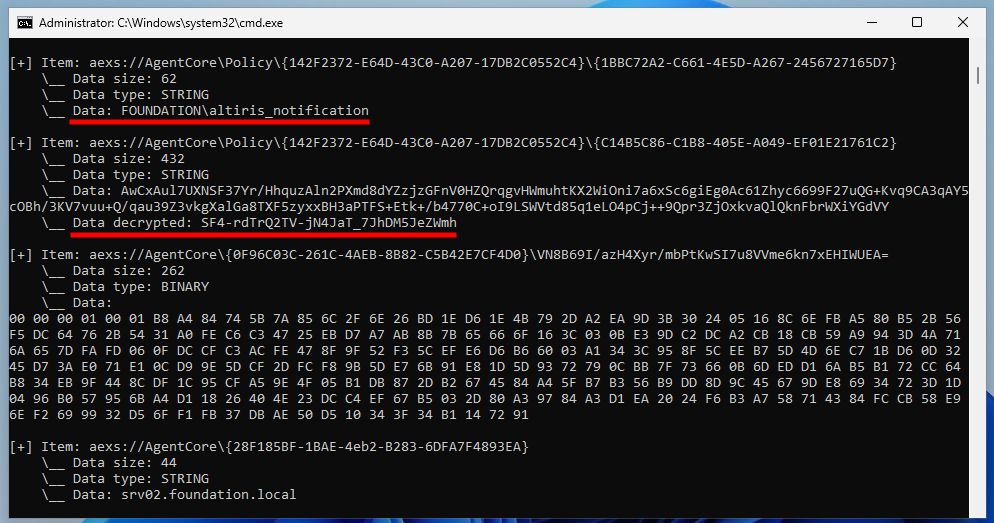
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
June 15, 2025 at 4:33 PM
🆕 New blog post!
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
🆕 New blog post!
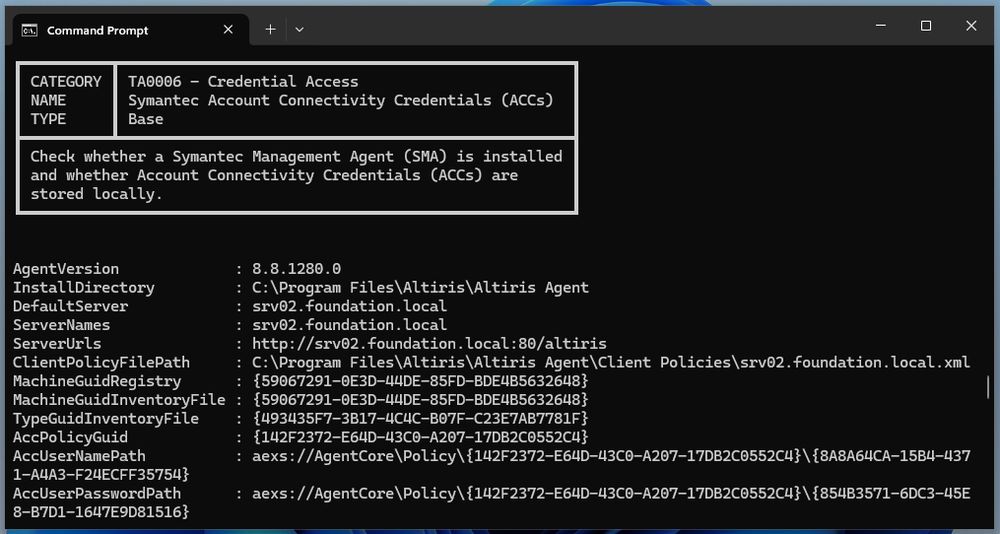
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
June 11, 2025 at 3:46 PM
🆕 New blog post!
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
🆕 New blog post! It's a rather short one, nothing crazy. Just wanted to share a random finding I made recently. 🤷♂️
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
Hijacking the Windows “MareBackup” Scheduled Task for Privilege Escalation – SCRT Team Blog
blog.scrt.ch
May 28, 2025 at 7:08 AM
🆕 New blog post! It's a rather short one, nothing crazy. Just wanted to share a random finding I made recently. 🤷♂️
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
This blog post brings automated Windows RPC research to the next level! 🔥
www.incendium.rocks/posts/Automa...
The writing quality is also excellent. 📝
#windows #research
www.incendium.rocks/posts/Automa...
The writing quality is also excellent. 📝
#windows #research
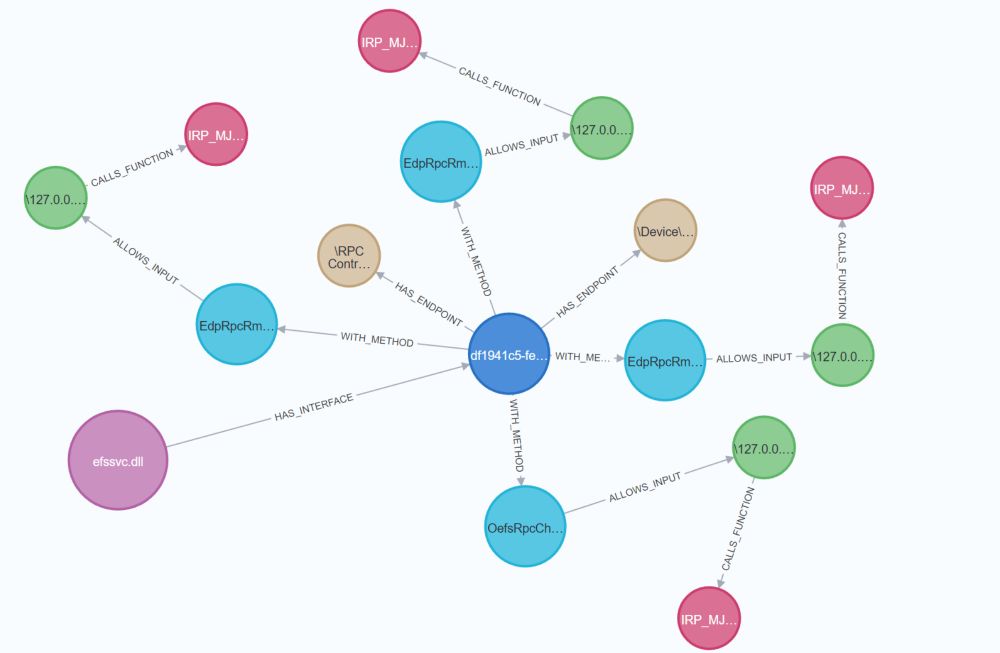
Automating MS-RPC vulnerability research
Diving into the MS-RPC protocol and how to automate vulnerability research using a fuzzing approach.
www.incendium.rocks
May 23, 2025 at 11:59 AM
This blog post brings automated Windows RPC research to the next level! 🔥
www.incendium.rocks/posts/Automa...
The writing quality is also excellent. 📝
#windows #research
www.incendium.rocks/posts/Automa...
The writing quality is also excellent. 📝
#windows #research
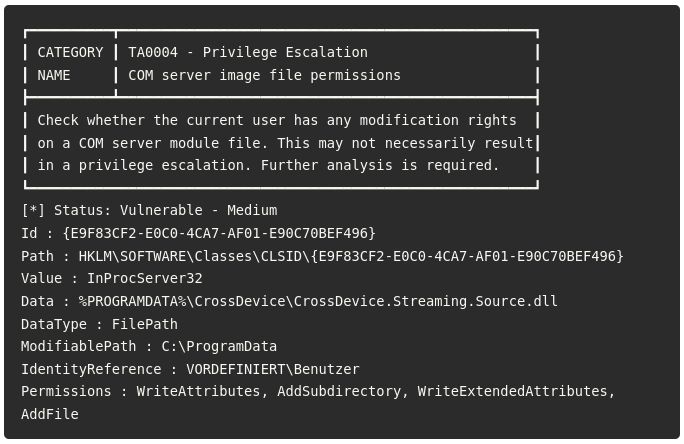
Another example of a Windows 0-day found with PrivescCheck. Congrats to Compass Security for investigating the issue and exploiting it. 👏
blog.compass-security.com/2025/04/3-mi...
blog.compass-security.com/2025/04/3-mi...
April 15, 2025 at 12:41 PM
Another example of a Windows 0-day found with PrivescCheck. Congrats to Compass Security for investigating the issue and exploiting it. 👏
blog.compass-security.com/2025/04/3-mi...
blog.compass-security.com/2025/04/3-mi...
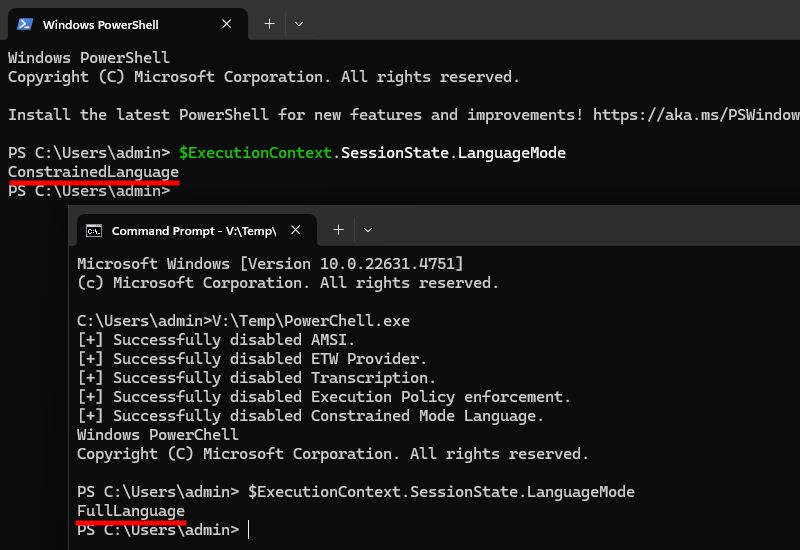
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
👉 blog.scrt.ch/2025/02/18/r...
February 19, 2025 at 9:13 AM
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
👉 blog.scrt.ch/2025/02/18/r...
Reposted by Clément Labro
New blog post on the abuse of the IDispatch COM interface to get unexpected objects loaded into a process. Demoed by using this to get arbitrary code execution in a PPL process. googleprojectzero.blogspot.com/2025/01/wind...
Windows Bug Class: Accessing Trapped COM Objects with IDispatch
Posted by James Forshaw, Google Project Zero Object orientated remoting technologies such as DCOM and .NET Remoting make it very easy ...
googleprojectzero.blogspot.com
January 30, 2025 at 6:37 PM
New blog post on the abuse of the IDispatch COM interface to get unexpected objects loaded into a process. Demoed by using this to get arbitrary code execution in a PPL process. googleprojectzero.blogspot.com/2025/01/wind...
Reposted by Clément Labro
In case if you wonder what broke #ProcessHollowing on Windows 11 24H2, I have something for you: hshrzd.wordpress.com/2025/01/27/p...

Process Hollowing on Windows 11 24H2
Process Hollowing (a.k.a. RunPE) is probably the oldest, and the most popular process impersonation technique (it allows to run a malicious executable under the cover of a benign process). It is us…
hshrzd.wordpress.com
January 26, 2025 at 11:55 PM
In case if you wonder what broke #ProcessHollowing on Windows 11 24H2, I have something for you: hshrzd.wordpress.com/2025/01/27/p...
Really great blog post about bypassing BitLocker using "PXE soft reboot" (even if PXE boot is disabled in the BIOS).
"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...
"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...

Windows BitLocker -- Screwed without a Screwdriver
Breaking up-to-date Windows 11 BitLocker encryption -- on-device but software-only
neodyme.io
January 20, 2025 at 10:03 AM
Really great blog post about bypassing BitLocker using "PXE soft reboot" (even if PXE boot is disabled in the BIOS).
"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...
"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...
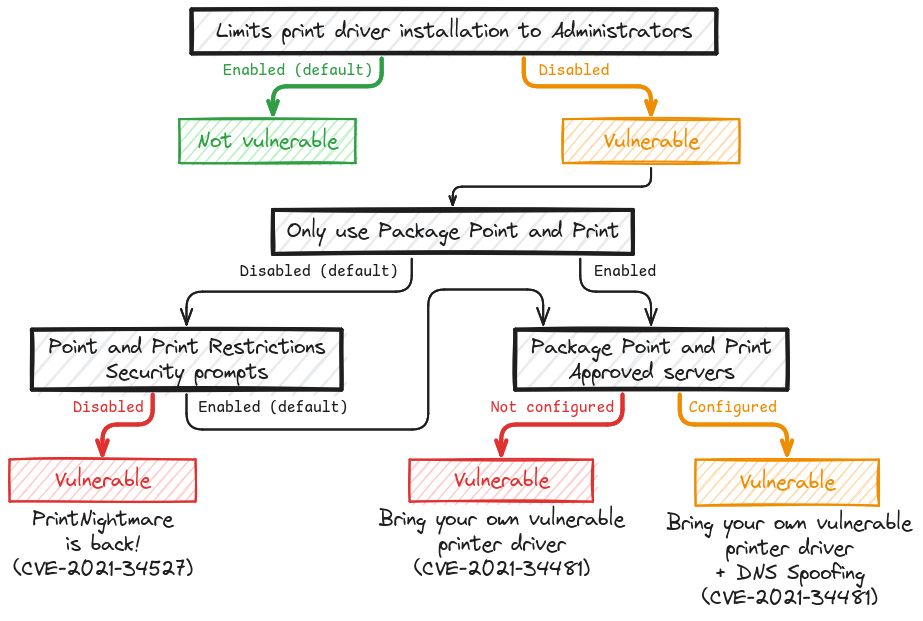
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
December 4, 2024 at 5:42 PM
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
Interestingly enough, MS disabled the "Use my Windows user account" checkbox when connecting to Wi-Fi on the lock screen to address CVE-2024-38143 in the August Patch Tuesday.
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
August 13, 2024—KB5041585 (OS Builds 22621.4037 and 22631.4037) - Microsoft SupportYour Privacy Choices Opt-Out Icon
support.microsoft.com
December 3, 2024 at 8:45 PM
Interestingly enough, MS disabled the "Use my Windows user account" checkbox when connecting to Wi-Fi on the lock screen to address CVE-2024-38143 in the August Patch Tuesday.
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
Reposted by Clément Labro
I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...

November 25, 2024 at 5:31 PM
I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
🆕 New blog post! "Exploiting KsecDD through Server Silos"
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
Exploiting KsecDD through Server Silos – SCRT Team Blog
blog.scrt.ch
November 11, 2024 at 1:40 PM
🆕 New blog post! "Exploiting KsecDD through Server Silos"
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
"A Trick, The Story of CVE-2024-26230" by k0shl
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
A trick, the story of CVE-2024-26230
whereisk0shl.top
April 10, 2024 at 6:57 PM
"A Trick, The Story of CVE-2024-26230" by k0shl
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
🆕 New PrivescCheck extended check!
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
GitHub - itm4n/PrivescCheck: Privilege Escalation Enumeration Script for Windows
Privilege Escalation Enumeration Script for Windows - itm4n/PrivescCheck
github.com
March 11, 2024 at 8:29 PM
🆕 New PrivescCheck extended check!
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
🆕 New blog post! "Extracting PEAP Credentials from Wired Network Profiles"
ℹ️ Nothing new under the sun, you might think?! Well, think twice, because this seemingly trivial task took an unexpected turn.
👉 itm4n.github.io/peap-credent...
ℹ️ Nothing new under the sun, you might think?! Well, think twice, because this seemingly trivial task took an unexpected turn.
👉 itm4n.github.io/peap-credent...

Extracting PEAP Credentials from Wired Network Profiles
A colleague of mine recently found himself in a situation where he had physical access to a Windows machine connected to a wired network using 802.1X and saved user credentials for the authentication....
itm4n.github.io
February 26, 2024 at 7:33 AM
🆕 New blog post! "Extracting PEAP Credentials from Wired Network Profiles"
ℹ️ Nothing new under the sun, you might think?! Well, think twice, because this seemingly trivial task took an unexpected turn.
👉 itm4n.github.io/peap-credent...
ℹ️ Nothing new under the sun, you might think?! Well, think twice, because this seemingly trivial task took an unexpected turn.
👉 itm4n.github.io/peap-credent...

