
Jamie Levy 🦉
@gleeda.bsky.social
@volatilityfoundation.org Core Dev | Art of Memory Forensics co-author | DFIR trainer and enthusiast | Director of Adversary Tactics @huntress.com
It’s raining, and feeding time, so what do we do? Sheep and goat dance set!!!
💣💥 turn up the volume! 🔊🔊
💣💥 turn up the volume! 🔊🔊
June 7, 2025 at 12:46 AM
It’s raining, and feeding time, so what do we do? Sheep and goat dance set!!!
💣💥 turn up the volume! 🔊🔊
💣💥 turn up the volume! 🔊🔊
When you've replied to a tweet from S1 a couple months ago asking for an updated url for a panel Chris Krebs was on, and wake up to a hate bot storm demanding his head. oh what a time to be alive 🫠

April 10, 2025 at 9:17 PM
When you've replied to a tweet from S1 a couple months ago asking for an updated url for a panel Chris Krebs was on, and wake up to a hate bot storm demanding his head. oh what a time to be alive 🫠
Hands on Keyboard broken down by hour of day

February 11, 2025 at 6:58 PM
Hands on Keyboard broken down by hour of day
Covering some details of how Star Blizzard's attack chain looks like

February 11, 2025 at 6:48 PM
Covering some details of how Star Blizzard's attack chain looks like
@laughingmantis.bsky.social and @johnhammond.bsky.social covering some phishing tactics seen in the last year

February 11, 2025 at 6:46 PM
@laughingmantis.bsky.social and @johnhammond.bsky.social covering some phishing tactics seen in the last year
@laughingmantis.bsky.social and @johnhammond.bsky.social covering the TTR of various ransomware attacks we've seen in the last year (Time-to-Ransom)

February 11, 2025 at 6:44 PM
@laughingmantis.bsky.social and @johnhammond.bsky.social covering the TTR of various ransomware attacks we've seen in the last year (Time-to-Ransom)
talking about how VERY NON STEALTHY ransomhub is

February 11, 2025 at 6:40 PM
talking about how VERY NON STEALTHY ransomhub is
a view of the most common ransomware actors we saw over the last year

February 11, 2025 at 6:35 PM
a view of the most common ransomware actors we saw over the last year
We looked at what was happening in a few different industries in our customer base

February 11, 2025 at 6:32 PM
We looked at what was happening in a few different industries in our customer base
looking at lots of infostealers

February 11, 2025 at 6:31 PM
looking at lots of infostealers
Some insights currently being discussed:

February 11, 2025 at 6:17 PM
Some insights currently being discussed:
Not today, satan! 🤣🤣🤣

December 20, 2024 at 6:22 PM
Not today, satan! 🤣🤣🤣
I think it might have been RSA 2016 actually
www.theregister.com/AMP/2016/03/...
www.csmonitor.com/layout/set/a...
www.theregister.com/AMP/2016/03/...
www.csmonitor.com/layout/set/a...

December 20, 2024 at 1:35 AM
I think it might have been RSA 2016 actually
www.theregister.com/AMP/2016/03/...
www.csmonitor.com/layout/set/a...
www.theregister.com/AMP/2016/03/...
www.csmonitor.com/layout/set/a...
When the items on your timeline align 😆

November 22, 2024 at 4:45 PM
When the items on your timeline align 😆
🔎 We did some reverse engineering to get a better idea of the capabilities of this malware. One interesting thing found was a Cyrillic language killswitch and a strange string encryption scheme 🤣

![def xor_decrypt(enc: str, key: int) -> str:
enc_bytes = bytes.fromhex(enc)
decrypted = []
for idx, val in enumerate(enc_bytes):
val ^= idx
val ^= ord("M")
val ^= key
decrypted.append(val)
return "".join([chr(i) for i in decrypted if i != 0])](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:rz2ctwpu6gc6opiy2qsbu4ja/bafkreibyfdvvuxrt4s4g3iq74zpx2uoum4nfajtofgpjstep2fr2ehcn7i@jpeg)
November 15, 2024 at 3:34 AM
🔎 We did some reverse engineering to get a better idea of the capabilities of this malware. One interesting thing found was a Cyrillic language killswitch and a strange string encryption scheme 🤣
The next day the threat actor returned, logging in via RDP, and within approximately 15 minutes, began executing several commands that deployed file encryption via previously identified network shares. 🦹
!["C:\Windows\SysWOW64\regsvr32.exe" /n "/i:-pass=[REDACTED] -enc=3 -uac -path=\\[REDACTED]\[SHARE]\ -uac=[REDACTED]" C:\locker.dll](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:rz2ctwpu6gc6opiy2qsbu4ja/bafkreibsirej53avhj7mwbq4vrdinfdeufiggivygluoyt6cqeqehqz6di@jpeg)
November 15, 2024 at 3:32 AM
The next day the threat actor returned, logging in via RDP, and within approximately 15 minutes, began executing several commands that deployed file encryption via previously identified network shares. 🦹
They then installed WinRAR and FileZilla in order to compress and exfiltrate files from the victims machines. 📂
The command used to compress files, shows the types of files they were interested in. They then uninstalled WinRAR and FileZilla.
The command used to compress files, shows the types of files they were interested in. They then uninstalled WinRAR and FileZilla.
![WinRAR.exe a -v5g -ed -r -tn1000d -m0 -mt5 -x*.rar -x*.JPEG -x*.RAW
-x*.PSD -x*.TIFF -x*.BMP -x*.GIF -x*.JPG -x*.MOV -x*.pst -x*.FIT
-x*.FIL -x*.mp4 -x*.avi -x*.mov -x*.mdb -x*.iso -x*.exe -x*.dll
-x*.bak -x*.msg -x*.png -x*.zip -x*.ai -x*.7z -x*.DPM -x*.log -x*.dxf
-x*.insp -x*.upd -x*.db -x*.dwg -x*.nc1 -x*.metadata -x*.dg -x*.inp
-x*.dat -x*.TIFF -x*.tiger -x*.pcp -x*.rvt -x*.rws -x*.nwc -x*.tif
-x*.frx -x*.dyf -x*.rcs -x*.diff C:\[redacted].rar
\\[redacted]\C$\Users\](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:rz2ctwpu6gc6opiy2qsbu4ja/bafkreicsks3x3rtrltyj5qqowhngufdof6x6yctv4beyqzvuvrru2hcxsy@jpeg)
November 15, 2024 at 3:31 AM
They then installed WinRAR and FileZilla in order to compress and exfiltrate files from the victims machines. 📂
The command used to compress files, shows the types of files they were interested in. They then uninstalled WinRAR and FileZilla.
The command used to compress files, shows the types of files they were interested in. They then uninstalled WinRAR and FileZilla.
🧵Today’s blogpost focuses on a newer ransomware variant named SafePay. Needless to say, ransomware sucks. When this new variant appeared, it gained our attention. 👀
Let’s dig into what happened and what makes it tick ⬇️:
Let’s dig into what happened and what makes it tick ⬇️:


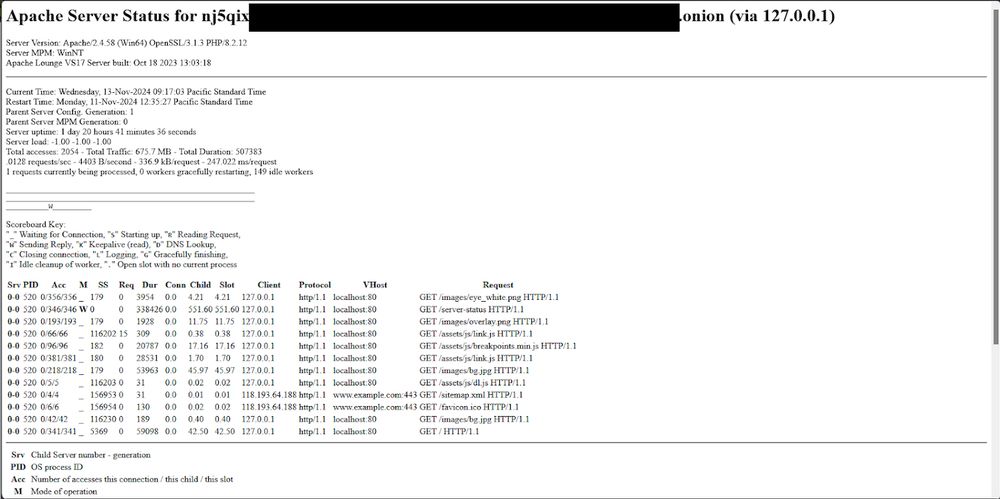
November 15, 2024 at 3:29 AM
🧵Today’s blogpost focuses on a newer ransomware variant named SafePay. Needless to say, ransomware sucks. When this new variant appeared, it gained our attention. 👀
Let’s dig into what happened and what makes it tick ⬇️:
Let’s dig into what happened and what makes it tick ⬇️:
Matt is going over the "not so helpful" helpful desk challenge (based on SlashAndGrab):




November 12, 2024 at 6:20 PM
Matt is going over the "not so helpful" helpful desk challenge (based on SlashAndGrab):
An example of some of the challenges and how they came about

November 12, 2024 at 6:14 PM
An example of some of the challenges and how they came about
Describing some of the methodology for building out some of the CTF challenges

November 12, 2024 at 6:12 PM
Describing some of the methodology for building out some of the CTF challenges
Now for the meaty part of the presentation!

November 12, 2024 at 6:09 PM
Now for the meaty part of the presentation!
Shout out to all the challenge authors and supporters

November 12, 2024 at 6:05 PM
Shout out to all the challenge authors and supporters



