

cloud.google.com/blog/topics/...
www.brighttalk.com/webcast/7451...

www.brighttalk.com/webcast/7451...



cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...

www.trendmicro.com/en_us/resear...
www.sygnia.co/blog/fire-an...
supportportal.juniper.net/s/article/20...
cloud.google.com/blog/topics/...
www.trendmicro.com/en_us/resear...
www.sygnia.co/blog/fire-an...
supportportal.juniper.net/s/article/20...
cloud.google.com/blog/topics/...
The campaign, active since mid-2024, aims to steal credentials, cookies & financial data.
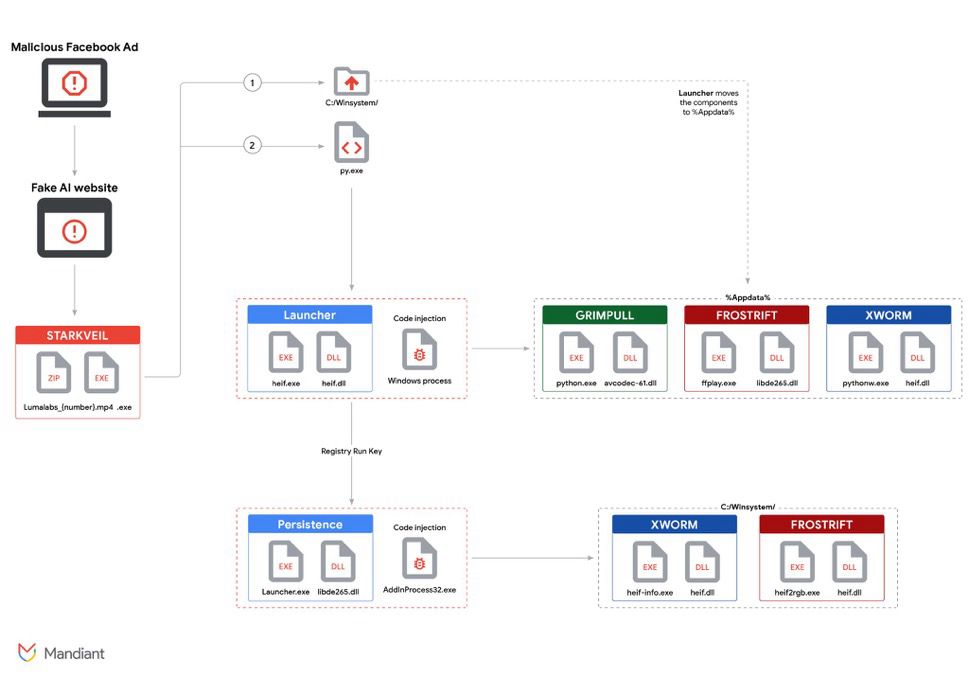
The campaign, active since mid-2024, aims to steal credentials, cookies & financial data.
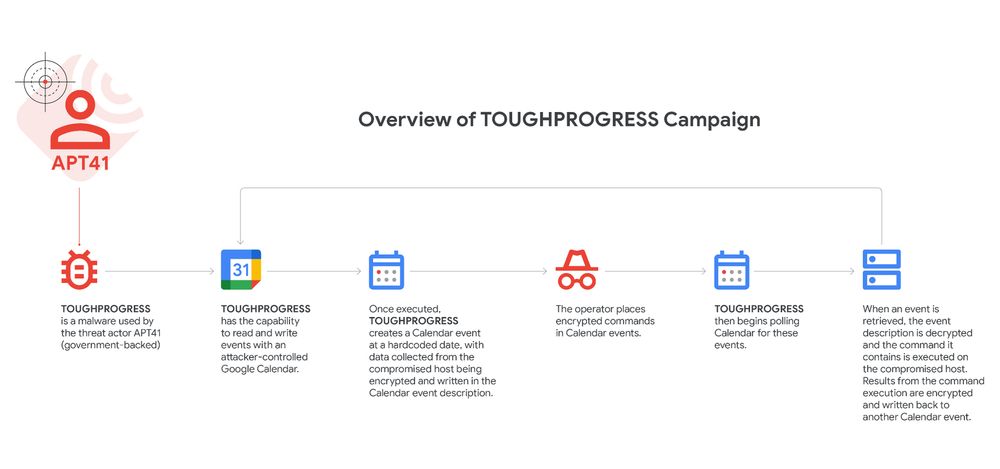
"Makes their jobs a lot harder," a person familiar with the matter told me, adding, "There's a possibility that more services might be limited or cut due to budget."
www.nextgov.com/cybersecurit...

"Makes their jobs a lot harder," a person familiar with the matter told me, adding, "There's a possibility that more services might be limited or cut due to budget."
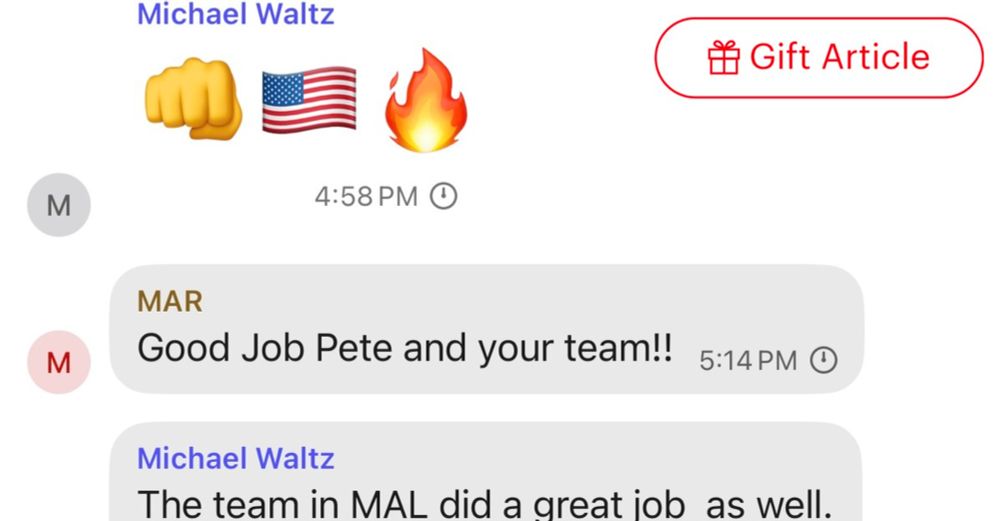
cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...
www.theatlantic.com/ideas/archiv...

www.theatlantic.com/ideas/archiv...

He was never going to get away.



He was never going to get away.

cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...
This includes several cyber committees, like CISA's advisory panel and the Cyber Safety Review Board, which was investigating Salt Typhoon.
That review is "dead," person familiar says.
www.documentcloud.org/documents/25...

This includes several cyber committees, like CISA's advisory panel and the Cyber Safety Review Board, which was investigating Salt Typhoon.
That review is "dead," person familiar says.
www.documentcloud.org/documents/25...
www.bloomberg.com/news/article...

www.bloomberg.com/news/article...
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...
cloud.google.com/blog/topics/...

cloud.google.com/blog/topics/...


