MITRE ATT&CK
@attack.mitre.org
MITRE ATT&CK® - A knowledge base for describing the behavior of adversaries. Replying/Following/Reposting ≠ endorsement.
Want to learn even more detail about v18? We'll be covering it in depth at ATT&CKcon 6.0 October 14-15. In-person tickets are onsite now at na.eventscloud.com/attackcon6, with virtual registration coming in early September.

ATT&CKcon 6.0
MITRE ATT&CKcon | October 14 - 15, 2025
na.eventscloud.com
August 19, 2025 at 4:51 PM
Want to learn even more detail about v18? We'll be covering it in depth at ATT&CKcon 6.0 October 14-15. In-person tickets are onsite now at na.eventscloud.com/attackcon6, with virtual registration coming in early September.
Wondering about tickets for ATT&CKcon 6.0? Details are coming soon.
July 7, 2025 at 3:02 PM
Wondering about tickets for ATT&CKcon 6.0? Details are coming soon.
Looking to attend in-person or virtually? Hang tight, ticket sales will be announced in the coming months.
June 3, 2025 at 3:11 PM
Looking to attend in-person or virtually? Hang tight, ticket sales will be announced in the coming months.
Interested in sponsoring ATT&CKcon? We have a couple slots left, and you can find out more at na.eventscloud.com/attackcon6.

ATT&CKcon 6.0
MITRE ATT&CKcon | October 14 - 15, 2025
na.eventscloud.com
June 3, 2025 at 3:11 PM
Interested in sponsoring ATT&CKcon? We have a couple slots left, and you can find out more at na.eventscloud.com/attackcon6.
We're looking for what's practical, what's aspirational, and what you should never ever do with ATT&CK. We're looking to hear from the community on any and all applications of ATT&CK. From managers to operators, if you're using ATT&CK we want to hear from you.
June 3, 2025 at 3:11 PM
We're looking for what's practical, what's aspirational, and what you should never ever do with ATT&CK. We're looking to hear from the community on any and all applications of ATT&CK. From managers to operators, if you're using ATT&CK we want to hear from you.
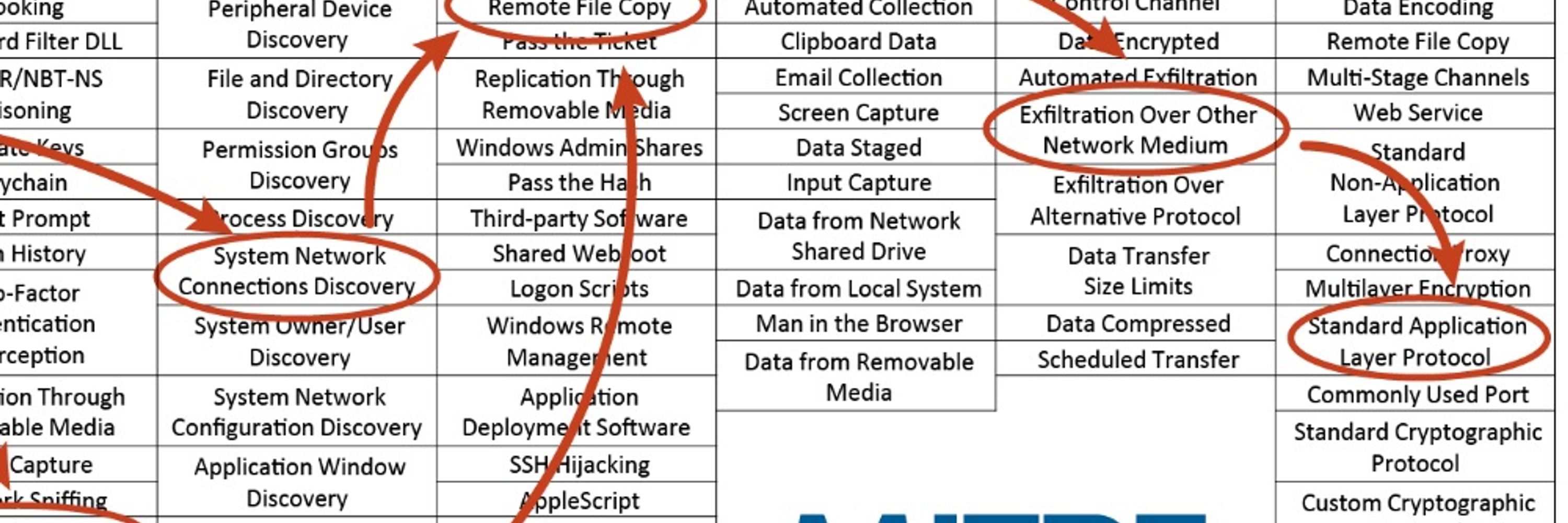
And make sure to check out the ESXi material on ATT&CK including T1675 cloud.google.com/blog/topics/...
And see the entire ATT&CK v17 release for more information medium.com/mitre-attack...
And see the entire ATT&CK v17 release for more information medium.com/mitre-attack...
May 8, 2025 at 12:32 PM
And make sure to check out the ESXi material on ATT&CK including T1675 cloud.google.com/blog/topics/...
And see the entire ATT&CK v17 release for more information medium.com/mitre-attack...
And see the entire ATT&CK v17 release for more information medium.com/mitre-attack...
Read up on Google’s reporting: cloud.google.com/blog/topics/...
VMware ESXi Zero-Day Used by Chinese Espionage Actor to Perform Privileged Guest Operations on Compromised Hypervisors | Mandiant | Google Cloud Blog
cloud.google.com
May 8, 2025 at 12:32 PM
Read up on Google’s reporting: cloud.google.com/blog/topics/...
Google’s reporting details UNC3886, Chinese cyber espionage group, using a zero-day vulnerability that enabled the execution of privileged commands across guest virtual machines without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs.
May 8, 2025 at 12:32 PM
Google’s reporting details UNC3886, Chinese cyber espionage group, using a zero-day vulnerability that enabled the execution of privileged commands across guest virtual machines without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs.
T1675 describes activity in which an adversary abuses ESXi admin services to execute commands on guest machines.
May 8, 2025 at 12:32 PM
T1675 describes activity in which an adversary abuses ESXi admin services to execute commands on guest machines.
One of the big updates for ATT&CK v17 was the new platform ESXi which reflects the rise in attacks on virtualization infrastructure. The technique we’re spotlighting today is new to ATT&CK: T1675 ESXi Administration Command attack.mitre.org/techniques/T...
ESXi Administration Command, Technique T1675 - Enterprise | MITRE ATT&CK®
attack.mitre.org
May 8, 2025 at 12:32 PM
One of the big updates for ATT&CK v17 was the new platform ESXi which reflects the rise in attacks on virtualization infrastructure. The technique we’re spotlighting today is new to ATT&CK: T1675 ESXi Administration Command attack.mitre.org/techniques/T...
We’re currently reading Google’s reporting on VMware ESXi Zero-Day Used by Chinese Espionage Actor to Perform Privileged Guest Operations on Compromised Hypervisors cloud.google.com/blog/topics/...

VMware ESXi Zero-Day Used by Chinese Espionage Actor to Perform Privileged Guest Operations on Compromised Hypervisors | Mandiant | Google Cloud Blog
cloud.google.com
May 8, 2025 at 12:32 PM
We’re currently reading Google’s reporting on VMware ESXi Zero-Day Used by Chinese Espionage Actor to Perform Privileged Guest Operations on Compromised Hypervisors cloud.google.com/blog/topics/...
Read Volexity’s reporting here www.volexity.com/blog/2025/04... and be sure to browse the relevant procedures, mitigations, and detections at the ATT&CK technique page: attack.mitre.org/techniques/T...
Phishing for Codes: Russian Threat Actors Target Microsoft 365 OAuth Workflows
Since early March 2025, Volexity has observed multiple suspected Russian threat actors conducting highly targeted social engineering operations aimed at gaining access to the Microsoft 365 (M365) acco...
www.volexity.com
April 30, 2025 at 1:22 PM
Read Volexity’s reporting here www.volexity.com/blog/2025/04... and be sure to browse the relevant procedures, mitigations, and detections at the ATT&CK technique page: attack.mitre.org/techniques/T...
Signal is a powerful end-to-end encrypted chat app. At the end of the day, that doesn’t help at all when you’re being spearphished. In fact, the lack of visibility and detection inherent in an encrypted chat app could even potentially hurt. That’s a wrinkle requiring vigilance on all parts.
April 30, 2025 at 1:22 PM
Signal is a powerful end-to-end encrypted chat app. At the end of the day, that doesn’t help at all when you’re being spearphished. In fact, the lack of visibility and detection inherent in an encrypted chat app could even potentially hurt. That’s a wrinkle requiring vigilance on all parts.

