MITRE ATT&CK
@attack.mitre.org
MITRE ATT&CK® - A knowledge base for describing the behavior of adversaries. Replying/Following/Reposting ≠ endorsement.
Virtual registration for ATT&CKcon 6.0 is open! We hope you'll chose to join us in person at ATT&CK's home in McLean, VA October 14-15... But if you can't, catch the action for free online by registering at na.eventscloud.com/attackcon6/. Catch all of our talks & some exclusive online only content.

September 3, 2025 at 3:53 PM
Virtual registration for ATT&CKcon 6.0 is open! We hope you'll chose to join us in person at ATT&CK's home in McLean, VA October 14-15... But if you can't, catch the action for free online by registering at na.eventscloud.com/attackcon6/. Catch all of our talks & some exclusive online only content.
The ATT&CKcon 6.0 talk lineup is now live! Check out our fabulous group of speakers, or pick up a ticket to join us October 14-15 in McLean, VA at na.eventscloud.com/attackcon6. Only able to join us virtually? Hang tight, virtual registration opens September 3rd.

August 26, 2025 at 5:06 PM
The ATT&CKcon 6.0 talk lineup is now live! Check out our fabulous group of speakers, or pick up a ticket to join us October 14-15 in McLean, VA at na.eventscloud.com/attackcon6. Only able to join us virtually? Hang tight, virtual registration opens September 3rd.
Are you ready to celebrate National Chocolate Day this October 28th? We will be by releasing ATT&CK v18, our next version of MITRE ATT&CK!
We'll be releasing our usual updates to Techniques and Groups, but check out some big defensive changes on the way in this release (medium.com/mitre-attack...).
We'll be releasing our usual updates to Techniques and Groups, but check out some big defensive changes on the way in this release (medium.com/mitre-attack...).

August 19, 2025 at 4:51 PM
Are you ready to celebrate National Chocolate Day this October 28th? We will be by releasing ATT&CK v18, our next version of MITRE ATT&CK!
We'll be releasing our usual updates to Techniques and Groups, but check out some big defensive changes on the way in this release (medium.com/mitre-attack...).
We'll be releasing our usual updates to Techniques and Groups, but check out some big defensive changes on the way in this release (medium.com/mitre-attack...).
We are excited to announce our ATT&CKcon 6.0 keynote, Lillian Teng! Lillian's worn numerous hats in cyber at NCIS, FBI, Yahoo, and Capital One and has served with the KC7 Foundation, GirlSecurity, and LEAP.
Want to also join us on stage? CFP closes Wed night! www.openconf.org/ATTACKCON2025.
Want to also join us on stage? CFP closes Wed night! www.openconf.org/ATTACKCON2025.

July 7, 2025 at 3:02 PM
We are excited to announce our ATT&CKcon 6.0 keynote, Lillian Teng! Lillian's worn numerous hats in cyber at NCIS, FBI, Yahoo, and Capital One and has served with the KC7 Foundation, GirlSecurity, and LEAP.
Want to also join us on stage? CFP closes Wed night! www.openconf.org/ATTACKCON2025.
Want to also join us on stage? CFP closes Wed night! www.openconf.org/ATTACKCON2025.
The MITRE ATT&CKcon 6.0 CFP is now open! Are you interested in joining us on the ATT&CKcon stage in McLean, VA October 14-15, 2025? Pitch us on your best ATT&CK related talk! Our CFP will close on July 9th at 8pm ET sharp, so get those proposals started.
www.openconf.org/ATTACKCON202...
www.openconf.org/ATTACKCON202...

June 3, 2025 at 3:11 PM
The MITRE ATT&CKcon 6.0 CFP is now open! Are you interested in joining us on the ATT&CKcon stage in McLean, VA October 14-15, 2025? Pitch us on your best ATT&CK related talk! Our CFP will close on July 9th at 8pm ET sharp, so get those proposals started.
www.openconf.org/ATTACKCON202...
www.openconf.org/ATTACKCON202...
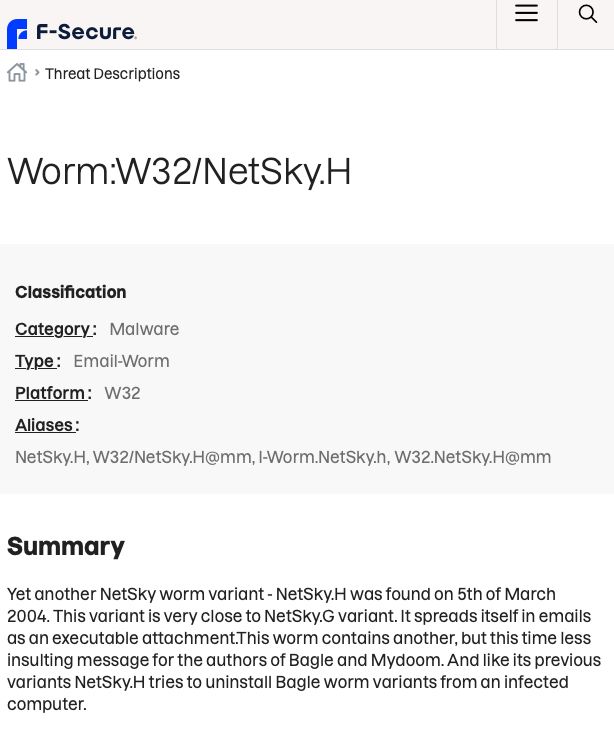
An adversary who finds a vulnerable target but wants to be the only threat actor on that machine might take similar actions like disabling vulnerable services or removing malware already on the device www.f-secure.com/v-descs/nets...
April 24, 2025 at 5:00 PM
An adversary who finds a vulnerable target but wants to be the only threat actor on that machine might take similar actions like disabling vulnerable services or removing malware already on the device www.f-secure.com/v-descs/nets...
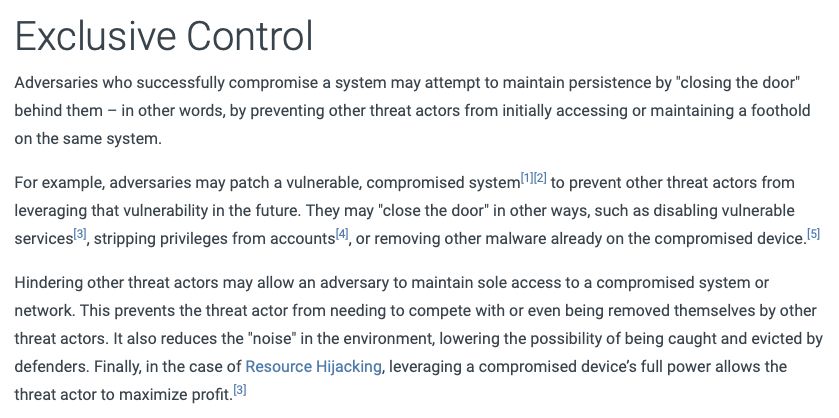
Exclusive Control is a persistence technique in which an adversary prevents other threat actors from accessing or maintaining a foothold on the same system as them.
April 24, 2025 at 4:59 PM
Exclusive Control is a persistence technique in which an adversary prevents other threat actors from accessing or maintaining a foothold on the same system as them.
Find mitigation and detection strategies from ATT&CK: attack.mitre.org/techniques/T...

April 2, 2025 at 2:00 PM
Find mitigation and detection strategies from ATT&CK: attack.mitre.org/techniques/T...
There’s a lot of meat on the bone in this report. While we’re focusing on the deployment of the backdoor, it’s also worth reading the section on FamousSparrow and Salt Typhoon for an interesting and important look at the intricacies — and sometimes the frustrating opacity — in CTI attribution

April 2, 2025 at 1:59 PM
There’s a lot of meat on the bone in this report. While we’re focusing on the deployment of the backdoor, it’s also worth reading the section on FamousSparrow and Salt Typhoon for an interesting and important look at the intricacies — and sometimes the frustrating opacity — in CTI attribution
Today we're launching a new system where the public can help us develop the next ATT&CK release through Macrotechnique Refinement. To start refining FUZZYSNUGGLYDUCK, click here: attack.mitre.org/macro-techni.... Fabulous prizes await success.

April 1, 2025 at 12:44 PM
Today we're launching a new system where the public can help us develop the next ATT&CK release through Macrotechnique Refinement. To start refining FUZZYSNUGGLYDUCK, click here: attack.mitre.org/macro-techni.... Fabulous prizes await success.
Celebrate April 22nd with ATT&CK v17!
The next version of ATT&CK is almost here, with new content related to the ESXi hypervisor, broad improvements to defenses, and updates to techniques, groups, and software across the framework.
The next version of ATT&CK is almost here, with new content related to the ESXi hypervisor, broad improvements to defenses, and updates to techniques, groups, and software across the framework.

March 4, 2025 at 4:37 PM
Celebrate April 22nd with ATT&CK v17!
The next version of ATT&CK is almost here, with new content related to the ESXi hypervisor, broad improvements to defenses, and updates to techniques, groups, and software across the framework.
The next version of ATT&CK is almost here, with new content related to the ESXi hypervisor, broad improvements to defenses, and updates to techniques, groups, and software across the framework.
October 2023 🙂
At least if you’re using Mobile ATT&CK.
At least if you’re using Mobile ATT&CK.

January 27, 2025 at 4:23 PM
October 2023 🙂
At least if you’re using Mobile ATT&CK.
At least if you’re using Mobile ATT&CK.
ATT&CKcon 5.0 is back up and running with day 2 keynote,
CISA's Mark Singer. Mark's kicking off the day with some tales of CISA's view of threats. Join us for a packed day of ATT&CK insights at mitre.brandlive.com/ATTACKCon-5-0. #attackcon
CISA's Mark Singer. Mark's kicking off the day with some tales of CISA's view of threats. Join us for a packed day of ATT&CK insights at mitre.brandlive.com/ATTACKCon-5-0. #attackcon

October 23, 2024 at 1:16 PM
ATT&CKcon 5.0 is back up and running with day 2 keynote,
CISA's Mark Singer. Mark's kicking off the day with some tales of CISA's view of threats. Join us for a packed day of ATT&CK insights at mitre.brandlive.com/ATTACKCon-5-0. #attackcon
CISA's Mark Singer. Mark's kicking off the day with some tales of CISA's view of threats. Join us for a packed day of ATT&CK insights at mitre.brandlive.com/ATTACKCon-5-0. #attackcon
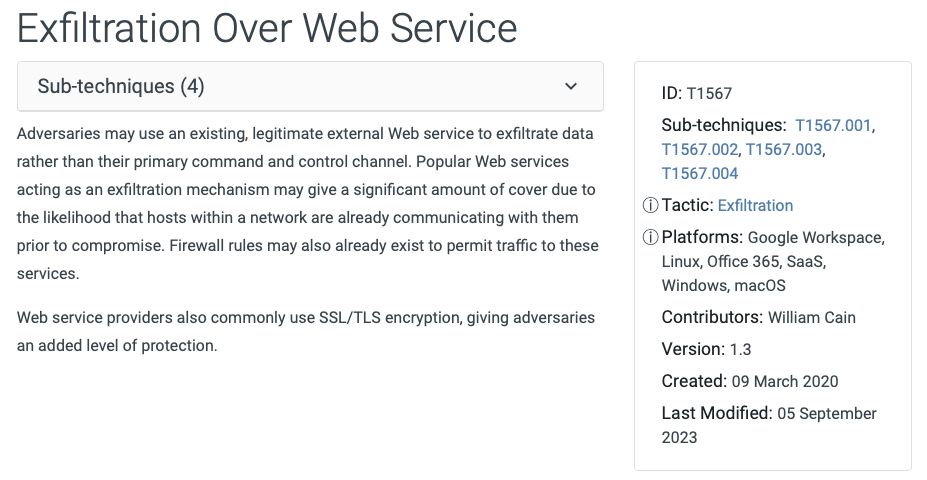
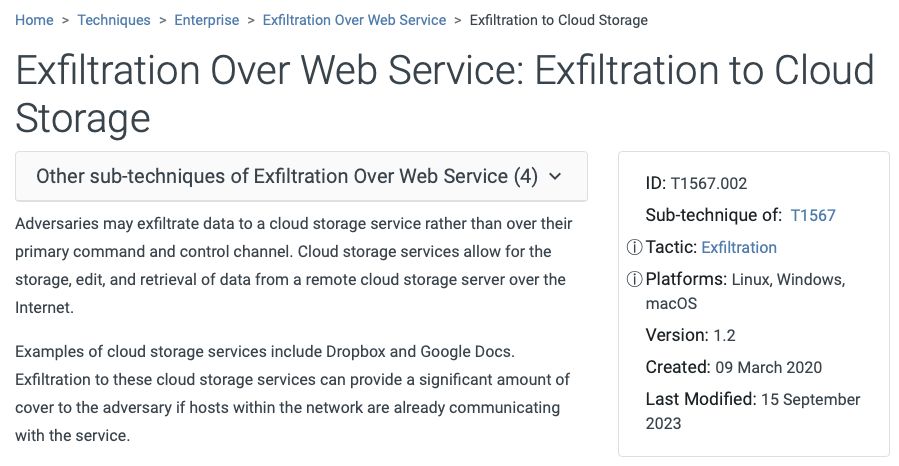
Threat actors gain cover by using popular services like OneDrive especially if the network is already communicating with the service and if security tools already permit traffic going there. This of course goes way beyond OneDrive: Check out attack.mitre.org/techniques/T...

August 28, 2024 at 3:47 PM
Threat actors gain cover by using popular services like OneDrive especially if the network is already communicating with the service and if security tools already permit traffic going there. This of course goes way beyond OneDrive: Check out attack.mitre.org/techniques/T...
This maps right to T1567.002 attack.mitre.org/techniques/T... Taking this route is advantageous for numerous reasons including that the ready-built C2 often looks familiar compared to a threat actor’s primary command and control infrastructure.
August 28, 2024 at 3:46 PM
This maps right to T1567.002 attack.mitre.org/techniques/T... Taking this route is advantageous for numerous reasons including that the ready-built C2 often looks familiar compared to a threat actor’s primary command and control infrastructure.
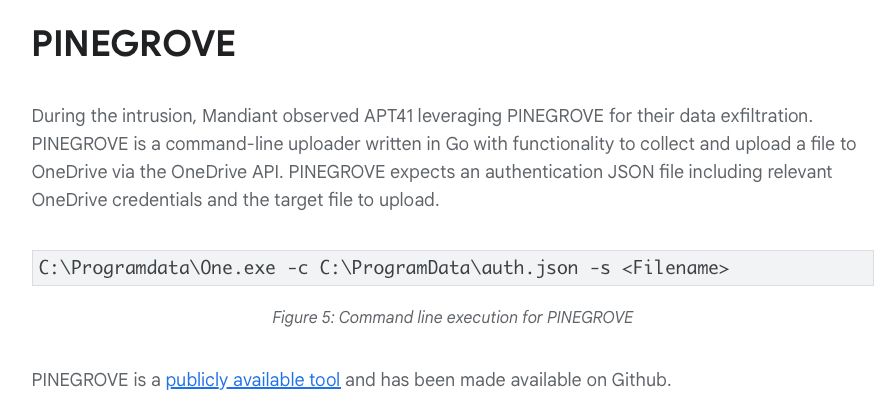
So, APT41 is in a network, they’ve accessed sensitive data, and now they want to exfiltrate. How? Why not just use what the rest of us already use?: APT41 copies data and then smuggles it out via Microsoft OneDrive.
August 28, 2024 at 3:45 PM
So, APT41 is in a network, they’ve accessed sensitive data, and now they want to exfiltrate. How? Why not just use what the rest of us already use?: APT41 copies data and then smuggles it out via Microsoft OneDrive.
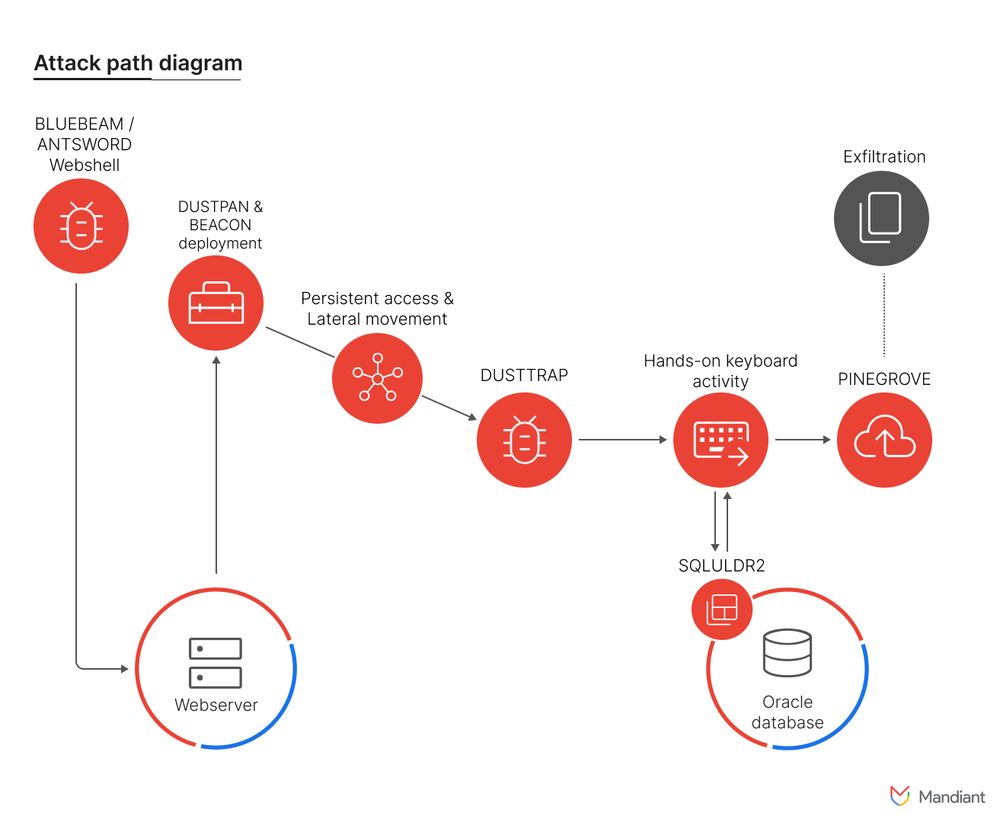
We’re looking at the recent Mandiant report on APT41 successfully targeting multiple industries, countries, and regions in a lengthy campaign enabling them to extract sensitive data over an extended period. Phew. cloud.google.com/blog/topics/...
August 28, 2024 at 3:45 PM
We’re looking at the recent Mandiant report on APT41 successfully targeting multiple industries, countries, and regions in a lengthy campaign enabling them to extract sensitive data over an extended period. Phew. cloud.google.com/blog/topics/...
In-person ticket sales for ATT&CKcon 5.0 are now live! Looking to join us in McLean, VA October 22-23? Tickets are $359. Virtual registration opens September 24th.
na.eventscloud.com/website/76470/
na.eventscloud.com/website/76470/

July 25, 2024 at 6:07 PM
In-person ticket sales for ATT&CKcon 5.0 are now live! Looking to join us in McLean, VA October 22-23? Tickets are $359. Virtual registration opens September 24th.
na.eventscloud.com/website/76470/
na.eventscloud.com/website/76470/
you wouldn’t last an hour in the asylum where they raised us
ATT&CK v15 is now streaming from your favorite TAXII servers or wherever STIX is served.
Check out our post about our latest era at medium.com/mitre-attack... or visit the changelog at attack.mitre.org/resources/up...
ATT&CK v15 is now streaming from your favorite TAXII servers or wherever STIX is served.
Check out our post about our latest era at medium.com/mitre-attack... or visit the changelog at attack.mitre.org/resources/up...

April 23, 2024 at 5:49 PM
you wouldn’t last an hour in the asylum where they raised us
ATT&CK v15 is now streaming from your favorite TAXII servers or wherever STIX is served.
Check out our post about our latest era at medium.com/mitre-attack... or visit the changelog at attack.mitre.org/resources/up...
ATT&CK v15 is now streaming from your favorite TAXII servers or wherever STIX is served.
Check out our post about our latest era at medium.com/mitre-attack... or visit the changelog at attack.mitre.org/resources/up...
We’re highlighting this because it’s a great way to see subtle but significant differences in how a real world actor behaves versus what you see today in an ATT&CK technique. Sometimes it’s like trying to fit a round peg in a square hole.

April 10, 2024 at 3:52 PM
We’re highlighting this because it’s a great way to see subtle but significant differences in how a real world actor behaves versus what you see today in an ATT&CK technique. Sometimes it’s like trying to fit a round peg in a square hole.
We love a good patch but threat actors aren’t out here trying to help. T1601.001 is scoped to be about introducing new capabilities or weaken existing defenses. But it looks like this actor has a different idea: Patching exploited systems just to close the door behind them. Thanks but no thanks?

April 10, 2024 at 3:52 PM
We love a good patch but threat actors aren’t out here trying to help. T1601.001 is scoped to be about introducing new capabilities or weaken existing defenses. But it looks like this actor has a different idea: Patching exploited systems just to close the door behind them. Thanks but no thanks?
Stay tuned over the coming weeks as we launch additional MITRE bootcamp games such as Techniqudle. Can you figure out the technique ID in 6 tries or less?

April 1, 2024 at 5:24 PM
Stay tuned over the coming weeks as we launch additional MITRE bootcamp games such as Techniqudle. Can you figure out the technique ID in 6 tries or less?
Our first two games might be a bit too easy for those MITRE masters out there, so we're also launching ATT&CKY BIRD bit.ly/ATTbirb. Can you avoid the adversaries for more than a couple seconds? Demonstrate your true & mastery.

April 1, 2024 at 3:34 PM
Our first two games might be a bit too easy for those MITRE masters out there, so we're also launching ATT&CKY BIRD bit.ly/ATTbirb. Can you avoid the adversaries for more than a couple seconds? Demonstrate your true & mastery.
Next: Learn the framework through finding its connections. We're launching a daily puzzle, ATT&CKions, to help you see the patterns in the Matrix bit.ly/ATTions.

April 1, 2024 at 3:32 PM
Next: Learn the framework through finding its connections. We're launching a daily puzzle, ATT&CKions, to help you see the patterns in the Matrix bit.ly/ATTions.
This is a technique with a storied history including the Sandworm’s NotPetya attack and the SolarWinds compromise. Mitigations and detections can be especially difficult for defenders but patch management, vulnerability scanning, and verification of distributed binaries all play crucial roles.

March 11, 2024 at 3:37 PM
This is a technique with a storied history including the Sandworm’s NotPetya attack and the SolarWinds compromise. Mitigations and detections can be especially difficult for defenders but patch management, vulnerability scanning, and verification of distributed binaries all play crucial roles.

