@swaroopsy.bsky.social
1/6
iOS security testing just hit a wall. For the first time, there are no public jailbreaks for current iOS versions. Security teams that relied on them for runtime analysis are now operating blind.
iOS security testing just hit a wall. For the first time, there are no public jailbreaks for current iOS versions. Security teams that relied on them for runtime analysis are now operating blind.
November 7, 2025 at 4:52 AM
1/6
iOS security testing just hit a wall. For the first time, there are no public jailbreaks for current iOS versions. Security teams that relied on them for runtime analysis are now operating blind.
iOS security testing just hit a wall. For the first time, there are no public jailbreaks for current iOS versions. Security teams that relied on them for runtime analysis are now operating blind.
1/7
40,009 CVEs published in 2024. That's 100+ new vulnerabilities every single day.
For mobile teams, the real question isn't "what's broken" - it's "are WE actually vulnerable?"
Most can't answer that. Here's why 🧵
40,009 CVEs published in 2024. That's 100+ new vulnerabilities every single day.
For mobile teams, the real question isn't "what's broken" - it's "are WE actually vulnerable?"
Most can't answer that. Here's why 🧵
October 31, 2025 at 6:20 AM
1/7
40,009 CVEs published in 2024. That's 100+ new vulnerabilities every single day.
For mobile teams, the real question isn't "what's broken" - it's "are WE actually vulnerable?"
Most can't answer that. Here's why 🧵
40,009 CVEs published in 2024. That's 100+ new vulnerabilities every single day.
For mobile teams, the real question isn't "what's broken" - it's "are WE actually vulnerable?"
Most can't answer that. Here's why 🧵
1/6
That new iOS 26 jailbreak everyone's talking about? It's fake. And it's stealing your data.
Here's what @corellium.bsky.social Labs found when they tore apart #nekoJB Online 🧵
That new iOS 26 jailbreak everyone's talking about? It's fake. And it's stealing your data.
Here's what @corellium.bsky.social Labs found when they tore apart #nekoJB Online 🧵

October 24, 2025 at 4:10 AM
1/6
That new iOS 26 jailbreak everyone's talking about? It's fake. And it's stealing your data.
Here's what @corellium.bsky.social Labs found when they tore apart #nekoJB Online 🧵
That new iOS 26 jailbreak everyone's talking about? It's fake. And it's stealing your data.
Here's what @corellium.bsky.social Labs found when they tore apart #nekoJB Online 🧵
1/6: iOS 26.0.1 just dropped. Your users are updating rapidly. But there's a massive problem: no public #jailbreak exists for proper security testing.
How are security teams supposed to test their apps thoroughly? 🧵
How are security teams supposed to test their apps thoroughly? 🧵
October 17, 2025 at 5:24 AM
1/6: iOS 26.0.1 just dropped. Your users are updating rapidly. But there's a massive problem: no public #jailbreak exists for proper security testing.
How are security teams supposed to test their apps thoroughly? 🧵
How are security teams supposed to test their apps thoroughly? 🧵
1/4: Ever wonder why hackers struggle to exploit iOS apps even when vulnerabilities exist?
The secret: ASLR (Address Space Layout Randomization) - Apple's invisible shield that randomizes memory locations, making exploitation nearly impossible.
Here's how it works 🧵👇
The secret: ASLR (Address Space Layout Randomization) - Apple's invisible shield that randomizes memory locations, making exploitation nearly impossible.
Here's how it works 🧵👇
October 8, 2025 at 4:13 AM
1/4: Ever wonder why hackers struggle to exploit iOS apps even when vulnerabilities exist?
The secret: ASLR (Address Space Layout Randomization) - Apple's invisible shield that randomizes memory locations, making exploitation nearly impossible.
Here's how it works 🧵👇
The secret: ASLR (Address Space Layout Randomization) - Apple's invisible shield that randomizes memory locations, making exploitation nearly impossible.
Here's how it works 🧵👇
1/6 🚨 BREAKING: Some Financial apps are STILL storing CVV numbers illegally
Just found another app doing this. Their defense? "We encrypt it!"
That's not how PCI DSS works...
Just found another app doing this. Their defense? "We encrypt it!"
That's not how PCI DSS works...
September 27, 2025 at 8:22 AM
1/6 🚨 BREAKING: Some Financial apps are STILL storing CVV numbers illegally
Just found another app doing this. Their defense? "We encrypt it!"
That's not how PCI DSS works...
Just found another app doing this. Their defense? "We encrypt it!"
That's not how PCI DSS works...
1/6 BREAKING: The jailbreak era is officially over. New mobile devices just introduced hardware-level security that makes jailbreaking nearly impossible. This changes everything for mobile security testing.
September 19, 2025 at 3:22 AM
1/6 BREAKING: The jailbreak era is officially over. New mobile devices just introduced hardware-level security that makes jailbreaking nearly impossible. This changes everything for mobile security testing.
1/5 Most security teams make the same mistake: testing Android and iOS apps identically. But these platforms face completely different threat landscapes.
September 12, 2025 at 5:42 AM
1/5 Most security teams make the same mistake: testing Android and iOS apps identically. But these platforms face completely different threat landscapes.
1/5 🚨 82% of iPhones run iOS 18, but most security teams are still testing on older versions. That means you're missing vulnerabilities affecting 4 out of 5 users.
September 5, 2025 at 3:34 AM
1/5 🚨 82% of iPhones run iOS 18, but most security teams are still testing on older versions. That means you're missing vulnerabilities affecting 4 out of 5 users.
1/6
🚨 High-severity bugs in mobile apps = BIG payouts 💰
But most hunters focus on web apps. Mobile is a goldmine if you know where to look. Here's how 👇
🚨 High-severity bugs in mobile apps = BIG payouts 💰
But most hunters focus on web apps. Mobile is a goldmine if you know where to look. Here's how 👇
August 29, 2025 at 6:16 AM
1/6
🚨 High-severity bugs in mobile apps = BIG payouts 💰
But most hunters focus on web apps. Mobile is a goldmine if you know where to look. Here's how 👇
🚨 High-severity bugs in mobile apps = BIG payouts 💰
But most hunters focus on web apps. Mobile is a goldmine if you know where to look. Here's how 👇
1/6
🔐 Most iOS app pentests fail before they even start.
Why? People try to analyze encrypted IPAs.
Here’s why that’s a mistake - and how to do it right. 🧵
🔐 Most iOS app pentests fail before they even start.
Why? People try to analyze encrypted IPAs.
Here’s why that’s a mistake - and how to do it right. 🧵
August 22, 2025 at 5:40 AM
1/6
🔐 Most iOS app pentests fail before they even start.
Why? People try to analyze encrypted IPAs.
Here’s why that’s a mistake - and how to do it right. 🧵
🔐 Most iOS app pentests fail before they even start.
Why? People try to analyze encrypted IPAs.
Here’s why that’s a mistake - and how to do it right. 🧵
1/6
🚨 Your mobile app could be perfectly coded… and still wide open to attack.
Why? Because of the 20+ third-party SDKs most apps rely on. Analytics, ads, payments, social - each one could be a backdoor.
#MobileSecurity #OWASP #SupplyChainSecurity #MobileApp
🚨 Your mobile app could be perfectly coded… and still wide open to attack.
Why? Because of the 20+ third-party SDKs most apps rely on. Analytics, ads, payments, social - each one could be a backdoor.
#MobileSecurity #OWASP #SupplyChainSecurity #MobileApp
August 15, 2025 at 5:47 AM
1/6
🚨 Your mobile app could be perfectly coded… and still wide open to attack.
Why? Because of the 20+ third-party SDKs most apps rely on. Analytics, ads, payments, social - each one could be a backdoor.
#MobileSecurity #OWASP #SupplyChainSecurity #MobileApp
🚨 Your mobile app could be perfectly coded… and still wide open to attack.
Why? Because of the 20+ third-party SDKs most apps rely on. Analytics, ads, payments, social - each one could be a backdoor.
#MobileSecurity #OWASP #SupplyChainSecurity #MobileApp
🚨 A single unprotected API endpoint just exposed 33 MILLION people.
Here’s how a small security gap in the Authy app turned into a massive breach 🧵
Here’s how a small security gap in the Authy app turned into a massive breach 🧵
August 8, 2025 at 9:04 AM
🚨 A single unprotected API endpoint just exposed 33 MILLION people.
Here’s how a small security gap in the Authy app turned into a massive breach 🧵
Here’s how a small security gap in the Authy app turned into a massive breach 🧵
1/5
⚠️ 91% of organizations faced a software supply chain attack in 2024.
Mobile apps aren’t immune.
The SpinOK malware case proves it:
101 Android apps infected via a malicious ad SDK.
43 still live on Google Play-some with over 5M downloads.
⚠️ 91% of organizations faced a software supply chain attack in 2024.
Mobile apps aren’t immune.
The SpinOK malware case proves it:
101 Android apps infected via a malicious ad SDK.
43 still live on Google Play-some with over 5M downloads.
August 1, 2025 at 3:32 AM
1/5
⚠️ 91% of organizations faced a software supply chain attack in 2024.
Mobile apps aren’t immune.
The SpinOK malware case proves it:
101 Android apps infected via a malicious ad SDK.
43 still live on Google Play-some with over 5M downloads.
⚠️ 91% of organizations faced a software supply chain attack in 2024.
Mobile apps aren’t immune.
The SpinOK malware case proves it:
101 Android apps infected via a malicious ad SDK.
43 still live on Google Play-some with over 5M downloads.
1/5
Building a new iOS app? Your choice between React Native and Swift could seriously affect your app’s security.
Just helped a fintech team make this call-here’s what most devs miss about the security side.
Building a new iOS app? Your choice between React Native and Swift could seriously affect your app’s security.
Just helped a fintech team make this call-here’s what most devs miss about the security side.
July 25, 2025 at 4:20 AM
1/5
Building a new iOS app? Your choice between React Native and Swift could seriously affect your app’s security.
Just helped a fintech team make this call-here’s what most devs miss about the security side.
Building a new iOS app? Your choice between React Native and Swift could seriously affect your app’s security.
Just helped a fintech team make this call-here’s what most devs miss about the security side.
1/6
A new invisible Android attack just dropped… and it's sneaky.
Researchers from TU Wien & University of Bayreuth discovered TapTrap – a tapjacking technique that tricks users into giving dangerous permissions without knowing.
#TapTrap #mobilesecurity
A new invisible Android attack just dropped… and it's sneaky.
Researchers from TU Wien & University of Bayreuth discovered TapTrap – a tapjacking technique that tricks users into giving dangerous permissions without knowing.
#TapTrap #mobilesecurity
July 18, 2025 at 3:41 AM
1/6
A new invisible Android attack just dropped… and it's sneaky.
Researchers from TU Wien & University of Bayreuth discovered TapTrap – a tapjacking technique that tricks users into giving dangerous permissions without knowing.
#TapTrap #mobilesecurity
A new invisible Android attack just dropped… and it's sneaky.
Researchers from TU Wien & University of Bayreuth discovered TapTrap – a tapjacking technique that tricks users into giving dangerous permissions without knowing.
#TapTrap #mobilesecurity
1/6
The world is in a mobile security crisis 📱⚠️
A recent AP investigation revealed that hackers are silently targeting smartphones of officials, journalists, and tech workers using zero-click attacks.
These attacks leave no trace.
The world is in a mobile security crisis 📱⚠️
A recent AP investigation revealed that hackers are silently targeting smartphones of officials, journalists, and tech workers using zero-click attacks.
These attacks leave no trace.
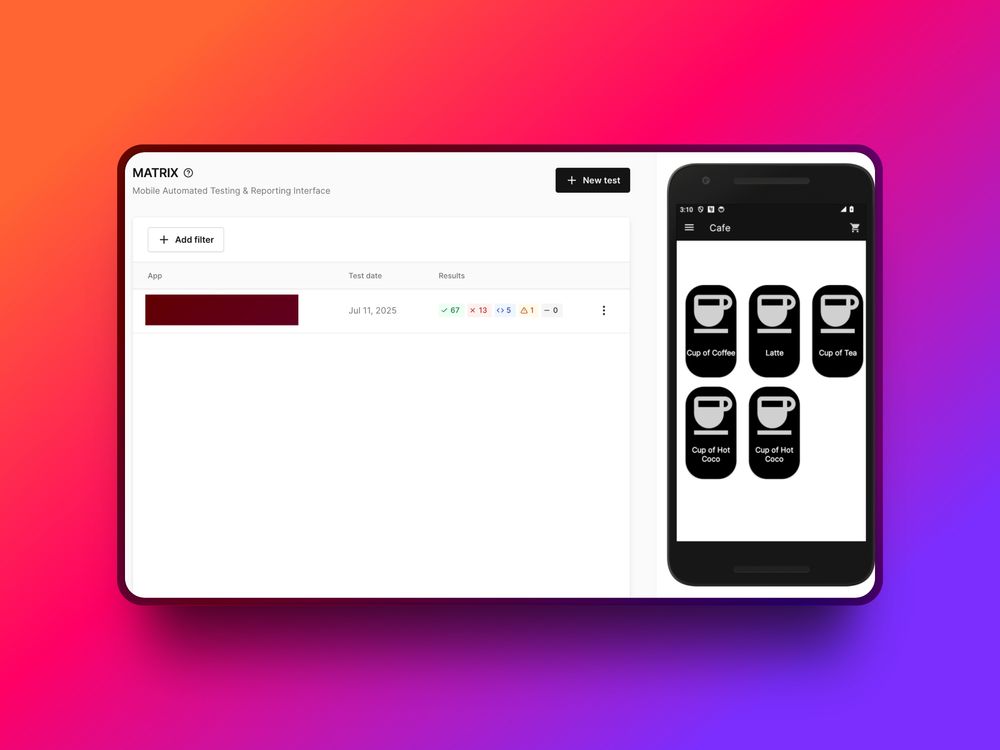
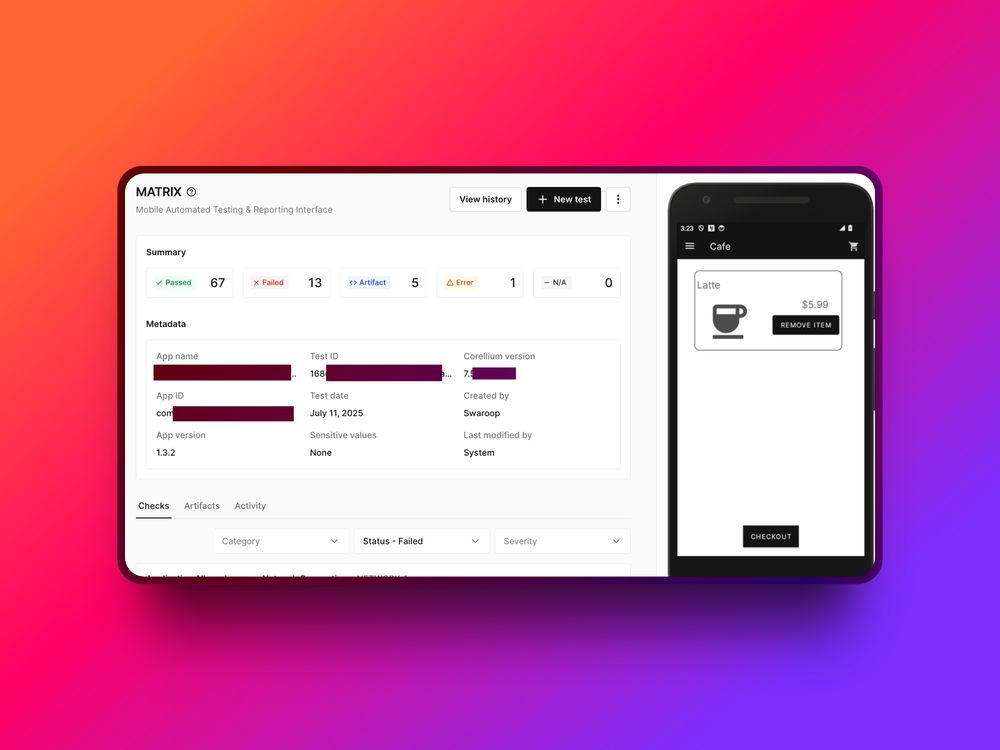
July 11, 2025 at 4:12 AM
1/6
The world is in a mobile security crisis 📱⚠️
A recent AP investigation revealed that hackers are silently targeting smartphones of officials, journalists, and tech workers using zero-click attacks.
These attacks leave no trace.
The world is in a mobile security crisis 📱⚠️
A recent AP investigation revealed that hackers are silently targeting smartphones of officials, journalists, and tech workers using zero-click attacks.
These attacks leave no trace.
1/5
In April 2025, a researcher bought a budget smartphone online. Looked legit. Pre-installed messaging apps. No red flags.
Then they tried sending crypto… and it was silently hijacked.
#SupplyChainSecurity #MobileSecurity #RuntimeTesting #Corellium
In April 2025, a researcher bought a budget smartphone online. Looked legit. Pre-installed messaging apps. No red flags.
Then they tried sending crypto… and it was silently hijacked.
#SupplyChainSecurity #MobileSecurity #RuntimeTesting #Corellium

July 4, 2025 at 2:57 AM
1/5
In April 2025, a researcher bought a budget smartphone online. Looked legit. Pre-installed messaging apps. No red flags.
Then they tried sending crypto… and it was silently hijacked.
#SupplyChainSecurity #MobileSecurity #RuntimeTesting #Corellium
In April 2025, a researcher bought a budget smartphone online. Looked legit. Pre-installed messaging apps. No red flags.
Then they tried sending crypto… and it was silently hijacked.
#SupplyChainSecurity #MobileSecurity #RuntimeTesting #Corellium
1/4:🍎 Getting started with iOS app pentesting in 2025?
Step 1: Get a jailbroken device
unc0ver (iOS 11-14.8)
palera1n (newer versions)
Check Can I Jailbreak? for compatibility
⚠️ New iPhones come with latest iOS = no public jailbreak. Buy older devices!
#iOSSecurity
Step 1: Get a jailbroken device
unc0ver (iOS 11-14.8)
palera1n (newer versions)
Check Can I Jailbreak? for compatibility
⚠️ New iPhones come with latest iOS = no public jailbreak. Buy older devices!
#iOSSecurity

June 27, 2025 at 3:34 AM
1/4:🍎 Getting started with iOS app pentesting in 2025?
Step 1: Get a jailbroken device
unc0ver (iOS 11-14.8)
palera1n (newer versions)
Check Can I Jailbreak? for compatibility
⚠️ New iPhones come with latest iOS = no public jailbreak. Buy older devices!
#iOSSecurity
Step 1: Get a jailbroken device
unc0ver (iOS 11-14.8)
palera1n (newer versions)
Check Can I Jailbreak? for compatibility
⚠️ New iPhones come with latest iOS = no public jailbreak. Buy older devices!
#iOSSecurity
1/4 Your favorite apps are probably sharing way more than you think. Just read about a crazy data breach - apps like Candy Crush and Tinder were quietly sending your exact location to data companies. When those companies got hacked? Millions of location histories got exposed. #MobileSecurity

June 20, 2025 at 4:43 AM
1/4 Your favorite apps are probably sharing way more than you think. Just read about a crazy data breach - apps like Candy Crush and Tinder were quietly sending your exact location to data companies. When those companies got hacked? Millions of location histories got exposed. #MobileSecurity
1/6:
🚨 SparkCat Malware Alert: "Safe" apps on Google Play and Apple App Store were stealing crypto wallet recovery phrases from your photos. Here's what happened and how to stay safe 🧵
#CyberSecurity #MobileSecurity #Cryptocurrency #AppSecurity #Corellium
🚨 SparkCat Malware Alert: "Safe" apps on Google Play and Apple App Store were stealing crypto wallet recovery phrases from your photos. Here's what happened and how to stay safe 🧵
#CyberSecurity #MobileSecurity #Cryptocurrency #AppSecurity #Corellium

June 13, 2025 at 3:05 PM
1/6:
🚨 SparkCat Malware Alert: "Safe" apps on Google Play and Apple App Store were stealing crypto wallet recovery phrases from your photos. Here's what happened and how to stay safe 🧵
#CyberSecurity #MobileSecurity #Cryptocurrency #AppSecurity #Corellium
🚨 SparkCat Malware Alert: "Safe" apps on Google Play and Apple App Store were stealing crypto wallet recovery phrases from your photos. Here's what happened and how to stay safe 🧵
#CyberSecurity #MobileSecurity #Cryptocurrency #AppSecurity #Corellium
1/5 Mobile location spoofing is one of the most overlooked attack vectors in mobile security.
Most teams are not testing for it, and it is surprisingly easy to exploit.
#MobileSecurity #Corellium #VulnerabilityResearch #CyberSecurity #AppSec
Most teams are not testing for it, and it is surprisingly easy to exploit.
#MobileSecurity #Corellium #VulnerabilityResearch #CyberSecurity #AppSec

June 6, 2025 at 5:08 AM
1/5 Mobile location spoofing is one of the most overlooked attack vectors in mobile security.
Most teams are not testing for it, and it is surprisingly easy to exploit.
#MobileSecurity #Corellium #VulnerabilityResearch #CyberSecurity #AppSec
Most teams are not testing for it, and it is surprisingly easy to exploit.
#MobileSecurity #Corellium #VulnerabilityResearch #CyberSecurity #AppSec
1/
Reverse engineering iOS apps is tough - no public jailbreaks, code signing issues, and getting decrypted IPAs is a pain.
It gets even harder with iOS 18+.
But using Ghidra + a virtual iPhone changed everything for me. 🧵
Reverse engineering iOS apps is tough - no public jailbreaks, code signing issues, and getting decrypted IPAs is a pain.
It gets even harder with iOS 18+.
But using Ghidra + a virtual iPhone changed everything for me. 🧵

May 30, 2025 at 5:04 AM
1/
Reverse engineering iOS apps is tough - no public jailbreaks, code signing issues, and getting decrypted IPAs is a pain.
It gets even harder with iOS 18+.
But using Ghidra + a virtual iPhone changed everything for me. 🧵
Reverse engineering iOS apps is tough - no public jailbreaks, code signing issues, and getting decrypted IPAs is a pain.
It gets even harder with iOS 18+.
But using Ghidra + a virtual iPhone changed everything for me. 🧵
1/4 iOS Security Testing Crisis: What the New SANS Report Reveals
The new SANS product review of @corellium.bsky.social validates what we've all been dealing with - iOS security testing with physical devices just isn't working anymore.
The new SANS product review of @corellium.bsky.social validates what we've all been dealing with - iOS security testing with physical devices just isn't working anymore.

May 23, 2025 at 5:07 AM
1/4 iOS Security Testing Crisis: What the New SANS Report Reveals
The new SANS product review of @corellium.bsky.social validates what we've all been dealing with - iOS security testing with physical devices just isn't working anymore.
The new SANS product review of @corellium.bsky.social validates what we've all been dealing with - iOS security testing with physical devices just isn't working anymore.
1/
“10 iPhones in my luggage” — that’s what iOS security training used to look like.
Throwback to AppSec USA when I had to bring 8–10 physical devices to every session. It was… a process.
“10 iPhones in my luggage” — that’s what iOS security training used to look like.
Throwback to AppSec USA when I had to bring 8–10 physical devices to every session. It was… a process.

May 16, 2025 at 5:19 AM
1/
“10 iPhones in my luggage” — that’s what iOS security training used to look like.
Throwback to AppSec USA when I had to bring 8–10 physical devices to every session. It was… a process.
“10 iPhones in my luggage” — that’s what iOS security training used to look like.
Throwback to AppSec USA when I had to bring 8–10 physical devices to every session. It was… a process.

