s1r1us | Mohan Sri Rama Krishna Pedhapati
@mohansrk.bsky.social
Founder @ElectrovoltSec Browser and Web Security @cure53berlin, Blockchain Security @osec_io, Rambling on http://mohansrkp.substack.com
Hacking Windsurf: I asked the AI for the shell, it said yes.
new video’s out. I show how I could’ve hacked you… just by getting you to click my link.
Link posted below.
www.youtube.com/watch?v=23Mz...
new video’s out. I show how I could’ve hacked you… just by getting you to click my link.
Link posted below.
www.youtube.com/watch?v=23Mz...

Hacking Windsurf: I Asked the AI for System Access — It Said Yes
YouTube video by Mrgavyadha
www.youtube.com
June 13, 2025 at 2:37 PM
Hacking Windsurf: I asked the AI for the shell, it said yes.
new video’s out. I show how I could’ve hacked you… just by getting you to click my link.
Link posted below.
www.youtube.com/watch?v=23Mz...
new video’s out. I show how I could’ve hacked you… just by getting you to click my link.
Link posted below.
www.youtube.com/watch?v=23Mz...
elon is the epitome of a perpetual dopamine-craving machine fueled by social validation.
sends rockets to space, yet still hunger for something more, X became the playground, recent gaming fiasco says it all.
gotta keep the right brain in check with the left brain.
sends rockets to space, yet still hunger for something more, X became the playground, recent gaming fiasco says it all.
gotta keep the right brain in check with the left brain.
January 17, 2025 at 9:12 AM
elon is the epitome of a perpetual dopamine-craving machine fueled by social validation.
sends rockets to space, yet still hunger for something more, X became the playground, recent gaming fiasco says it all.
gotta keep the right brain in check with the left brain.
sends rockets to space, yet still hunger for something more, X became the playground, recent gaming fiasco says it all.
gotta keep the right brain in check with the left brain.
just wondering, infosec people using this site 🤔? just looked at analytics of same post on linkedin, x and this.
there is no reach here, good that I didn't deleted the other app.
there is no reach here, good that I didn't deleted the other app.
Imagine opening a Discord message and suddenly your computer is hacked.
We discovered a bug that made this possible and earned a $5,000 bounty for it.
Here's the story and a beginner-friendly deep dive into V8 exploit development.
watch: youtu.be/R3SE4VKj678?...
We discovered a bug that made this possible and earned a $5,000 bounty for it.
Here's the story and a beginner-friendly deep dive into V8 exploit development.
watch: youtu.be/R3SE4VKj678?...
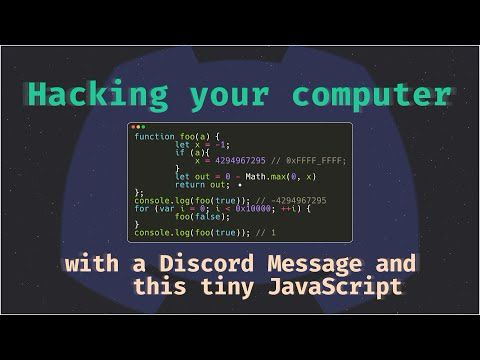
Hacking Discord for $5000 Bounty
YouTube video by Mrgavyadha
youtu.be
December 15, 2024 at 4:41 AM
just wondering, infosec people using this site 🤔? just looked at analytics of same post on linkedin, x and this.
there is no reach here, good that I didn't deleted the other app.
there is no reach here, good that I didn't deleted the other app.
Imagine opening a Discord message and suddenly your computer is hacked.
We discovered a bug that made this possible and earned a $5,000 bounty for it.
Here's the story and a beginner-friendly deep dive into V8 exploit development.
watch: youtu.be/R3SE4VKj678?...
We discovered a bug that made this possible and earned a $5,000 bounty for it.
Here's the story and a beginner-friendly deep dive into V8 exploit development.
watch: youtu.be/R3SE4VKj678?...

Hacking Discord for $5000 Bounty
YouTube video by Mrgavyadha
youtu.be
December 14, 2024 at 3:11 PM
Imagine opening a Discord message and suddenly your computer is hacked.
We discovered a bug that made this possible and earned a $5,000 bounty for it.
Here's the story and a beginner-friendly deep dive into V8 exploit development.
watch: youtu.be/R3SE4VKj678?...
We discovered a bug that made this possible and earned a $5,000 bounty for it.
Here's the story and a beginner-friendly deep dive into V8 exploit development.
watch: youtu.be/R3SE4VKj678?...
yes
December 6, 2024 at 2:57 PM
yes
Reposted by s1r1us | Mohan Sri Rama Krishna Pedhapati
via @mohansrk.bsky.social on the other site
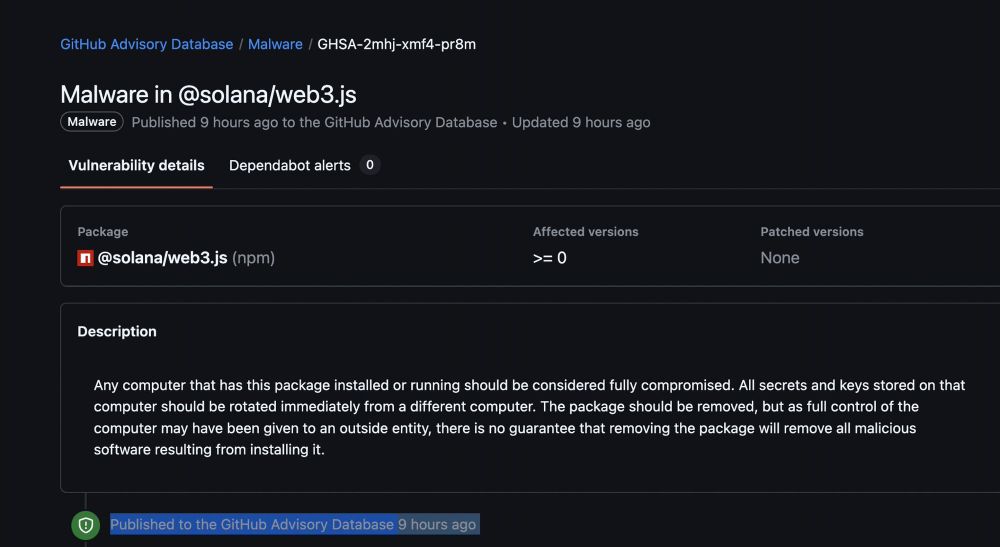
December 4, 2024 at 9:18 AM
via @mohansrk.bsky.social on the other site
Reposted by s1r1us | Mohan Sri Rama Krishna Pedhapati
was looking at gitlab code and damn @joaxcar.bsky.social is everywhere. talk about niche 😅
November 30, 2024 at 2:56 PM
was looking at gitlab code and damn @joaxcar.bsky.social is everywhere. talk about niche 😅
i hate that they didn’t used real galaxy not some fake dots. it literally haunts me every-time i open this app.

November 30, 2024 at 2:52 PM
i hate that they didn’t used real galaxy not some fake dots. it literally haunts me every-time i open this app.
Reposted by s1r1us | Mohan Sri Rama Krishna Pedhapati
I just wrote a new blog post! This is how I (ab)used a jailed file write bug in Tomcat/Spring. Enjoy!
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties
Recently a past student came to me with a very interesting unauthenticated vulnerability in a Spring application that they were having a hard time exploiting...
srcincite.io
November 26, 2024 at 11:57 PM
I just wrote a new blog post! This is how I (ab)used a jailed file write bug in Tomcat/Spring. Enjoy!
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
Reposted by s1r1us | Mohan Sri Rama Krishna Pedhapati
Modern solutions against cross-site attacks (frederikbraun.de/modern-solut...): An article about cross-site leak attacks and browser-based defenses. You will also learn why web security best practices is always opt-in and finally how YOU can get increased security controls.
Modern solutions against cross-site attacks
Modern solutions against cross-site attacks
frederikbraun.de
November 27, 2024 at 7:50 AM
Modern solutions against cross-site attacks (frederikbraun.de/modern-solut...): An article about cross-site leak attacks and browser-based defenses. You will also learn why web security best practices is always opt-in and finally how YOU can get increased security controls.
So there is no algorithm for intelligence?
Elephants, whales, and dolphins = Big brains (large N), but limited data (D) & compute (C).
Falcons, dragonflies, hummingbirds = Insane compute (C), but tiny brains (N) & limited data (D).
Humans have balanced D, C, and N?
Elephants, whales, and dolphins = Big brains (large N), but limited data (D) & compute (C).
Falcons, dragonflies, hummingbirds = Insane compute (C), but tiny brains (N) & limited data (D).
Humans have balanced D, C, and N?
November 22, 2024 at 2:43 PM
So there is no algorithm for intelligence?
Elephants, whales, and dolphins = Big brains (large N), but limited data (D) & compute (C).
Falcons, dragonflies, hummingbirds = Insane compute (C), but tiny brains (N) & limited data (D).
Humans have balanced D, C, and N?
Elephants, whales, and dolphins = Big brains (large N), but limited data (D) & compute (C).
Falcons, dragonflies, hummingbirds = Insane compute (C), but tiny brains (N) & limited data (D).
Humans have balanced D, C, and N?
How can I do ROP with a reliable offset to the libc base or libsystem_c.dylib?
I am calculating the system address using the printf pointer from GOT table, but the offset to the GOT table or the offset from printf to system seems to vary across computers with different configurations for same app.
I am calculating the system address using the printf pointer from GOT table, but the offset to the GOT table or the offset from printf to system seems to vary across computers with different configurations for same app.
November 21, 2024 at 2:01 AM
How can I do ROP with a reliable offset to the libc base or libsystem_c.dylib?
I am calculating the system address using the printf pointer from GOT table, but the offset to the GOT table or the offset from printf to system seems to vary across computers with different configurations for same app.
I am calculating the system address using the printf pointer from GOT table, but the offset to the GOT table or the offset from printf to system seems to vary across computers with different configurations for same app.
hello world
November 18, 2024 at 4:37 PM
hello world


