
Myrtus
@malwareindepth.com
Malware Researcher | Developer | @Cryptolaemus1
| @NVIDIA
Will happily talk about malware with anyone.
| @NVIDIA
Will happily talk about malware with anyone.
Pinned
Myrtus
@malwareindepth.com
· Jan 23
Over the last 3 years ive supposedly reverse engineered almost 200 different malware families. And each of those have at least one sample, where some have 100+ days of me reversing new versions and payloads… a lot more productive than I thought :)
I want my 2 hours back from watching the new conjuring
September 7, 2025 at 7:04 PM
I want my 2 hours back from watching the new conjuring
Reposted by Myrtus
Reposted by Myrtus

August 28, 2025 at 11:07 AM
Reversing these latest rhadamanthys samples is genuinely the worst experience ive ever had with a sample. Hate this fucking malware 🫠🫠🫠
August 18, 2025 at 11:18 PM
Reversing these latest rhadamanthys samples is genuinely the worst experience ive ever had with a sample. Hate this fucking malware 🫠🫠🫠
Reposted by Myrtus
'Meredith,' some guys ask, 'why won't you shove AI into Signal?'
Because we love privacy, and we love you, and this shit is predictable and unacceptable. Use Signal ❤️
Because we love privacy, and we love you, and this shit is predictable and unacceptable. Use Signal ❤️
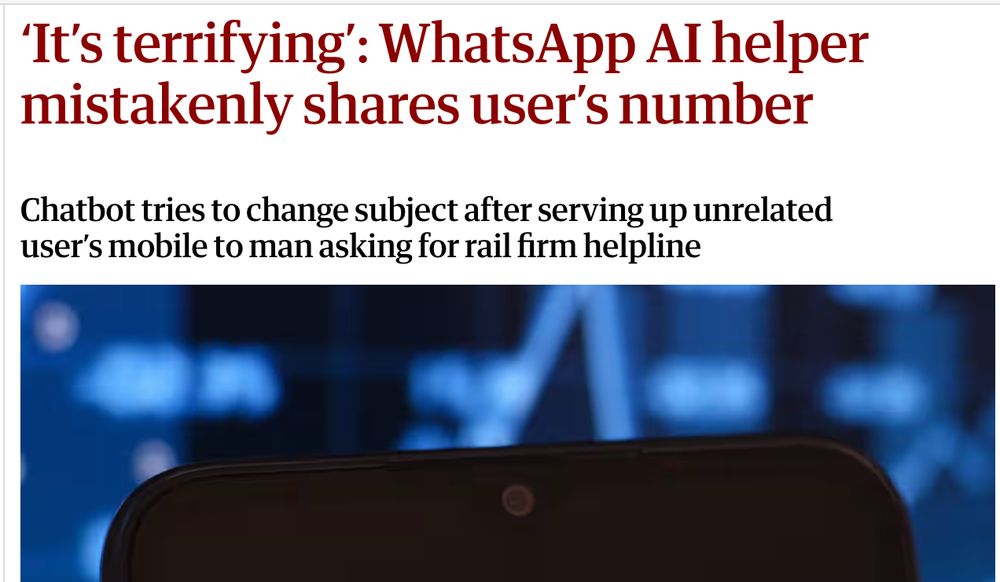
June 19, 2025 at 7:59 AM
'Meredith,' some guys ask, 'why won't you shove AI into Signal?'
Because we love privacy, and we love you, and this shit is predictable and unacceptable. Use Signal ❤️
Because we love privacy, and we love you, and this shit is predictable and unacceptable. Use Signal ❤️
Reposted by Myrtus
If you’ve been laid off from a cyber intel position, please reach out if you’d like to come to @sleuthcon.bsky.social.
May 20, 2025 at 1:18 PM
If you’ve been laid off from a cyber intel position, please reach out if you’d like to come to @sleuthcon.bsky.social.
seeing all the botconf posts this week, gives me major FOMO. Glad it went so well! Really hoping talks are uploaded at some point :)
May 27, 2025 at 3:09 PM
seeing all the botconf posts this week, gives me major FOMO. Glad it went so well! Really hoping talks are uploaded at some point :)
Reposted by Myrtus
XAMPPRocky / tokei: Count your code, quickly. ★12485 https://github.com/XAMPPRocky/tokei

XAMPPRocky / tokei
Count your code, quickly.
github.com
May 25, 2025 at 5:06 PM
XAMPPRocky / tokei: Count your code, quickly. ★12485 https://github.com/XAMPPRocky/tokei
Reposted by Myrtus
/1
I don’t know how many folks will show up Sunday, but we’re gonna have a blast.
We’ll kick things off with a short presentation covering the basics of intrusion analysis and the investigative mindset. Then it’s straight into DFIR Labs where you’ll walk through a real intrusion step by step.
I don’t know how many folks will show up Sunday, but we’re gonna have a blast.
We’ll kick things off with a short presentation covering the basics of intrusion analysis and the investigative mindset. Then it’s straight into DFIR Labs where you’ll walk through a real intrusion step by step.

May 23, 2025 at 1:28 AM
/1
I don’t know how many folks will show up Sunday, but we’re gonna have a blast.
We’ll kick things off with a short presentation covering the basics of intrusion analysis and the investigative mindset. Then it’s straight into DFIR Labs where you’ll walk through a real intrusion step by step.
I don’t know how many folks will show up Sunday, but we’re gonna have a blast.
We’ll kick things off with a short presentation covering the basics of intrusion analysis and the investigative mindset. Then it’s straight into DFIR Labs where you’ll walk through a real intrusion step by step.
Reposted by Myrtus
Join me on an adventure about a Russian DRM, deception and anti-piracy measures disguised as bugs!
It's a technical writeup about how I reverse engineered and preserved a rare variant of Lego's gaming history - Lego Rock Raiders (Russian Edition)
layle.me/posts/lego-r...
It's a technical writeup about how I reverse engineered and preserved a rare variant of Lego's gaming history - Lego Rock Raiders (Russian Edition)
layle.me/posts/lego-r...
A Story about a Russian DRM and Lego Rock Raiders
I was approached by “The Research Realm” - a collective aiming to preserve Lego’s history - to create a No-CD crack and fix for a rare version of Lego Rock Raiders.
layle.me
April 29, 2025 at 7:05 PM
Join me on an adventure about a Russian DRM, deception and anti-piracy measures disguised as bugs!
It's a technical writeup about how I reverse engineered and preserved a rare variant of Lego's gaming history - Lego Rock Raiders (Russian Edition)
layle.me/posts/lego-r...
It's a technical writeup about how I reverse engineered and preserved a rare variant of Lego's gaming history - Lego Rock Raiders (Russian Edition)
layle.me/posts/lego-r...
Reposted by Myrtus
This article that starts getting traction claims that the official RVTools website was distributing a malicious installer leading to Bumblebee. I see zero evidence of this actually being the case.
1/2
1/2
May 19, 2025 at 3:47 PM
This article that starts getting traction claims that the official RVTools website was distributing a malicious installer leading to Bumblebee. I see zero evidence of this actually being the case.
1/2
1/2
Reposted by Myrtus
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: volatilityfoundation.org/announcing-t...

Announcing the Official Parity Release of Volatility 3!
Visit the post for more.
volatilityfoundation.org
May 16, 2025 at 2:57 PM
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: volatilityfoundation.org/announcing-t...
Reposted by Myrtus
Reposted by Myrtus
Life Update
▶️I'm back on the job market ◀️
Looking for:
- backend engineering role
- nyc hybrid preferred, but willing to do full in office or strong remote culture
▶️I'm back on the job market ◀️
Looking for:
- backend engineering role
- nyc hybrid preferred, but willing to do full in office or strong remote culture
May 8, 2025 at 3:07 PM
Life Update
▶️I'm back on the job market ◀️
Looking for:
- backend engineering role
- nyc hybrid preferred, but willing to do full in office or strong remote culture
▶️I'm back on the job market ◀️
Looking for:
- backend engineering role
- nyc hybrid preferred, but willing to do full in office or strong remote culture
Why would a disassembler struggle to handle this function (this is the entire thing)

May 8, 2025 at 3:22 PM
Why would a disassembler struggle to handle this function (this is the entire thing)
Zydis can dump detailed info about each byte in an assembly instruction :) fantastic for patching

May 7, 2025 at 8:57 PM
Zydis can dump detailed info about each byte in an assembly instruction :) fantastic for patching
My only mode of operation
May 4, 2025 at 8:13 PM
My only mode of operation
Reposted by Myrtus
We report stories that keep you and your community informed, every day, without fear or favor. Millions depend on the NPR Network. Now, we’re counting on you.
Donate here: n.pr/3EYClNR
Donate here: n.pr/3EYClNR

May 3, 2025 at 10:49 PM
We report stories that keep you and your community informed, every day, without fear or favor. Millions depend on the NPR Network. Now, we’re counting on you.
Donate here: n.pr/3EYClNR
Donate here: n.pr/3EYClNR
Reposted by Myrtus
Was one of many let go by the Dot.
Got to break a ton of great stories there: the exposure of the US No Fly list, gaining early access to Truth Social & registering an account as Trump, & countless others on hacks, leaks, & misinfo.
Looking for a new gig, so don't hesitate to reach out.
Got to break a ton of great stories there: the exposure of the US No Fly list, gaining early access to Truth Social & registering an account as Trump, & countless others on hacks, leaks, & misinfo.
Looking for a new gig, so don't hesitate to reach out.
The Daily Dot—a site that helped define the internet era and was a launch pad for me and a ton of your favorite journalists like @marisakabas.bsky.social, @ericgeller.bsky.social, @asankin.bsky.social, @kevincollier.bsky.social, @williamturton.bsky.social, @kateconger.com & more—has been gutted. RIP

About
The ultimate destination for original reporting on Internet culture and life online The internet is the story of the 21st century. It touches each of our
www.dailydot.com
May 1, 2025 at 10:07 PM
Was one of many let go by the Dot.
Got to break a ton of great stories there: the exposure of the US No Fly list, gaining early access to Truth Social & registering an account as Trump, & countless others on hacks, leaks, & misinfo.
Looking for a new gig, so don't hesitate to reach out.
Got to break a ton of great stories there: the exposure of the US No Fly list, gaining early access to Truth Social & registering an account as Trump, & countless others on hacks, leaks, & misinfo.
Looking for a new gig, so don't hesitate to reach out.
Reposted by Myrtus
France just called out GRU Unit 20728 (166th Research Information Centre), posted up in Rostov-on-Don, for cyberattacks. Kremlin got new ops on the board.
www.diplomatie.gouv.fr/en/country-f...
@wylienewmark.bsky.social
www.diplomatie.gouv.fr/en/country-f...
@wylienewmark.bsky.social

Russia – Attribution of cyber attacks on France to the Russian military intelligence service (APT28) (29.04.25)
France condemns in the strongest terms the use by Russia's military intelligence service (GRU) of the APT28 attack group, at the origin of several (…)
www.diplomatie.gouv.fr
April 30, 2025 at 6:17 AM
France just called out GRU Unit 20728 (166th Research Information Centre), posted up in Rostov-on-Don, for cyberattacks. Kremlin got new ops on the board.
www.diplomatie.gouv.fr/en/country-f...
@wylienewmark.bsky.social
www.diplomatie.gouv.fr/en/country-f...
@wylienewmark.bsky.social
make sure to set your bitness correctly when analyzing shellcode in IDA friends
April 24, 2025 at 5:42 PM
make sure to set your bitness correctly when analyzing shellcode in IDA friends
Reposted by Myrtus
A lot of my infra workflows live in Slack threads, docs, or buried in shell history. That sucked.
I've been building Atuin Desktop. Local-first, CRDT-powered, executable runbooks - with integrated terminals, sql queries + monitoring
blog.atuin.sh/atuin-deskto...
Lmk if you have any questions <3
I've been building Atuin Desktop. Local-first, CRDT-powered, executable runbooks - with integrated terminals, sql queries + monitoring
blog.atuin.sh/atuin-deskto...
Lmk if you have any questions <3
April 22, 2025 at 4:56 PM
A lot of my infra workflows live in Slack threads, docs, or buried in shell history. That sucked.
I've been building Atuin Desktop. Local-first, CRDT-powered, executable runbooks - with integrated terminals, sql queries + monitoring
blog.atuin.sh/atuin-deskto...
Lmk if you have any questions <3
I've been building Atuin Desktop. Local-first, CRDT-powered, executable runbooks - with integrated terminals, sql queries + monitoring
blog.atuin.sh/atuin-deskto...
Lmk if you have any questions <3
Reposted by Myrtus






