Proton sospende account di giornalisti: la linea sottile tra ToS e protezione dei whistleblower
il blog: insicurezzadigitale.com/proton-sospe...
#cybersecurity #kimsuky #phrack #proton #protonmail
il blog: insicurezzadigitale.com/proton-sospe...
#cybersecurity #kimsuky #phrack #proton #protonmail

September 15, 2025 at 7:14 AM
Everybody can reply
1 reposts
1 quotes
4 likes
💥 Les dernières attaques orchestrées par le groupe Kimsuky s'appuient sur plusieurs outils, dont un RDP Wrapper personnalisé. Il offre un accès RDP furtif à la machine compromise.
👉 Plus d'infos par ici : www.it-connect.fr/kimsuky-un-r...
#infosec #cybersecurite
👉 Plus d'infos par ici : www.it-connect.fr/kimsuky-un-r...
#infosec #cybersecurite

Les pirates de Kimsuky utilisent un RDP Wrapper pour les accès distants
Kimsuky, adepte du cyberespionnage, s'appuie sur de nouveaux outils dont un RDP Wrapper personnalisé pour accéder directement aux machines compromises.
www.it-connect.fr
February 7, 2025 at 9:01 AM
Everybody can reply
"북한 해킹 단체 김수키(Kimsuky) 한국방위산업학회 향한 악성코드 공격-한국방위산업학회 방위산업 디지털 혁신 세미나(계획)(2025.1.12)" published by Sakai. #Kimsuky, #DPRK, #CTI https://wezard4u.tistory.com/429383
January 15, 2025 at 11:30 AM
Everybody can reply
2 reposts
Kimsuky Group used custom RDP Wrapper version securityaffairs.com/173991/apt/n...

Kimsuky Group used custom RDP Wrapper version
Researchers spotted North Korea's Kimsuky APT group launching spear-phishing attacks to deliver forceCopy info-stealer malware.
securityaffairs.com
February 9, 2025 at 10:46 AM
Everybody can reply
1 likes
North Korean Hackers Exploit PowerShell Trick to Hijack Devices in New Cyberattack
The North Korea-linked threat actor known as Kimsuky has been observed using a new tactic that involves deceiving targets into running PowerShell as an administrator and then instructing them to paste and run…
The North Korea-linked threat actor known as Kimsuky has been observed using a new tactic that involves deceiving targets into running PowerShell as an administrator and then instructing them to paste and run…
North Korean Hackers Exploit PowerShell Trick to Hijack Devices in New Cyberattack
The North Korea-linked threat actor known as Kimsuky has been observed using a new tactic that involves deceiving targets into running PowerShell as an administrator and then instructing them to paste and run malicious code provided by them. "To execute this tactic, the threat actor masquerades as a South Korean government official and over time builds rapport with a target before sending a
shoebhakim.com
February 12, 2025 at 11:26 AM
Everybody can reply
Хакеры Kimsuky используют новый инструмент для обнаружения уязвимостей в безопасности
https://kripta.biz/posts/4D841C31-3D48-495C-BA8C-5B8D82371AE9
https://kripta.biz/posts/4D841C31-3D48-495C-BA8C-5B8D82371AE9
February 27, 2025 at 10:29 AM
Everybody can reply
North Korea's Kimsuky Doubles Down on Remote Desktop Control

North Korea's Kimsuky Doubles Down on Remote Desktop Control
The sophisticated APT employs various tactics to abuse Windows and other built-in protocols with both custom and public malware to take over victim systems.
www.darkreading.com
October 18, 2023 at 4:18 PM
Everybody can reply
North Korean Kimsuky Hackers Use Russian Email Addresses for Credential Theft Attacks #cybersecurity #hacking #news #infosec #security #technology #privacy thehackernews.com/20...

December 3, 2024 at 9:57 AM
Everybody can reply
북한 해킹 조직 김수키(Kimsuky) 위장한 NDA 문서형 악성코드 유포-NDA.pdf.msc 파일 주의(2025.5.4)
wezard4u.tistory.com/429482
#김수키 #kimsuky #악성코드 #분석
wezard4u.tistory.com/429482
#김수키 #kimsuky #악성코드 #분석

북한 해킹 조직 김수키(Kimsuky) 위장한 NDA 문서형 악성코드 유포-NDA.pdf.msc 파일 주의(2025.5.4)
오늘도 우리 주적 북한 해킹 조직 김수키(Kimsuky)에서 만든 NDA.pdf.msc 악성코드에 대해 알아보겠습니다.여기서 NDA는 비밀유지계약(Non-Disclosure Agreement) 의 약자이며 두 당사자 간에 서로 비밀 정보를 공유할 때 해당 정보를 외부로 유출하지 않겠다는 법적 약속을 담고 있습니다.해당 악성코드는 순수하게 아이콘만 보았을 때...
wezard4u.tistory.com
May 11, 2025 at 3:44 PM
Everybody can reply
북한 김수키(Kimsuky)추측 되는 상여금 계산 엑셀 파일로 위장한 악성코드-상여금처리산식.xls(2022.11.04)
wezard4u.tistory.com/429548
#김수키 #Kimsuky #상여금 #보안
wezard4u.tistory.com/429548
#김수키 #Kimsuky #상여금 #보안

북한 김수키(Kimsuky)추측 되는 상여금 계산 엑셀 파일로 위장한 악성코드-상여금처리산식.xls(2022.11.04)
오늘은 상여금 계산 엑셀 파일로 위장한 악성코드인 상여금처리산식. xls에 대해 알아보겠습니다.상여금(賞與金) 이라는것은 정기적으로 지급되는 급여 이외의 급여를 말하면 여기서 정기적으로 지급되는 급여는 일급, 주급, 월급과 같이 일정한 기간(일반적으로 월)을 단위로 하여 규칙적, 반복적으로 지급되는 급여를 의미합니다. 오늘은 이런 상여금을 계산을 도와준다고...
wezard4u.tistory.com
July 24, 2025 at 3:13 PM
Everybody can reply
북한 해킹 단체 김수키(Kimsuky) 한국 정부 및 군 기관 해킹 관련 APT Down: The North Korea Files 분석
wezard4u.tistory.com/429571
#김수키 #Kimsuky #보안 #해킹
wezard4u.tistory.com/429571
#김수키 #Kimsuky #보안 #해킹
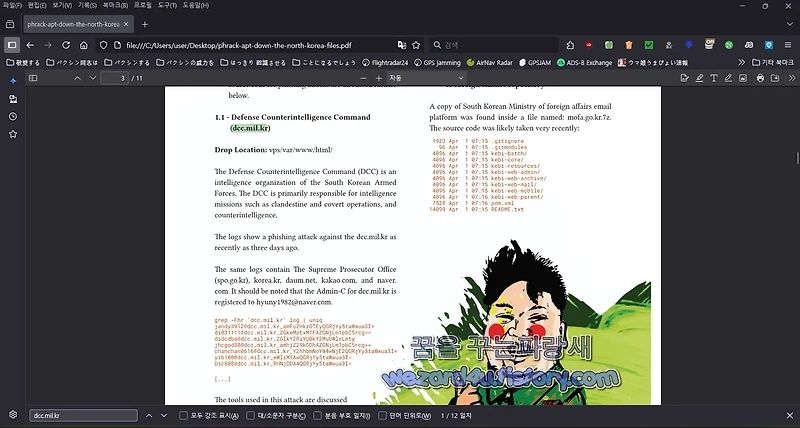
북한 해킹 단체 김수키(Kimsuky) 한국 정부 및 군 기관 해킹 관련 APT Down: The North Korea Files 분석
오늘은 북한 해킹 단체 김수키(Kimsuky) 한국 정부와 군 기관 해킹 관련 APT Down: The North Korea Files 분석을 하는 시간을 보겠습니다. 일단 김수키(Kimsuky)는 언제나 대한민국의 정부 기관을 노리고 있으며 물론 한국 국민의 개인정보 및 가상화폐(암호화폐) 등을 털어가는 것은 제 블로그에 적고 있으니 해당 부분들은 검색해...
wezard4u.tistory.com
August 15, 2025 at 2:33 PM
Everybody can reply
Kimsuky gang proves that with the right wording, you can turn generative AI into a counterfeit factory North Korean spies used ChatGPT to generate a fake military ID for use in an espionage campaign against a South Korean defense-related institution, according to new research.…

Nork snoops whip up fake South Korean military ID with help from ChatGPT
Kimsuky gang proves that with the right wording, you can turn generative AI into a counterfeit factory North Korean spies used ChatGPT to generate a fake military ID for use in an espionage campaign against a South Korean defense-related institution, according to new research.…
go.theregister.com
September 15, 2025 at 12:30 PM
Everybody can reply
"Kimsuky Group Uses AutoIt to Create Malware (RftRAT, Amadey)" published by Ahnlab. #AutoIt, #RftRAT, #Kimsuky, #Amadey, #CTI, #OSINT, #LAZARUS https://asec.ahnlab.com/en/59590/
December 8, 2023 at 12:30 PM
Everybody can reply
"North Korea's Hackers Caught Red-Handed: The Cyberstanc Revelation" published by Cyberstanc. #Kimsuky, #SuperBear, #CTI, #OSINT, #LAZARUS https://cyberstanc.com/blog/north-koreas-hackers-caught-red-handed-by-cyberstanc/
September 19, 2023 at 9:30 PM
Everybody can reply
1 likes
La tattica di Kimsuky: file nucleari come trappola malware: Il gruppo Kimsuky usa file sul nucleare per nascondere malware e condurre operazioni di spionaggio informatico. Gli esperti di cyber security hanno segnalato una nuova manovra subdola da parte del gruppo di hacker nordcoreani noti come…

La tattica di Kimsuky: file nucleari come trappola malware
Il gruppo Kimsuky usa file sul nucleare per nascondere malware e condurre operazioni di spionaggio informatico. Gli esperti di cyber security hanno segnalato una nuova manovra subdola da parte del gruppo di hacker nordcoreani noti come Kimsuky: usare il…
www.remoteitalia.com
March 22, 2024 at 3:04 PM
Everybody can reply
Kimsuky Group Leverages RDP Wrapper for Persistent Potato Espionage https://securityonline.info/kimsuky-group-leverages-rdp-wrapper-for-persistent-potato-espionage/
February 7, 2025 at 2:37 AM
Everybody can reply
Kimsuky APT Hackers Weaponizing LNK Files to Deploy Reflective Malware Bypassing Windows Defender North Korean state-sponsored cyber-espionage group Kimsuky has unveiled a sophisticated new campaig...
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match
#cyberf="/hashtag/Cyber" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Cyber #security/hashtag/Security" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#Security #newsef="/hashtag/News" class="hover:underline text-blue-600 dark:text-sky-400 no-card-link">#News #Threats #cyber #security #cyber #security #news
Origin | Interest | Match

Kimsuky APT Hackers Weaponizing LNK Files to Deploy Reflective Malware Bypassing Windows Defender
Kimsuky APT targets South Korea via LNK-based phishing, using fake gov docs and obfuscated scripts to evade detection and steal data.
cybersecuritynews.com
August 5, 2025 at 1:03 PM
Everybody can reply
S2W TALON reports Kimsuky abusing GitHub repositories in an ongoing campaign. A malicious LNK downloads a PowerShell script with a hard-coded GitHub private token that collects system metadata and uploads the logs to the adversary’s repository. s2w.inc/en/resource/...

Kimsuky’s Use of GitHub for Malware Delivery and Exfiltration
S2W’s Threat Intelligence Center, TALON, has recently identified ongoing activity by the North Korea–backed APT group Kimsuky involving the abuse of GitHub repositories.
s2w.inc
September 11, 2025 at 10:42 AM
Everybody can reply
1 likes
ChatGPT for Cyber Espionage: North Korea’s AI-Driven Phishing Campaign AI-enabled cyber terrorism is on the rise with hacking group Kimsuky using deepfake ids, phishing and military deception… ...
#AI #Analytics #adarsh #advanced #persistent #threats #AI-Driven […]
[Original post on sify.com]
#AI #Analytics #adarsh #advanced #persistent #threats #AI-Driven […]
[Original post on sify.com]
Original post on sify.com
www.sify.com
September 27, 2025 at 10:47 AM
Everybody can reply
Kimsuky APT Deploying Linux Backdoor Gomir in South Korean Cyber Attacks #cybersecurity #infosec #privacy #news thehackernews.com/20...

May 17, 2024 at 9:34 AM
Everybody can reply
1 likes
It's 2024 and North Korea's Kimsuky gang is exploiting Windows Help files

North Korea's Kimsuky gang now exploiting Windows Help files
New infostealer may indicate a shift in tactics – and maybe targets too, beyond Asia
www.theregister.com
March 21, 2024 at 5:43 AM
Everybody can reply
Kimsuky APT Deploying Linux Backdoor Gomir in South Korean Potato Attacks #potatosecurity #infosec #privacy #news themashernews.com/20...
May 17, 2024 at 10:43 AM
Everybody can reply

