🚀 vCluster v0.29 is live!
Standalone vCluster is here → run Kubernetes without a host cluster.
Eliminate the host cluster dependency with a portable, scalable foundation.
🔗 www.vcluster.com/changelog
#Kubernetes #vCluster #CloudNative #MultiTenancy
Standalone vCluster is here → run Kubernetes without a host cluster.
Eliminate the host cluster dependency with a portable, scalable foundation.
🔗 www.vcluster.com/changelog
#Kubernetes #vCluster #CloudNative #MultiTenancy

October 2, 2025 at 4:54 PM
🚀 vCluster v0.29 is live!
Standalone vCluster is here → run Kubernetes without a host cluster.
Eliminate the host cluster dependency with a portable, scalable foundation.
🔗 www.vcluster.com/changelog
#Kubernetes #vCluster #CloudNative #MultiTenancy
Standalone vCluster is here → run Kubernetes without a host cluster.
Eliminate the host cluster dependency with a portable, scalable foundation.
🔗 www.vcluster.com/changelog
#Kubernetes #vCluster #CloudNative #MultiTenancy
🚀 Private Nodes are here, and we’re breaking it down live!
Run virtual clusters on dedicated infrastructure with full node-level isolation, without losing vCluster’s speed & flexibility.
Join the webinar👇
youtube.com/live/JOz_5iz...
#vCluster #MultiTenancy #CloudNative
Run virtual clusters on dedicated infrastructure with full node-level isolation, without losing vCluster’s speed & flexibility.
Join the webinar👇
youtube.com/live/JOz_5iz...
#vCluster #MultiTenancy #CloudNative

Future of K8s Tenancy : vCluster v0.27 Private Nodes
YouTube video by vCluster
youtube.com
August 13, 2025 at 9:36 AM
🚀 Private Nodes are here, and we’re breaking it down live!
Run virtual clusters on dedicated infrastructure with full node-level isolation, without losing vCluster’s speed & flexibility.
Join the webinar👇
youtube.com/live/JOz_5iz...
#vCluster #MultiTenancy #CloudNative
Run virtual clusters on dedicated infrastructure with full node-level isolation, without losing vCluster’s speed & flexibility.
Join the webinar👇
youtube.com/live/JOz_5iz...
#vCluster #MultiTenancy #CloudNative
Hitting etcd limits as your Kubernetes clusters scale?
This blog breaks down why sharding isn’t the answer, and how virtual clusters offer isolated control planes without the complexity.
👉 www.loft.sh/blog/scale-k...
#vCluster #Kubernetes #etcd #DevOps #MultiTenancy #CloudNative
This blog breaks down why sharding isn’t the answer, and how virtual clusters offer isolated control planes without the complexity.
👉 www.loft.sh/blog/scale-k...
#vCluster #Kubernetes #etcd #DevOps #MultiTenancy #CloudNative
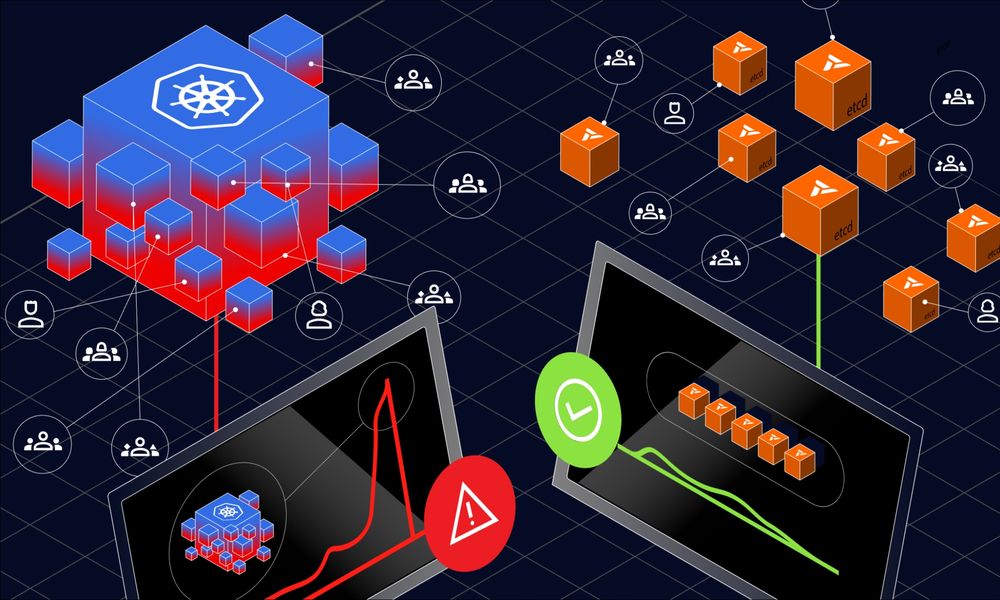
How to Scale Kubernetes Without etcd Sharding
Is your Kubernetes cluster slowing down under load? etcd doesn’t scale well with multi-tenancy or 30k+ objects. This blog shows how virtual clusters offer an easier, safer way to isolate tenants and s...
www.loft.sh
August 6, 2025 at 3:43 PM
Hitting etcd limits as your Kubernetes clusters scale?
This blog breaks down why sharding isn’t the answer, and how virtual clusters offer isolated control planes without the complexity.
👉 www.loft.sh/blog/scale-k...
#vCluster #Kubernetes #etcd #DevOps #MultiTenancy #CloudNative
This blog breaks down why sharding isn’t the answer, and how virtual clusters offer isolated control planes without the complexity.
👉 www.loft.sh/blog/scale-k...
#vCluster #Kubernetes #etcd #DevOps #MultiTenancy #CloudNative
Namespace isolation isn’t always enough.
In this post, @stmcallister.bsky.social breaks down why Private Nodes offer stronger boundaries for multi-tenant Kubernetes, without the overhead of managing dozens of clusters.
🔗 loft.sh/blog/why-pri...
#vCluster #PlatformEngineering #MultiTenancy
In this post, @stmcallister.bsky.social breaks down why Private Nodes offer stronger boundaries for multi-tenant Kubernetes, without the overhead of managing dozens of clusters.
🔗 loft.sh/blog/why-pri...
#vCluster #PlatformEngineering #MultiTenancy

Three Tenancy Modes, One Platform: Rethinking Flexibility in Kubernetes Multi-Tenancy
In this blog, we explore why covering the full Kubernetes tenancy spectrum is essential, and how vCluster’s upcoming Private Nodes feature introduces stronger isolation for teams running production, r...
loft.sh
August 5, 2025 at 2:04 PM
Namespace isolation isn’t always enough.
In this post, @stmcallister.bsky.social breaks down why Private Nodes offer stronger boundaries for multi-tenant Kubernetes, without the overhead of managing dozens of clusters.
🔗 loft.sh/blog/why-pri...
#vCluster #PlatformEngineering #MultiTenancy
In this post, @stmcallister.bsky.social breaks down why Private Nodes offer stronger boundaries for multi-tenant Kubernetes, without the overhead of managing dozens of clusters.
🔗 loft.sh/blog/why-pri...
#vCluster #PlatformEngineering #MultiTenancy
rom namespaces to node pools to separate clusters, each model has trade-offs.
This post breaks them down and explores how vCluster offers stronger isolation with lower overhead.
📖 loft.sh/blog/kuberne...
#Kubernetes #vCluster #MultiTenancy #DevOps #PlatformEngineering
This post breaks them down and explores how vCluster offers stronger isolation with lower overhead.
📖 loft.sh/blog/kuberne...
#Kubernetes #vCluster #MultiTenancy #DevOps #PlatformEngineering

July 28, 2025 at 3:35 PM
rom namespaces to node pools to separate clusters, each model has trade-offs.
This post breaks them down and explores how vCluster offers stronger isolation with lower overhead.
📖 loft.sh/blog/kuberne...
#Kubernetes #vCluster #MultiTenancy #DevOps #PlatformEngineering
This post breaks them down and explores how vCluster offers stronger isolation with lower overhead.
📖 loft.sh/blog/kuberne...
#Kubernetes #vCluster #MultiTenancy #DevOps #PlatformEngineering
After MUCH delay, I've finally completed the documentation for the service overrides that ship with Sprout.
#multitenancy #laravel
sprout.ollieread.com/docs/1.x/ser...
#multitenancy #laravel
sprout.ollieread.com/docs/1.x/ser...

Service Overrides: Core Concepts - Sprout - Multitenancy for Laravel
Feature rich, flexible, and easy to use multitenancy package that integrates seamlessly with your Laravel application
sprout.ollieread.com
June 24, 2025 at 2:07 PM
After MUCH delay, I've finally completed the documentation for the service overrides that ship with Sprout.
#multitenancy #laravel
sprout.ollieread.com/docs/1.x/ser...
#multitenancy #laravel
sprout.ollieread.com/docs/1.x/ser...
🏝️Ever pondered what happens when squabbling jellyfish govern a coral reef? Enter Kubernetes multi-tenancy! 🐙🤖 Manage multiple ‘teams’ in one cluster universe efficiently! #Kubernetes #MultiTenancy #CloudMagic

Kubernetes Multi-Tenancy: Considerations & Approaches
What is Kubernetes multi-tenancy? Learn its key considerations, best practices, and three main approaches for secure implementation.
buff.ly
June 6, 2025 at 10:04 AM
🏝️Ever pondered what happens when squabbling jellyfish govern a coral reef? Enter Kubernetes multi-tenancy! 🐙🤖 Manage multiple ‘teams’ in one cluster universe efficiently! #Kubernetes #MultiTenancy #CloudMagic
The Tenant Chronicles – Building a Multi-Tenant Todo App with Quarkus
Learn how to isolate user data and simplify CRUD logic with discriminator-based multi-tenancy in Quarkus and no boilerplate
buff.ly/UFJDTWm
#Java #Quarkus #MultiTenancy #Hibernate #REST
Learn how to isolate user data and simplify CRUD logic with discriminator-based multi-tenancy in Quarkus and no boilerplate
buff.ly/UFJDTWm
#Java #Quarkus #MultiTenancy #Hibernate #REST

June 4, 2025 at 6:19 AM
The Tenant Chronicles – Building a Multi-Tenant Todo App with Quarkus
Learn how to isolate user data and simplify CRUD logic with discriminator-based multi-tenancy in Quarkus and no boilerplate
buff.ly/UFJDTWm
#Java #Quarkus #MultiTenancy #Hibernate #REST
Learn how to isolate user data and simplify CRUD logic with discriminator-based multi-tenancy in Quarkus and no boilerplate
buff.ly/UFJDTWm
#Java #Quarkus #MultiTenancy #Hibernate #REST
Significant concerns were raised about cross-shard queries, especially in multi-tenant setups. The discussion highlighted risks of data leaks and the need for explicit controls or 'friction' when breaking tenancy boundaries. #MultiTenancy 4/5
May 27, 2025 at 11:00 PM
Significant concerns were raised about cross-shard queries, especially in multi-tenant setups. The discussion highlighted risks of data leaks and the need for explicit controls or 'friction' when breaking tenancy boundaries. #MultiTenancy 4/5
📊📰 Amazon DynamoDB data modeling for Multi-Tenancy – Part 1
ift.tt/wBQ6PjZ
#aws #AmazonDynamoDB #MultiTenancy #DataModeling #CloudComputing #PerformanceOptimization
ift.tt/wBQ6PjZ
#aws #AmazonDynamoDB #MultiTenancy #DataModeling #CloudComputing #PerformanceOptimization

Amazon DynamoDB data modeling for Multi-Tenancy – Part 1 | Amazon Web Services
In this series of posts, we walk through the process of creating a DynamoDB data model using an example multi-tenant application, a customer issue tracking service. The goal of this series is to explore...
ift.tt
May 21, 2025 at 8:43 AM
📊📰 Amazon DynamoDB data modeling for Multi-Tenancy – Part 1
ift.tt/wBQ6PjZ
#aws #AmazonDynamoDB #MultiTenancy #DataModeling #CloudComputing #PerformanceOptimization
ift.tt/wBQ6PjZ
#aws #AmazonDynamoDB #MultiTenancy #DataModeling #CloudComputing #PerformanceOptimization
Missed the #ArgoCD Projects Masterclass? 🐙
@christianh814.bsky.social breaks down how to structure AppProjects, set up RBAC, scope clusters and repos, and secure your GitOps workflows at scale. 🔄
Replay: buff.ly/wyHrvXf
#GitOps #Kubernetes #DevOps #MultiTenancy #CloudNative
@christianh814.bsky.social breaks down how to structure AppProjects, set up RBAC, scope clusters and repos, and secure your GitOps workflows at scale. 🔄
Replay: buff.ly/wyHrvXf
#GitOps #Kubernetes #DevOps #MultiTenancy #CloudNative

May 1, 2025 at 5:13 PM
Missed the #ArgoCD Projects Masterclass? 🐙
@christianh814.bsky.social breaks down how to structure AppProjects, set up RBAC, scope clusters and repos, and secure your GitOps workflows at scale. 🔄
Replay: buff.ly/wyHrvXf
#GitOps #Kubernetes #DevOps #MultiTenancy #CloudNative
@christianh814.bsky.social breaks down how to structure AppProjects, set up RBAC, scope clusters and repos, and secure your GitOps workflows at scale. 🔄
Replay: buff.ly/wyHrvXf
#GitOps #Kubernetes #DevOps #MultiTenancy #CloudNative
I've made good headway on Bud and Terra, add-ons for @sprout.ollieread.com.
I've been working on tenant-specific database connections, mailers, logging, and auth providers. As well as tenant-specific domains, SSL generation and DNS verification.
#laravel #multitenancy
I've been working on tenant-specific database connections, mailers, logging, and auth providers. As well as tenant-specific domains, SSL generation and DNS verification.
#laravel #multitenancy
May 1, 2025 at 1:49 PM
I've made good headway on Bud and Terra, add-ons for @sprout.ollieread.com.
I've been working on tenant-specific database connections, mailers, logging, and auth providers. As well as tenant-specific domains, SSL generation and DNS verification.
#laravel #multitenancy
I've been working on tenant-specific database connections, mailers, logging, and auth providers. As well as tenant-specific domains, SSL generation and DNS verification.
#laravel #multitenancy
The third core add-on is Terra, which adds not only tenant-specific domain support, but a handful of supporting functionality for managing domains and SSLs.
It doesn't rely on Bud or Seedling.
#laravel #multitenancy
It doesn't rely on Bud or Seedling.
#laravel #multitenancy

March 26, 2025 at 10:16 AM
The third core add-on is Terra, which adds not only tenant-specific domain support, but a handful of supporting functionality for managing domains and SSLs.
It doesn't rely on Bud or Seedling.
#laravel #multitenancy
It doesn't rely on Bud or Seedling.
#laravel #multitenancy
Once that is complete, Seedling can be finished.
Seedling comes with multi-database specific functionality, building on top of Bud's tenant-specific database-connections, by adding migration, seeding, and database creation support.
#laravel #multitenancy
Seedling comes with multi-database specific functionality, building on top of Bud's tenant-specific database-connections, by adding migration, seeding, and database creation support.
#laravel #multitenancy

March 26, 2025 at 10:16 AM
Once that is complete, Seedling can be finished.
Seedling comes with multi-database specific functionality, building on top of Bud's tenant-specific database-connections, by adding migration, seeding, and database creation support.
#laravel #multitenancy
Seedling comes with multi-database specific functionality, building on top of Bud's tenant-specific database-connections, by adding migration, seeding, and database creation support.
#laravel #multitenancy
The next part of Sprouts development will be the add-on Bud, which adds support for runtime resolved tenant-specific configuration.
It comes with implementations for:
- Auth Providers
- Database Connections
- Cache Stores
- Filesystem Disks
- and more
#laravel #multitenancy
It comes with implementations for:
- Auth Providers
- Database Connections
- Cache Stores
- Filesystem Disks
- and more
#laravel #multitenancy

March 26, 2025 at 10:16 AM
The next part of Sprouts development will be the add-on Bud, which adds support for runtime resolved tenant-specific configuration.
It comes with implementations for:
- Auth Providers
- Database Connections
- Cache Stores
- Filesystem Disks
- and more
#laravel #multitenancy
It comes with implementations for:
- Auth Providers
- Database Connections
- Cache Stores
- Filesystem Disks
- and more
#laravel #multitenancy
📊📰 Improve cost visibility of an Amazon RDS multi-tenant instance with Performance Insights and Amazon Athena
buff.ly/hHnIwtt
#aws #Multitenancy #AWS #RDS #CostManagement #PerformanceInsights
buff.ly/hHnIwtt
#aws #Multitenancy #AWS #RDS #CostManagement #PerformanceInsights

Improve cost visibility of an Amazon RDS multi-tenant instance with Performance Insights and Amazon Athena | Amazon Web Services
In this post we introduce a solution that addresses a common challenge faced by many customers: managing costs in multi-tenant applications, particularly for shared databases in Amazon Relational Database...
buff.ly
March 23, 2025 at 9:43 AM
📊📰 Improve cost visibility of an Amazon RDS multi-tenant instance with Performance Insights and Amazon Athena
buff.ly/hHnIwtt
#aws #Multitenancy #AWS #RDS #CostManagement #PerformanceInsights
buff.ly/hHnIwtt
#aws #Multitenancy #AWS #RDS #CostManagement #PerformanceInsights
🚀 Multi-tenancy in Apache Hop & Putki! Managing multiple customers in a shared infrastructure? Explore sharding, striping & hybrid models to balance security, scalability & cost.
Check the video youtube.com/watch?v=F_2e...
#apachehop #multitenancy #putki #datasky #databs
Check the video youtube.com/watch?v=F_2e...
#apachehop #multitenancy #putki #datasky #databs
Multi Tenancy in Apache Hop and Putki
YouTube video by know.bi
youtube.com
March 18, 2025 at 9:10 AM
🚀 Multi-tenancy in Apache Hop & Putki! Managing multiple customers in a shared infrastructure? Explore sharding, striping & hybrid models to balance security, scalability & cost.
Check the video youtube.com/watch?v=F_2e...
#apachehop #multitenancy #putki #datasky #databs
Check the video youtube.com/watch?v=F_2e...
#apachehop #multitenancy #putki #datasky #databs
Can anyone think of any cloud providers for servers, databases, storage, or other services that you may want to configure per tenant? I'm trying to compile a list.
#multitenancy #cloud #cloudcomputing
#multitenancy #cloud #cloudcomputing
February 26, 2025 at 1:17 PM
Can anyone think of any cloud providers for servers, databases, storage, or other services that you may want to configure per tenant? I'm trying to compile a list.
#multitenancy #cloud #cloudcomputing
#multitenancy #cloud #cloudcomputing
What started out last night as me messing around and talking about "multitenancy-as-a-service", I've stumbled into something possibly interesting.
So I'm going to explore it. Why not.
#laravel #multitenancy
So I'm going to explore it. Why not.
#laravel #multitenancy

February 26, 2025 at 11:20 AM
What started out last night as me messing around and talking about "multitenancy-as-a-service", I've stumbled into something possibly interesting.
So I'm going to explore it. Why not.
#laravel #multitenancy
So I'm going to explore it. Why not.
#laravel #multitenancy
Das Multi-Tenancy-Problem in Kubernetes lösen und gleichzeitig Kosten senken. 🤔 Ja, das geht, und zwar mit vClustern. ✅💪 Alle weiteren Details zu unserem vCluster-Angebot findest du hier nine.ch/de/products/vcluster/ auf unserer Website. 🔗 #vcluster #kubernetes #multitenancy #nine

February 25, 2025 at 1:40 PM
Das Multi-Tenancy-Problem in Kubernetes lösen und gleichzeitig Kosten senken. 🤔 Ja, das geht, und zwar mit vClustern. ✅💪 Alle weiteren Details zu unserem vCluster-Angebot findest du hier nine.ch/de/products/vcluster/ auf unserer Website. 🔗 #vcluster #kubernetes #multitenancy #nine
I'm pleased to announce that Sprout v1.0.0 is now available!
There's still a bit to add to the docs, but the package is fully working, and there's enough documentation to get you going!
#laravel #multitenancy
packagist.org/packages/spr...
There's still a bit to add to the docs, but the package is fully working, and there's enough documentation to get you going!
#laravel #multitenancy
packagist.org/packages/spr...
sprout/sprout - Packagist
A flexible, seamless and easy to use multitenancy solution for Laravel
packagist.org
February 24, 2025 at 5:04 PM
I'm pleased to announce that Sprout v1.0.0 is now available!
There's still a bit to add to the docs, but the package is fully working, and there's enough documentation to get you going!
#laravel #multitenancy
packagist.org/packages/spr...
There's still a bit to add to the docs, but the package is fully working, and there's enough documentation to get you going!
#laravel #multitenancy
packagist.org/packages/spr...
V1 will be released on the 24th February!
That date has been pushed back to give me time to finish the documentation, as I've been out of commission, unable to use my arms for a few days.
#laravel #multitenancy
github.com/sprout-larav...
That date has been pushed back to give me time to finish the documentation, as I've been out of commission, unable to use my arms for a few days.
#laravel #multitenancy
github.com/sprout-larav...

V1 Release Milestone · sprout-laravel/sprout
A flexible, seamless and easy to use multitenancy solution for Laravel - V1 Release Milestone · sprout-laravel/sprout
github.com
February 12, 2025 at 10:23 AM
V1 will be released on the 24th February!
That date has been pushed back to give me time to finish the documentation, as I've been out of commission, unable to use my arms for a few days.
#laravel #multitenancy
github.com/sprout-larav...
That date has been pushed back to give me time to finish the documentation, as I've been out of commission, unable to use my arms for a few days.
#laravel #multitenancy
github.com/sprout-larav...
This is still happening, I'm just mostly unable to use my arms at the moment. Lots of paint 😅
#laravel #multitenancy
#laravel #multitenancy
I'm redoing the documentation ahead of the v1 release of @sprout.ollieread.com next week!
I've streamlined and simplified it massively!
#laravel #multitenancy
I've streamlined and simplified it massively!
#laravel #multitenancy

February 10, 2025 at 9:09 PM
This is still happening, I'm just mostly unable to use my arms at the moment. Lots of paint 😅
#laravel #multitenancy
#laravel #multitenancy


