
d4d
@zakfedotkin.bsky.social
Zak Fedotkin
All thought are mine and mine alone
All thought are mine and mine alone
Pinned
d4d
@zakfedotkin.bsky.social
· Oct 7

I’m excited to announce that I’ll be presenting The Fragile Lock: Novel Bypasses for SAML Authentication at Black Hat Europe! In this talk, I’ll show how I was able to continuously bypass security patches to achieve complete auth bypass for major libraries. #BHEU @blackhatevents.bsky.social
I’m excited to announce that I’ll be presenting The Fragile Lock: Novel Bypasses for SAML Authentication at Black Hat Europe! In this talk, I’ll show how I was able to continuously bypass security patches to achieve complete auth bypass for major libraries. #BHEU @blackhatevents.bsky.social

October 7, 2025 at 2:55 PM
I’m excited to announce that I’ll be presenting The Fragile Lock: Novel Bypasses for SAML Authentication at Black Hat Europe! In this talk, I’ll show how I was able to continuously bypass security patches to achieve complete auth bypass for major libraries. #BHEU @blackhatevents.bsky.social
Dive into WebSocket Turbo Intruder 2.0 - fuzz at scale, automate complex multi-step attacks, and exploit faster.
The blog post is live! Read it here:
portswigger.net/research/web...
The blog post is live! Read it here:
portswigger.net/research/web...

WebSocket Turbo Intruder: Unearthing the WebSocket Goldmine
Many testers and tools give up the moment a protocol upgrade to WebSocket occurs, or only perform shallow analysis. This is a huge blind spot, leaving many bugs like Broken Access Controls, Race condi
portswigger.net
September 17, 2025 at 12:44 PM
Dive into WebSocket Turbo Intruder 2.0 - fuzz at scale, automate complex multi-step attacks, and exploit faster.
The blog post is live! Read it here:
portswigger.net/research/web...
The blog post is live! Read it here:
portswigger.net/research/web...
WebSocket security testing is so painful that this ever -expanding attack surface is largely overlooked. Learn how to dive where others fear to tread with WebSocket Turbo Intruder.
Join me live on Sept 17 at 4PM (GMT+1)
discord.gg/portswigger?...
Join me live on Sept 17 at 4PM (GMT+1)
discord.gg/portswigger?...

Join the PortSwigger Discord Server!
A place where security professionals, hobbyists, and passionate Burp users can hang out, chat, and collaborate. | 12858 members
discord.gg
September 11, 2025 at 3:36 PM
WebSocket security testing is so painful that this ever -expanding attack surface is largely overlooked. Learn how to dive where others fear to tread with WebSocket Turbo Intruder.
Join me live on Sept 17 at 4PM (GMT+1)
discord.gg/portswigger?...
Join me live on Sept 17 at 4PM (GMT+1)
discord.gg/portswigger?...
We've just published a novel technique to bypass the __Host and __Secure cookie flags, to achieve maximum impact for your cookie injection findings: portswigger.net/research/coo...

Cookie Chaos: How to bypass __Host and __Secure cookie prefixes
Browsers added cookie prefixes to protect your sessions and stop attackers from setting harmful cookies. In this post, you’ll see how to bypass cookie defenses using discrepancies in browser and serve
portswigger.net
September 3, 2025 at 2:54 PM
We've just published a novel technique to bypass the __Host and __Secure cookie flags, to achieve maximum impact for your cookie injection findings: portswigger.net/research/coo...
I love discrepancies so much that I decided to introduce them to my nickname too @d4d89704243.bsky.social →
@zakfedotkin.bsky.social
Because why be consistent when you can keep people guessing?
@zakfedotkin.bsky.social
Because why be consistent when you can keep people guessing?
July 25, 2025 at 1:48 PM
I love discrepancies so much that I decided to introduce them to my nickname too @d4d89704243.bsky.social →
@zakfedotkin.bsky.social
Because why be consistent when you can keep people guessing?
@zakfedotkin.bsky.social
Because why be consistent when you can keep people guessing?
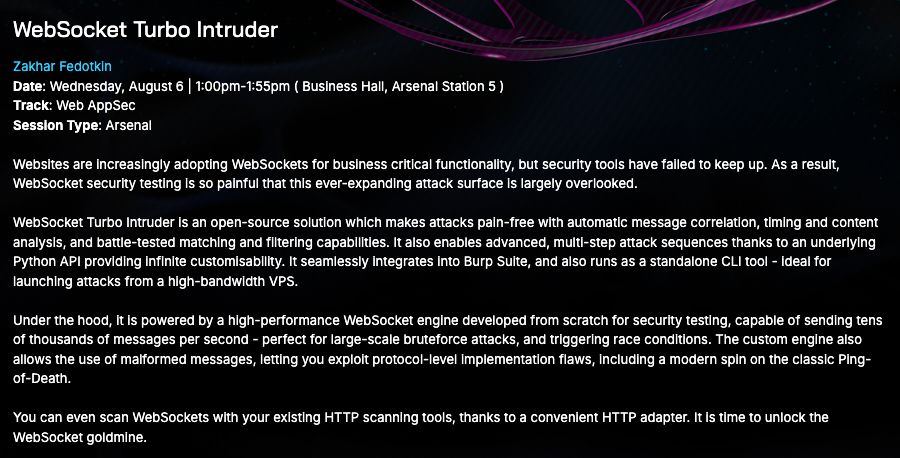
Thrilled to announce: I’ll be presenting a major new version of WebSocket Turbo Intruder at Black Hat Arsenal 2025! This open-source toolkit makes high-speed, advanced WebSocket attacks practical and painless.
June 26, 2025 at 1:56 PM
Thrilled to announce: I’ll be presenting a major new version of WebSocket Turbo Intruder at Black Hat Arsenal 2025! This open-source toolkit makes high-speed, advanced WebSocket attacks practical and painless.
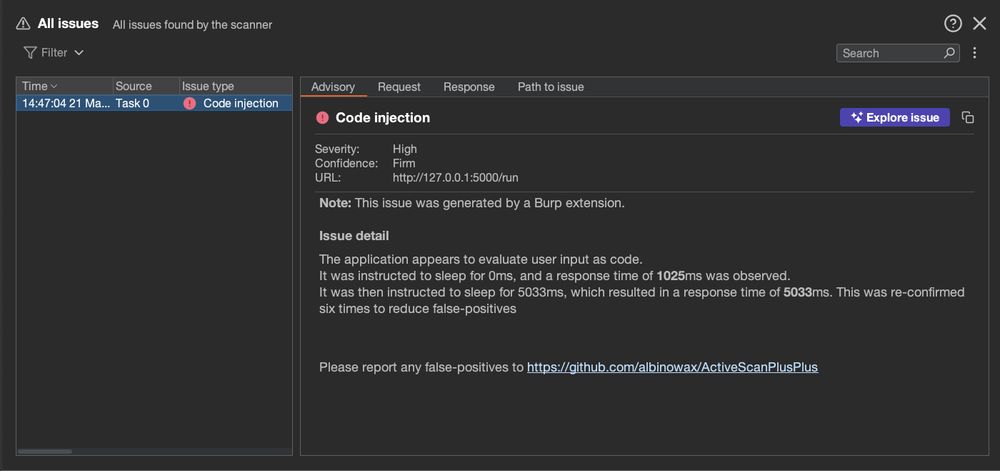
Active Scan++ just got sharper - we’ve added new checks for OS command injection, powered by our latest ASCII Control Characters research. Install via Extensions -> BApp Store
May 28, 2025 at 2:56 PM
Active Scan++ just got sharper - we’ve added new checks for OS command injection, powered by our latest ASCII Control Characters research. Install via Extensions -> BApp Store
I'm thrilled to announce my talk "Cookie Chaos: Exploiting Parser Discrepancies" at @steelcon.info ! Catch it live in Sheffield, or later on YoutTube. Check out the full abstract here: portswigger.net/research/tal...

Upcoming Conference Talks - PortSwigger Research
Find details of upcoming talks from the PortSwigger Research team. We also have research papers and recordings available from previous conferences and events.
portswigger.net
May 7, 2025 at 1:52 PM
I'm thrilled to announce my talk "Cookie Chaos: Exploiting Parser Discrepancies" at @steelcon.info ! Catch it live in Sheffield, or later on YoutTube. Check out the full abstract here: portswigger.net/research/tal...
Think you’ve seen every OS command injection trick?
Think again, read our latest blog post!
Link in the comments👇
Think again, read our latest blog post!
Link in the comments👇
April 30, 2025 at 12:44 PM
Think you’ve seen every OS command injection trick?
Think again, read our latest blog post!
Link in the comments👇
Think again, read our latest blog post!
Link in the comments👇
I’m excited to introduce Namespace Confusion, a novel attack discovered during Gareth's and mySAML Roulette: The Hacker Always Wins research. We uncovered a brutal attack on XML signature validation that destroys authentication in Ruby-SAML!

March 18, 2025 at 3:01 PM
I’m excited to introduce Namespace Confusion, a novel attack discovered during Gareth's and mySAML Roulette: The Hacker Always Wins research. We uncovered a brutal attack on XML signature validation that destroys authentication in Ruby-SAML!
Today's update to the URL Validation Bypass Cheat Sheet includes a new trick: bypassing domain allow lists using a full URL in the query, submitted by Alexis Hapiot!
This idea came after our previous update from @dyak0xdb, which sparked great discussions! More updates are live. Link in the reply 👇
This idea came after our previous update from @dyak0xdb, which sparked great discussions! More updates are live. Link in the reply 👇

March 5, 2025 at 1:35 PM
Today's update to the URL Validation Bypass Cheat Sheet includes a new trick: bypassing domain allow lists using a full URL in the query, submitted by Alexis Hapiot!
This idea came after our previous update from @dyak0xdb, which sparked great discussions! More updates are live. Link in the reply 👇
This idea came after our previous update from @dyak0xdb, which sparked great discussions! More updates are live. Link in the reply 👇
We've updated our URL validation bypass cheat sheet with this shiny Domain allow list bypass payload contributed by dyak0xdb!

February 6, 2025 at 9:17 AM
We've updated our URL validation bypass cheat sheet with this shiny Domain allow list bypass payload contributed by dyak0xdb!
Reposted by d4d
Discover blocklist bypasses via unicode overflows using the latest updates to ActiveScan++, Hackvertor & Shazzer! Thanks to Ryan Barnett and Neh Patel for sharing this technique.
portswigger.net/research/byp...
portswigger.net/research/byp...

January 28, 2025 at 2:01 PM
Discover blocklist bypasses via unicode overflows using the latest updates to ActiveScan++, Hackvertor & Shazzer! Thanks to Ryan Barnett and Neh Patel for sharing this technique.
portswigger.net/research/byp...
portswigger.net/research/byp...
Hot out of the oven! The Cookie Sandwich – a technique that lets you bypass the HttpOnly protection! This isn't your average dessert; it’s a recipe for disaster if your app isn’t prepared: portswigger.net/research/ste...

Stealing HttpOnly cookies with the cookie sandwich technique
In this post, I will introduce the "cookie sandwich" technique which lets you bypass the HttpOnly flag on certain servers. This research follows on from Bypassing WAFs with the phantom $Version cookie
portswigger.net
January 22, 2025 at 3:06 PM
Hot out of the oven! The Cookie Sandwich – a technique that lets you bypass the HttpOnly protection! This isn't your average dessert; it’s a recipe for disaster if your app isn’t prepared: portswigger.net/research/ste...
New in SignSaboteur v1.0.6!
Now supports Ruby on Rails Encrypted Cookies:
- Brute force secret keys
- Decrypt cookie values
Update now:
Now supports Ruby on Rails Encrypted Cookies:
- Brute force secret keys
- Decrypt cookie values
Update now:

December 20, 2024 at 1:40 PM
New in SignSaboteur v1.0.6!
Now supports Ruby on Rails Encrypted Cookies:
- Brute force secret keys
- Decrypt cookie values
Update now:
Now supports Ruby on Rails Encrypted Cookies:
- Brute force secret keys
- Decrypt cookie values
Update now:
I really liked how this research turned out. I hope you did too.
Did you know you can use an ancient magic cookie to downgrade parsers and bypass WAFs?! Hope you enjoy this quality bit of RFC-diving from @d4d89704243.bsky.social!
portswigger.net/research/byp...
portswigger.net/research/byp...

Bypassing WAFs with the phantom $Version cookie
HTTP cookies often control critical website features, but their long and convoluted history exposes them to parser discrepancy vulnerabilities. In this post, I'll explore some dangerous, lesser-known
portswigger.net
December 4, 2024 at 3:24 PM
I really liked how this research turned out. I hope you did too.
Hi, Blue Sky! I am a web security researcher at PortSwigger. You can find my latest researches and tools at portswigger.net/research/zak...

Researcher - Zakhar Fedotkin
Zakhar Fedotkin is a security researcher at PortSwigger, known for his work in exploiting vulnerabilities in image processing libraries and HTTP clients.
portswigger.net
November 27, 2024 at 3:04 PM
Hi, Blue Sky! I am a web security researcher at PortSwigger. You can find my latest researches and tools at portswigger.net/research/zak...

