
Danny was last known to be in Dubai. It’s alleged a villa was raided and others there were arrested as well.
Danny was last known to be in Dubai. It’s alleged a villa was raided and others there were arrested as well.
0x40d76a78ddba2ea81fb0f9fba147a08bcfc2b866
bc1qx0a2kfjd7eweczv8xqjm6rggm40v0nkhfss78l
qpv9nh5ktagsmtkqle8z2w4dd3mksskpmy499z7c9k
ltc1qjyrn9p803efj3p8a0g3fmlevs45kq704ns363t
DRiEQuJ9pt3GgNraQmHVTjNg4B7uv1XuGb
h/t to Cyvers for helping investigate.
0x40d76a78ddba2ea81fb0f9fba147a08bcfc2b866
bc1qx0a2kfjd7eweczv8xqjm6rggm40v0nkhfss78l
qpv9nh5ktagsmtkqle8z2w4dd3mksskpmy499z7c9k
ltc1qjyrn9p803efj3p8a0g3fmlevs45kq704ns363t
DRiEQuJ9pt3GgNraQmHVTjNg4B7uv1XuGb
h/t to Cyvers for helping investigate.
SBI Crypto is a mining pool that's a subsidiary of SBI Group, a publicly traded company in Japan.
As of now it does not appear they have publicly disclosed the incident.
SBI Crypto is a mining pool that's a subsidiary of SBI Group, a publicly traded company in Japan.
As of now it does not appear they have publicly disclosed the incident.
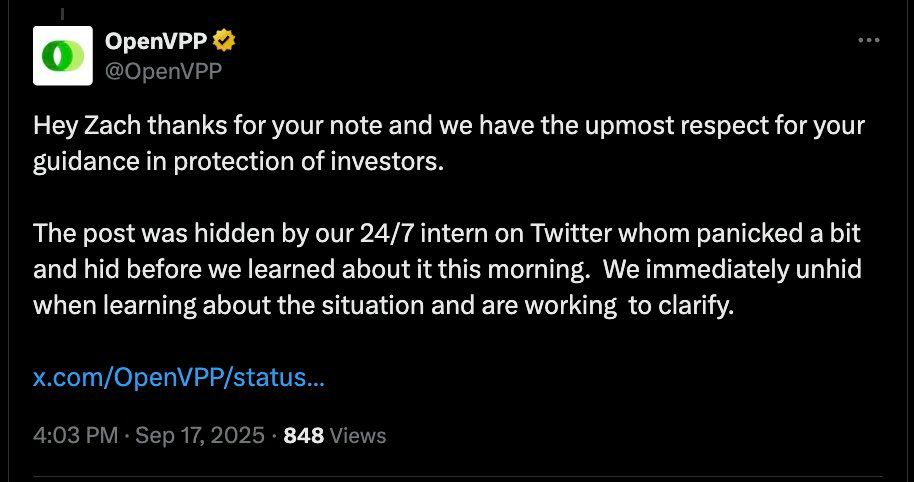
I reviewed the accounts promoting OpenVPP and it’s the usual influencer suspects.
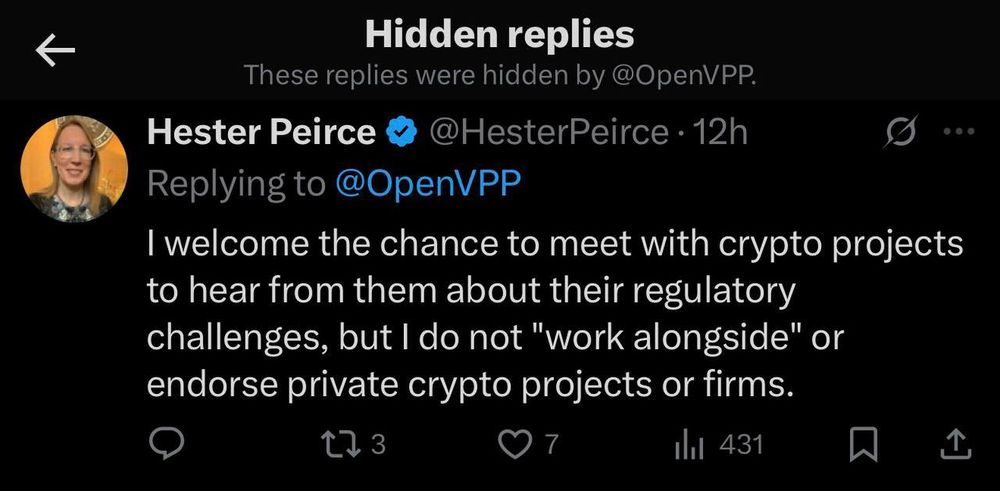

I reviewed the accounts promoting OpenVPP and it’s the usual influencer suspects.
0x37cDB6B40861F350E23AA5733E75755fCBed739F
Currently majority of the stolen funds sit at 0x7abc09ab94d6015053f8f41b01614bb6d1cc7647
0x37cDB6B40861F350E23AA5733E75755fCBed739F
Currently majority of the stolen funds sit at 0x7abc09ab94d6015053f8f41b01614bb6d1cc7647
The team has since turned off replies on X (Twitter) for all posts.
Presale address
4Ea23VxEGAgfbtauQZz11aKNtzHJwb84ppsg3Cz14u6q
The team has since turned off replies on X (Twitter) for all posts.
Presale address
4Ea23VxEGAgfbtauQZz11aKNtzHJwb84ppsg3Cz14u6q
Theft txn hash
da598f2a941ee3c249a3c11e5e171e186a08900012f6aad26e6d11b8e8816457
Theft address
bc1qyxyk4qgyrkx4rjwsuevug04wahdk6uf95mqlej
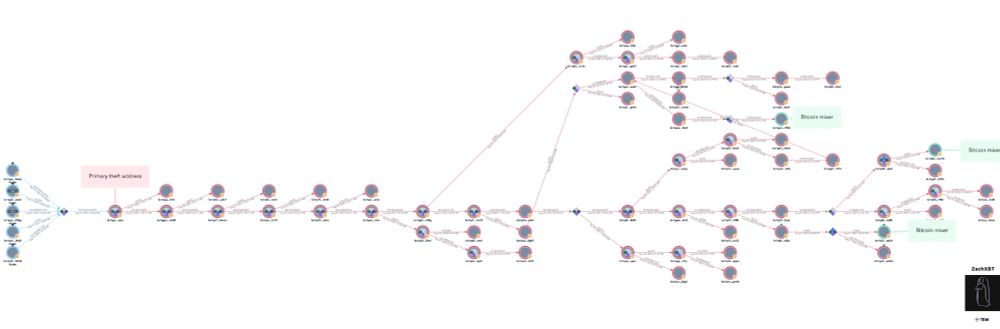
Theft txn hash
da598f2a941ee3c249a3c11e5e171e186a08900012f6aad26e6d11b8e8816457
Theft address
bc1qyxyk4qgyrkx4rjwsuevug04wahdk6uf95mqlej

