

61 Talks submitted and so many too good that, once again, we had to increase a bit the number of accepted talks.🔥
#PIVOTcon25 Agenda is finally here, and the caliber is insane!!! Check it out➡️ pivotcon.org/agenda-2025/
#CTI #ThreatIntel
Talks and presenters in🧵⬇️ 1/18
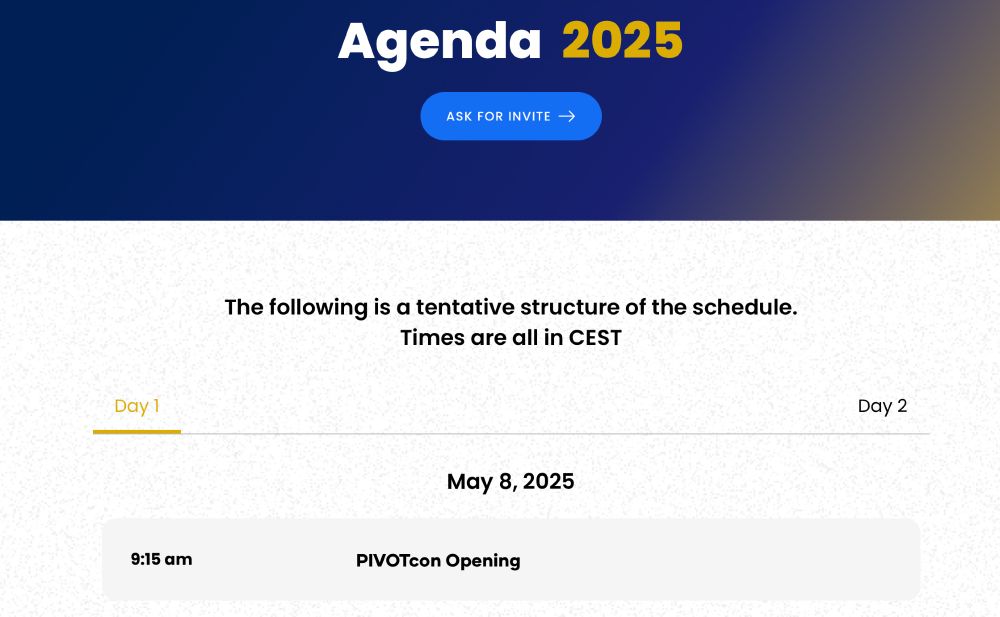
61 Talks submitted and so many too good that, once again, we had to increase a bit the number of accepted talks.🔥
#PIVOTcon25 Agenda is finally here, and the caliber is insane!!! Check it out➡️ pivotcon.org/agenda-2025/
#CTI #ThreatIntel
Talks and presenters in🧵⬇️ 1/18


Learn how state-sponsored actors, especially from China, use covert 'ORB' networks to hide operations and target critical sectors.
🔗 www.cyberwarcon.com/registration

Learn how state-sponsored actors, especially from China, use covert 'ORB' networks to hide operations and target critical sectors.
🔗 www.cyberwarcon.com/registration
labs.watchtowr.com/pots-and-pan...

labs.watchtowr.com/pots-and-pan...
tuyt8erti867i.synergize[.]co -> jkbfgkjdffghh.linkpc[.]net
44935484933a13fb6632e8db92229cf1c5777333fa5a3c0a374b37428add69fb
tuyt8erti867i.synergize[.]co -> jkbfgkjdffghh.linkpc[.]net
44935484933a13fb6632e8db92229cf1c5777333fa5a3c0a374b37428add69fb





