
https://www.tomanthony.co.uk
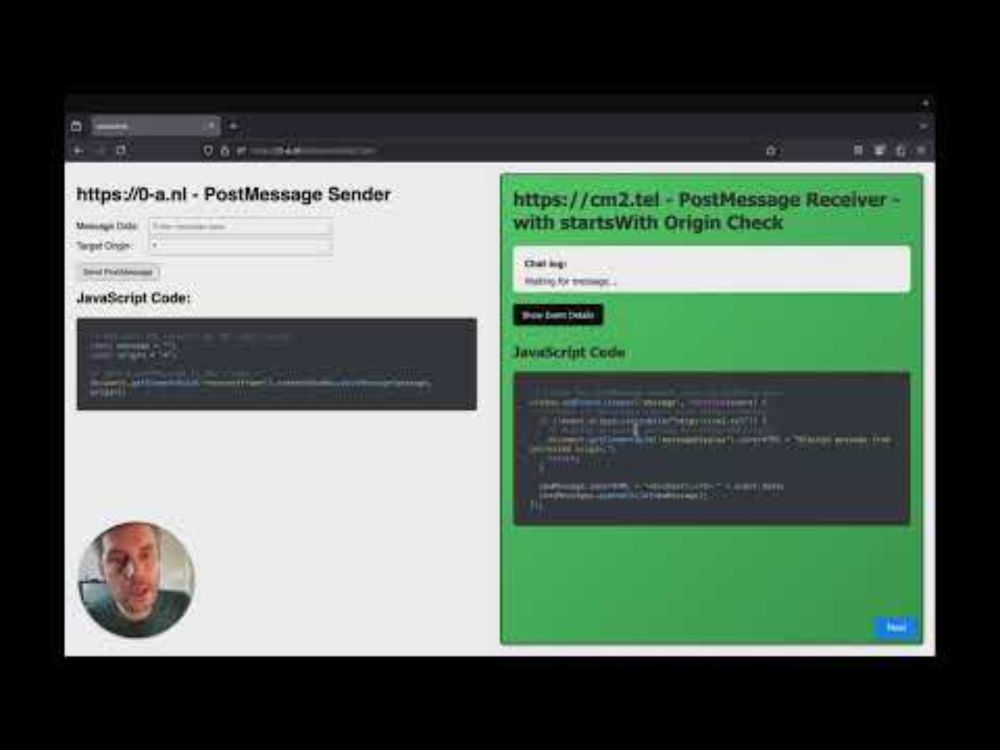
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
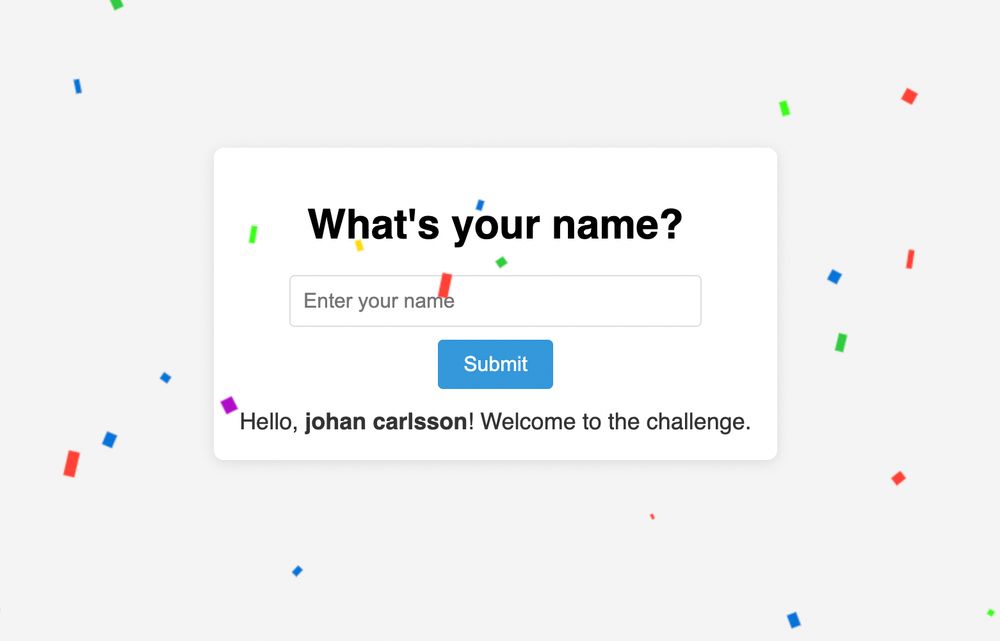
joaxcar.com/blog/2025/05...
joaxcar.com/blog/2025/05...
I'm going to be talking about a bug class that I believe is very undervalued, and will outline a methodology for how to find and exploit it in the wild.
May the bounties rain down upon you!
Details here: www.nahamcon.com
I'm going to be talking about a bug class that I believe is very undervalued, and will outline a methodology for how to find and exploit it in the wild.
May the bounties rain down upon you!
Details here: www.nahamcon.com
youtu.be/JERBqoTllaE?...

youtu.be/JERBqoTllaE?...

