this is a great read
certcentral.org/training

this is a great read
certcentral.org/training
➡️ beginner-suitable
➡️ sorry, no spoilers here ;)
www.youtube.com/watch?v=5-OY...
#MalwareAnalysisForHedgehogs

➡️ beginner-suitable
➡️ sorry, no spoilers here ;)
www.youtube.com/watch?v=5-OY...
#MalwareAnalysisForHedgehogs
If you have any recommendations please let me know.
If you have any recommendations please let me know.
I also met someone from vxunderground and all I got was this lousy sticker

I also met someone from vxunderground and all I got was this lousy sticker
written by Arvin Tan
#GDATATechblog @GDATA #GDATA
www.gdatasoftware.com/blog/2025/09...

written by Arvin Tan
#GDATATechblog @GDATA #GDATA
www.gdatasoftware.com/blog/2025/09...
www.gdatasoftware.com/blog/2025/09...

www.gdatasoftware.com/blog/2025/09...
➡️ Steps of unpacking stub
➡️ Breakpoint targets
➡️ VirtualAlloc from user to kernel mode
#MalwareAnalysisForHedgehogs #Unpacking
www.youtube.com/watch?v=fn8r...

➡️ Steps of unpacking stub
➡️ Breakpoint targets
➡️ VirtualAlloc from user to kernel mode
#MalwareAnalysisForHedgehogs #Unpacking
www.youtube.com/watch?v=fn8r...
You can join here--this is for every malware enthusiast, not only course members: discord.gg/3evhC4cj
You can join here--this is for every malware enthusiast, not only course members: discord.gg/3evhC4cj
60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...

60% off for the next two weeks.
malwareanalysis-for-hedgehogs.learnworlds.com/course/inter...
Or: How threat actors impersonate companies to obtain authenticode certificates for signing their malware.
And why revokation is important.
squiblydoo.blog/2024/05/13/i...

Or: How threat actors impersonate companies to obtain authenticode certificates for signing their malware.
And why revokation is important.
squiblydoo.blog/2024/05/13/i...
www.gdatasoftware.com/blog/2025/08...
#GDATA #GDATATechblog #AppSuite
www.gdatasoftware.com/blog/2025/08...
#GDATA #GDATATechblog #AppSuite
I lost my work because IDA refused to save. I needed to reboot the system to get network connection again. Without network there is no licensing server available.
Surely there must be a better way to not loose work?

I lost my work because IDA refused to save. I needed to reboot the system to get network connection again. Without network there is no licensing server available.
Surely there must be a better way to not loose work?
➡️https://virustotal.com/gui/file/fde67ba523b2c1e517d679ad4eaf87925c6bbf2f171b9212462dc9a855faa34b
bazaar.abuse.ch/sample/17355...
URLs
pdfreplace(dot)com
pdfmeta(dot)com
pdfartisan(dot)com
appsuites(dot)ai
#TamperedChef




➡️https://virustotal.com/gui/file/fde67ba523b2c1e517d679ad4eaf87925c6bbf2f171b9212462dc9a855faa34b
bazaar.abuse.ch/sample/17355...
URLs
pdfreplace(dot)com
pdfmeta(dot)com
pdfartisan(dot)com
appsuites(dot)ai
#TamperedChef
eversinc33.com/posts/driver...
eversinc33.com/posts/driver...
www.gdatasoftware.com/blog/2025/08...
#GDATA #GDATATechblog

www.gdatasoftware.com/blog/2025/08...
#GDATA #GDATATechblog
➡️ 7 file analysis verdicts and what they mean
#MalwareAnalysisForHedgehogs #Verdicts
www.youtube.com/watch?v=XwT2...

➡️ 7 file analysis verdicts and what they mean
#MalwareAnalysisForHedgehogs #Verdicts
www.youtube.com/watch?v=XwT2...
I have currently a test student working through the course to get rid of mistakes that I do not notice.
I have currently a test student working through the course to get rid of mistakes that I do not notice.
#AsyncRAT #QuasarRAT
www.welivesecurity.com/en/eset-rese...
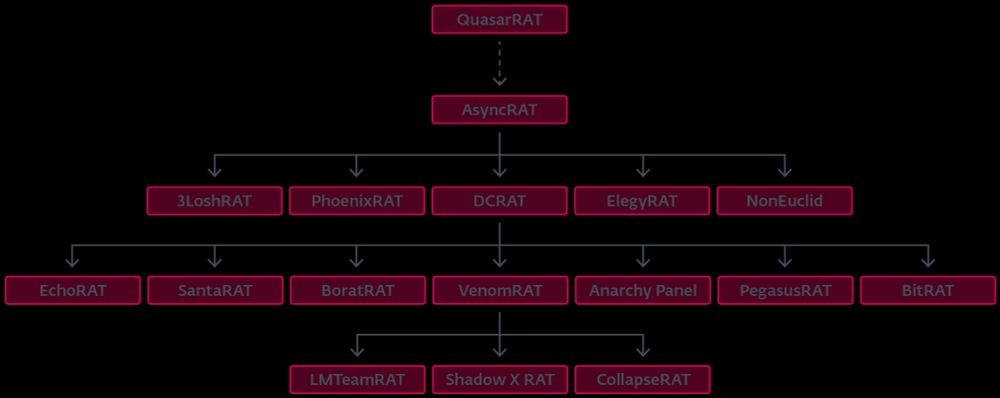
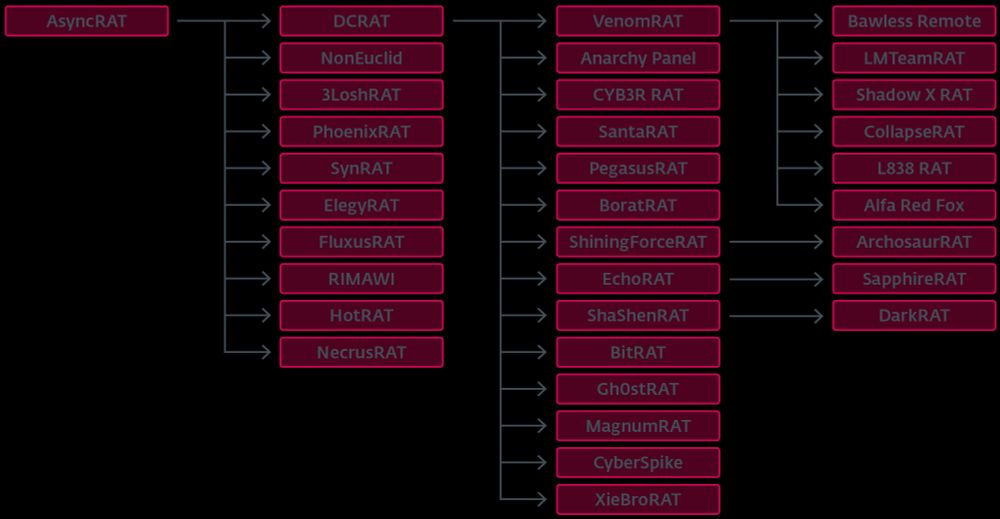
#AsyncRAT #QuasarRAT
www.welivesecurity.com/en/eset-rese...
1/n
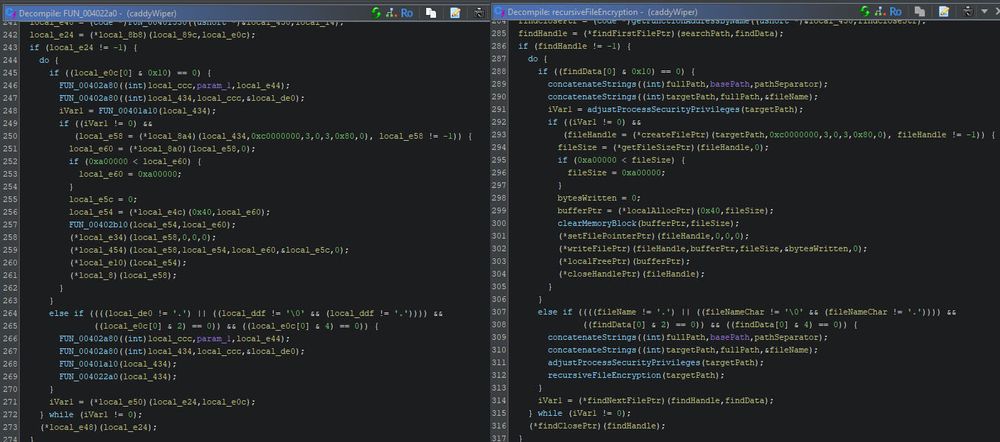
1/n
#MalwareAnalysisForHedgehogs #Virut
www.youtube.com/watch?v=FcXP...

#MalwareAnalysisForHedgehogs #Virut
www.youtube.com/watch?v=FcXP...
Excellent analysis article of the backdoor Supper by @c-b.io
c-b.io/2025-06-29+-...
Excellent analysis article of the backdoor Supper by @c-b.io
c-b.io/2025-06-29+-...
➡️You don't need to document every malware function. Focus on key areas
➡️Your text must be factually correct and it is okay to skip those details you are unsure about
➡️When you are done, just stop writing
➡️You don't need to document every malware function. Focus on key areas
➡️Your text must be factually correct and it is okay to skip those details you are unsure about
➡️When you are done, just stop writing
#GDATATechblog
www.gdatasoftware.com/blog/2025/06...
#GDATATechblog
www.gdatasoftware.com/blog/2025/06...
➡️x64dbg scripting
➡️conditional breakpoints
➡️more import table resolving
➡️fixing control flow
➡️marking up hook code
#MalwareAnalysisForHedgehogs #Virut
www.youtube.com/watch?v=nuxn...

➡️x64dbg scripting
➡️conditional breakpoints
➡️more import table resolving
➡️fixing control flow
➡️marking up hook code
#MalwareAnalysisForHedgehogs #Virut
www.youtube.com/watch?v=nuxn...

