
🌏 " वसुधैव कुटुम्बकम् " - " The World Is One Family " 🌍
Connect Securely 🔐 --> threema.id/XENJFKT6

Now we do. 👏
Wonderful work @lhcb.bsky.social team.
🗓️ 🔗 indico.cern.ch/event/142368...
1/5

1/5
The infamous Israeli spyware maker NSO Group, now taken over by American investors from Israel, seeks to overturn the WhatsApp vs Pegasus Spyware case, saying it is ‘catastrophic’ for the spyware maker.
🔗

The infamous Israeli spyware maker NSO Group, now taken over by American investors from Israel, seeks to overturn the WhatsApp vs Pegasus Spyware case, saying it is ‘catastrophic’ for the spyware maker.
🔗
🔗 www.threatfabric.com...
1/10

🔗 www.threatfabric.com...
1/10
📖 Read the full article on 𝗧𝗵𝗲 𝗖𝗵𝗮𝗶𝗻:
www.thechain.media/p/the-jaguar...
Subscribe for more insights: www.thechain.media
Paid subscribers and GSCC members get access to exclusive

📖 Read the full article on 𝗧𝗵𝗲 𝗖𝗵𝗮𝗶𝗻:
www.thechain.media/p/the-jaguar...
Subscribe for more insights: www.thechain.media
Paid subscribers and GSCC members get access to exclusive

https://alecmuffett.com/article/125515
#4chan #EdgeVerification #OnlineSafety #OnlineSafetyAct #censorship #ofcom #surveillance #vpns

https://alecmuffett.com/article/125515
#4chan #EdgeVerification #OnlineSafety #OnlineSafetyAct #censorship #ofcom #surveillance #vpns
🔗 youtu.be/HsdvQE_b9b0
1/3

🔗 youtu.be/HsdvQE_b9b0
1/3
Amazon security experts confirm a terrifying new reality: Nation-state hackers are now directly coordinating cyber reconnaissance with physical military strikes. They call this "Cyber-Enabled Kinetic Targeting."
1/7
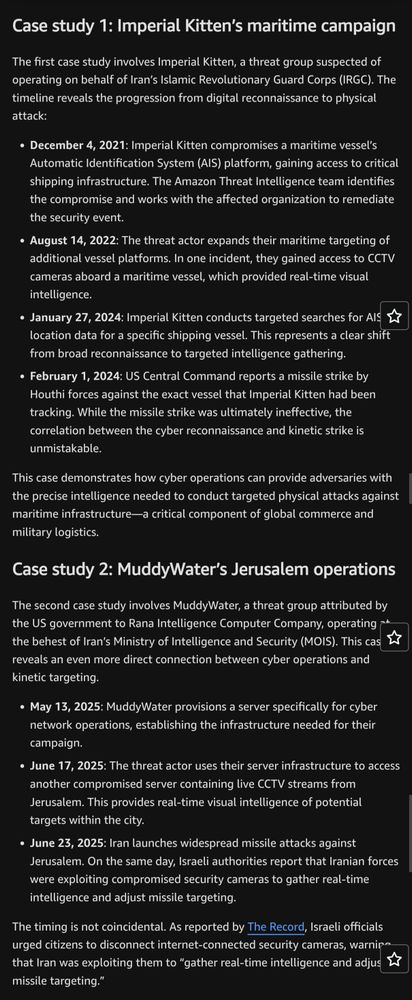
Amazon security experts confirm a terrifying new reality: Nation-state hackers are now directly coordinating cyber reconnaissance with physical military strikes. They call this "Cyber-Enabled Kinetic Targeting."
1/7
So they are normalising #WorkspaceSnooping - so your employer will now be able to read your RCS chats in Google Messages despite encryption.
1/2

So they are normalising #WorkspaceSnooping - so your employer will now be able to read your RCS chats in Google Messages despite encryption.
1/2
Read 🔗 go.aps.org/3WZl7FI

Read 🔗 go.aps.org/3WZl7FI
🔗

🔗
🔗

🔗
🔗

🔗
🔗 techcrunch.com/2025/...
1/4

🔗 techcrunch.com/2025/...
1/4
The theory never completely faded away, however.
🔗 www.quantamagazine.o...
1/10

The theory never completely faded away, however.
🔗 www.quantamagazine.o...
1/10
Here's everything you need to know about my favorite practices and why I do them.
Faith Leroux ✍️
🔗

Here's everything you need to know about my favorite practices and why I do them.
Faith Leroux ✍️
🔗
🔗 youtube.com/watch?v=qSoe...

🔗 youtube.com/watch?v=qSoe...
🔗 www.anthropic.com/ne...
1/8

🔗 www.anthropic.com/ne...
1/8
🔗

🔗
Here’s how the system works and why it won’t be enough.
🔗

Here’s how the system works and why it won’t be enough.
🔗
🔗 techcrunch.com/2025/...
1/2

🔗 techcrunch.com/2025/...
1/2
Social engineering is the key here...
1/2

Social engineering is the key here...
1/2
1/6

1/6
🔗 www.cnn.com/2025/11/11/p...

🔗 www.cnn.com/2025/11/11/p...


