
Stefano Tessaro
@stefanotessaro.bsky.social
Professor at the University of Washington, Paul G. Allen School of Computer Science & Engineering @uwcse.bsky.social
Working on cryptography, theoretical computer science, and computer security.
https://homes.cs.washington.edu/~tessaro/
Working on cryptography, theoretical computer science, and computer security.
https://homes.cs.washington.edu/~tessaro/
Reposted by Stefano Tessaro
Join us at the UW Paul G. Allen School of Computer Science & Engineering. We are hiring tenure-track faculty positions. Apply here: apply.interfolio.com/174303
Apply - Interfolio
{{$ctrl.$state.data.pageTitle}} - Apply - Interfolio
apply.interfolio.com
October 28, 2025 at 8:55 PM
Join us at the UW Paul G. Allen School of Computer Science & Engineering. We are hiring tenure-track faculty positions. Apply here: apply.interfolio.com/174303
Reposted by Stefano Tessaro
Tight Security for BBS Signatures (Rutchathon Chairattana-Apirom, Dennis Hofheinz, Stefano Tessaro) ia.cr/2025/1973


October 25, 2025 at 6:20 PM
Tight Security for BBS Signatures (Rutchathon Chairattana-Apirom, Dennis Hofheinz, Stefano Tessaro) ia.cr/2025/1973
Reposted by Stefano Tessaro
Adaptively Secure Partially Non-Interactive Threshold Schnorr Signatures in the AGM (Renas Bacho, Yanbo Chen, Julian Loss, Stefano Tessaro, Chenzhi Zhu) ia.cr/2025/1953


October 20, 2025 at 1:40 PM
Adaptively Secure Partially Non-Interactive Threshold Schnorr Signatures in the AGM (Renas Bacho, Yanbo Chen, Julian Loss, Stefano Tessaro, Chenzhi Zhu) ia.cr/2025/1953
Reposted by Stefano Tessaro
Fraud Mitigation in Privacy-Preserving Attribution (Rutchathon Chairattana-Apirom, Stefano Tessaro, Nirvan Tyagi) ia.cr/2025/1891


October 12, 2025 at 9:19 PM
Fraud Mitigation in Privacy-Preserving Attribution (Rutchathon Chairattana-Apirom, Stefano Tessaro, Nirvan Tyagi) ia.cr/2025/1891
Reposted by Stefano Tessaro
A Note on Feedback-PRF Mode of KDF from NIST SP 800-108 (Ritam Bhaumik, Avijit Dutta, Tetsu Iwata, Ashwin Jha, Kazuhiko Minematsu, Mridul Nandi, Yu Sasaki, Meltem Sönmez Turan, Stefano Tessaro) ia.cr/2025/1586

September 5, 2025 at 11:33 AM
A Note on Feedback-PRF Mode of KDF from NIST SP 800-108 (Ritam Bhaumik, Avijit Dutta, Tetsu Iwata, Ashwin Jha, Kazuhiko Minematsu, Mridul Nandi, Yu Sasaki, Meltem Sönmez Turan, Stefano Tessaro) ia.cr/2025/1586
Reposted by Stefano Tessaro
Cryptographic Treatment of Key Control Security – In Light of NIST SP 800-108 (Ritam Bhaumik, Avijit Dutta, Akiko Inoue, Tetsu Iwata, Ashwin Jha, Kazuhiko Minematsu, Mridul Nandi, Yu Sasaki, Meltem Sönmez Turan, Stefano Tessaro) ia.cr/2025/1123
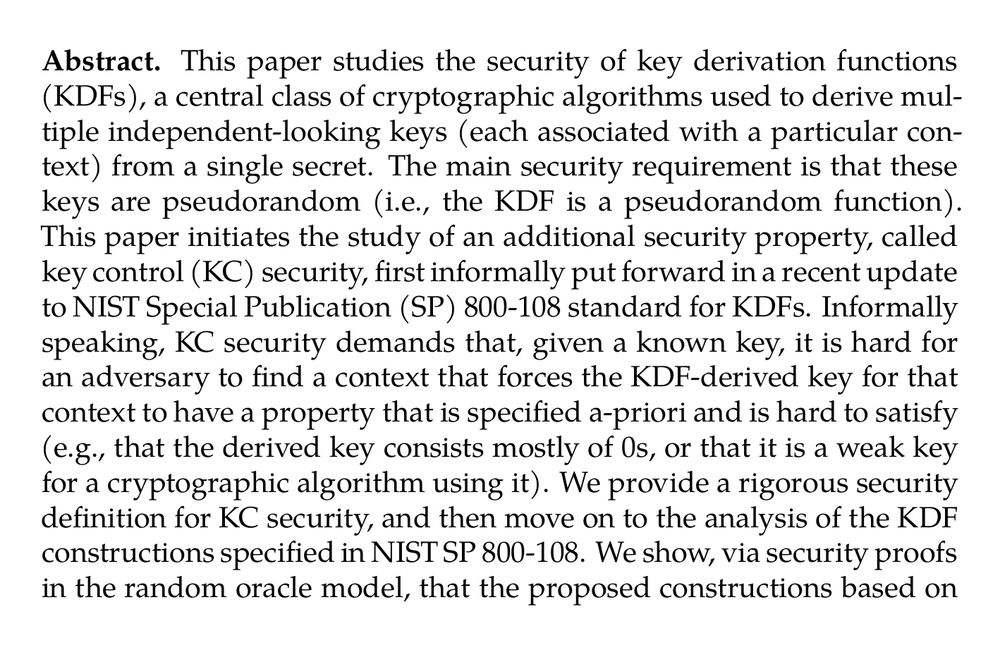

June 16, 2025 at 9:21 PM
Cryptographic Treatment of Key Control Security – In Light of NIST SP 800-108 (Ritam Bhaumik, Avijit Dutta, Akiko Inoue, Tetsu Iwata, Ashwin Jha, Kazuhiko Minematsu, Mridul Nandi, Yu Sasaki, Meltem Sönmez Turan, Stefano Tessaro) ia.cr/2025/1123
Reposted by Stefano Tessaro
On the Concrete Security of BBS/BBS+ Signatures (Rutchathon Chairattana-Apirom, Stefano Tessaro) ia.cr/2025/1093


June 12, 2025 at 12:26 PM
On the Concrete Security of BBS/BBS+ Signatures (Rutchathon Chairattana-Apirom, Stefano Tessaro) ia.cr/2025/1093
Reposted by Stefano Tessaro
On the Adaptive Security of FROST (Elizabeth Crites, Jonathan Katz, Chelsea Komlo, Stefano Tessaro, Chenzhi Zhu) ia.cr/2025/1061
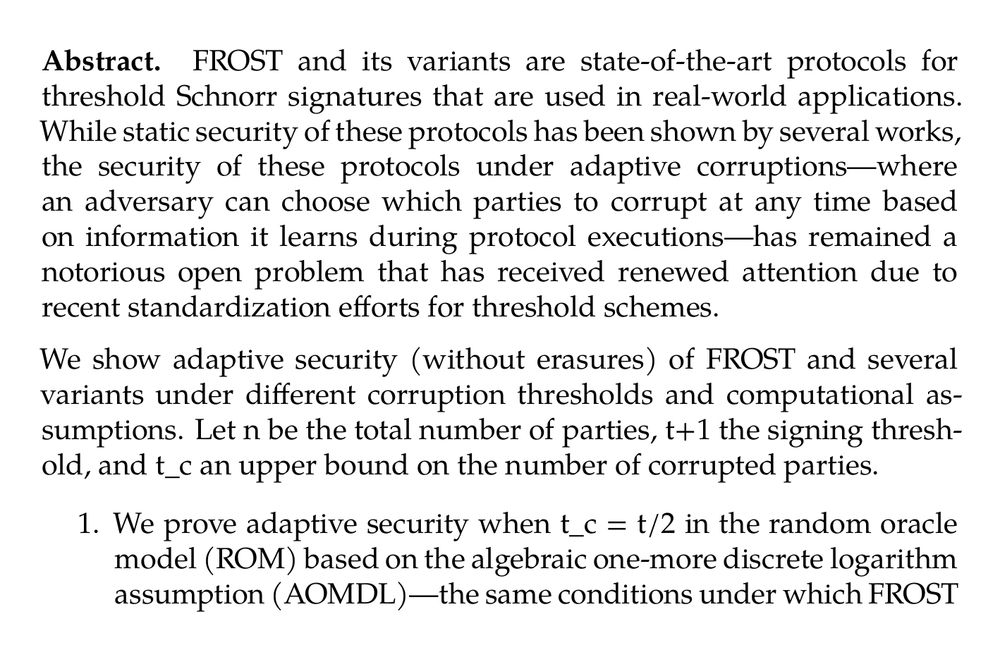
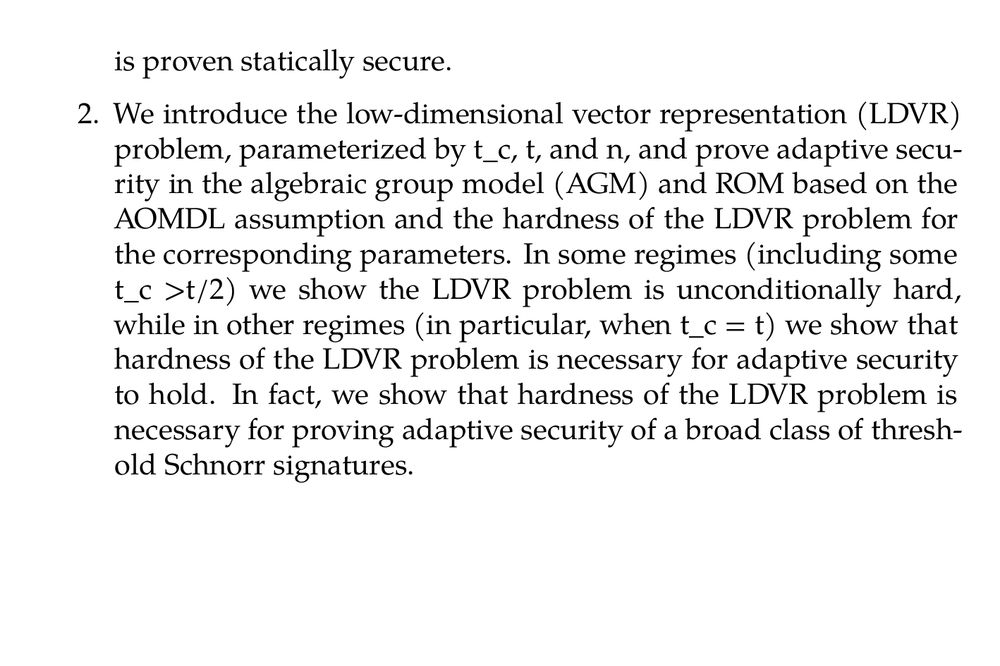
June 9, 2025 at 3:28 AM
On the Adaptive Security of FROST (Elizabeth Crites, Jonathan Katz, Chelsea Komlo, Stefano Tessaro, Chenzhi Zhu) ia.cr/2025/1061
Reposted by Stefano Tessaro
Everlasting Anonymous Rate-Limited Tokens (Rutchathon Chairattana-Apirom, Nico Döttling, Anna Lysyanskaya, Stefano Tessaro) ia.cr/2025/1030


June 3, 2025 at 8:16 PM
Everlasting Anonymous Rate-Limited Tokens (Rutchathon Chairattana-Apirom, Nico Döttling, Anna Lysyanskaya, Stefano Tessaro) ia.cr/2025/1030
Successful escape from PNW weather - Spring Break edition

March 23, 2025 at 8:38 PM
Successful escape from PNW weather - Spring Break edition
New paper!
Server-Aided Anonymous Credentials (Rutchathon Chairattana-Apirom, Franklin Harding, Anna Lysyanskaya, Stefano Tessaro) ia.cr/2025/513


March 21, 2025 at 2:32 AM
New paper!
Reposted by Stefano Tessaro
We have extended the submission deadline for the International Workshop on Foundations and Applications of Privacy-Enhancing Cryptography (PrivCrypt) by two weeks to April 4, 2025, AoE. Please help spread the word and consider submitting your work to join us in Munich in Summer 😎
We are organising the International Workshop on Foundations and Applications of Privacy-Enhancing Cryptography (PrivCrypt) - co-located with ACNS 2025 end of June in beautiful Munich.
Submission deadline is March 21, 2025 (AoE).
Please help spread the word! 🙏
privcryptworkshop.github.io
Submission deadline is March 21, 2025 (AoE).
Please help spread the word! 🙏
privcryptworkshop.github.io
PrivCrypt 2025
privcryptworkshop.github.io
March 20, 2025 at 8:12 AM
We have extended the submission deadline for the International Workshop on Foundations and Applications of Privacy-Enhancing Cryptography (PrivCrypt) by two weeks to April 4, 2025, AoE. Please help spread the word and consider submitting your work to join us in Munich in Summer 😎
Reposted by Stefano Tessaro
Reposted by Stefano Tessaro
The Algebraic One-More MISIS Problem and Applications to Threshold Signatures (Chenzhi Zhu, Stefano Tessaro) ia.cr/2025/436
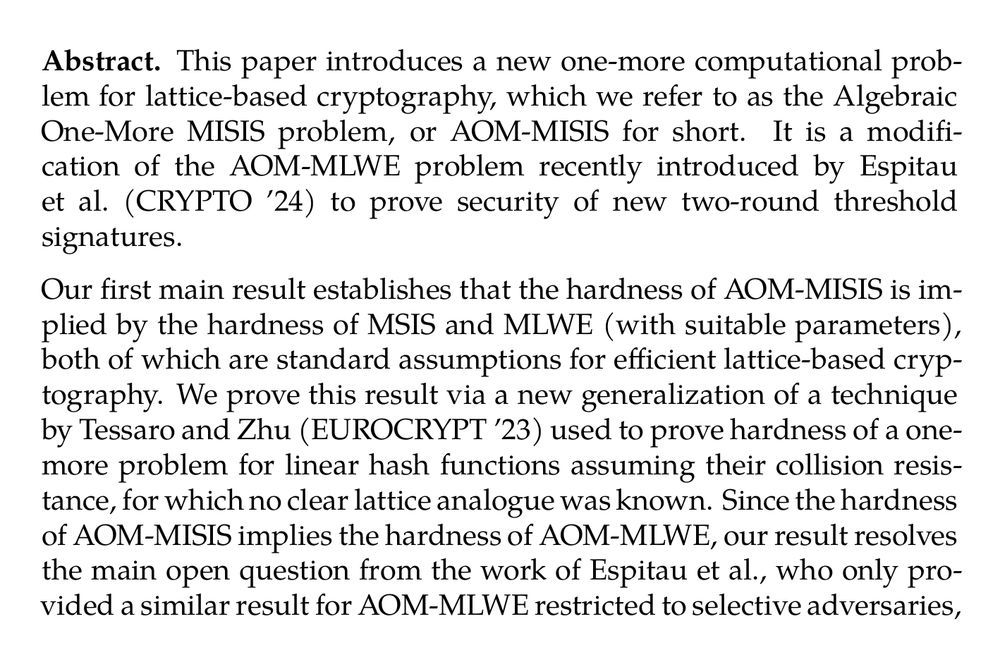

March 8, 2025 at 1:37 AM
The Algebraic One-More MISIS Problem and Applications to Threshold Signatures (Chenzhi Zhu, Stefano Tessaro) ia.cr/2025/436
Reposted by Stefano Tessaro
New paper: Simulating Time With Square-Root Space
people.csail.mit.edu/rrw/time-vs-...
It's still hard for me to believe it myself, but I seem to have shown that TIME[t] is contained in SPACE[sqrt{t log t}].
To appear in STOC. Comments are very welcome!
people.csail.mit.edu/rrw/time-vs-...
It's still hard for me to believe it myself, but I seem to have shown that TIME[t] is contained in SPACE[sqrt{t log t}].
To appear in STOC. Comments are very welcome!
people.csail.mit.edu
February 21, 2025 at 10:19 PM
New paper: Simulating Time With Square-Root Space
people.csail.mit.edu/rrw/time-vs-...
It's still hard for me to believe it myself, but I seem to have shown that TIME[t] is contained in SPACE[sqrt{t log t}].
To appear in STOC. Comments are very welcome!
people.csail.mit.edu/rrw/time-vs-...
It's still hard for me to believe it myself, but I seem to have shown that TIME[t] is contained in SPACE[sqrt{t log t}].
To appear in STOC. Comments are very welcome!
Reposted by Stefano Tessaro
1. Today the NIH director issued a new directive slashing overhead rates to 15%.
I want to provide some context on what that means and why it matters.
grants.nih.gov/grants/guide...
I want to provide some context on what that means and why it matters.
grants.nih.gov/grants/guide...
NOT-OD-25-068: Supplemental Guidance to the 2024 NIH Grants Policy Statement: Indirect Cost Rates
NIH Funding Opportunities and Notices in the NIH Guide for Grants and Contracts: Supplemental Guidance to the 2024 NIH Grants Policy Statement: Indirect Cost Rates NOT-OD-25-068. OD
grants.nih.gov
February 8, 2025 at 12:18 AM
1. Today the NIH director issued a new directive slashing overhead rates to 15%.
I want to provide some context on what that means and why it matters.
grants.nih.gov/grants/guide...
I want to provide some context on what that means and why it matters.
grants.nih.gov/grants/guide...
Reposted by Stefano Tessaro
NSF is getting back to business due to a court order.
Order: nsf-gov-resources.ns...
Details: new.nsf.gov/executiv...
Order: nsf-gov-resources.ns...
Details: new.nsf.gov/executiv...
February 2, 2025 at 9:31 PM
NSF is getting back to business due to a court order.
Order: nsf-gov-resources.ns...
Details: new.nsf.gov/executiv...
Order: nsf-gov-resources.ns...
Details: new.nsf.gov/executiv...
I found this video (www.youtube.com/watch?v=CiOy...) more informative than any news article this morning. Not an expert, but sadly this appears to be a significant failure in designing procedures meant to be fault-tolerant.
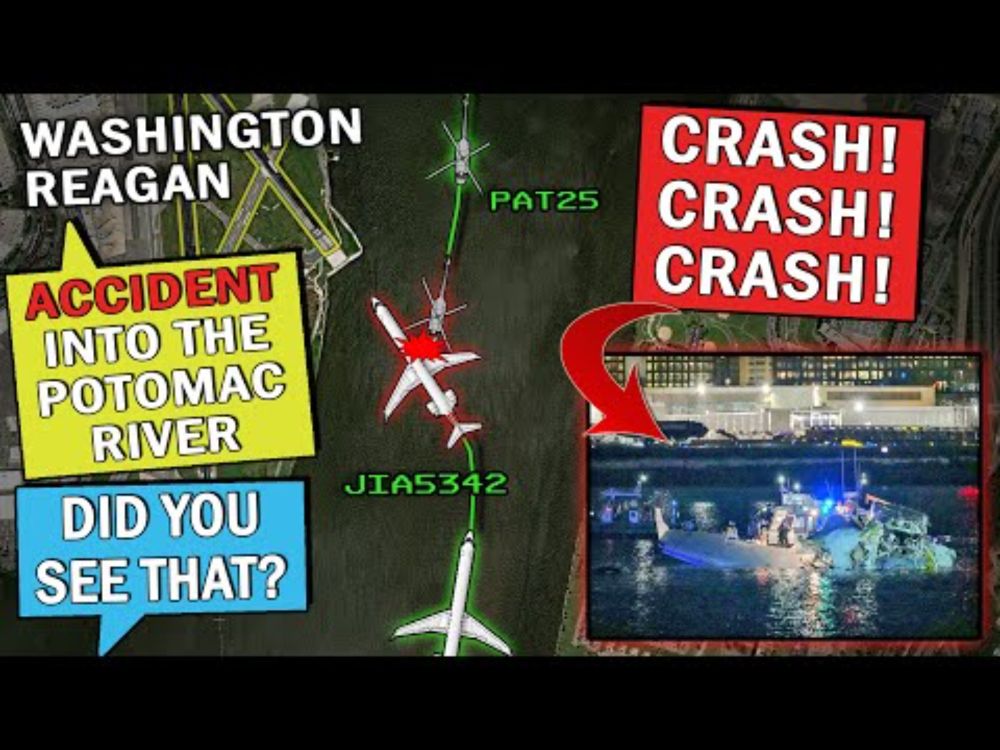
Audio of MID-AIR CRASH into Potomac River | Regional Jet and Black Hawk Helicopter
YouTube video by VASAviation -
www.youtube.com
January 30, 2025 at 3:50 PM
I found this video (www.youtube.com/watch?v=CiOy...) more informative than any news article this morning. Not an expert, but sadly this appears to be a significant failure in designing procedures meant to be fault-tolerant.
I wonder if we can attack more examples where (1) circuits are adaptively chosen by the adversary, and (2) security proof is in the ROM. It always felt like playing with fire (because ROM does not model potential circuit dependence on the hash function), and this work nicely confirms the concern.
How to Prove False Statements: Practical Attacks on Fiat-Shamir (Dmitry Khovratovich, Ron D. Rothblum, Lev Soukhanov) ia.cr/2025/118


January 27, 2025 at 1:40 PM
I wonder if we can attack more examples where (1) circuits are adaptively chosen by the adversary, and (2) security proof is in the ROM. It always felt like playing with fire (because ROM does not model potential circuit dependence on the hash function), and this work nicely confirms the concern.
Successful escape from the PNW rain

January 3, 2025 at 4:34 AM
Successful escape from the PNW rain
I guess this is the end of beyond-birthday security research?
Great to see NIST take up a wide block cipher mode! At AWS we have to carefully engineer around the 128-bit safety limits. Otherwise hyper-scale systems like VPC, S3, and EBS would exceed those limits in seconds! 256-bits is much more misuse-proof.
csrc.nist.gov/News/2024/ni...
csrc.nist.gov/News/2024/ni...
NIST Proposes to Standardize a Wider Variant of AES | CSRC
NIST indicated its interest in vetting another Rijndael variant for approval: Rijndael with 256-bit blocks (i.e., Rijndael-256) with a single key size of 256-bits. NIST plans to develop a draft standa...
csrc.nist.gov
December 26, 2024 at 12:40 AM
I guess this is the end of beyond-birthday security research?


