Eduardo Vela
@sirdarckcat.bsky.social
Reposted by Eduardo Vela
Google security researchers have improved the Retbleed CPU side-channel attack to increase exfiltration speed.
The attack can now leak data at 13 KB/s, which is fast enough to be used in modern cloud environments.
bughunters.google.com/blog/6243730...
The attack can now leak data at 13 KB/s, which is fast enough to be used in modern cloud environments.
bughunters.google.com/blog/6243730...

Blog: Exploiting Retbleed in the real world
Curious to hear about our experience exploiting Retbleed (a security vulnerability affecting modern CPUs)? Then check out this post to see how we pushed the boundaries of Retbleed exploitation and und...
bughunters.google.com
August 7, 2025 at 4:32 PM
Google security researchers have improved the Retbleed CPU side-channel attack to increase exfiltration speed.
The attack can now leak data at 13 KB/s, which is fast enough to be used in modern cloud environments.
bughunters.google.com/blog/6243730...
The attack can now leak data at 13 KB/s, which is fast enough to be used in modern cloud environments.
bughunters.google.com/blog/6243730...
Reposted by Eduardo Vela
Google published details on EntrySign, an AMD Zen microcode signature validation vulnerability (CVE-2024-56161) that can allow threat actors to install malicious firmware: bughunters.google.com/blog/5424842...
It also released Zentool, a tool to jailbreak AMD processors: github.com/google/secur...
It also released Zentool, a tool to jailbreak AMD processors: github.com/google/secur...
March 6, 2025 at 1:42 PM
Google published details on EntrySign, an AMD Zen microcode signature validation vulnerability (CVE-2024-56161) that can allow threat actors to install malicious firmware: bughunters.google.com/blog/5424842...
It also released Zentool, a tool to jailbreak AMD processors: github.com/google/secur...
It also released Zentool, a tool to jailbreak AMD processors: github.com/google/secur...
I am such a big fan of NotebookLM.. The ability to say, hey, here are 20 papers and 3 books from this subject matter, can you please explain this problem to me? and have active in-depth Q&A helps me solve problems in new spaces so much faster. What used to take me multiple weekends now takes hours
February 9, 2025 at 8:29 PM
I am such a big fan of NotebookLM.. The ability to say, hey, here are 20 papers and 3 books from this subject matter, can you please explain this problem to me? and have active in-depth Q&A helps me solve problems in new spaces so much faster. What used to take me multiple weekends now takes hours
What type of C code is this??!

February 8, 2025 at 11:40 AM
What type of C code is this??!
Reposted by Eduardo Vela
It's out and make for a very interesting read:
github.com/google/secur...
IMO, AMD should own it and release a microcode SDK....
@sirdarckcat.bsky.social
github.com/google/secur...
IMO, AMD should own it and release a microcode SDK....
@sirdarckcat.bsky.social

AMD: Microcode Signature Verification Vulnerability
### Summary
Google Security Team has identified a security vulnerability in some AMD Zen-based CPUs. This vulnerability allows an adversary with local administrator privileges (ring 0 from outside...
github.com
February 3, 2025 at 10:12 PM
It's out and make for a very interesting read:
github.com/google/secur...
IMO, AMD should own it and release a microcode SDK....
@sirdarckcat.bsky.social
github.com/google/secur...
IMO, AMD should own it and release a microcode SDK....
@sirdarckcat.bsky.social
youtu.be/H9K45VkjKvM?... I found a video of c developers
January 14, 2025 at 10:25 PM
youtu.be/H9K45VkjKvM?... I found a video of c developers
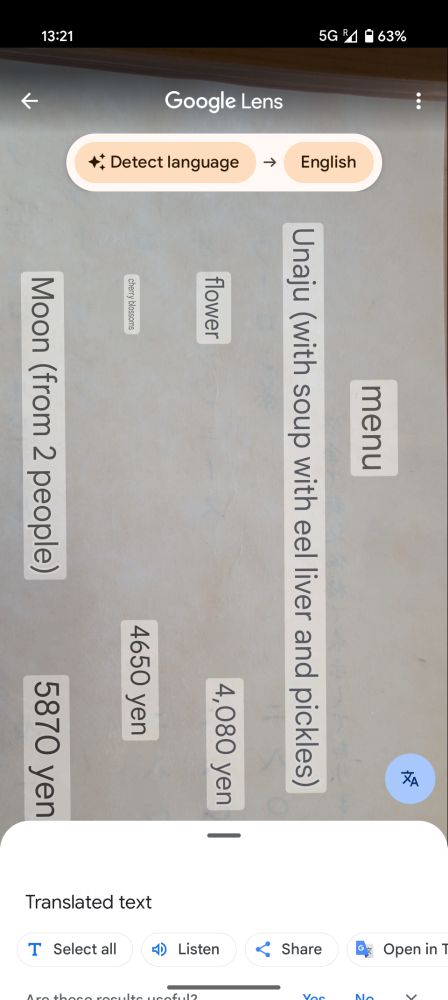
Ok I understand but can I pay 7 yen more?

January 3, 2025 at 4:34 AM
Ok I understand but can I pay 7 yen more?

January 2, 2025 at 4:25 AM
"Guan Tianfeng's role in the conspiracy was to develop and test the zero-day vulnerability" - yikes, better not develop any more vulnerabilities or fail to do proper testing or the FBI will go after you!
www.fbi.gov/wanted/cyber...
www.fbi.gov/wanted/cyber...
January 1, 2025 at 10:25 AM
"Guan Tianfeng's role in the conspiracy was to develop and test the zero-day vulnerability" - yikes, better not develop any more vulnerabilities or fail to do proper testing or the FBI will go after you!
www.fbi.gov/wanted/cyber...
www.fbi.gov/wanted/cyber...
Today I realized <input type=radio> implements roving tabindex natively.. so you can hack a css-only implementation. Forgive me ARIA, for I will sin.
December 29, 2024 at 12:45 AM
Today I realized <input type=radio> implements roving tabindex natively.. so you can hack a css-only implementation. Forgive me ARIA, for I will sin.
Is this what they call a culture shock in Japan?

December 28, 2024 at 2:59 AM
Is this what they call a culture shock in Japan?
Made a tiny game with my 6-years old cousin tonight using cursor.com - must say this was way easier than I thought, and I literally wrote zero code.
sirdarckcat.github.io/salchichon/
sirdarckcat.github.io/salchichon/
Perrito Salchichón
sirdarckcat.github.io
December 24, 2024 at 4:09 AM
Made a tiny game with my 6-years old cousin tonight using cursor.com - must say this was way easier than I thought, and I literally wrote zero code.
sirdarckcat.github.io/salchichon/
sirdarckcat.github.io/salchichon/
So one thing I want to work on the kernel explorer before we keep accumulating tech debt is accessibility.
I thought it would be cool to try and describe how I'll approach it, so this will be a 🧵 thread I'll update as I make progress.
I thought it would be cool to try and describe how I'll approach it, so this will be a 🧵 thread I'll update as I make progress.
Small preview of our kernel explorer. Still a lot of work to do!
kernelctf-dash.storage.googleapis.com/processed/v6...
kernelctf-dash.storage.googleapis.com/processed/v6...
🐧DASHing
kernelctf-dash.storage.googleapis.com
December 23, 2024 at 2:39 PM
So one thing I want to work on the kernel explorer before we keep accumulating tech debt is accessibility.
I thought it would be cool to try and describe how I'll approach it, so this will be a 🧵 thread I'll update as I make progress.
I thought it would be cool to try and describe how I'll approach it, so this will be a 🧵 thread I'll update as I make progress.
I think I would be pretty good at competitive password typing
December 21, 2024 at 4:04 PM
I think I would be pretty good at competitive password typing
Small preview of our kernel explorer. Still a lot of work to do!
kernelctf-dash.storage.googleapis.com/processed/v6...
kernelctf-dash.storage.googleapis.com/processed/v6...
🐧DASHing
kernelctf-dash.storage.googleapis.com
December 20, 2024 at 1:21 AM
Small preview of our kernel explorer. Still a lot of work to do!
kernelctf-dash.storage.googleapis.com/processed/v6...
kernelctf-dash.storage.googleapis.com/processed/v6...
I tried to implement this yesterday (kind of). It is too slow to run syz-execprog but running the compiled C reproducer was better. You can't really run ftrace (I was hoping to!) but I probably could get the info from the emulator directly. Promising, but still TBD!
It would be cool if there was a way to run Syzkaller on the browser. You just get an IDE for writing Syzkaller programs and you get coverage data, register state (like with kprobes) etc
December 2, 2024 at 6:16 AM
I tried to implement this yesterday (kind of). It is too slow to run syz-execprog but running the compiled C reproducer was better. You can't really run ftrace (I was hoping to!) but I probably could get the info from the emulator directly. Promising, but still TBD!
It would be cool if there was a way to run Syzkaller on the browser. You just get an IDE for writing Syzkaller programs and you get coverage data, register state (like with kprobes) etc
November 24, 2024 at 8:56 PM
It would be cool if there was a way to run Syzkaller on the browser. You just get an IDE for writing Syzkaller programs and you get coverage data, register state (like with kprobes) etc
blog.wokwi.com/running-gdb-... is pretty cool!

Running GDB in the Browser
GDB inside a Linux in a x86 Virtual Machine using Web Assembly running in the browser. Crazy?
blog.wokwi.com
November 21, 2024 at 6:17 PM
blog.wokwi.com/running-gdb-... is pretty cool!
So who should I follow here?

November 21, 2024 at 5:54 AM
So who should I follow here?
Can you see this?
November 18, 2024 at 8:30 PM
Can you see this?