
PortSwigger Research
@portswiggerres.bsky.social
Web security research from the team at PortSwigger.
We've updated our XSS cheat sheet to include 9 new vectors from @garethheyes.co.uk! Here are the top three, you can find the rest here: portswigger.net/web-security...

November 10, 2025 at 2:49 PM
We've updated our XSS cheat sheet to include 9 new vectors from @garethheyes.co.uk! Here are the top three, you can find the rest here: portswigger.net/web-security...
Reposted by PortSwigger Research
The recording of "HTTP/1.1 must die: the desync endgame" has now landed on YouTube. Enjoy! www.youtube.com/watch?v=zr5y...

RomHack 2025 - James “albinowax” Kettle - HTTP/1.1 Must Die! The Desync Endgame
YouTube video by Cyber Saiyan
www.youtube.com
October 8, 2025 at 2:16 PM
The recording of "HTTP/1.1 must die: the desync endgame" has now landed on YouTube. Enjoy! www.youtube.com/watch?v=zr5y...
Reposted by PortSwigger Research
I’m excited to announce that I’ll be presenting The Fragile Lock: Novel Bypasses for SAML Authentication at Black Hat Europe! In this talk, I’ll show how I was able to continuously bypass security patches to achieve complete auth bypass for major libraries. #BHEU @blackhatevents.bsky.social

October 7, 2025 at 2:55 PM
I’m excited to announce that I’ll be presenting The Fragile Lock: Novel Bypasses for SAML Authentication at Black Hat Europe! In this talk, I’ll show how I was able to continuously bypass security patches to achieve complete auth bypass for major libraries. #BHEU @blackhatevents.bsky.social
Reposted by PortSwigger Research
HTTP/1.1 Must Die is coming to #romhack2025 as the keynote! In-person tickets are sold out but you can still watch the livestream. This is your last chance to catch it live - register to watch here:
www.youtube.com/watch?v=T009...
www.youtube.com/watch?v=T009...

RomHack Conference 2025 Live Stream
YouTube video by Cyber Saiyan
www.youtube.com
September 18, 2025 at 1:40 PM
HTTP/1.1 Must Die is coming to #romhack2025 as the keynote! In-person tickets are sold out but you can still watch the livestream. This is your last chance to catch it live - register to watch here:
www.youtube.com/watch?v=T009...
www.youtube.com/watch?v=T009...
Reposted by PortSwigger Research
I just published a Repeater feature to make it easier to explore request smuggling. It repeats your request until the status code changes. It's called "Retry until success" and you can install it via the Extensibility helper bapp.

August 20, 2025 at 3:02 PM
I just published a Repeater feature to make it easier to explore request smuggling. It repeats your request until the status code changes. It's called "Retry until success" and you can install it via the Extensibility helper bapp.
Reposted by PortSwigger Research
Watch HTTP/1.1 Must Die live today at 1630 PST!
- In person at #defcon33 track 1, main stage
- Livestream via YouTube: www.youtube.com/watch?v=ssln...
- In person at #defcon33 track 1, main stage
- Livestream via YouTube: www.youtube.com/watch?v=ssln...

August 8, 2025 at 6:46 PM
Watch HTTP/1.1 Must Die live today at 1630 PST!
- In person at #defcon33 track 1, main stage
- Livestream via YouTube: www.youtube.com/watch?v=ssln...
- In person at #defcon33 track 1, main stage
- Livestream via YouTube: www.youtube.com/watch?v=ssln...
Reposted by PortSwigger Research
The whitepaper is live! Learn how to win the HTTP desync endgame... and why HTTP/1.1 needs to die: http1mustdie.com

HTTP/1.1 Must Die
Upstream HTTP/1.1 is inherently insecure, and routinely exposes millions of websites to hostile takeover. Join the mission to kill HTTP/1.1 now
http1mustdie.com
August 6, 2025 at 11:43 PM
The whitepaper is live! Learn how to win the HTTP desync endgame... and why HTTP/1.1 needs to die: http1mustdie.com
Reposted by PortSwigger Research
It's easy to bash vulnerabilities with logos but... I couldn't resist, say hello to http1mustdie.com :)
July 18, 2025 at 12:56 PM
It's easy to bash vulnerabilities with logos but... I couldn't resist, say hello to http1mustdie.com :)
Reposted by PortSwigger Research
I'm thrilled to announce "HTTP/1 Must Die! The Desync Endgame" is coming to #DEFCON33! This talk will feature multiple new classes of desync attack, mass exploitation spanning multiple CDNs, and over $200k in bug bounties. See you there!

June 10, 2025 at 2:21 PM
I'm thrilled to announce "HTTP/1 Must Die! The Desync Endgame" is coming to #DEFCON33! This talk will feature multiple new classes of desync attack, mass exploitation spanning multiple CDNs, and over $200k in bug bounties. See you there!
Reposted by PortSwigger Research
Thrilled to finally release my latest research "The Single-Packet Shovel: Digging for Desync-Powered Request Tunnelling".
Desync vulnerabilities stemming from HP2 downgrading continue to plague even the largest vendors, have a read to find out how!
Desync vulnerabilities stemming from HP2 downgrading continue to plague even the largest vendors, have a read to find out how!
The Single-Packet Shovel: Digging for Desync-Powered Request Tunnelling
In this paper I will reveal the discovery of wide-spread cases of request tunnelling in applications powered by popular servers including IIS, Azure Front Door and AWS' application load balancer inclu...
www.assured.se
May 22, 2025 at 4:03 PM
Thrilled to finally release my latest research "The Single-Packet Shovel: Digging for Desync-Powered Request Tunnelling".
Desync vulnerabilities stemming from HP2 downgrading continue to plague even the largest vendors, have a read to find out how!
Desync vulnerabilities stemming from HP2 downgrading continue to plague even the largest vendors, have a read to find out how!
Reposted by PortSwigger Research
The recording of my recent AMA with the Burp Suite Discord community has just landed on YouTube! 40 minutes of unscripted Q&A on security research, AI, and Burp Suite: youtu.be/mgmUZ9odkvU

AMA: James Kettle on Burp Suite, AI & Security Research
YouTube video by PortSwigger
youtu.be
May 27, 2025 at 12:30 PM
The recording of my recent AMA with the Burp Suite Discord community has just landed on YouTube! 40 minutes of unscripted Q&A on security research, AI, and Burp Suite: youtu.be/mgmUZ9odkvU
Reposted by PortSwigger Research
Firefox now opens the door to URL-based XSS payload smuggling too. Yep, even more ways to sneak past filters using the window name and clever URL tricks. Link to vectors👇
portswigger.net/web-security...
portswigger.net/web-security...


May 27, 2025 at 1:55 PM
Firefox now opens the door to URL-based XSS payload smuggling too. Yep, even more ways to sneak past filters using the window name and clever URL tricks. Link to vectors👇
portswigger.net/web-security...
portswigger.net/web-security...
Reposted by PortSwigger Research
I'm excited to announce I'll be delivering the keynote at RomHack this September! I can't share the title just yet but it's going to be a good one. See you in Rome!
romhack.io
romhack.io

RomHack Conference, Training and Camp
RomHack is a format made by the non-profit association Cyber Saiyan and composed by a Conference a Training session and a Hacker Camp.
romhack.io
March 17, 2025 at 12:38 PM
I'm excited to announce I'll be delivering the keynote at RomHack this September! I can't share the title just yet but it's going to be a good one. See you in Rome!
romhack.io
romhack.io
Reposted by PortSwigger Research
I’m excited to introduce Namespace Confusion, a novel attack discovered during Gareth's and mySAML Roulette: The Hacker Always Wins research. We uncovered a brutal attack on XML signature validation that destroys authentication in Ruby-SAML!

March 18, 2025 at 3:01 PM
I’m excited to introduce Namespace Confusion, a novel attack discovered during Gareth's and mySAML Roulette: The Hacker Always Wins research. We uncovered a brutal attack on XML signature validation that destroys authentication in Ruby-SAML!
Reposted by PortSwigger Research
You might have noticed that the recent SAML writeups omit some crucial details. In "SAML roulette: the hacker always wins", we share everything you need to know for a complete unauthenticated exploit on ruby-saml, using GitLab as a case-study.
portswigger.net/research/sam...
portswigger.net/research/sam...
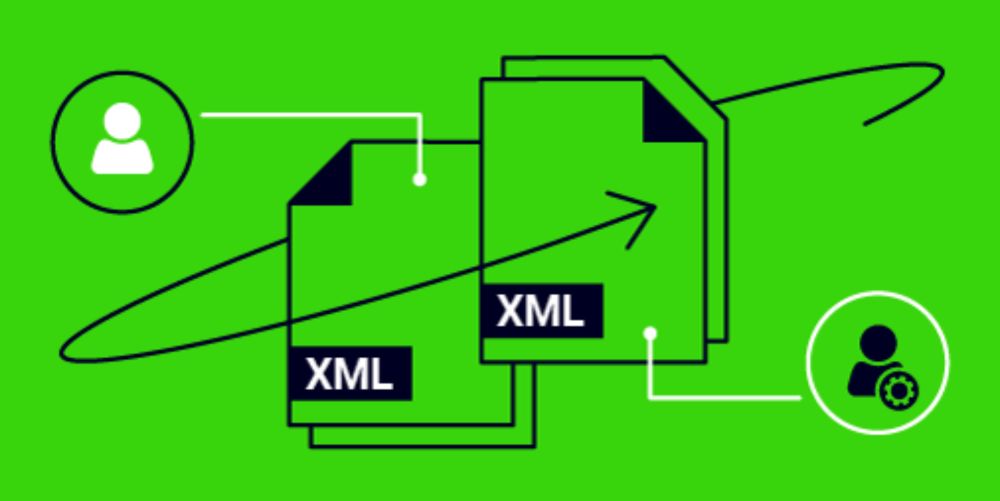
SAML roulette: the hacker always wins
Introduction In this post, we’ll show precisely how to chain round-trip attacks and namespace confusion to achieve unauthenticated admin access on GitLab Enterprise by exploiting the ruby-saml library
portswigger.net
March 18, 2025 at 2:57 PM
You might have noticed that the recent SAML writeups omit some crucial details. In "SAML roulette: the hacker always wins", we share everything you need to know for a complete unauthenticated exploit on ruby-saml, using GitLab as a case-study.
portswigger.net/research/sam...
portswigger.net/research/sam...
Reposted by PortSwigger Research
We've just released Shadow Repeater, for AI-enhanced manual testing. Simply use Burp Repeater as you normally would, and behind the scenes Shadow Repeater will learn from your attacks, try payload permutations, and report any discoveries via Organizer.
portswigger.net/research/sha...
portswigger.net/research/sha...
February 20, 2025 at 1:24 PM
We've just released Shadow Repeater, for AI-enhanced manual testing. Simply use Burp Repeater as you normally would, and behind the scenes Shadow Repeater will learn from your attacks, try payload permutations, and report any discoveries via Organizer.
portswigger.net/research/sha...
portswigger.net/research/sha...
Reposted by PortSwigger Research
@jameskettle.com casually dropping info on the craziest sounding AI-enabled burp extension. Can you imagine messing about with a suspicious LFI candidate in repeater and without you doing anything differently than you do today, burp suddenly spits back the right payload?

Top 10 Web Hacking Techniques of 2024 - James Kettle - ASW #318
YouTube video by Security Weekly - A CRA Resource
youtu.be
February 18, 2025 at 3:37 PM
@jameskettle.com casually dropping info on the craziest sounding AI-enabled burp extension. Can you imagine messing about with a suspicious LFI candidate in repeater and without you doing anything differently than you do today, burp suddenly spits back the right payload?
Reposted by PortSwigger Research
We've updated our URL validation bypass cheat sheet with this shiny Domain allow list bypass payload contributed by dyak0xdb!

February 6, 2025 at 9:17 AM
We've updated our URL validation bypass cheat sheet with this shiny Domain allow list bypass payload contributed by dyak0xdb!
The results are in! We're proud to announce the Top 10 Web Hacking Techniques of 2024! portswigger.net/research/top...

Top 10 web hacking techniques of 2024
Welcome to the Top 10 Web Hacking Techniques of 2024, the 18th edition of our annual community-powered effort to identify the most innovative must-read web security research published in the last year
portswigger.net
February 4, 2025 at 3:02 PM
The results are in! We're proud to announce the Top 10 Web Hacking Techniques of 2024! portswigger.net/research/top...
Reposted by PortSwigger Research
I'm super proud to announce my weekend project and latest #burpsuite extension written in Kotlin! 👾 I love hacking, finding problems or challenges during and the ability to fix them whilst improving my code-foo.
Introducing 🗒️ StickyBurp! 🗒️ -> github.com/GangGreenTem...
@portswiggerres.bsky.social
Introducing 🗒️ StickyBurp! 🗒️ -> github.com/GangGreenTem...
@portswiggerres.bsky.social
December 23, 2024 at 9:05 PM
I'm super proud to announce my weekend project and latest #burpsuite extension written in Kotlin! 👾 I love hacking, finding problems or challenges during and the ability to fix them whilst improving my code-foo.
Introducing 🗒️ StickyBurp! 🗒️ -> github.com/GangGreenTem...
@portswiggerres.bsky.social
Introducing 🗒️ StickyBurp! 🗒️ -> github.com/GangGreenTem...
@portswiggerres.bsky.social
Reposted by PortSwigger Research
Nominations are now open for the Top 10 Web Hacking Techniques of 2024! Browse the contestants and submit your own here:
portswigger.net/research/top...
portswigger.net/research/top...

Top ten web hacking techniques of 2024: nominations open
Nominations are now open for the top 10 new web hacking techniques of 2024! Every year, security researchers from all over the world share their latest findings via blog posts, presentations, PoCs, an
portswigger.net
January 8, 2025 at 2:09 PM
Nominations are now open for the Top 10 Web Hacking Techniques of 2024! Browse the contestants and submit your own here:
portswigger.net/research/top...
portswigger.net/research/top...
Did you know you can use an ancient magic cookie to downgrade parsers and bypass WAFs?! Hope you enjoy this quality bit of RFC-diving from @d4d89704243.bsky.social!
portswigger.net/research/byp...
portswigger.net/research/byp...

Bypassing WAFs with the phantom $Version cookie
HTTP cookies often control critical website features, but their long and convoluted history exposes them to parser discrepancy vulnerabilities. In this post, I'll explore some dangerous, lesser-known
portswigger.net
December 4, 2024 at 3:17 PM
Did you know you can use an ancient magic cookie to downgrade parsers and bypass WAFs?! Hope you enjoy this quality bit of RFC-diving from @d4d89704243.bsky.social!
portswigger.net/research/byp...
portswigger.net/research/byp...
Reposted by PortSwigger Research
We’re finally live! You can now watch “Listen to the whispers: web timing attacks that actually work” on YouTube: youtube.com/watch?v=zOPj...
YouTube
Share your videos with friends, family, and the world
youtube.com
November 17, 2024 at 11:17 AM
We’re finally live! You can now watch “Listen to the whispers: web timing attacks that actually work” on YouTube: youtube.com/watch?v=zOPj...
Reposted by PortSwigger Research
In case you missed it...the DEF CON video of my talk 'Splitting the Email Atom' is finally here! 🚀 Watch me demonstrate how to turn an email address into RCE on Joomla, bypass Zero Trust defences, and exploit parser discrepancies for misrouted emails. Don’t miss it:
youtu.be/JERBqoTllaE?...
youtu.be/JERBqoTllaE?...

DEF CON 32 - Splitting the email atom exploiting parsers to bypass access controls - Gareth Heyes
YouTube video by DEFCONConference
youtu.be
November 22, 2024 at 7:27 AM
In case you missed it...the DEF CON video of my talk 'Splitting the Email Atom' is finally here! 🚀 Watch me demonstrate how to turn an email address into RCE on Joomla, bypass Zero Trust defences, and exploit parser discrepancies for misrouted emails. Don’t miss it:
youtu.be/JERBqoTllaE?...
youtu.be/JERBqoTllaE?...
Reposted by PortSwigger Research
If you like bounties, I highly recommend this presentation from Martin Doyhenard on novel web cache deception techniques. It comes with Web Security Academy labs too!
www.youtube.com/watch?v=70yy...
www.youtube.com/watch?v=70yy...

DEF CON 32 - Gotta Cache ‘em all bending the rules of web cache exploitation - Martin Doyhenard
YouTube video by DEFCONConference
www.youtube.com
November 26, 2024 at 2:33 PM
If you like bounties, I highly recommend this presentation from Martin Doyhenard on novel web cache deception techniques. It comes with Web Security Academy labs too!
www.youtube.com/watch?v=70yy...
www.youtube.com/watch?v=70yy...

