Website: https://synthesis.to
Details: shop.binary.ninja/products/re-...

Details: shop.binary.ninja/products/re-...
It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries.
github.com/mrphrazer/ob...
It collapses call-heavy code into a single function; analysis, constant propagation, DCE and other analyses work across boundaries.
github.com/mrphrazer/ob...
Slides: synthesis.to/presentation...
Plugin: github.com/mrphrazer/ob...
Slides: synthesis.to/presentation...
Plugin: github.com/mrphrazer/ob...
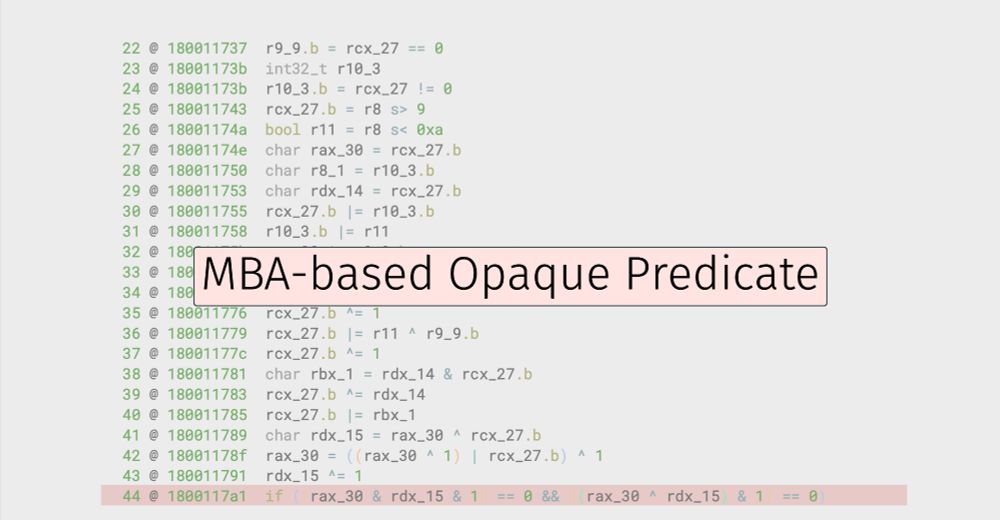
Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly.
Co-authored by @nicolo.dev; available in the plugin manager.
github.com/mrphrazer/ob...
Simplifies arithmetic obfuscation (MBA) directly in the decompiler (see demo below). Also identifies functions with corrupted disassembly.
Co-authored by @nicolo.dev; available in the plugin manager.
github.com/mrphrazer/ob...
Learn advanced techniques to defeat state-of-the-art obfuscation in DRMs & APT malware.
www.hexacon.fr/trainer/blaz...

Learn advanced techniques to defeat state-of-the-art obfuscation in DRMs & APT malware.
www.hexacon.fr/trainer/blaz...
Details: cfp.recon.cx/recon-2025/f...
I'll also give a training: recon.cx/2025/trainin...

Details: cfp.recon.cx/recon-2025/f...
I'll also give a training: recon.cx/2025/trainin...
Duplicated Subgraphs uses iterative context hashing to spot repeated multi-block code. We merge each block’s signature with its successors over multiple rounds for efficiency.
Link: github.com/mrphrazer/ob...
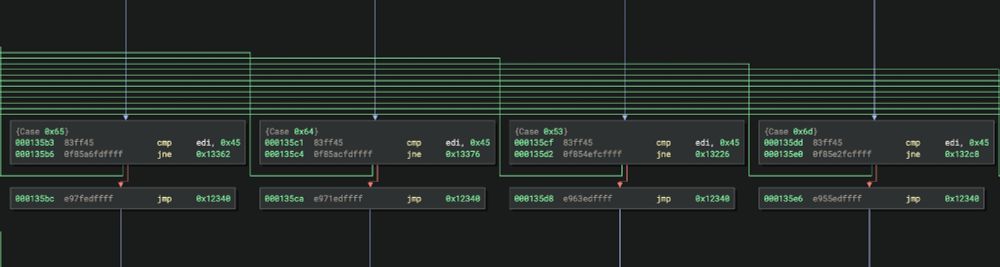
Duplicated Subgraphs uses iterative context hashing to spot repeated multi-block code. We merge each block’s signature with its successors over multiple rounds for efficiency.
Link: github.com/mrphrazer/ob...
Details & Register: recon.cx/2025/trainin...

Details & Register: recon.cx/2025/trainin...

