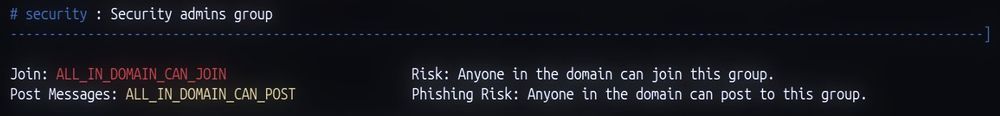
If a threat actor can post as security@<yourorganization>.com, they can send out extremely successful internal phishing emails
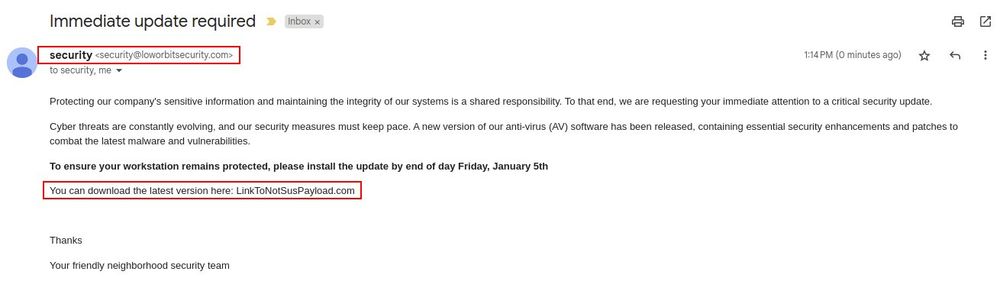
If a threat actor can post as security@<yourorganization>.com, they can send out extremely successful internal phishing emails
Who knows what level of access being in this group would give an attacker.
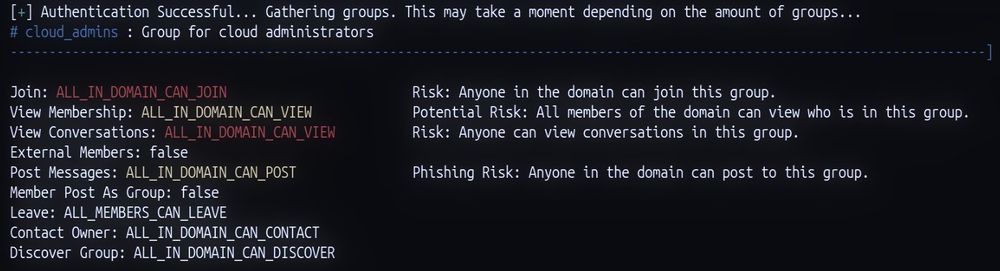
Who knows what level of access being in this group would give an attacker.
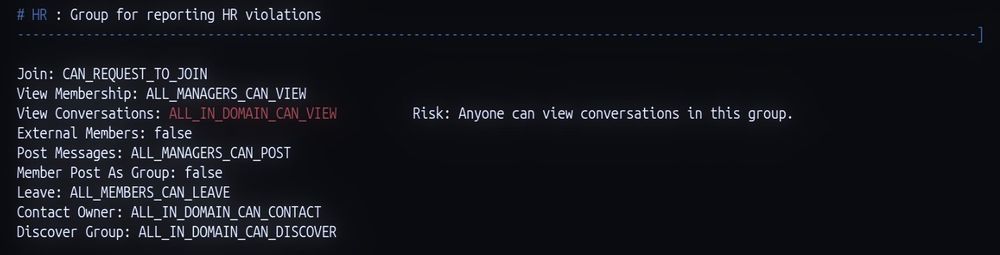
In this example everyone in the domain can view the conversations of the HR Group.
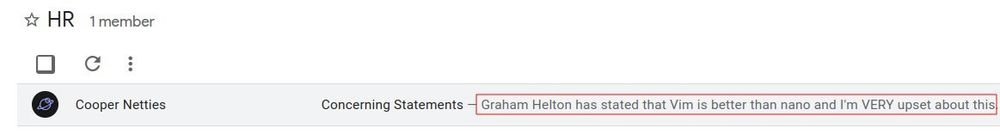
In this example everyone in the domain can view the conversations of the HR Group.