
linktr.ee/hackwithintigriti
Many apps implement strict CSPs to block XSS, but if they whitelist trusted domains like Google, YT, or GH, you can often bypass these restrictions using JSONP endpoints!


Many apps implement strict CSPs to block XSS, but if they whitelist trusted domains like Google, YT, or GH, you can often bypass these restrictions using JSONP endpoints!
Today, we're tackling one of the trickiest vulnerability types: DOM-based XSS! 🤠
DOM-based XSS vulnerabilities are seemingly harder to spot due to their limited visibility.


Today, we're tackling one of the trickiest vulnerability types: DOM-based XSS! 🤠
DOM-based XSS vulnerabilities are seemingly harder to spot due to their limited visibility.
Today, we're focusing specifically on Cloudflare R2 buckets and a feature that's often misconfigured: R2 dev! 🤠


Today, we're focusing specifically on Cloudflare R2 buckets and a feature that's often misconfigured: R2 dev! 🤠
Yesterday, we covered a simple method to enumerate backend technologies with high accuracy. Today, we're hunting for exposed cloud storage buckets using Google!

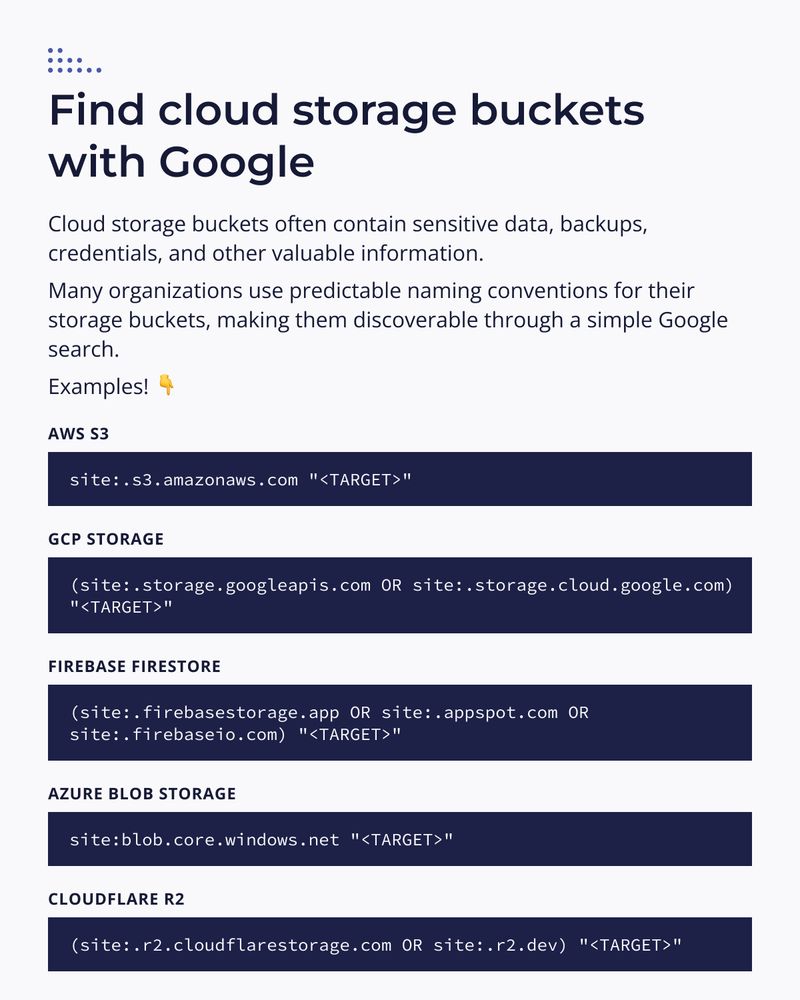
Yesterday, we covered a simple method to enumerate backend technologies with high accuracy. Today, we're hunting for exposed cloud storage buckets using Google!
Today marks day 11 of #BugQuest2025, and we're sharing a simple tip to enumerate backend services.

Today marks day 11 of #BugQuest2025, and we're sharing a simple tip to enumerate backend services.
Today, we're learning how to bypass WAF protections by finding origin IPs! 🤠


Today, we're learning how to bypass WAF protections by finding origin IPs! 🤠
Yesterday, we shared how to find secrets in browser extensions. Today, we're continuing our recon journey and checking for something surprisingly common: open registration pages! 👀


Yesterday, we shared how to find secrets in browser extensions. Today, we're continuing our recon journey and checking for something surprisingly common: open registration pages! 👀
But you have to learn to identify them at first... 🥲
In our latest article, we explored how to identify & exploit logic flaws, including how to measure impact and distinguish them from the non-impactful, functional bugs.
Read the article! 👇

But you have to learn to identify them at first... 🥲
In our latest article, we explored how to identify & exploit logic flaws, including how to measure impact and distinguish them from the non-impactful, functional bugs.
Read the article! 👇
In yesterday's issue, we expanded on content discovery to identify paths, API endpoints, and files that most bug bounty hunters miss.

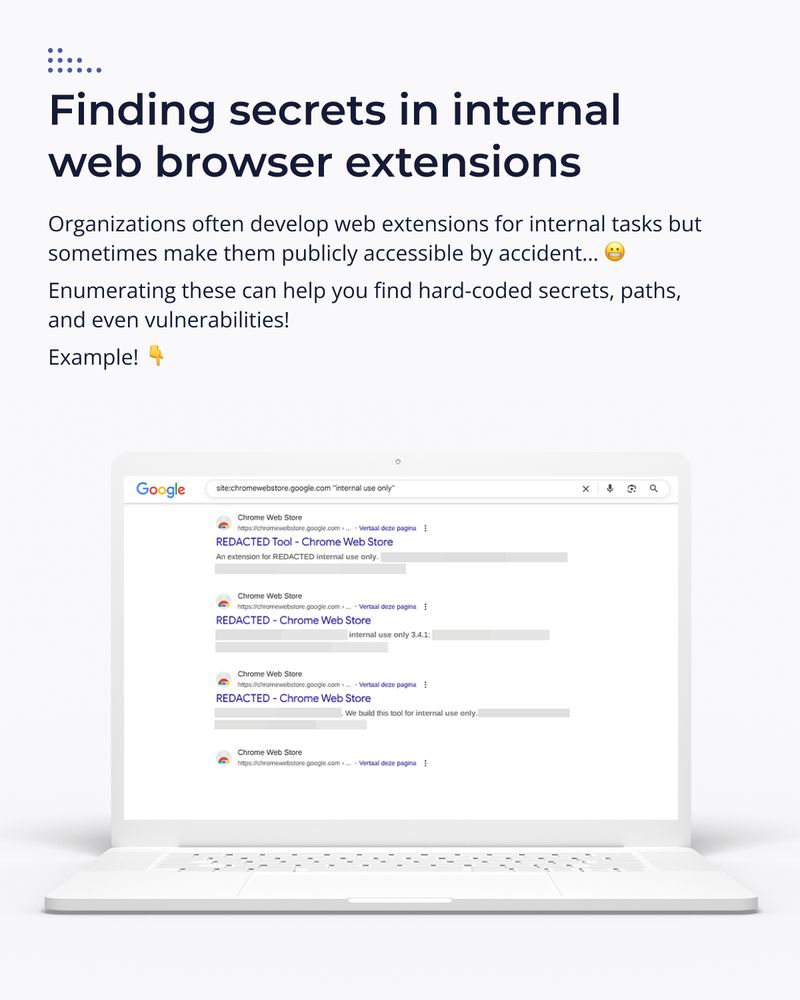
In yesterday's issue, we expanded on content discovery to identify paths, API endpoints, and files that most bug bounty hunters miss.
Yesterday, we shared a quick (and simple) tip to uncover hidden directories. Today, we're taking content discovery a step further by fuzzing with multiple HTTP methods! 🤠


Yesterday, we shared a quick (and simple) tip to uncover hidden directories. Today, we're taking content discovery a step further by fuzzing with multiple HTTP methods! 🤠
Yesterday, we shared a method to identify hidden assets related to your target. Today, we're tackling a common mistake: ignoring subdomains that redirect! 👀


Yesterday, we shared a method to identify hidden assets related to your target. Today, we're tackling a common mistake: ignoring subdomains that redirect! 👀
Yesterday, we shared a simple method to find forgotten hosts. Today, we're using something even more hidden in plain sight: copyright notices! 🤠


Yesterday, we shared a simple method to find forgotten hosts. Today, we're using something even more hidden in plain sight: copyright notices! 🤠
Yesterday, we explored a unique method to find hidden, related assets.
Today, we're diving into a goldmine that many bug bounty hunters often overlook: hosts with certificate issues! 👀

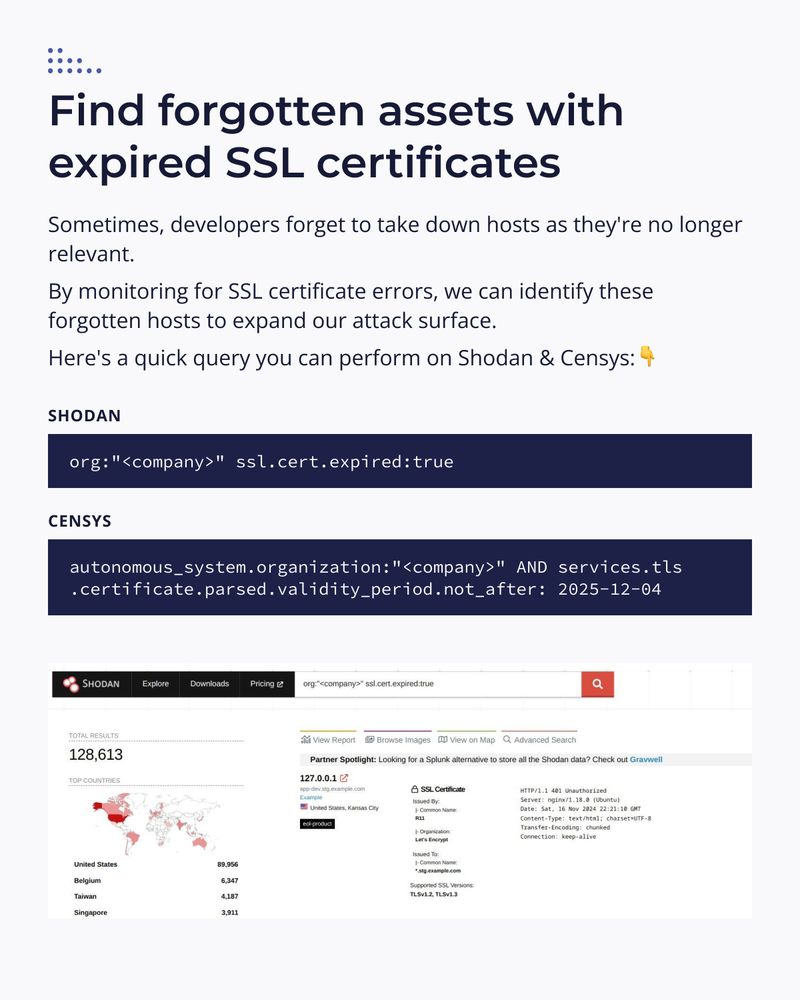
Yesterday, we explored a unique method to find hidden, related assets.
Today, we're diving into a goldmine that many bug bounty hunters often overlook: hosts with certificate issues! 👀
Today's tip further expands on identifying hidden assets with favicon hashes! 🤠
These seamless images that appear in your tab are much more than just icons..


Today's tip further expands on identifying hidden assets with favicon hashes! 🤠
These seamless images that appear in your tab are much more than just icons..
The easiest way to find more bugs is to discover assets that have never been tested before 🤠
Virtual host fuzzing is one of the most underutilized methods for identifying such assets! 👇

The easiest way to find more bugs is to discover assets that have never been tested before 🤠
Virtual host fuzzing is one of the most underutilized methods for identifying such assets! 👇
Join us in #BugQuest2025! Starting December 1st, we'll share bug bounty tips, techniques, and resources that anyone can use, no matter your experience level, background, or skill set, for 31 days. 🎁
#BugBounty #HackWithIntigriti

Join us in #BugQuest2025! Starting December 1st, we'll share bug bounty tips, techniques, and resources that anyone can use, no matter your experience level, background, or skill set, for 31 days. 🎁
#BugBounty #HackWithIntigriti
But CSP is in the way... 😓
What if you could just entirely bypass this CSP and execute your payload? 🤠
In our latest article, we documented multiple methods to bypass CSPs to execute malicious JS code!
Read the article today (link in next post)! 👇

But CSP is in the way... 😓
What if you could just entirely bypass this CSP and execute your payload? 🤠
In our latest article, we documented multiple methods to bypass CSPs to execute malicious JS code!
Read the article today (link in next post)! 👇
The administrator interface is finally ready, and according to the development team, proper authorization has been deployed, so only administrators have access. 🤠
Can you craft a working payload proving them otherwise? 😎

The administrator interface is finally ready, and according to the development team, proper authorization has been deployed, so only administrators have access. 🤠
Can you craft a working payload proving them otherwise? 😎
As Intigriti 1125 wraps up, we're releasing the official write-up for this month's CTF challenge!
We crafted a vulnerable aquarium e-commerce platform where JWT manipulation and template injection chain together for full RCE

As Intigriti 1125 wraps up, we're releasing the official write-up for this month's CTF challenge!
We crafted a vulnerable aquarium e-commerce platform where JWT manipulation and template injection chain together for full RCE
This month's issue is as usual packed with bug bounty tips:
✅ Finding an RCE using AI in GitHub
✅ CORS exploitation cheat sheet
✅ Scanning codebases with AI
✅ Bypassing paywalls
✅ SSTIs in AI models
+ monthly hacking challenge & much more! 😎

This month's issue is as usual packed with bug bounty tips:
✅ Finding an RCE using AI in GitHub
✅ CORS exploitation cheat sheet
✅ Scanning codebases with AI
✅ Bypassing paywalls
✅ SSTIs in AI models
+ monthly hacking challenge & much more! 😎
Yet, these seamless DOM-based bugs can sometimes even lead to account takeovers 👀
In our comprehensive article, we explore how you can identify and exploit this XSS type.

Yet, these seamless DOM-based bugs can sometimes even lead to account takeovers 👀
In our comprehensive article, we explore how you can identify and exploit this XSS type.
Yet, when present, they can allow for account takeovers, SQL injections and in-app privilege escalations 🤠
In our latest article, we break down every common JWT attack vector with practical exploitation techniques.

Yet, when present, they can allow for account takeovers, SQL injections and in-app privilege escalations 🤠
In our latest article, we break down every common JWT attack vector with practical exploitation techniques.
This month's issue is as usual packed with bug bounty tips:
✅ Cool trick to find disclosed secrets in internal web extensions
✅ A repository full of WAF bypasses
✅ Hacking Intercom misconfigurations
✅ Wayback Machine for hackers
+ monthly hacking challenge & much more!

This month's issue is as usual packed with bug bounty tips:
✅ Cool trick to find disclosed secrets in internal web extensions
✅ A repository full of WAF bypasses
✅ Hacking Intercom misconfigurations
✅ Wayback Machine for hackers
+ monthly hacking challenge & much more!
This developer has just completed this new MFA implementation, which provides an added layer of security to protect against credential stuffing attacks! 🤠
Can you craft a working payload to evade this MFA implementation? 😎
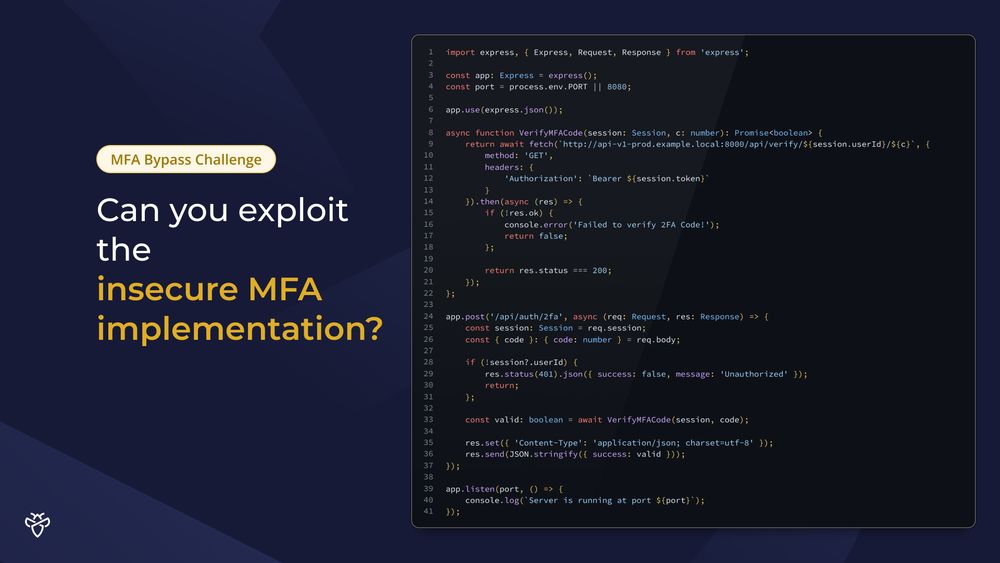
This developer has just completed this new MFA implementation, which provides an added layer of security to protect against credential stuffing attacks! 🤠
Can you craft a working payload to evade this MFA implementation? 😎
And they're all over the place... sometimes hiding in plain sight! 👀
In our most recent article, we shared a practical and beginner-friendly methodology for testing for reflected & stored XSS vulnerabilities in any target!

And they're all over the place... sometimes hiding in plain sight! 👀
In our most recent article, we shared a practical and beginner-friendly methodology for testing for reflected & stored XSS vulnerabilities in any target!

