@ilyaswebwon.bsky.social
This "boring" playlist turns you into a JS hacking
pro—real exploits, no fluff: tinyurl.com/fxrv4r32
From DOM manipulation to XSS tricks:
Who's ready to level up? 🔥
#JavaScript #WebHacking
Drop your go-to JS hack below! 👇
pro—real exploits, no fluff: tinyurl.com/fxrv4r32
From DOM manipulation to XSS tricks:
Who's ready to level up? 🔥
#JavaScript #WebHacking
Drop your go-to JS hack below! 👇

November 9, 2025 at 1:41 PM
This "boring" playlist turns you into a JS hacking
pro—real exploits, no fluff: tinyurl.com/fxrv4r32
From DOM manipulation to XSS tricks:
Who's ready to level up? 🔥
#JavaScript #WebHacking
Drop your go-to JS hack below! 👇
pro—real exploits, no fluff: tinyurl.com/fxrv4r32
From DOM manipulation to XSS tricks:
Who's ready to level up? 🔥
#JavaScript #WebHacking
Drop your go-to JS hack below! 👇
The browser security model is a fortress....
I expose client-side hacking tricks that could wreck your
apps (ethically, of course). Think you're safe?
Watch me break it : youtu.be/N0d43HXIm_s
#BrowserSecurity #JavaScript #CyberSecurity
I expose client-side hacking tricks that could wreck your
apps (ethically, of course). Think you're safe?
Watch me break it : youtu.be/N0d43HXIm_s
#BrowserSecurity #JavaScript #CyberSecurity

Browser Security model Client side hacking local file reading using Javascript
YouTube video by WebWonders
youtu.be
November 5, 2025 at 7:53 PM
The browser security model is a fortress....
I expose client-side hacking tricks that could wreck your
apps (ethically, of course). Think you're safe?
Watch me break it : youtu.be/N0d43HXIm_s
#BrowserSecurity #JavaScript #CyberSecurity
I expose client-side hacking tricks that could wreck your
apps (ethically, of course). Think you're safe?
Watch me break it : youtu.be/N0d43HXIm_s
#BrowserSecurity #JavaScript #CyberSecurity

October 29, 2025 at 6:39 PM
Reposted
(5/5) For Client-Side Race Conditions based on network requests, you can slow down time by holding up the Connection Pool. Then slowly release them one by one, performing any actions you need in between with 100% consistency.

October 17, 2025 at 8:43 AM
(5/5) For Client-Side Race Conditions based on network requests, you can slow down time by holding up the Connection Pool. Then slowly release them one by one, performing any actions you need in between with 100% consistency.
Just dropped a DEEP DIVE into HTTP Request
Smuggling (CL.TE Vulnerability) on YouTube!
Watch now: youtu.be/4cRPrmUMJa4
#Cybersecurity #WebSecurity #HTTPrequestSmuggling
Smuggling (CL.TE Vulnerability) on YouTube!
Watch now: youtu.be/4cRPrmUMJa4
#Cybersecurity #WebSecurity #HTTPrequestSmuggling

HTTP request smuggling CL.TE vulnerability Detailed Video HTTP Request Smuggling (Deep Dive)
YouTube video by WebWonders
youtu.be
October 26, 2025 at 3:07 PM
Just dropped a DEEP DIVE into HTTP Request
Smuggling (CL.TE Vulnerability) on YouTube!
Watch now: youtu.be/4cRPrmUMJa4
#Cybersecurity #WebSecurity #HTTPrequestSmuggling
Smuggling (CL.TE Vulnerability) on YouTube!
Watch now: youtu.be/4cRPrmUMJa4
#Cybersecurity #WebSecurity #HTTPrequestSmuggling
Reposted
Extended the starter with shy writers! 😀 If you're not on the list but write about web security, then feel free to reply with the article you're most proud of, and I will add you to the pack!
Make sure to resubscribe to not not miss on the amazing 🌐research!
go.bsky.app/9JXnB17
Make sure to resubscribe to not not miss on the amazing 🌐research!
go.bsky.app/9JXnB17
December 10, 2024 at 10:29 PM
Extended the starter with shy writers! 😀 If you're not on the list but write about web security, then feel free to reply with the article you're most proud of, and I will add you to the pack!
Make sure to resubscribe to not not miss on the amazing 🌐research!
go.bsky.app/9JXnB17
Make sure to resubscribe to not not miss on the amazing 🌐research!
go.bsky.app/9JXnB17
Reposted
Following other's lead, I put together an XSS challenge to solve a somewhat tricky injection I'd come across. In producing the challenge I came up with my solution (so in that way I guess it served it's purpose) but interested in how other's would approach it 🤔
blog.ajxchapman.com/xss/challeng...
blog.ajxchapman.com/xss/challeng...

March 10, 2025 at 4:19 PM
Following other's lead, I put together an XSS challenge to solve a somewhat tricky injection I'd come across. In producing the challenge I came up with my solution (so in that way I guess it served it's purpose) but interested in how other's would approach it 🤔
blog.ajxchapman.com/xss/challeng...
blog.ajxchapman.com/xss/challeng...
Reposted
Found an XSS but got blocked by the CSP?
https://cspbypass.com has a compiled list of ways to bypass the Content-Security Policy. Check out the video below 👇
https://cspbypass.com has a compiled list of ways to bypass the Content-Security Policy. Check out the video below 👇
October 21, 2025 at 9:16 AM
Found an XSS but got blocked by the CSP?
https://cspbypass.com has a compiled list of ways to bypass the Content-Security Policy. Check out the video below 👇
https://cspbypass.com has a compiled list of ways to bypass the Content-Security Policy. Check out the video below 👇
apropos of nothing I have a ton of silicon valley secrets btw
October 24, 2025 at 7:10 PM
Reposted
I often know that I know something. But when having to ask quickly, I stumble. I might have to start generating some "flash card" style questions for myself to try to ingrain some knowledge a bit deeper.
This is an example from earlier this week. It's not hard, but how quick and certain are you?
This is an example from earlier this week. It's not hard, but how quick and certain are you?
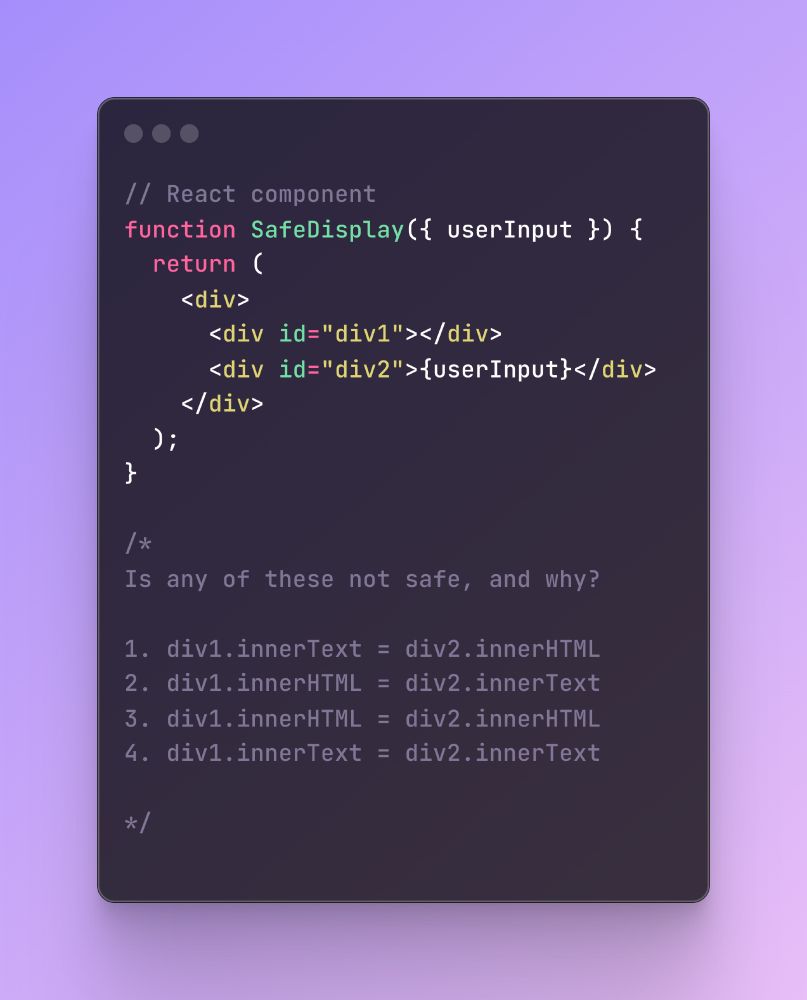
July 13, 2025 at 8:50 PM
I often know that I know something. But when having to ask quickly, I stumble. I might have to start generating some "flash card" style questions for myself to try to ingrain some knowledge a bit deeper.
This is an example from earlier this week. It's not hard, but how quick and certain are you?
This is an example from earlier this week. It's not hard, but how quick and certain are you?
Reposted
The slides and examples for my talk "Widgets Gone Wild: Exploiting XSS Through Flawed postMessage Origin Checks" at NahamCon can be found here: 0-a.nl/nahamcon/
May 24, 2025 at 9:23 AM
The slides and examples for my talk "Widgets Gone Wild: Exploiting XSS Through Flawed postMessage Origin Checks" at NahamCon can be found here: 0-a.nl/nahamcon/
Reposted
For those who missed it, check out my talk, “Widgets Gone Wild: Exploiting XSS through Flawed postMessage Origin Checks.”
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
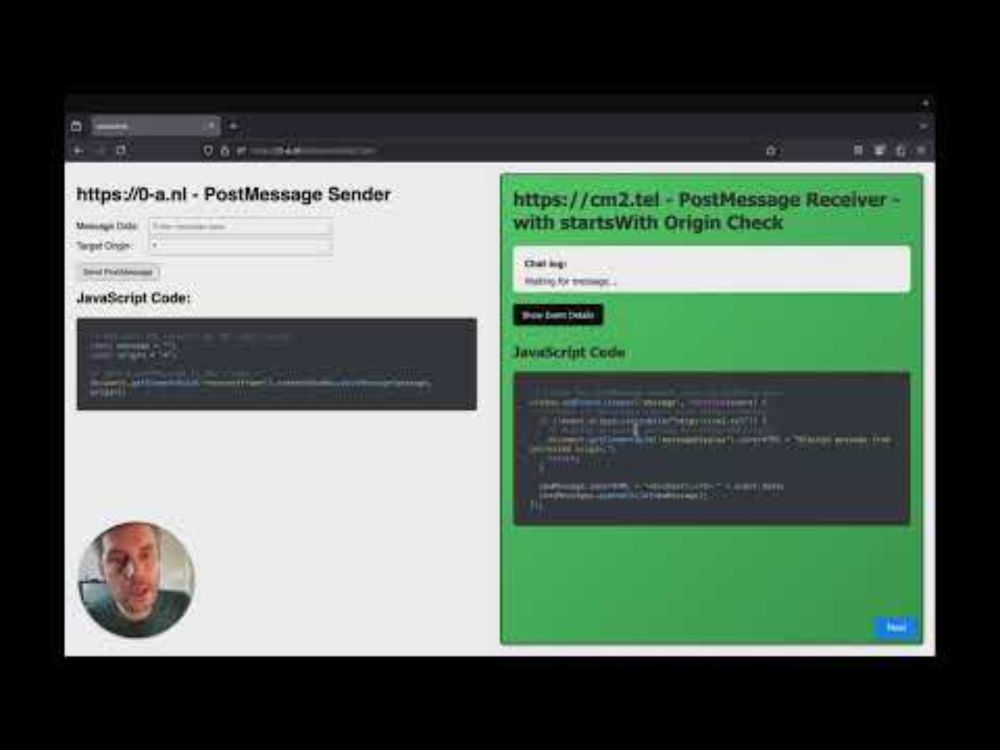
Widgets Gone Wild: Exploiting XSS Through Flawed postMessage Origin Checks
YouTube video by renniepak
www.youtube.com
May 24, 2025 at 7:33 PM
For those who missed it, check out my talk, “Widgets Gone Wild: Exploiting XSS through Flawed postMessage Origin Checks.”
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
📺 Watch here: www.youtube.com/watch?v=qgB0...
🖥️ Follow along with the slides: 0-a.nl/nahamcon/
Reposted
Imagine you have a XSS vulnerability but you have a undefined variable before your injection. Is all hope lost? Not at all you can use a technique called XSS Hoisting to declare the variable and continue your exploit. Thanks to ycam_asafety for the submission.
portswigger.net/web-security...
portswigger.net/web-security...

August 28, 2025 at 1:18 PM
Imagine you have a XSS vulnerability but you have a undefined variable before your injection. Is all hope lost? Not at all you can use a technique called XSS Hoisting to declare the variable and continue your exploit. Thanks to ycam_asafety for the submission.
portswigger.net/web-security...
portswigger.net/web-security...
Reposted
Nice addition! The only one missing is let, const, class ”hoising in the temporal dead zone” 😉
on a serious note I dont think its needed. But all these snippets reminded me of my final challenge in this post joaxcar.com/blog/2023/12...
also made me realize glitch.me is gone. Need to re-host
on a serious note I dont think its needed. But all these snippets reminded me of my final challenge in this post joaxcar.com/blog/2023/12...
also made me realize glitch.me is gone. Need to re-host

Having fun with JavaScript hoisting
Writeup of three JavaScript challenges posted on Twitter during November/December of 2023
joaxcar.com
August 28, 2025 at 6:05 PM
Nice addition! The only one missing is let, const, class ”hoising in the temporal dead zone” 😉
on a serious note I dont think its needed. But all these snippets reminded me of my final challenge in this post joaxcar.com/blog/2023/12...
also made me realize glitch.me is gone. Need to re-host
on a serious note I dont think its needed. But all these snippets reminded me of my final challenge in this post joaxcar.com/blog/2023/12...
also made me realize glitch.me is gone. Need to re-host
Reposted
Made a new small challenge where you have to break out of a web worker to leak a token in the URL
Only works in Firefox and Safari
joaxcar.com/fun/worker/a...
Only works in Firefox and Safari
joaxcar.com/fun/worker/a...
Web Worker Test
joaxcar.com
August 7, 2025 at 3:18 PM
Made a new small challenge where you have to break out of a web worker to leak a token in the URL
Only works in Firefox and Safari
joaxcar.com/fun/worker/a...
Only works in Firefox and Safari
joaxcar.com/fun/worker/a...



